mirror of
https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite.git
synced 2025-12-06 17:11:29 +00:00
Compare commits
1 Commits
linpeas_de
...
refs/pull/
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
d63d1ef32b |
57
.github/workflows/CI-master_tests.yml
vendored
57
.github/workflows/CI-master_tests.yml
vendored
@@ -5,9 +5,6 @@ on:
|
||||
branches:
|
||||
- master
|
||||
|
||||
schedule:
|
||||
- cron: "5 4 * * SUN"
|
||||
|
||||
workflow_dispatch:
|
||||
|
||||
jobs:
|
||||
@@ -87,9 +84,9 @@ jobs:
|
||||
# copy the files
|
||||
- name: Copy Dotfuscator generated files
|
||||
run: |
|
||||
cp $env:DotFuscatorGeneratedPath\x64\winPEASx64.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64_ofs.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\x86\winPEASx86.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86_ofs.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\any\winPEASany.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany_ofs.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\x64\winPEASx64.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\x86\winPEASx86.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\any\winPEASany.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany.exe"
|
||||
|
||||
# Upload all the versions for the release
|
||||
- name: Upload winpeasx64
|
||||
@@ -114,19 +111,19 @@ jobs:
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: winPEASx64_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64.exe
|
||||
|
||||
- name: Upload winpeasx86ofs
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: winPEASx86_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86.exe
|
||||
|
||||
- name: Upload winpeasanyofs
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: winPEASany_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany.exe
|
||||
|
||||
- name: Upload winpeas.bat
|
||||
uses: actions/upload-artifact@v2
|
||||
@@ -199,7 +196,7 @@ jobs:
|
||||
|
||||
# Run linpeas as a test
|
||||
- name: Run linpeas
|
||||
run: linPEAS/linpeas.sh -a -D
|
||||
run: linPEAS/linpeas.sh -t -e
|
||||
|
||||
# Upload files for release
|
||||
- name: Upload linpeas.sh
|
||||
@@ -286,7 +283,7 @@ jobs:
|
||||
|
||||
# Run macpeas parts to test it
|
||||
- name: Run macpeas
|
||||
run: linPEAS/linpeas.sh -D -o system_information,container,procs_crons_timers_srvcs_sockets,network_information,users_information,software_information
|
||||
run: linPEAS/linpeas.sh -o system_information,container,procs_crons_timers_srvcs_sockets,network_information,users_information,software_information
|
||||
|
||||
|
||||
Publish_release:
|
||||
@@ -295,21 +292,6 @@ jobs:
|
||||
|
||||
steps:
|
||||
# Download files to release
|
||||
- name: Download winpeasx64ofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx64_ofs.exe
|
||||
|
||||
- name: Download winpeasx86ofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx86_ofs.exe
|
||||
|
||||
- name: Download winpeasanyofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASany_ofs.exe
|
||||
|
||||
- name: Download winpeasx64
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
@@ -325,6 +307,21 @@ jobs:
|
||||
with:
|
||||
name: winPEASany.exe
|
||||
|
||||
- name: Download winpeasx64ofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx64_ofs.exe
|
||||
|
||||
- name: Download winpeasx86ofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx86_ofs.exe
|
||||
|
||||
- name: Download winpeasanyofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASany_ofs.exe
|
||||
|
||||
- name: Download winpeas.bat
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
@@ -365,10 +362,6 @@ jobs:
|
||||
with:
|
||||
name: linpeas_darwin_arm64
|
||||
|
||||
- name: Get current date
|
||||
id: date
|
||||
run: echo "::set-output name=date::$(date +'%Y%m%d')"
|
||||
|
||||
# Create the release
|
||||
- name: Create Release
|
||||
id: create_release
|
||||
@@ -376,8 +369,8 @@ jobs:
|
||||
env:
|
||||
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
||||
with:
|
||||
tag_name: ${{steps.date.outputs.date}}
|
||||
release_name: Release ${{ github.ref }} ${{steps.date.outputs.date}}
|
||||
tag_name: ${{ github.ref }}
|
||||
release_name: Release ${{ github.ref }}
|
||||
draft: false
|
||||
prerelease: false
|
||||
|
||||
|
||||
@@ -19,10 +19,7 @@ These tools search for possible **local privilege escalation paths** that you co
|
||||
- **[LinPEAS](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) - Linux local Privilege Escalation Awesome Script (.sh)**
|
||||
|
||||
## Quick Start
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/latest)**.
|
||||
|
||||
## JSON, HTML & PDF output
|
||||
Check the **[parsers](./parsers/)** directory to **transform PEASS outputs to JSON, HTML and PDF**
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)**.
|
||||
|
||||
## Let's improve PEASS together
|
||||
|
||||
@@ -37,5 +34,8 @@ Are you a PEASS fan? Get now our merch at **[PEASS Shop](https://teespring.com/s
|
||||
All the scripts/binaries of the PEAS suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own machines and/or with the owner's permission.
|
||||
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
|
||||
@@ -92,9 +92,7 @@ cap_setgid_markup: "peass{CAP_SETGID_HERE}"
|
||||
les_markup: "peass{LES}"
|
||||
les2_markup: "peass{LES2}"
|
||||
|
||||
fat_linpeas_amicontained_markup: "peass{AMICONTAINED}"
|
||||
fat_linpeas_gitleaks_linux_markup: "peass{GITLEAKS_LINUX}"
|
||||
fat_linpeas_gitleaks_macos_markup: "peass{GITLEAKS_MACOS}"
|
||||
|
||||
|
||||
##############################
|
||||
## AUTO GENERATED VARIABLES ##
|
||||
@@ -120,7 +118,7 @@ defaults:
|
||||
check_extra_path: "" #Check if the found files are in a specific path (only linpeas)
|
||||
good_regex: "" #The regex to color green
|
||||
just_list_file: False #Just mention the path to the file, do not cat it
|
||||
line_grep: "" #The regex to grep lines in a file. IMPORTANT: This is the argument for "grep" command so you need to specify the single and double quotes (see examples). Use double quotes to indicate the interesting things to grep as winpeas greps the things inside th double qoutes.
|
||||
line_grep: "" #The regex to grep lines in a file. IMPORTANT: This is the argument for "grep" command so you need to specify the single and double quotes (see examples)
|
||||
only_bad_lines: False #Only print lines containing something red (cnotaining bad_regex)
|
||||
remove_empty_lines: False #Remove empty lines, use only for text files (-I param in grep)
|
||||
remove_path: "" #Not interested in files containing this path (only linpeas)
|
||||
@@ -319,24 +317,6 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "passwd.ibd"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "password*.ibd"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "pwd.ibd"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: MariaDB
|
||||
value:
|
||||
config:
|
||||
@@ -403,16 +383,14 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: Apache-Nginx
|
||||
- name: Apache
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
exec:
|
||||
- 'echo "Apache version: $(warn_exec apache2 -v 2>/dev/null; warn_exec httpd -v 2>/dev/null)"'
|
||||
- 'echo "Nginx version: $(warn_exec nginx -v 2>/dev/null)"'
|
||||
- if [ -d "/etc/apache2" ] && [ -r "/etc/apache2" ]; then 'grep -R -B1 "httpd-php" /etc/apache2 2>/dev/null'; fi
|
||||
- if [ -d "/usr/share/nginx/modules" ] && [ -r "/usr/share/nginx/modules" ]; then print_3title 'Nginx modules'; ls /usr/share/nginx/modules | sed -${E} "s,$NGINX_KNOWN_MODULES,${SED_GREEN},g"; fi
|
||||
- 'echo "Version: $(warn_exec apache2 -v 2>/dev/null; warn_exec httpd -v 2>/dev/null)"'
|
||||
- "print_3title 'PHP exec extensions'"
|
||||
- 'grep -R -B1 "httpd-php" /etc/apache2 2>/dev/null'
|
||||
|
||||
files:
|
||||
- name: "sites-enabled"
|
||||
@@ -421,7 +399,8 @@ search:
|
||||
files:
|
||||
- name: "*"
|
||||
value:
|
||||
bad_regex: "AuthType|AuthName|AuthUserFile|ServerName|ServerAlias|command on"
|
||||
bad_regex: "AuthType|AuthName|AuthUserFile|ServerName|ServerAlias"
|
||||
only_bad_lines: True
|
||||
remove_empty_lines: True
|
||||
remove_regex: '#'
|
||||
search_in:
|
||||
@@ -430,7 +409,6 @@ search:
|
||||
- name: "000-default.conf"
|
||||
value:
|
||||
bad_regex: "AuthType|AuthName|AuthUserFile|ServerName|ServerAlias"
|
||||
remove_regex: '#'
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
@@ -439,7 +417,7 @@ search:
|
||||
value:
|
||||
bad_regex: "On"
|
||||
remove_regex: "^;"
|
||||
line_grep: '"allow_"'
|
||||
line_grep: "allow_"
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
