mirror of
https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite.git
synced 2025-12-08 10:01:29 +00:00
Compare commits
49 Commits
refs/pull/
...
20220206
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
0a4df51b06 | ||
|
|
7c275d50bc | ||
|
|
d57877077f | ||
|
|
e3238acc2b | ||
|
|
9f4045c697 | ||
|
|
52c2a1e11b | ||
|
|
f3495c48e9 | ||
|
|
db89a779ad | ||
|
|
77cc22a657 | ||
|
|
cc1e2b4d3c | ||
|
|
6ab4e6798f | ||
|
|
568f8cafa9 | ||
|
|
159a2d8643 | ||
|
|
d02e91a451 | ||
|
|
db1ad797d9 | ||
|
|
b9c8df71c5 | ||
|
|
c53425d4bc | ||
|
|
3723327e21 | ||
|
|
8f12ad9d67 | ||
|
|
3faac92a01 | ||
|
|
cb81dbf02f | ||
|
|
8c67152e17 | ||
|
|
9c31073279 | ||
|
|
f7eb8ce150 | ||
|
|
c8b28b1fb6 | ||
|
|
d15e3dffd5 | ||
|
|
07a2db8553 | ||
|
|
e81069ea0a | ||
|
|
21d3b3f349 | ||
|
|
aa94d9d432 | ||
|
|
5b8f3968e8 | ||
|
|
94e10c0ae7 | ||
|
|
5d0d7c7997 | ||
|
|
600dcc4549 | ||
|
|
a65d251242 | ||
|
|
0a605cdd32 | ||
|
|
5d763a1c8b | ||
|
|
23d8f264be | ||
|
|
1c02bbc9d6 | ||
|
|
70e85e14dd | ||
|
|
bfd0cf62a7 | ||
|
|
be85f7e0e0 | ||
|
|
6a0b3f7cb1 | ||
|
|
3ecb6090c1 | ||
|
|
86a2a24a1c | ||
|
|
605b718fba | ||
|
|
3ffaf1f1bb | ||
|
|
f27c56bd3c | ||
|
|
2e5e368109 |
57
.github/workflows/CI-master_tests.yml
vendored
57
.github/workflows/CI-master_tests.yml
vendored
@@ -5,6 +5,9 @@ on:
|
||||
branches:
|
||||
- master
|
||||
|
||||
schedule:
|
||||
- cron: "5 4 * * SUN"
|
||||
|
||||
workflow_dispatch:
|
||||
|
||||
jobs:
|
||||
@@ -84,9 +87,9 @@ jobs:
|
||||
# copy the files
|
||||
- name: Copy Dotfuscator generated files
|
||||
run: |
|
||||
cp $env:DotFuscatorGeneratedPath\x64\winPEASx64.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\x86\winPEASx86.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\any\winPEASany.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\x64\winPEASx64.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64_ofs.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\x86\winPEASx86.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86_ofs.exe"
|
||||
cp $env:DotFuscatorGeneratedPath\any\winPEASany.exe "winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany_ofs.exe"
|
||||
|
||||
# Upload all the versions for the release
|
||||
- name: Upload winpeasx64
|
||||
@@ -111,19 +114,19 @@ jobs:
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: winPEASx64_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx64_ofs.exe
|
||||
|
||||
- name: Upload winpeasx86ofs
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: winPEASx86_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASx86_ofs.exe
|
||||
|
||||
- name: Upload winpeasanyofs
|
||||
uses: actions/upload-artifact@v2
|
||||
with:
|
||||
name: winPEASany_ofs.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany.exe
|
||||
path: winPEAS\winPEASexe\binaries\Obfuscated Releases\winPEASany_ofs.exe
|
||||
|
||||
- name: Upload winpeas.bat
|
||||
uses: actions/upload-artifact@v2
|
||||
@@ -196,7 +199,7 @@ jobs:
|
||||
|
||||
# Run linpeas as a test
|
||||
- name: Run linpeas
|
||||
run: linPEAS/linpeas.sh -t -e
|
||||
run: linPEAS/linpeas.sh -a -D
|
||||
|
||||
# Upload files for release
|
||||
- name: Upload linpeas.sh
|
||||
@@ -283,7 +286,7 @@ jobs:
|
||||
|
||||
# Run macpeas parts to test it
|
||||
- name: Run macpeas
|
||||
run: linPEAS/linpeas.sh -o system_information,container,procs_crons_timers_srvcs_sockets,network_information,users_information,software_information
|
||||
run: linPEAS/linpeas.sh -D -o system_information,container,procs_crons_timers_srvcs_sockets,network_information,users_information,software_information
|
||||
|
||||
|
||||
Publish_release:
|
||||
@@ -292,21 +295,6 @@ jobs:
|
||||
|
||||
steps:
|
||||
# Download files to release
|
||||
- name: Download winpeasx64
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx64.exe
|
||||
|
||||
- name: Download winpeasx86
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx86.exe
|
||||
|
||||
- name: Download winpeasany
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASany.exe
|
||||
|
||||
- name: Download winpeasx64ofs
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
@@ -322,6 +310,21 @@ jobs:
|
||||
with:
|
||||
name: winPEASany_ofs.exe
|
||||
|
||||
- name: Download winpeasx64
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx64.exe
|
||||
|
||||
- name: Download winpeasx86
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASx86.exe
|
||||
|
||||
- name: Download winpeasany
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
name: winPEASany.exe
|
||||
|
||||
- name: Download winpeas.bat
|
||||
uses: actions/download-artifact@v2
|
||||
with:
|
||||
@@ -362,6 +365,10 @@ jobs:
|
||||
with:
|
||||
name: linpeas_darwin_arm64
|
||||
|
||||
- name: Get current date
|
||||
id: date
|
||||
run: echo "::set-output name=date::$(date +'%Y%m%d')"
|
||||
|
||||
# Create the release
|
||||
- name: Create Release
|
||||
id: create_release
|
||||
@@ -369,8 +376,8 @@ jobs:
|
||||
env:
|
||||
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
||||
with:
|
||||
tag_name: ${{ github.ref }}
|
||||
release_name: Release ${{ github.ref }}
|
||||
tag_name: ${{steps.date.outputs.date}}
|
||||
release_name: Release ${{ github.ref }} ${{steps.date.outputs.date}}
|
||||
draft: false
|
||||
prerelease: false
|
||||
|
||||
|
||||
@@ -19,7 +19,7 @@ These tools search for possible **local privilege escalation paths** that you co
|
||||
- **[LinPEAS](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) - Linux local Privilege Escalation Awesome Script (.sh)**
|
||||
|
||||
## Quick Start
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)**.
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/latest)**.
|
||||
|
||||
## Let's improve PEASS together
|
||||
|
||||
@@ -34,8 +34,5 @@ Are you a PEASS fan? Get now our merch at **[PEASS Shop](https://teespring.com/s
|
||||
All the scripts/binaries of the PEAS suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own machines and/or with the owner's permission.
|
||||
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
|
||||
@@ -13,11 +13,11 @@ Check the **Local Linux Privilege Escalation checklist** from **[book.hacktricks
|
||||
Just execute `linpeas.sh` in a MacOS system and the **MacPEAS version will be automatically executed**
|
||||
|
||||
## Quick Start
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)**.
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/latest)**.