@@ -563,7 +541,6 @@ search:
|
||||
auto_check: True
|
||||
exec:
|
||||
- 'echo "Version: $(warn_exec mongo --version 2>/dev/null; warn_exec mongod --version 2>/dev/null)"'
|
||||
- if [ "$(command -v mongo)" ]; then echo "show dbs" | mongo 127.0.0.1 > /dev/null 2>&1;[ "$?" == "0" ] && echo "Possible mongo anonymous authentication" | sed -${E} "s,.*|kube,${SED_RED},"; fi
|
||||
|
||||
files:
|
||||
- name: "mongod*.conf"
|
||||
@@ -574,21 +551,6 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: Rocketchat
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
|
||||
files:
|
||||
- name: "rocketchat.service"
|
||||
value:
|
||||
bad_regex: "mongodb://.*"
|
||||
line_grep: '-i "Environment"'
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
- /lib
|
||||
- /systemd
|
||||
|
||||
- name: Supervisord
|
||||
value:
|
||||
@@ -707,34 +669,6 @@ search:
|
||||
search_in:
|
||||
- /etc
|
||||
|
||||
- name: GlusterFS
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
|
||||
files:
|
||||
- name: "glusterfs.pem"
|
||||
value:
|
||||
type: f
|
||||
just_list_file: True
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "glusterfs.ca"
|
||||
value:
|
||||
type: f
|
||||
just_list_file: True
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "glusterfs.key"
|
||||
value:
|
||||
type: f
|
||||
just_list_file: True
|
||||
search_in:
|
||||
- common
|
||||
|
||||
|
||||
- name: Anaconda ks
|
||||
value:
|
||||
config:
|
||||
@@ -772,74 +706,32 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: Kubernetes
|
||||
- name: Kubelet
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
exec:
|
||||
- (env || set) | grep -Ei "kubernetes|kube" | grep -v "PSTORAGE_KUBERNETES|USEFUL_SOFTWARE" | sed -${E} "s,kubernetes|kube,${SED_RED},"
|
||||
|
||||
files:
|
||||
- name: "kubelet"
|
||||
value:
|
||||
files:
|
||||
- name: "kubeconfig"
|
||||
value:
|
||||
bad_regex: "server:|cluster:|namespace:|user:|exec:"
|
||||
type: d
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "kubelet-kubeconfig"
|
||||
value:
|
||||
bad_regex: "server:|cluster:|namespace:|user:|exec:"
|
||||
type: d
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "psk.txt"
|
||||
value:
|
||||
remove_empty_lines: True
|
||||
bad_regex: ".*"
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: ".kube*"
|
||||
value:
|
||||
files:
|
||||
- name: "config"
|
||||
value:
|
||||
bad_regex: "server:|cluster:|namespace:|user:|exec:"
|
||||
type: d
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "kubelet"
|
||||
value:
|
||||
files:
|
||||
- name: "kubelet.conf"
|
||||
value:
|
||||
bad_regex: "server:|cluster:|namespace:|user:|exec:"
|
||||
- name: "config.yaml"
|
||||
value:
|
||||
bad_regex: "server:|cluster:|namespace:|user:|exec:"
|
||||
- name: "kubeadm-flags.env"
|
||||
value:
|
||||
remove_empty_lines: True
|
||||
type: d
|
||||
search_in:
|
||||
- /var
|
||||
|
||||
- name: "kube-proxy"
|
||||
value:
|
||||
files:
|
||||
- name: "kubeconfig"
|
||||
value:
|
||||
bad_regex: "cluster:|certificate-authority-data:|namespace:|user:|token:"
|
||||
type: d
|
||||
search_in:
|
||||
- /var
|
||||
|
||||
- name: "kubernetes"
|
||||
value:
|
||||
type: d
|
||||
search_in:
|
||||
- /etc
|
||||
|
||||
- name: VNC
|
||||
value:
|
||||
config:
|
||||
@@ -859,7 +751,6 @@ search:
|
||||
- name: "*vnc*.c*nf*"
|
||||
value:
|
||||
bad_regex: ".*"
|
||||
remove_regex: '^#'
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
@@ -1049,6 +940,7 @@ search:
|
||||
type: f
|
||||
search_in:
|
||||
- /tmp
|
||||
- /private
|
||||
|
||||
- name: SSH_CONFIG
|
||||
value:
|
||||
@@ -1069,12 +961,12 @@ search:
|
||||
auto_check: True
|
||||
|
||||
files:
|
||||
#- name: "credentials"
|
||||
# value:
|
||||
# bad_regex: ".*"
|
||||
# type: f
|
||||
# search_in:
|
||||
# - common
|
||||
- name: "credentials"
|
||||
value:
|
||||
bad_regex: ".*"
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "credentials.db"
|
||||
value:
|
||||
@@ -1624,37 +1516,6 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "dockershim.sock"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "containerd.sock"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "crio.sock"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "frakti.sock"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: "rktlet.sock"
|
||||
value:
|
||||
type: f
|
||||
search_in:
|
||||
- common
|
||||
|
||||
|
||||
- name: Firefox
|
||||
value:
|
||||
disable:
|
||||
@@ -2706,7 +2567,7 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: Other Interesting
|
||||
- name: Other Interesting Files
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
@@ -2775,7 +2636,7 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: Windows
|
||||
- name: Windows Files
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
@@ -3124,7 +2985,7 @@ search:
|
||||
search_in:
|
||||
- common
|
||||
|
||||
- name: Other Windows
|
||||
- name: Other Windows Files
|
||||
value:
|
||||
config:
|
||||
auto_check: True
|
||||
|
||||
@@ -13,11 +13,11 @@ Check the **Local Linux Privilege Escalation checklist** from **[book.hacktricks
|
||||
Just execute `linpeas.sh` in a MacOS system and the **MacPEAS version will be automatically executed**
|
||||
|
||||
## Quick Start
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/latest)**.
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)**.
|
||||
|
||||
```bash
|
||||
# From github
|
||||
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
|
||||
curl -L https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/linpeas.sh | sh
|
||||
```
|
||||
|
||||
```bash
|
||||
@@ -42,7 +42,7 @@ less -r /dev/shm/linpeas.txt #Read with colors
|
||||
|
||||
```bash
|
||||
# Use a linpeas binary
|
||||
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas_linux_amd64
|
||||
wget https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/linpeas_linux_amd64
|
||||
chmod +x linpeas_linux_amd64
|
||||
./linpeas_linux_amd64
|
||||
```
|
||||
@@ -203,5 +203,8 @@ If you find any issue, please report it using **[github issues](https://github.c
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
@@ -21,29 +21,6 @@ else echo_not_found "sudo"
|
||||
fi
|
||||
echo ""
|
||||
|
||||
#-- SY) CVE-2021-4034
|
||||
if [ `command -v pkexec` ] && stat -c '%a' $(which pkexec) | grep -q 4755 && [ "$(stat -c '%Y' $(which pkexec))" -lt "1642035600" ]; then
|
||||
echo "Vulnerable to CVE-2021-4034" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
echo ""
|
||||
fi
|
||||
|
||||
#-- SY) CVE-2021-3560
|
||||
polkitVersion=$(systemctl status polkit.service | grep version | cut -d " " -f 9)
|
||||
if [[ "$(apt list --installed 2>/dev/null | grep polkit | grep -c 0.105-26)" -ge 1 || "$(rpm -qa | grep polkit | grep -c '0.117-2\|0.115-6')" -ge 1 ]]; then
|
||||
echo "Vulnerable to CVE-2021-3560" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
echo ""
|
||||
fi
|
||||
|
||||
#-- SY) CVE-2022-0847
|
||||
#-- https://dirtypipe.cm4all.com/
|
||||
#-- https://stackoverflow.com/a/37939589
|
||||
kernelversion=$(uname -r | awk -F"-" '{print $1}')
|
||||
kernelnumber=$(echo $kernelversion | awk -F. '{ printf("%d%03d%03d%03d\n", $1,$2,$3,$4); }')
|
||||
if [[ $kernelnumber -ge 5008000000 && $kernelnumber -lt 5017000000 ]]; then # if kernel version beteen 5.8 and 5.17
|
||||
echo "Vulnerable to CVE-2022-0847" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
echo ""
|
||||
fi
|
||||
|
||||
#--SY) USBCreator
|
||||
if (busctl list 2>/dev/null | grep -q com.ubuntu.USBCreator) || [ "$DEBUG" ]; then
|
||||
print_2title "USBCreator"
|
||||
@@ -100,8 +77,8 @@ fi
|
||||
|
||||
if [ -f "/etc/fstab" ] || [ "$DEBUG" ]; then
|
||||
print_2title "Unmounted file-system?"
|
||||
print_info "Check if you can mount unmounted devices"
|
||||
grep -v "^#" /etc/fstab 2>/dev/null | grep -Ev "\W+\#|^#" | sed -${E} "s,$mountG,${SED_GREEN},g" | sed -${E} "s,$notmounted,${SED_RED},g" | sed -${E} "s%$mounted%${SED_BLUE}%g" | sed -${E} "s,$Wfolders,${SED_RED}," | sed -${E} "s,$mountpermsB,${SED_RED},g" | sed -${E} "s,$mountpermsG,${SED_GREEN},g"
|
||||
print_info "Check if you can mount umounted devices"
|
||||
grep -v "^#" /etc/fstab 2>/dev/null | grep -Ev "\W+\#|^#" | sed -${E} "s,$mountG,${SED_GREEN},g" | sed -${E} "s,$notmounted,${SED_RED}," | sed -${E} "s,$mounted,${SED_BLUE}," | sed -${E} "s,$Wfolders,${SED_RED}," | sed -${E} "s,$mountpermsB,${SED_RED},g" | sed -${E} "s,$mountpermsG,${SED_GREEN},g"
|
||||
echo ""
|
||||
fi
|
||||
|
||||
@@ -120,7 +97,7 @@ fi
|
||||
#-- SY) Environment vars
|
||||
print_2title "Environment"
|
||||
print_info "Any private information inside environment variables?"