|
||||
|
||||
```bash
|
||||
# From github
|
||||
curl -L https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/linpeas.sh | sh
|
||||
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
|
||||
```
|
||||
|
||||
```bash
|
||||
@@ -42,7 +42,7 @@ less -r /dev/shm/linpeas.txt #Read with colors
|
||||
|
||||
```bash
|
||||
# Use a linpeas binary
|
||||
wget https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/linpeas_linux_amd64
|
||||
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas_linux_amd64
|
||||
chmod +x linpeas_linux_amd64
|
||||
./linpeas_linux_amd64
|
||||
```
|
||||
@@ -203,8 +203,5 @@ If you find any issue, please report it using **[github issues](https://github.c
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
@@ -21,6 +21,17 @@ else echo_not_found "sudo"
|
||||
fi
|
||||
echo ""
|
||||
|
||||
#-- SY) CVE-2021-4034
|
||||
if [ `command -v pkexec` ] && stat -c '%a' $(which pkexec) | grep -q 4755 && [ "$(stat -c '%Y' $(which pkexec))" -lt "1642035600" ]; then
|
||||
echo "Vulnerable to CVE-2021-4034" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
fi
|
||||
|
||||
#-- SY) CVE-2021-3560
|
||||
polkitVersion=$(systemctl status polkit.service | grep version | cut -d " " -f 9)
|
||||
if [[ "$(apt list --installed 2>/dev/null | grep polkit | grep -c 0.105-26)" -ge 1 || "$(yum list installed | grep polkit | grep -c 0.117-2)" ]]; then
|
||||
echo "Vulnerable to CVE-2021-3560" | sed -${E} "s,.*,${SED_RED_YELLOW},"
|
||||
fi
|
||||
|
||||
#--SY) USBCreator
|
||||
if (busctl list 2>/dev/null | grep -q com.ubuntu.USBCreator) || [ "$DEBUG" ]; then
|
||||
print_2title "USBCreator"
|
||||
@@ -122,9 +133,10 @@ if [ "$(command -v bash 2>/dev/null)" ]; then
|
||||
print_2title "Executing Linux Exploit Suggester"
|
||||
print_info "https://github.com/mzet-/linux-exploit-suggester"
|
||||
les_b64="peass{LES}"
|
||||
echo $les_b64 | base64 -d | bash
|
||||
if [ "$EXTRA_CHECKS" ]; then
|
||||
echo $les_b64 | base64 -d | bash -s -- --checksec
|
||||
echo $les_b64 | base64 -d | bash -s -- --checksec | sed "s,$(printf '\033')\\[[0-9;]*[a-zA-Z],,g" | sed -E "s,\[CVE-[0-9]+-[0-9]+\].*,${SED_RED},g"
|
||||
else
|
||||
echo $les_b64 | base64 -d | bash | sed "s,$(printf '\033')\\[[0-9;]*[a-zA-Z],,g" | grep -i "\[CVE" -A 10 | grep -Ev "^\-\-$" | sed -${E} "s,\[CVE-[0-9]+-[0-9]+\],*,${SED_RED},g"
|
||||
fi
|
||||
echo ""
|
||||
fi
|
||||
@@ -133,7 +145,7 @@ if [ "$(command -v perl 2>/dev/null)" ]; then
|
||||
print_2title "Executing Linux Exploit Suggester 2"
|
||||
print_info "https://github.com/jondonas/linux-exploit-suggester-2"
|
||||
les2_b64="peass{LES2}"
|
||||
echo $les2_b64 | base64 -d | perl
|
||||
echo $les2_b64 | base64 -d | perl | sed "s,$(printf '\033')\\[[0-9;]*[a-zA-Z],,g" | grep -i "CVE" -B 1 -A 10 | grep -Ev "^\-\-$" | sed -${E} "s,CVE-[0-9]+-[0-9]+,${SED_RED},g"
|
||||
echo ""
|
||||
fi
|
||||
|
||||
|
||||
@@ -28,7 +28,7 @@ else
|
||||
echo ""
|
||||
|
||||
#-- PCS) Binary processes permissions
|
||||
print_2title "Binary processes permissions (non 'root root' and not beloging to current user)"
|
||||
print_2title "Binary processes permissions (non 'root root' and not belonging to current user)"
|
||||
print_info "https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes"
|
||||
binW="IniTialiZZinnggg"
|
||||
ps auxwww 2>/dev/null | awk '{print $11}' | while read bpath; do
|
||||
|
||||
@@ -60,9 +60,9 @@ fi
|
||||
#-- UI) Sudo -l
|
||||
print_2title "Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d"
|
||||
print_info "https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid"
|
||||
(echo '' | sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW}," | sed "s,\!root,${SED_RED},") 2>/dev/null || echo_not_found "sudo"
|
||||