|
||||
(env || printenv || set) 2>/dev/null | grep -v "RELEVANT*|FIND*|^VERSION=|dbuslistG|mygroups|ldsoconfdG|pwd_inside_history|kernelDCW_Ubuntu_Precise|kernelDCW_Ubuntu_Trusty|kernelDCW_Ubuntu_Xenial|kernelDCW_Rhel|^sudovB=|^rootcommon=|^mounted=|^mountG=|^notmounted=|^mountpermsB=|^mountpermsG=|^kernelB=|^C=|^RED=|^GREEN=|^Y=|^B=|^NC=|TIMEOUT=|groupsB=|groupsVB=|knw_grps=|sidG|sidB=|sidVB=|sidVB2=|sudoB=|sudoG=|sudoVB=|timersG=|capsB=|notExtensions=|Wfolders=|writeB=|writeVB=|_usrs=|compiler=|PWD=|LS_COLORS=|pathshG=|notBackup=|processesDump|processesB|commonrootdirs|USEFUL_SOFTWARE" | sed -${E} "s,[pP][wW][dD]|[pP][aA][sS][sS][wW]|[aA][pP][iI][kK][eE][yY]|[aA][pP][iI][_][kK][eE][yY]|KRB5CCNAME,${SED_RED},g" || echo_not_found "env || set"
|
||||
(env || printenv || set) 2>/dev/null | grep -v "RELEVANT*|FIND*|^VERSION=|dbuslistG|mygroups|ldsoconfdG|pwd_inside_history|kernelDCW_Ubuntu_Precise|kernelDCW_Ubuntu_Trusty|kernelDCW_Ubuntu_Xenial|kernelDCW_Rhel|^sudovB=|^rootcommon=|^mounted=|^mountG=|^notmounted=|^mountpermsB=|^mountpermsG=|^kernelB=|^C=|^RED=|^GREEN=|^Y=|^B=|^NC=|TIMEOUT=|groupsB=|groupsVB=|knw_grps=|sidG|sidB=|sidVB=|sidVB2=|sudoB=|sudoG=|sudoVB=|timersG=|capsB=|notExtensions=|Wfolders=|writeB=|writeVB=|_usrs=|compiler=|PWD=|LS_COLORS=|pathshG=|notBackup=|processesDump|processesB|commonrootdirs|USEFUL_SOFTWARE|PSTORAGE_KUBELET" | sed -${E} "s,[pP][wW][dD]|[pP][aA][sS][sS][wW]|[aA][pP][iI][kK][eE][yY]|[aA][pP][iI][_][kK][eE][yY]|KRB5CCNAME,${SED_RED},g" || echo_not_found "env || set"
|
||||
echo ""
|
||||
|
||||
#-- SY) Dmesg
|
||||
@@ -145,10 +122,9 @@ if [ "$(command -v bash 2>/dev/null)" ]; then
|
||||
print_2title "Executing Linux Exploit Suggester"
|
||||
print_info "https://github.com/mzet-/linux-exploit-suggester"
|
||||
les_b64="peass{LES}"
|
||||
echo $les_b64 | base64 -d | bash
|
||||
if [ "$EXTRA_CHECKS" ]; then
|
||||
echo $les_b64 | base64 -d | bash -s -- --checksec | sed "s,$(printf '\033')\\[[0-9;]*[a-zA-Z],,g" | sed -E "s,\[CVE-[0-9]+-[0-9]+\].*,${SED_RED},g"
|
||||
else
|
||||
echo $les_b64 | base64 -d | bash | sed "s,$(printf '\033')\\[[0-9;]*[a-zA-Z],,g" | grep -i "\[CVE" -A 10 | grep -Ev "^\-\-$" | sed -${E} "s,\[CVE-[0-9]+-[0-9]+\].*,${SED_RED},g"
|
||||
echo $les_b64 | base64 -d | bash -s -- --checksec
|
||||
fi
|
||||
echo ""
|
||||
fi
|
||||
@@ -157,7 +133,7 @@ if [ "$(command -v perl 2>/dev/null)" ]; then
|
||||
print_2title "Executing Linux Exploit Suggester 2"
|
||||
print_info "https://github.com/jondonas/linux-exploit-suggester-2"
|
||||
les2_b64="peass{LES2}"
|
||||
echo $les2_b64 | base64 -d | perl | sed "s,$(printf '\033')\\[[0-9;]*[a-zA-Z],,g" | grep -i "CVE" -B 1 -A 10 | grep -Ev "^\-\-$" | sed -${E} "s,CVE-[0-9]+-[0-9]+,${SED_RED},g"
|
||||
echo $les2_b64 | base64 -d | perl
|
||||
echo ""
|
||||
fi
|
||||
|
||||
|
||||
@@ -28,7 +28,7 @@ else
|
||||
echo ""
|
||||
|
||||
#-- PCS) Binary processes permissions
|
||||
print_2title "Binary processes permissions (non 'root root' and not belonging to current user)"
|
||||
print_2title "Binary processes permissions (non 'root root' and not beloging to current user)"
|
||||
print_info "https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes"
|
||||
binW="IniTialiZZinnggg"
|
||||
ps auxwww 2>/dev/null | awk '{print $11}' | while read bpath; do
|
||||
|
||||
@@ -60,15 +60,15 @@ fi
|
||||
#-- UI) Sudo -l
|
||||
print_2title "Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d"
|
||||
print_info "https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid"
|
||||
(echo '' | timeout 1 sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW}," | sed "s,\!root,${SED_RED},") 2>/dev/null || echo_not_found "sudo"
|
||||
(echo '' | sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW}," | sed "s,\!root,${SED_RED},") 2>/dev/null || echo_not_found "sudo"
|
||||
if [ "$PASSWORD" ]; then
|
||||
(echo "$PASSWORD" | timeout 1 sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},") 2>/dev/null || echo_not_found "sudo"
|
||||
(echo "$PASSWORD" | sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},") 2>/dev/null || echo_not_found "sudo"
|
||||
fi
|
||||
( grep -Iv "^$" cat /etc/sudoers | grep -v "#" | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed "s,pwfeedback,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},") 2>/dev/null || echo_not_found "/etc/sudoers"
|
||||
if ! [ "$IAMROOT" ] && [ -w '/etc/sudoers.d/' ]; then
|
||||
echo "You can create a file in /etc/sudoers.d/ and escalate privileges" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
fi
|
||||
for filename in /etc/sudoers.d/*; do
|
||||
for filename in '/etc/sudoers.d/*'; do
|
||||
if [ -r "$filename" ]; then
|
||||
echo "Sudoers file: $filename is readable" | sed -${E} "s,.*,${SED_RED},g"
|
||||
grep -Iv "^$" "$filename" | grep -v "#" | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed "s,pwfeedback,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},"
|
||||
|
||||
@@ -2,8 +2,6 @@
|
||||
#--------) Software Information (---------#
|
||||
###########################################
|
||||
|
||||
NGINX_KNOWN_MODULES="ngx_http_geoip_module.so|ngx_http_xslt_filter_module.so|ngx_stream_geoip_module.so|ngx_http_image_filter_module.so|ngx_mail_module.so|ngx_stream_module.so"
|
||||
|
||||
#-- SI) Useful software
|
||||
print_2title "Useful software"
|
||||
for tool in $USEFUL_SOFTWARE; do command -v "$tool"; done
|
||||
@@ -80,46 +78,30 @@ fi
|
||||
if [ "$PSTORAGE_MYSQL" ] || [ "$DEBUG" ]; then
|
||||
print_2title "Searching mysql credentials and exec"
|
||||
printf "%s\n" "$PSTORAGE_MYSQL" | while read d; do
|
||||
if [ -f "$d" ]; then
|
||||
STRINGS="`command -v strings`"
|
||||
echo "Potential file containing credentials:"
|
||||
ls -l "$d"
|
||||
if [ "$STRINGS" ]; then
|
||||
strings "$d"
|
||||
else
|
||||
echo "Strings not found, cat the file and check it to get the creds"
|
||||
fi
|
||||
|
||||
else
|
||||
for f in $(find $d -name debian.cnf 2>/dev/null); do
|
||||
if [ -r "$f" ]; then
|
||||
echo "We can read the mysql debian.cnf. You can use this username/password to log in MySQL" | sed -${E} "s,.*,${SED_RED},"
|
||||
cat "$f"
|
||||
fi
|
||||
done
|
||||
|
||||
for f in $(find $d -name user.MYD 2>/dev/null); do
|
||||
if [ -r "$f" ]; then
|
||||
echo "We can read the Mysql Hashes from $f" | sed -${E} "s,.*,${SED_RED},"
|
||||
grep -oaE "[-_\.\*a-Z0-9]{3,}" "$f" | grep -v "mysql_native_password"
|
||||
grep -oaE "[-_\.\*a-Z0-9]{3,}" $f | grep -v "mysql_native_password"
|
||||
fi
|
||||
done
|
||||
|
||||
for f in $(grep -lr "user\s*=" $d 2>/dev/null | grep -v "debian.cnf"); do
|
||||
if [ -r "$f" ]; then
|
||||
u=$(cat "$f" | grep -v "#" | grep "user" | grep "=" 2>/dev/null)
|
||||
echo "From '$f' Mysql user: $u" | sed -${E} "s,$sh_usrs,${SED_LIGHT_CYAN}," | sed -${E} "s,$nosh_usrs,${SED_BLUE}," | sed -${E} "s,$knw_usrs,${SED_GREEN}," | sed "s,$USER,${SED_LIGHT_MAGENTA}," | sed "s,root,${SED_RED},"
|
||||
fi
|
||||
done
|
||||
|
||||
for f in $(find $d -name my.cnf 2>/dev/null); do
|
||||
if [ -r "$f" ]; then
|
||||
echo "Found readable $f"
|
||||
grep -v "^#" "$f" | grep -Ev "\W+\#|^#" 2>/dev/null | grep -Iv "^$" | sed "s,password.*,${SED_RED},"
|
||||
fi
|
||||
done
|
||||
fi
|
||||
|
||||
mysqlexec=$(whereis lib_mysqludf_sys.so 2>/dev/null | grep "lib_mysqludf_sys\.so")