(echo '' | timeout 1 sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW}," | sed "s,\!root,${SED_RED},") 2>/dev/null || echo_not_found "sudo"
|
||||
if [ "$PASSWORD" ]; then
|
||||
(echo "$PASSWORD" | sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},") 2>/dev/null || echo_not_found "sudo"
|
||||
(echo "$PASSWORD" | timeout 1 sudo -S -l | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},") 2>/dev/null || echo_not_found "sudo"
|
||||
fi
|
||||
( grep -Iv "^$" cat /etc/sudoers | grep -v "#" | sed "s,_proxy,${SED_RED},g" | sed "s,$sudoG,${SED_GREEN},g" | sed -${E} "s,$sudoB,${SED_RED},g" | sed "s,pwfeedback,${SED_RED},g" | sed -${E} "s,$sudoVB1,${SED_RED_YELLOW}," | sed -${E} "s,$sudoVB2,${SED_RED_YELLOW},") 2>/dev/null || echo_not_found "/etc/sudoers"
|
||||
if ! [ "$IAMROOT" ] && [ -w '/etc/sudoers.d/' ]; then
|
||||
|
||||
@@ -37,7 +37,7 @@ class MetasploitModule < Msf::Post
|
||||
))
|
||||
register_options(
|
||||
[
|
||||
OptString.new('PEASS_URL', [true, 'Path to the PEASS script. Accepted: http(s):// URL or absolute local path. Linpeas: https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/linPEAS/linpeas.sh', "https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/winPEAS/winPEASexe/binaries/Obfuscated%20Releases/winPEASany.exe"]),
|
||||
OptString.new('PEASS_URL', [true, 'Path to the PEASS script. Accepted: http(s):// URL or absolute local path. Linpeas: https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh', "https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe"]),
|
||||
OptString.new('PASSWORD', [false, 'Password to encrypt and obfuscate the script (randomly generated). The length must be 32B. If no password is set, only base64 will be used.', rand(36**32).to_s(36)]),
|
||||
OptString.new('TEMP_DIR', [false, 'Path to upload the obfuscated PEASS script inside the compromised machine. By default "C:\Windows\System32\spool\drivers\color" is used in Windows and "/tmp" in Unix.', '']),
|
||||
OptString.new('PARAMETERS', [false, 'Parameters to pass to the script', nil]),
|
||||
|
||||
@@ -5,7 +5,7 @@ import re
|
||||
import json
|
||||
|
||||
# Pattern to identify main section titles
|
||||
TITLE1_PATTERN = r"════════════════════════════════════╣"
|
||||
TITLE1_PATTERN = r"══════════════╣" # The size of the first pattern varies, but at least should be that large
|
||||
TITLE2_PATTERN = r"╔══════════╣"
|
||||
TITLE3_PATTERN = r"══╣"
|
||||
INFO_PATTERN = r"╚ "
|
||||
@@ -14,15 +14,15 @@ TITLE_CHARS = ['═', '╔', '╣', '╚']
|
||||
# Patterns for colors
|
||||
## The order is important, the first string colored with a color will be the one selected (the same string cannot be colored with different colors)
|
||||
COLORS = {
|
||||
"REDYELLOW": [r"\x1b\[1;31;103m"],
|
||||
"RED": [r"\x1b\[1;31m"],
|
||||
"GREEN": [r"\x1b\[1;32m"],
|
||||
"YELLOW": [r"\x1b\[1;33m"],
|
||||
"BLUE": [r"\x1b\[1;34m"],
|
||||
"MAGENTA": [r"\x1b\[1;95m", r"\x1b\[1;35m"],
|
||||
"CYAN": [r"\x1b\[1;36m", r"\x1b\[1;96m"],
|
||||
"LIGHT_GREY": [r"\x1b\[1;37m"],
|
||||
"DARKGREY": [r"\x1b\[1;90m"],
|
||||
"REDYELLOW": ['\x1b[1;31;103m'],
|
||||
"RED": ['\x1b[1;31m'],
|
||||
"GREEN": ['\x1b[1;32m'],
|
||||
"YELLOW": ['\x1b[1;33m'],
|
||||
"BLUE": ['\x1b[1;34m'],
|
||||
"MAGENTA": ['\x1b[1;95m', '\x1b[1;35m'],
|
||||
"CYAN": ['\x1b[1;36m', '\x1b[1;96m'],
|
||||
"LIGHT_GREY": ['\x1b[1;37m'],
|
||||
"DARKGREY": ['\x1b[1;90m'],
|
||||
}
|
||||
|
||||
|
||||
@@ -52,11 +52,23 @@ def get_colors(line: str) -> dict:
|
||||
for c,regexs in COLORS.items():
|
||||
colors[c] = []
|
||||
for reg in regexs:
|
||||
for re_found in re.findall(reg+"(.+?)\x1b|$", line):
|
||||
re_found = clean_colors(re_found.strip())
|
||||
split_color = line.split(reg)
|
||||
|
||||
# Start from the index 1 as the index 0 isn't colored
|
||||
if split_color and len(split_color) > 1:
|