|
||||
if [ "$mysqlexec" ]; then
|
||||
echo "Found $mysqlexec"
|
||||
@@ -160,7 +142,7 @@ fi
|
||||
|
||||
peass{Mongo}
|
||||
|
||||
peass{Apache-Nginx}
|
||||
peass{Apache}
|
||||
|
||||
peass{Tomcat}
|
||||
|
||||
@@ -210,7 +192,7 @@ if [ "$PSTORAGE_CERTSB4" ]; then certsb4_grep=$(grep -L "\"\|'\|(" $PSTORAGE_CER
|
||||
sshconfig="$(ls /etc/ssh/ssh_config 2>/dev/null)"
|
||||
hostsdenied="$(ls /etc/hosts.denied 2>/dev/null)"
|
||||
hostsallow="$(ls /etc/hosts.allow 2>/dev/null)"
|
||||
writable_agents=$(find /tmp /etc /home -type s -name "agent.*" -or -name "*gpg-agent*" '(' '(' -user $USER ')' -or '(' -perm -o=w ')' -or '(' -perm -g=w -and '(' $wgroups ')' ')' ')' 2>/dev/null)
|
||||
writable_agents=$(find $folder_path -type s -name "agent.*" -or -name "*gpg-agent*" '(' '(' -user $USER ')' -or '(' -perm -o=w ')' -or '(' -perm -g=w -and '(' $wgroups ')' ')' ')')
|
||||
|
||||
peass{SSH}
|
||||
|
||||
@@ -566,17 +548,25 @@ fi
|
||||
#-- SI) Docker
|
||||
if [ "$PSTORAGE_DOCKER" ] || [ "$DEBUG" ]; then
|
||||
print_2title "Searching docker files (limit 70)"
|
||||
print_info "https://book.hacktricks.xyz/linux-unix/privilege-escalation/docker-breakout/docker-breakout-privilege-escalation"
|
||||
print_info "https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-docker-socket"
|
||||
printf "%s\n" "$PSTORAGE_DOCKER" | head -n 70 | while read f; do
|
||||
ls -l "$f" 2>/dev/null
|
||||
if ! [ "$IAMROOT" ] && [ -S "$f" ] && [ -w "$f" ]; then
|
||||
echo "Docker related socket ($f) is writable" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
echo "Docker socket file ($f) is writable" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
fi
|
||||
done
|
||||
echo ""
|
||||
fi
|
||||
|
||||
peass{Kubernetes}
|
||||
if [ -d "$HOME/.kube" ] || [ -d "/etc/kubernetes" ] || [ -d "/var/lib/localkube" ] || [ "`(env | set) | grep -Ei 'kubernetes|kube' | grep -v "PSTORAGE_KUBELET|USEFUL_SOFTWARE"`" ] || [ "$DEBUG" ]; then
|
||||
print_2title "Kubernetes information" | sed -${E} "s,config,${SED_RED},"
|
||||
ls -l "$HOME/.kube" 2>/dev/null
|
||||
grep -ERH "client-secret:|id-token:|refresh-token:" "$HOME/.kube" 2>/dev/null | sed -${E} "s,client-secret:.*|id-token:.*|refresh-token:.*,${SED_RED},"
|
||||
(env || set) | grep -Ei "kubernetes|kube" | grep -v "PSTORAGE_KUBELET|USEFUL_SOFTWARE" | sed -${E} "s,kubernetes|kube,${SED_RED},"
|
||||
ls -Rl /etc/kubernetes /var/lib/localkube 2>/dev/null
|
||||
fi
|
||||
|
||||
peass{Kubelet}
|
||||
|
||||
peass{Firefox}
|
||||
|
||||
@@ -632,20 +622,6 @@ peass{EXTRA_SECTIONS}
|
||||
|
||||
peass{Interesting logs}
|
||||
|
||||
peass{Windows}
|
||||
peass{Windows Files}
|
||||
|
||||
peass{Other Interesting}
|
||||
|
||||
if ! [ "$FAST" ] && ! [ "$SUPERFAST" ] && [ "$TIMEOUT" ]; then
|
||||
print_2title "Checking leaks in git repositories"
|
||||
printf "%s\n" "$PSTORAGE_GITHUB" | while read f; do
|
||||
if echo "$f" | grep -Eq ".git$"; then
|
||||
git_dirname=$(dirname "$f")
|
||||
if [ "$MACPEAS" ]; then
|
||||
execBin "GitLeaks (checking $git_dirname)" "https://github.com/zricethezav/gitleaks" "$FAT_LINPEAS_GITLEAKS_MACOS" "detect -s '$git_dirname' -v | grep -E 'Description|Match|Secret|Message|Date'"
|
||||
else
|
||||
execBin "GitLeaks (checking $git_dirname)" "https://github.com/zricethezav/gitleaks" "$FAT_LINPEAS_GITLEAKS_LINUX" "detect -s '$git_dirname' -v | grep -E 'Description|Match|Secret|Message|Date'"
|
||||
fi
|
||||
fi
|
||||
done
|
||||
fi
|
||||
peass{Other Interesting Files}
|
||||
|
||||
@@ -257,18 +257,12 @@ if [ "$broken_links" ] || [ "$DEBUG" ]; then
|
||||
echo ""
|
||||
fi
|
||||
|
||||
|
||||
if [ "$MACPEAS" ]; then
|
||||
print_2title "Unsigned Applications"
|
||||
macosNotSigned /System/Applications
|
||||
fi
|
||||
|
||||
##-- IF) Unexpected in /opt
|
||||
if [ "$(ls /opt 2>/dev/null)" ]; then
|
||||
print_2title "Unexpected in /opt (usually empty)"
|
||||
ls -la /opt
|
||||
echo ""
|
||||
fi
|
||||
|
||||
##-- IF) Unexpected folders in /
|
||||
print_2title "Unexpected in root"
|
||||
if [ "$MACPEAS" ]; then
|
||||
|
||||
@@ -220,7 +220,7 @@ print_support () {
|
||||
|---------------------------------------------------------------------------|
|
||||
| ${YELLOW}Become a Patreon${GREEN} : ${RED}https://www.patreon.com/peass${GREEN} |
|
||||
| ${YELLOW}Follow on Twitter${GREEN} : ${RED}@carlospolopm${GREEN} |
|
||||
| ${YELLOW}Respect on HTB${GREEN} : ${RED}SirBroccoli ${GREEN} |
|
||||
| ${YELLOW}Respect on HTB${GREEN} : ${RED}SirBroccoli & makikvues${GREEN} |
|
||||
|---------------------------------------------------------------------------|
|
||||
| ${BLUE}Thank you! ${GREEN} |
|
||||
\---------------------------------------------------------------------------/
|
||||
|
||||
@@ -37,7 +37,7 @@ class MetasploitModule < Msf::Post
|
||||
))
|
||||
register_options(
|
||||
[
|
||||
OptString.new('PEASS_URL', [true, 'Path to the PEASS script. Accepted: http(s):// URL or absolute local path. Linpeas: https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh', "https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe"]),
|
||||
OptString.new('PEASS_URL', [true, 'Path to the PEASS script. Accepted: http(s):// URL or absolute local path. Linpeas: https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/linPEAS/linpeas.sh', "https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/winPEAS/winPEASexe/binaries/Obfuscated%20Releases/winPEASany.exe"]),
|
||||
OptString.new('PASSWORD', [false, 'Password to encrypt and obfuscate the script (randomly generated). The length must be 32B. If no password is set, only base64 will be used.', rand(36**32).to_s(36)]),
|
||||
OptString.new('TEMP_DIR', [false, 'Path to upload the obfuscated PEASS script inside the compromised machine. By default "C:\Windows\System32\spool\drivers\color" is used in Windows and "/tmp" in Unix.', '']),
|
||||
OptString.new('PARAMETERS', [false, 'Parameters to pass to the script', nil]),
|
||||
|
||||
@@ -1,15 +1,14 @@
|
||||
# Privilege Escalation Awesome Scripts Parsers
|
||||
# Privilege Escalation Awesome Scripts JSON exporter
|
||||
|
||||
These scripts allows you to transform the output of linpeas/macpeas/winpeas to JSON and then to PDF and HTML.
|
||||
This script allows you to transform the output of linpeas/macpeas/winpeas to JSON.
|
||||
|
||||
```python3
|
||||
python3 peass2json.py </path/to/executed_peass.out> </path/to/peass.json>
|
||||
python3 json2pdf.py </path/to/peass.json> </path/to/peass.pdf>
|
||||
python3 json2html.py </path/to/peass.json> </path/to/peass.html>
|
||||
python3 peass-parser.py </path/to/executed_peass> </path/to/output_peass.json>
|
||||
```
|
||||
|
||||
This script is still in beta version and has been tested only with linpeas output.
|
||||
|
||||
## JSON Format
|
||||
## Format
|
||||
Basically, **each section has**:
|
||||
- Infos (URLs or info about the section)
|
||||
- Text lines (the real text info found in the section, colors included)
|
||||
@@ -76,4 +75,4 @@ There can also be a `<Third level Section Name>`
|
||||
|
||||
# TODO:
|
||||
|
||||
- **PRs improving the code and the aspect of the final PDFs and HTMLs are always welcome!**
|
||||
I'm looking for **someone that could create HTML and PDF reports** from this JSON.
|
||||
@@ -5,7 +5,7 @@ import re
|
||||
import json
|
||||
|
||||
# Pattern to identify main section titles
|
||||
TITLE1_PATTERN = r"══════════════╣" # The size of the first pattern varies, but at least should be that large
|
||||
TITLE1_PATTERN = r"════════════════════════════════════╣"
|
||||
TITLE2_PATTERN = r"╔══════════╣"
|
||||
TITLE3_PATTERN = r"══╣"
|
||||
INFO_PATTERN = r"╚ "
|
||||
@@ -14,15 +14,15 @@ TITLE_CHARS = ['═', '╔', '╣', '╚']
|
||||
# Patterns for colors
|
||||
## The order is important, the first string colored with a color will be the one selected (the same string cannot be colored with different colors)
|
||||
COLORS = {
|
||||
"REDYELLOW": ['\x1b[1;31;103m'],
|
||||
"RED": ['\x1b[1;31m'],
|
||||
"GREEN": ['\x1b[1;32m'],
|
||||
"YELLOW": ['\x1b[1;33m'],
|
||||
"BLUE": ['\x1b[1;34m'],
|
||||
"MAGENTA": ['\x1b[1;95m', '\x1b[1;35m'],
|
||||
"CYAN": ['\x1b[1;36m', '\x1b[1;96m'],
|
||||
"LIGHT_GREY": ['\x1b[1;37m'],
|
||||
"DARKGREY": ['\x1b[1;90m'],
|
||||
"REDYELLOW": [r"\x1b\[1;31;103m"],
|
||||
"RED": [r"\x1b\[1;31m"],
|
||||
"GREEN": [r"\x1b\[1;32m"],
|
||||
"YELLOW": [r"\x1b\[1;33m"],
|
||||
"BLUE": [r"\x1b\[1;34m"],
|
||||
"MAGENTA": [r"\x1b\[1;95m", r"\x1b\[1;35m"],
|
||||
"CYAN": [r"\x1b\[1;36m", r"\x1b\[1;96m"],
|
||||
"LIGHT_GREY": [r"\x1b\[1;37m"],
|
||||
"DARKGREY": [r"\x1b\[1;90m"],
|
||||
}
|
||||
|
||||
|
||||
@@ -52,23 +52,11 @@ def get_colors(line: str) -> dict:
|
||||
for c,regexs in COLORS.items():
|
||||
colors[c] = []
|
||||
for reg in regexs:
|
||||
split_color = line.split(reg)
|
||||
|
||||
# Start from the index 1 as the index 0 isn't colored
|
||||
if split_color and len(split_color) > 1:
|
||||
split_color = split_color[1:]
|
||||
|
||||
# For each potential color, find the string before any possible color terminatio
|
||||
for potential_color_str in split_color:
|
||||
color_str1 = potential_color_str.split('\x1b')[0]
|
||||
color_str2 = potential_color_str.split("\[0")[0]
|
||||
color_str = color_str1 if len(color_str1) < len(color_str2) else color_str2
|
||||
|
||||
if color_str:
|
||||
color_str = clean_colors(color_str.strip())
|
||||
for re_found in re.findall(reg+"(.+?)\x1b|$", line):
|
||||
re_found = clean_colors(re_found.strip())
|
||||
#Avoid having the same color for the same string
|
||||
if color_str and not any(color_str in values for values in colors.values()):
|
||||
colors[c].append(color_str)
|
||||
if re_found and not any(re_found in values for values in colors.values()):
|
||||
colors[c].append(re_found)
|
||||
|
||||
if not colors[c]:
|
||||
del colors[c]
|
||||
@@ -87,10 +75,10 @@ def clean_title(line: str) -> str:
|
||||
def clean_colors(line: str) -> str:
|
||||
"""Given a line clean the colors inside of it"""
|
||||
|
||||
for reg in re.findall(r'\x1b\[[^a-zA-Z]+\dm', line):
|
||||
for reg in re.findall(r'\x1b[^ ]+\dm', line):
|
||||
line = line.replace(reg,"")
|
||||
|
||||
line = line.replace('\x1b',"").replace("[0m", "").replace("[3m", "") #Sometimes that byte stays
|
||||
line = line.replace('\x1b',"") #Sometimes that byte stays
|
||||
line = line.strip()
|
||||
return line
|
||||
|
||||
@@ -106,9 +94,6 @@ def parse_line(line: str):
|
||||
|
||||
global FINAL_JSON, C_SECTION, C_MAIN_SECTION, C_2_SECTION, C_3_SECTION
|
||||
|
||||
if "Cron jobs" in line:
|
||||
a=1
|
||||
|
||||
if is_section(line, TITLE1_PATTERN):
|
||||
title = parse_title(line)
|
||||
FINAL_JSON[title] = { "sections": {}, "lines": [], "infos": [] }
|
||||
@@ -139,13 +124,13 @@ def parse_line(line: str):
|
||||
|
||||
C_SECTION["lines"].append({
|
||||
"raw_text": line,
|
||||
"colors": get_colors(line),
|
||||
"clean_text": clean_title(clean_colors(line))
|
||||
"clean_text": clean_colors(line),
|
||||
"colors": get_colors(line)
|
||||
})
|
||||
|
||||
|
||||
def main():
|
||||
for line in open(OUTPUT_PATH, 'r', encoding="utf8").readlines():
|
||||
for line in open(OUTPUT_PATH, 'r').readlines():
|
||||
line = line.strip()
|
||||
if not line or not clean_colors(line): #Remove empty lines or lines just with colors hex
|
||||
continue
|
||||
@@ -162,7 +147,7 @@ if __name__ == "__main__":
|
||||
OUTPUT_PATH = sys.argv[1]
|
||||
JSON_PATH = sys.argv[2]
|
||||
except IndexError as err:
|
||||
print("Error: Please pass the peas.out file and the path to save the json\npeas2json.py <output_file> <json_file.json>")
|
||||
print("Error: Please pass the peas.out file and the path to save the json\n./peas-parser.py <output_file> <json_file.json>")
|
||||
sys.exit(1)
|
||||
|
||||
main()
|
||||
File diff suppressed because one or more lines are too long
@@ -1,162 +0,0 @@
|
||||
#!/usr/bin/env python3
|
||||
import sys
|
||||
import json
|
||||
import html
|
||||
from reportlab.lib.pagesizes import letter
|
||||
from reportlab.platypus import Frame, Paragraph, Spacer, PageBreak,PageTemplate, BaseDocTemplate
|
||||
from reportlab.platypus.tableofcontents import TableOfContents
|
||||
from reportlab.lib.styles import getSampleStyleSheet, ParagraphStyle
|
||||
from reportlab.lib.units import cm
|
||||
|
||||
styles = getSampleStyleSheet()
|
||||
text_colors = { "GREEN": "#00DB00", "RED": "#FF0000", "REDYELLOW": "#FFA500", "BLUE": "#0000FF",
|
||||
"DARKGREY": "#5C5C5C", "YELLOW": "#ebeb21", "MAGENTA": "#FF00FF", "CYAN": "#00FFFF", "LIGHT_GREY": "#A6A6A6"}
|
||||
|
||||
# Required to automatically set Page Numbers
|
||||
class PageTemplateWithCount(PageTemplate):
|
||||
def __init__(self, id, frames, **kw):
|
||||
PageTemplate.__init__(self, id, frames, **kw)
|
||||
|
||||
def beforeDrawPage(self, canvas, doc):
|
||||
page_num = canvas.getPageNumber()
|
||||
canvas.drawRightString(10.5*cm, 1*cm, str(page_num))
|
||||
|
||||
# Required to automatically set the Table of Contents
|
||||
class MyDocTemplate(BaseDocTemplate):
|
||||
def __init__(self, filename, **kw):
|
||||
self.allowSplitting = 0
|
||||
BaseDocTemplate.__init__(self, filename, **kw)
|
||||
template = PageTemplateWithCount("normal", [Frame(2.5*cm, 2.5*cm, 15*cm, 25*cm, id='F1')])
|
||||
self.addPageTemplates(template)
|
||||
|
||||
def afterFlowable(self, flowable):
|
||||
if flowable.__class__.__name__ == "Paragraph":
|
||||
text = flowable.getPlainText()
|
||||
style = flowable.style.name
|
||||
if style == "Heading1":
|
||||
self.notify("TOCEntry", (0, text, self.page))
|
||||
if style == "Heading2":
|
||||
self.notify("TOCEntry", (1, text, self.page))
|
||||
if style == "Heading3":
|
||||
self.notify("TOCEntry", (2, text, self.page))
|
||||
|
||||
|
||||
# Poor take at dynamicly generating styles depending on depth(?)
|
||||
def get_level_styles(level):
|
||||
global styles
|
||||
indent_value = 10 * (level - 1);
|
||||
# Overriding some default stylings
|
||||
level_styles = {
|
||||
"title": ParagraphStyle(
|
||||
**dict(styles[f"Heading{level}"].__dict__,
|
||||
**{ "leftIndent": indent_value })),
|
||||
"text": ParagraphStyle(
|
||||
**dict(styles["Code"].__dict__,
|
||||
**{ "backColor": "#F0F0F0",
|
||||
"borderPadding": 5, "borderWidth": 1,
|
||||
"borderColor": "black", "borderRadius": 5,
|
||||
"leftIndent": 5 + indent_value})),
|
||||
"info": ParagraphStyle(
|
||||
**dict(styles["Italic"].__dict__,
|
||||
**{ "leftIndent": indent_value })),
|
||||
}
|
||||
return level_styles
|
||||
|
||||
def get_colors_by_text(colors):
|
||||
new_colors = {}
|
||||
for (color, words) in colors.items():
|
||||
for word in words:
|
||||
new_colors[html.escape(word)] = color
|
||||
return new_colors
|
||||
|
||||
def build_main_section(section, title, level=1):
|
||||
styles = get_level_styles(level)
|
||||
has_links = "infos" in section.keys() and len(section["infos"]) > 0
|
||||
has_lines = "lines" in section.keys() and len(section["lines"]) > 1
|
||||
has_children = "sections" in section.keys() and len(section["sections"].keys()) > 0
|
||||
|
||||
# Only display data for Sections with results
|
||||
show_section = has_lines or has_children
|
||||
|
||||
elements = []
|
||||
|
||||
if show_section:
|
||||
elements.append(Paragraph(title, style=styles["title"]))
|
||||
|
||||
# Print info if any
|
||||
if show_section and has_links:
|
||||
for info in section["infos"]:
|
||||
words = info.split()
|
||||
# Join all lines and encode any links that might be present.
|
||||
words = map(lambda word: f'<a href="{word}" color="blue">{word}</a>' if "http" in word else word, words)
|
||||
words = " ".join(words)
|
||||
elements.append(Paragraph(words, style=styles["info"] ))
|
||||
|
||||
# Print lines if any
|
||||
if "lines" in section.keys() and len(section["lines"]) > 1:
|
||||
colors_by_line = list(map(lambda x: x["colors"], section["lines"]))
|
||||
lines = list(map(lambda x: html.escape(x["clean_text"]), section["lines"]))
|
||||
for (idx, line) in enumerate(lines):
|
||||
colors = colors_by_line[idx]
|
||||
colored_text = get_colors_by_text(colors)
|
||||
colored_line = line
|
||||
for (text, color) in colored_text.items():
|
||||
if color == "REDYELLOW":
|
||||
colored_line = colored_line.replace(text, f'<font color="{text_colors[color]}"><b>{text}</b></font>')
|
||||
else:
|
||||
colored_line = colored_line.replace(text, f'<font color="{text_colors[color]}">{text}</font>')
|
||||
lines[idx] = colored_line
|
||||
elements.append(Spacer(0, 10))
|
||||
line = "<br/>".join(lines)
|
||||
|
||||
# If it's a top level entry remove the line break caused by an empty "clean_text"
|
||||
if level == 1: line = line[5:]
|
||||
elements.append(Paragraph(line, style=styles["text"]))
|
||||
|
||||
|
||||
# Print child sections
|
||||
if has_children:
|
||||
for child_title in section["sections"].keys():
|
||||
element_list = build_main_section(section["sections"][child_title], child_title, level + 1)
|
||||
elements.extend(element_list)
|
||||
|
||||
# Add spacing at the end of section. The deeper the level the smaller the spacing.
|
||||
if show_section:
|
||||
elements.append(Spacer(1, 40 - (10 * level)))
|
||||
|
||||
return elements
|
||||
|
||||
|
||||
def main():
|
||||
with open(JSON_PATH) as file:
|
||||
# Read and parse JSON file
|
||||
data = json.loads(file.read())
|
||||
|
||||
# Default pdf values
|
||||
doc = MyDocTemplate(PDF_PATH)
|
||||
toc = TableOfContents()
|
||||
toc.levelStyles = [
|
||||
ParagraphStyle(name = "Heading1", fontSize = 14, leading=16),
|
||||
ParagraphStyle(name = "Heading2", fontSize = 12, leading=14, leftIndent = 10),
|
||||
ParagraphStyle(name = "Heading3", fontSize = 10, leading=12, leftIndent = 20),
|
||||
]
|
||||
|
||||
elements = [Paragraph("PEAS Report", style=styles["Title"]), Spacer(0, 30), toc, PageBreak()]
|
||||
|
||||
# Iterate over all top level sections and build their elements.
|
||||
for title in data.keys():
|
||||
element_list = build_main_section(data[title], title)
|
||||
elements.extend(element_list)
|
||||
|
||||
doc.multiBuild(elements)
|
||||
|
||||
# Start execution
|
||||
if __name__ == "__main__":
|
||||
try:
|
||||
JSON_PATH = sys.argv[1]
|
||||
PDF_PATH = sys.argv[2]
|
||||
except IndexError as err:
|
||||
print("Error: Please pass the peas.json file and the path to save the pdf\njson2pdf.py <json_file> <pdf_file.pdf>")
|
||||
sys.exit(1)
|
||||
|
||||
main()
|
||||
@@ -7,7 +7,7 @@ Check the **Local Windows Privilege Escalation checklist** from **[book.hacktric
|
||||
Check more **information about how to exploit** found misconfigurations in **[book.hacktricks.xyz](https://book.hacktricks.xyz/windows/windows-local-privilege-escalation)**
|
||||
|
||||
## Quick Start
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/latest)**.
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)**.
|
||||
|
||||
## WinPEAS .exe and .bat
|
||||
- [Link to WinPEAS .bat project](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS/winPEASbat)
|
||||
@@ -26,4 +26,8 @@ Are you a PEASS fan? Get now our merch at **[PEASS Shop](https://teespring.com/s
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
|
||||
@@ -137,5 +137,8 @@ This is the kind of outpuf that you have to look for when usnig the winPEAS.bat
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
|
||||
@@ -237,7 +237,7 @@ CALL :T_Progress 2
|
||||
:RemodeDeskCredMgr
|
||||
CALL :ColorLine " %E%33m[+]%E%97m Remote Desktop Credentials Manager"
|
||||
ECHO. [?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#remote-desktop-credential-manager
|
||||
IF exist "%LOCALAPPDATA%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings" ECHO.Found: RDCMan.settings in %AppLocal%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings, check for credentials in .rdg files
|
||||
IF exist "%AppLocal%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings" ECHO.Found: RDCMan.settings in %AppLocal%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings, check for credentials in .rdg files
|
||||
ECHO.
|
||||
CALL :T_Progress 1
|
||||
|
||||
|
||||
@@ -13,16 +13,14 @@ Check also the **Local Windows Privilege Escalation checklist** from **[book.hac
|
||||
**.Net >= 4.5.2 is required**
|
||||
|
||||
Precompiled binaries:
|
||||
- Download the **[latest obfuscated and not obfuscated versions from here](https://github.com/carlospolop/PEASS-ng/releases/latest)** or **compile it yourself** (read instructions for compilation).
|
||||
- Download the **[latest obfuscated and not obfuscated versions from here](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)** or **compile it yourself** (read instructions for compilation).
|
||||
|
||||
```bash
|
||||
# Get latest release
|
||||
$url = "https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe"
|
||||
|
||||
#One liner to download and execute winPEASany from memory in a PS shell
|
||||
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "$url" -UseBasicParsing | Select-Object -ExpandProperty Content)); [winPEAS.Program]::Main("")
|
||||
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/winPEASany_ofs.exe" -UseBasicParsing | Select-Object -ExpandProperty Content)); [winPEAS.Program]::Main("")
|
||||
|
||||
#Before cmd in 3 lines
|
||||
$url = "https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/winPEASany_ofs.exe"
|
||||
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "$url" -UseBasicParsing | Select-Object -ExpandProperty Content));
|
||||
[winPEAS.Program]::Main("") #Put inside the quotes the winpeas parameters you want to use
|
||||
|
||||
@@ -105,13 +103,9 @@ REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1
|
||||
|
||||
Below you have some indications about what does each color means exacty, but keep in mind that **Red** is for something interesting (from a pentester perspective) and **Green** is something well configured (from a defender perspective).
|
||||
|
||||

|
||||
|
||||
## Instructions to compile you own obfuscated version
|
||||
|
||||
<details>
|
||||
<summary>Details</summary>
|
||||
|
||||
In order to compile an **ofuscated version** of Winpeas and bypass some AVs you need to ** install dotfuscator ** in *VisualStudio*.
|
||||
|
||||
To install it *open VisualStudio --> Go to Search (CTRL+Q) --> Write "dotfuscator"* and just follow the instructions to install it.
|
||||
@@ -129,9 +123,10 @@ Once you have installed and activated it you need to:
|
||||
|
||||
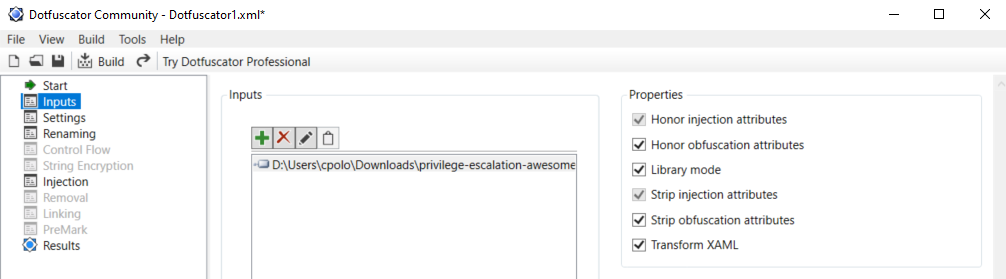
|
||||
|
||||
**IMPORTANT**: Note that Defender will higly probable delete the winpeas iintial unobfuscated version, so you need to set as expections the origin folder of Winpeas and the folder were the obfuscated version will be saved:
|
||||

|
||||
</details>
|
||||
|
||||
## Colors
|
||||
|
||||

|
||||
|
||||
## Checks
|
||||
|
||||
@@ -284,5 +279,8 @@ If you find any issue, please report it using **[github issues](https://github.c
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>, makikvues (makikvues2[at]gmail[dot].com)
|
||||
|
||||
@@ -42,7 +42,7 @@ namespace winPEAS.Checks
|
||||
private static readonly HashSet<string> _systemCheckSelectedKeysHashSet = new HashSet<string>();
|
||||
|
||||
// github url for Linpeas.sh
|
||||
public static string LinpeasUrl = "https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh";
|
||||
public static string LinpeasUrl = "https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh";
|
||||
|
||||
public const string DefaultLogFile = "out.txt";
|
||||
|
||||
@@ -80,7 +80,7 @@ namespace winPEAS.Checks
|
||||
new SystemCheck("windowscreds", new WindowsCreds()),
|
||||
new SystemCheck("browserinfo", new BrowserInfo()),
|
||||
new SystemCheck("filesinfo", new FilesInfo()),
|
||||
new SystemCheck("fileanalysis", new FileAnalysis())
|
||||
new SystemCheck("fileAnalysis", new FileAnalysis())
|
||||
};
|
||||
|
||||
var systemCheckAllKeys = new HashSet<string>(_systemChecks.Select(i => i.Key));
|
||||
|
||||
@@ -62,7 +62,7 @@ namespace winPEAS.Checks
|
||||
return files;
|
||||
}
|
||||
|
||||
private static bool[] Search(List<CustomFileInfo> files, string fileName, FileSettings fileSettings, ref int resultsCount, string searchName, bool somethingFound)
|
||||
private static bool Search(List<CustomFileInfo> files, string fileName, FileSettings fileSettings, ref int resultsCount)
|
||||
{
|
||||
bool isRegexSearch = fileName.Contains("*");
|
||||
string pattern = string.Empty;
|
||||
@@ -86,18 +86,13 @@ namespace winPEAS.Checks
|
||||
|
||||
if (isFileFound)
|
||||
{
|
||||
if (!somethingFound) {
|
||||
Beaprint.MainPrint($"Found {searchName} Files");
|
||||
somethingFound = true;
|
||||
}
|
||||
|
||||
// there are no inner sections
|
||||
if (fileSettings.files == null)
|
||||
{
|
||||
var isProcessed = ProcessResult(file, fileSettings, ref resultsCount);
|
||||
if (!isProcessed)
|
||||
{
|
||||
return new bool[] { true, somethingFound };
|
||||
return true;
|
||||
}
|
||||
}
|
||||
// there are inner sections
|
||||
@@ -114,7 +109,7 @@ namespace winPEAS.Checks
|
||||
var isProcessed = ProcessResult(innerFile, innerFileToSearch.value, ref resultsCount);
|
||||
if (!isProcessed)
|
||||
{
|
||||
return new bool[] { true, somethingFound };
|
||||
return true;
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -122,7 +117,7 @@ namespace winPEAS.Checks
|
||||
}
|
||||
}
|
||||
|
||||
return new bool[] { false, somethingFound };
|
||||
return false;
|
||||
}
|
||||
|
||||
private static void PrintYAMLSearchFiles()
|
||||
@@ -138,17 +133,15 @@ namespace winPEAS.Checks
|
||||
|
||||
foreach (var searchItem in searchItems)
|
||||
{
|
||||
if (searchItem.name != "Wifi Connections")
|
||||
continue;
|
||||
var searchName = searchItem.name;
|
||||
var value = searchItem.value;
|
||||
var searchConfig = value.config;
|
||||
bool somethingFound = false;
|
||||
|
||||
CheckRunner.Run(() =>
|
||||
{
|
||||
Beaprint.MainPrint($"Analyzing {searchName} Files (limit {ListFileLimit})");
|
||||
|
||||
int resultsCount = 0;
|
||||
bool[] results;
|
||||
bool isSearchFinished = false;
|
||||
|
||||
foreach (var file in value.files)
|
||||
@@ -157,10 +150,7 @@ namespace winPEAS.Checks
|
||||
var fileSettings = file.value;
|
||||
var itemsToSearch = fileSettings.type == "f" ? files : folders;
|
||||
|
||||
results = Search(itemsToSearch, fileName, fileSettings, ref resultsCount, searchName, somethingFound);
|
||||
|
||||
isSearchFinished = results[0];
|
||||
somethingFound = results[1];
|
||||
isSearchFinished = Search(itemsToSearch, fileName, fileSettings, ref resultsCount);
|
||||
|
||||
if (isSearchFinished)
|
||||
{
|
||||
@@ -203,21 +193,17 @@ namespace winPEAS.Checks
|
||||
|
||||
if (fileSettings.type == "f")
|
||||
{
|
||||
var colors = new Dictionary<string, string>();
|
||||
colors.Add(fileInfo.Filename, Beaprint.ansi_color_bad);
|
||||
Beaprint.AnsiPrint($"File: {fileInfo.FullPath}", colors);
|
||||
|
||||
if (!(bool)fileSettings.just_list_file)
|
||||
if ((bool)fileSettings.just_list_file)
|
||||
{
|
||||
Beaprint.BadPrint($" {fileInfo.FullPath}");
|
||||
}
|
||||
else
|
||||
{
|
||||
GrepResult(fileInfo, fileSettings);
|
||||
}
|
||||
}
|
||||
else if (fileSettings.type == "d")
|
||||
{
|
||||
var colors = new Dictionary<string, string>();
|
||||
colors.Add(fileInfo.Filename, Beaprint.ansi_color_bad);
|
||||
Beaprint.AnsiPrint($"Folder: {fileInfo.FullPath}", colors);
|
||||
|
||||
// just list the directory
|
||||
if ((bool)fileSettings.just_list_file)
|
||||
{
|
||||
@@ -239,6 +225,8 @@ namespace winPEAS.Checks
|
||||
|
||||
private static void GrepResult(CustomFileInfo fileInfo, FileSettings fileSettings)
|
||||
{
|
||||
Beaprint.NoColorPrint($" '{fileInfo.FullPath}' - content:");
|
||||
|
||||
var fileContent = File.ReadLines(fileInfo.FullPath);
|
||||
var colors = new Dictionary<string, string>();
|
||||
|
||||
@@ -284,7 +272,6 @@ namespace winPEAS.Checks
|
||||
|
||||
Beaprint.AnsiPrint(content, colors);
|
||||
|
||||
if (content.Length > 0)
|
||||
Console.WriteLine();
|
||||
}
|
||||
|
||||
@@ -294,16 +281,7 @@ namespace winPEAS.Checks
|
||||
// '-i -a -o "description.*" | sort | uniq'
|
||||
// - remove everything except from "description.*"
|
||||
|
||||
Regex regex;
|
||||
if (lineGrep.Contains("-i"))
|
||||
{
|
||||
regex = new Regex("\"([^\"]+)\"", RegexOptions.IgnoreCase);
|
||||
}
|
||||
else
|
||||
{
|
||||
regex = new Regex("\"([^\"]+)\"");
|
||||
}
|
||||
|
||||
Regex regex = new Regex("\"([^\"]+)\"");
|
||||
Match match = regex.Match(lineGrep);
|
||||
|
||||
if (match.Success)
|
||||
|
||||
@@ -44,31 +44,32 @@ namespace winPEAS.Helpers
|
||||
public static void PrintBanner()
|
||||
{
|
||||
Console.WriteLine(BLUE + string.Format(@"
|
||||
{0}((((((((((((((((((((((((((((((((
|
||||
{0}(((((((((((((((((((((((((((((((((((((((((((
|
||||
{0}(((((((((((((({2}**********/{1}##########{0}.((((((((((((
|
||||
{0}(((((((((((/{2}********************/{1}#######{0}.((((((((((
|
||||
{0}(((((((.{2}******************{3}/@@@@@/{0}{2}****{1}######{0}.(((((((((
|
||||
{0}(((((.{2}********************{3}@@@@@@@@@@/{0}{2}***,{1}####{0}.(((((((((
|
||||
{0}((((.{2}********************{3}/@@@@@%@@@@{0}{2}/********{1}##{0}(((((((((
|
||||
{0}.(({1}############{2}*********{3}/%@@@@@@@@@{0}{2}/************{0}.(((((((
|
||||
{0}.({1}##################(/{2}******{3}/@@@@@{0}{2}/***************{0}.(((((
|
||||
{0}.({1}#########################(/{2}**********************{0}.((((
|
||||
{0}.({1}##############################(/{2}*****************{0}.((((
|
||||
{0}.({1}###################################(/{2}************{0}.((((
|
||||
{0}.({1}#######################################({2}*********{0}.((((
|
||||
{0}.({1}#######(,.***.,(###################(..***.{2}*******{0}.((((
|
||||
{0}.({1}#######*(#####((##################((######/({2}*****{0}.((((
|
||||
{0}.({1}###################(/***********(##############({0}).((((
|
||||
{0}.(({1}#####################/*******(################{0})((((((
|
||||
{0}.((({1}############################################{0}).(((((
|
||||
{0}..((({1}##########################################{0}).((((((
|
||||
{0}....(({1}########################################{0}).((((((
|
||||
{0}......(({1}####################################{0}).(((((((
|
||||
{0}((((((((({1}#################################{0}).((((((((
|
||||
{0}(((((((((/{1}##########################{0}).((((((((
|
||||
{0}((((((((((((((((((((((((((((((((((((((
|
||||
{0}((((((((((((((((((((((((((((((", LGREEN, GREEN, BLUE, NOCOLOR) + NOCOLOR);
|
||||
{0}*((,.,/((((((((((((((((((((/, */
|
||||
{0},/*,..*((((((((((((((((((((((((((((((((((,
|
||||
{0},*/((((((((((((((((((/, .*//((//**, .*(((((((*
|
||||
{0}(((((((((((((((({2}**********/{1}########## {0}.(* ,(((((((
|
||||
{0}(((((((((((/{2}********************/{1}####### {0}.(. (((((((
|
||||
{0}((((((..{2}******************{3}/@@@@@/{2}***/{1}###### {0}./(((((((
|
||||
{0},,....{2}********************{3}@@@@@@@@@@{2}(***,{1}#### {0}.//((((((
|
||||
{0}, ,..{2}********************{3}/@@@@@%@@@@{2}/********{1}##{0}((/ /((((
|
||||
{0}..(({1}###########{2}*********{3}/%@@@@@@@@@{2}/************{0},,..((((
|
||||
{0}.({1}##################(/{2}******{3}/@@@@@{2}/***************{0}.. /((
|
||||
{0}.({1}#########################(/{2}**********************{0}..*((
|
||||
{0}.({1}##############################(/{2}*****************{0}.,(((
|
||||
{0}.({1}###################################(/{2}************{0}..(((
|
||||
{0}.({1}#######################################({2}*********{0}..(((
|
||||
{0}.({1}#######(,.***.,(###################(..***.{2}*******{0}..(((
|
||||
{0}.({1}#######*(#####((##################((######/({2}*****{0}..(((
|
||||
{0}.({1}###################(/***********(##############({0}...(((
|
||||
{0}.(({1}#####################/*******(################{0}.((((((
|
||||
{0}.((({1}############################################{0}(..((((
|
||||
{0}..((({1}##########################################{0}(..(((((
|
||||
{0}....(({1}########################################{0}( .(((((
|
||||
{0}......(({1}####################################{0}( .((((((
|
||||
{0}((((((((({1}#################################{0}(../((((((
|
||||
{0}(((((((((/{1}##########################{0}(/..((((((
|
||||
{0}(((((((((/,. ,*//////*,. ./(((((((((((((((.
|
||||
{0}(((((((((((((((((((((((((((((/", LGREEN, GREEN, BLUE, NOCOLOR) + NOCOLOR);
|
||||
|
||||
Console.WriteLine();
|
||||
Console.WriteLine(LYELLOW + "ADVISORY: " + BLUE + Advisory);
|
||||
@@ -135,8 +136,7 @@ namespace winPEAS.Helpers
|
||||
Console.WriteLine(LBLUE + " networkinfo" + GRAY + " Search network information" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " windowscreds" + GRAY + " Search windows credentials" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " browserinfo" + GRAY + " Search browser information" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " filesinfo" + GRAY + " Search generic files that can contains credentials" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " fileanalysis" + GRAY + " Search specific files that can contains credentials" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " filesinfo" + GRAY + " Search files that can contains credentials" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " eventsinfo" + GRAY + " Display interesting events information" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " wait" + GRAY + " Wait for user input between checks" + NOCOLOR);
|
||||
Console.WriteLine(LBLUE + " debug" + GRAY + " Display debugging information - memory usage, method execution time" + NOCOLOR);
|
||||
|
||||
@@ -25,7 +25,6 @@ namespace winPEAS.Helpers.Search
|
||||
ConcurrentBag<CustomFileInfo> files = new ConcurrentBag<CustomFileInfo>();
|
||||
IEnumerable<DirectoryInfo> startDirs = GetStartDirectories(folder, files, pattern, isFoldersIncluded);
|
||||
IList<DirectoryInfo> startDirsExcluded = new List<DirectoryInfo>();
|
||||
IList<string> known_dirs = new List<string>();
|
||||
|
||||
if (excludedDirs != null)
|
||||
{
|
||||
@@ -52,17 +51,8 @@ namespace winPEAS.Helpers.Search
|
||||
Parallel.ForEach(GetStartDirectories(d.FullName, files, pattern, isFoldersIncluded), (dir) =>
|
||||
{
|
||||
GetFiles(dir.FullName, pattern).ForEach(
|
||||
(f) => {
|
||||
CustomFileInfo file_info = new CustomFileInfo(f.Name, f.Extension, f.FullName, false);
|
||||
files.Add(file_info);
|
||||
|
||||
CustomFileInfo file_dir = new CustomFileInfo(f.Directory.Name, "", f.Directory.FullName, true);
|
||||
if (!known_dirs.Contains(file_dir.FullPath))
|
||||
{
|
||||
known_dirs.Add(file_dir.FullPath);
|
||||
files.Add(file_dir);
|
||||
}
|
||||
}
|
||||
(f) =>
|
||||
files.Add(new CustomFileInfo(f.Name, f.Extension, f.FullName, false))
|
||||
);
|
||||
});
|
||||
});
|
||||
@@ -185,28 +175,29 @@ namespace winPEAS.Helpers.Search
|
||||
|
||||
// c:\users\current_user
|
||||
string rootCurrentUserSearchPath = Environment.GetEnvironmentVariable("USERPROFILE");
|
||||
SearchHelper.RootDirCurrentUser = SearchHelper.GetFilesFast(rootCurrentUserSearchPath, GlobalPattern, isFoldersIncluded: true);
|
||||
SearchHelper.RootDirCurrentUser = SearchHelper.GetFilesFast(rootCurrentUserSearchPath, GlobalPattern);
|
||||
|
||||
// c:\Program Files\
|
||||
string rootProgramFiles = $"{SystemDrive}\\Program Files\\";
|
||||
SearchHelper.ProgramFiles = SearchHelper.GetFilesFast(rootProgramFiles, GlobalPattern, isFoldersIncluded: true);
|
||||
SearchHelper.ProgramFiles = SearchHelper.GetFilesFast(rootProgramFiles, GlobalPattern);
|
||||
|
||||
// c:\Program Files (x86)\
|
||||
string rootProgramFilesX86 = $"{SystemDrive}\\Program Files (x86)\\";
|
||||
SearchHelper.ProgramFilesX86 = SearchHelper.GetFilesFast(rootProgramFilesX86, GlobalPattern, isFoldersIncluded: true);
|
||||
SearchHelper.ProgramFilesX86 = SearchHelper.GetFilesFast(rootProgramFilesX86, GlobalPattern);
|
||||
|
||||
// c:\Documents and Settings\
|
||||
string documentsAndSettings = $"{SystemDrive}\\Documents and Settings\\";
|
||||
SearchHelper.DocumentsAndSettings = SearchHelper.GetFilesFast(documentsAndSettings, GlobalPattern, isFoldersIncluded: true);
|
||||
SearchHelper.DocumentsAndSettings = SearchHelper.GetFilesFast(documentsAndSettings, GlobalPattern);
|
||||
|
||||
// c:\ProgramData\Microsoft\Group Policy\History
|
||||
string groupPolicyHistory = $"{SystemDrive}\\ProgramData\\Microsoft\\Group Policy\\History";
|
||||
SearchHelper.GroupPolicyHistory = SearchHelper.GetFilesFast(groupPolicyHistory, GlobalPattern, isFoldersIncluded: true);
|
||||
SearchHelper.GroupPolicyHistory = SearchHelper.GetFilesFast(groupPolicyHistory, GlobalPattern);
|
||||
|
||||
// c:\Documents and Settings\All Users\Application Data\\Microsoft\\Group Policy\\History
|
||||
string groupPolicyHistoryLegacy = $"{documentsAndSettings}\\All Users\\Application Data\\Microsoft\\Group Policy\\History";
|
||||
//SearchHelper.GroupPolicyHistoryLegacy = SearchHelper.GetFilesFast(groupPolicyHistoryLegacy, globalPattern);
|
||||
var groupPolicyHistoryLegacyFiles = SearchHelper.GetFilesFast(groupPolicyHistoryLegacy, GlobalPattern, isFoldersIncluded: true);
|
||||
var groupPolicyHistoryLegacyFiles = SearchHelper.GetFilesFast(groupPolicyHistoryLegacy, GlobalPattern);
|
||||
|
||||
SearchHelper.GroupPolicyHistory.AddRange(groupPolicyHistoryLegacyFiles);
|
||||
}
|
||||
|
||||
|
||||
@@ -217,17 +217,13 @@ namespace winPEAS.Info.ServicesInfo
|
||||
{
|
||||
if (SIDs.ContainsKey(ace.SecurityIdentifier.ToString()))
|
||||
{
|
||||
string aceType = ace.AceType.ToString();
|
||||
if (!(aceType.Contains("Denied")))
|
||||
{ //https://docs.microsoft.com/en-us/dotnet/api/system.security.accesscontrol.commonace?view=net-6.0
|
||||
int serviceRights = ace.AccessMask;
|
||||
string current_perm_str = PermissionsHelper.PermInt2Str(serviceRights, PermissionType.WRITEABLE_OR_EQUIVALENT_SVC);
|
||||
|
||||
string current_perm_str = PermissionsHelper.PermInt2Str(serviceRights, PermissionType.WRITEABLE_OR_EQUIVALENT_SVC);
|
||||
if (!string.IsNullOrEmpty(current_perm_str) && !permissions.Contains(current_perm_str))
|
||||
permissions.Add(current_perm_str);
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
if (permissions.Count > 0)
|
||||
{
|
||||
|
||||
@@ -5,12 +5,12 @@ using System.Runtime.InteropServices;
|
||||
// General Information about an assembly is controlled through the following
|
||||
// set of attributes. Change these attribute values to modify the information
|
||||
// associated with an assembly.
|
||||
[assembly: AssemblyTitle("")]
|
||||
[assembly: AssemblyTitle("asdas2dasd")]
|
||||
[assembly: AssemblyDescription("")]
|
||||
[assembly: AssemblyConfiguration("")]
|
||||
[assembly: AssemblyCompany("")]
|
||||
[assembly: AssemblyProduct("")]
|
||||
[assembly: AssemblyCopyright("")]
|
||||
[assembly: AssemblyProduct("asdas2dasd")]
|
||||
[assembly: AssemblyCopyright("Copyright © 2019")]
|
||||
[assembly: AssemblyTrademark("")]
|
||||
[assembly: AssemblyCulture("")]
|
||||
|
||||
|
||||
@@ -14,21 +14,6 @@
|
||||
<NuGetPackageImportStamp>
|
||||
</NuGetPackageImportStamp>
|
||||
<TargetFrameworkProfile />
|
||||
<PublishUrl>publish\</PublishUrl>
|
||||
<Install>true</Install>
|
||||
<InstallFrom>Disk</InstallFrom>
|
||||
<UpdateEnabled>false</UpdateEnabled>
|
||||
<UpdateMode>Foreground</UpdateMode>
|
||||
<UpdateInterval>7</UpdateInterval>
|
||||
<UpdateIntervalUnits>Days</UpdateIntervalUnits>
|
||||
<UpdatePeriodically>false</UpdatePeriodically>
|
||||
<UpdateRequired>false</UpdateRequired>
|
||||
<MapFileExtensions>true</MapFileExtensions>
|
||||
<ApplicationRevision>0</ApplicationRevision>
|
||||
<ApplicationVersion>1.0.0.%2a</ApplicationVersion>
|
||||
<IsWebBootstrapper>false</IsWebBootstrapper>
|
||||
<UseApplicationTrust>false</UseApplicationTrust>
|
||||
<BootstrapperEnabled>true</BootstrapperEnabled>
|
||||
</PropertyGroup>
|
||||
<PropertyGroup Condition=" '$(Configuration)|$(Platform)' == 'Debug|AnyCPU' ">
|
||||
<PlatformTarget>AnyCPU</PlatformTarget>
|
||||
@@ -110,8 +95,7 @@
|
||||
<AllowUnsafeBlocks>true</AllowUnsafeBlocks>
|
||||
</PropertyGroup>
|
||||
<PropertyGroup>
|
||||
<StartupObject>
|
||||
</StartupObject>
|
||||
<StartupObject>winPEAS.Program</StartupObject>
|
||||
</PropertyGroup>
|
||||
<ItemGroup>
|
||||
<Reference Include="System" />
|
||||
@@ -708,17 +692,5 @@
|
||||
<EmbeddedResource Include="Properties\Resources.ru.resx" />
|
||||
<EmbeddedResource Include="Properties\Resources.zh-CN.resx" />
|
||||
</ItemGroup>
|
||||
<ItemGroup>
|
||||
<BootstrapperPackage Include=".NETFramework,Version=v4.5.2">
|
||||
<Visible>False</Visible>
|
||||
<ProductName>Microsoft .NET Framework 4.5.2 %28x86 and x64%29</ProductName>
|
||||
<Install>true</Install>
|
||||
</BootstrapperPackage>
|
||||
<BootstrapperPackage Include="Microsoft.Net.Framework.3.5.SP1">
|
||||
<Visible>False</Visible>
|
||||
<ProductName>.NET Framework 3.5 SP1</ProductName>
|
||||
<Install>false</Install>
|
||||
</BootstrapperPackage>
|
||||
</ItemGroup>
|
||||
<Import Project="$(MSBuildToolsPath)\Microsoft.CSharp.targets" />
|
||||
</Project>
|
||||
@@ -5,7 +5,7 @@
|
||||
</StartArguments>
|
||||
</PropertyGroup>
|
||||
<PropertyGroup Condition="'$(Configuration)|$(Platform)' == 'Debug|AnyCPU'">
|
||||
<StartArguments>fileAnalysis</StartArguments>
|
||||
<StartArguments>servicesinfo</StartArguments>
|
||||
</PropertyGroup>
|
||||
<PropertyGroup Condition="'$(Configuration)|$(Platform)' == 'Debug|x64'">
|
||||
<StartArguments>debug</StartArguments>
|
||||
@@ -21,14 +21,4 @@
|
||||
<StartArguments>
|
||||
</StartArguments>
|
||||
</PropertyGroup>
|
||||
<PropertyGroup>
|
||||
<PublishUrlHistory>publish\</PublishUrlHistory>
|
||||
<InstallUrlHistory />
|
||||
<SupportUrlHistory />
|
||||
<UpdateUrlHistory />
|
||||
<BootstrapperUrlHistory />
|
||||
<ErrorReportUrlHistory />
|
||||
<FallbackCulture>en-US</FallbackCulture>
|
||||
<VerifyUploadedFiles>false</VerifyUploadedFiles>
|
||||
</PropertyGroup>
|
||||
</Project>
|
||||
Reference in New Issue
Block a user