||||
split_color = split_color[1:]
|
||||
|
||||
# For each potential color, find the string before any possible color terminatio
|
||||
for potential_color_str in split_color:
|
||||
color_str1 = potential_color_str.split('\x1b')[0]
|
||||
color_str2 = potential_color_str.split("\[0")[0]
|
||||
color_str = color_str1 if len(color_str1) < len(color_str2) else color_str2
|
||||
|
||||
if color_str:
|
||||
color_str = clean_colors(color_str.strip())
|
||||
#Avoid having the same color for the same string
|
||||
if re_found and not any(re_found in values for values in colors.values()):
|
||||
colors[c].append(re_found)
|
||||
if color_str and not any(color_str in values for values in colors.values()):
|
||||
colors[c].append(color_str)
|
||||
|
||||
if not colors[c]:
|
||||
del colors[c]
|
||||
@@ -75,10 +87,10 @@ def clean_title(line: str) -> str:
|
||||
def clean_colors(line: str) -> str:
|
||||
"""Given a line clean the colors inside of it"""
|
||||
|
||||
for reg in re.findall(r'\x1b[^ ]+\dm', line):
|
||||
for reg in re.findall(r'\x1b\[[^a-zA-Z]+\dm', line):
|
||||
line = line.replace(reg,"")
|
||||
|
||||
line = line.replace('\x1b',"") #Sometimes that byte stays
|
||||
line = line.replace('\x1b',"").replace("[0m", "") #Sometimes that byte stays
|
||||
line = line.strip()
|
||||
return line
|
||||
|
||||
@@ -94,6 +106,9 @@ def parse_line(line: str):
|
||||
|
||||
global FINAL_JSON, C_SECTION, C_MAIN_SECTION, C_2_SECTION, C_3_SECTION
|
||||
|
||||
if "Cron jobs" in line:
|
||||
a=1
|
||||
|
||||
if is_section(line, TITLE1_PATTERN):
|
||||
title = parse_title(line)
|
||||
FINAL_JSON[title] = { "sections": {}, "lines": [], "infos": [] }
|
||||
@@ -124,8 +139,8 @@ def parse_line(line: str):
|
||||
|
||||
C_SECTION["lines"].append({
|
||||
"raw_text": line,
|
||||
"clean_text": clean_colors(line),
|
||||
"colors": get_colors(line)
|
||||
"colors": get_colors(line),
|
||||
"clean_text": clean_title(clean_colors(line))
|
||||
})
|
||||
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ Check the **Local Windows Privilege Escalation checklist** from **[book.hacktric
|
||||
Check more **information about how to exploit** found misconfigurations in **[book.hacktricks.xyz](https://book.hacktricks.xyz/windows/windows-local-privilege-escalation)**
|
||||
|
||||
## Quick Start
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)**.
|
||||
Find the **latest versions of all the scripts and binaries in [the releases page](https://github.com/carlospolop/PEASS-ng/releases/latest)**.
|
||||
|
||||
## WinPEAS .exe and .bat
|
||||
- [Link to WinPEAS .bat project](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS/winPEASbat)
|
||||
@@ -26,8 +26,4 @@ Are you a PEASS fan? Get now our merch at **[PEASS Shop](https://teespring.com/s
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
|
||||
@@ -137,8 +137,5 @@ This is the kind of outpuf that you have to look for when usnig the winPEAS.bat
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>
|
||||
|
||||
@@ -237,7 +237,7 @@ CALL :T_Progress 2
|
||||
:RemodeDeskCredMgr
|
||||
CALL :ColorLine " %E%33m[+]%E%97m Remote Desktop Credentials Manager"
|
||||
ECHO. [?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#remote-desktop-credential-manager
|
||||
IF exist "%AppLocal%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings" ECHO.Found: RDCMan.settings in %AppLocal%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings, check for credentials in .rdg files
|
||||
IF exist "%LOCALAPPDATA%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings" ECHO.Found: RDCMan.settings in %AppLocal%\Local\Microsoft\Remote Desktop Connection Manager\RDCMan.settings, check for credentials in .rdg files
|
||||
ECHO.
|
||||
CALL :T_Progress 1
|
||||
|
||||
|
||||
@@ -13,22 +13,24 @@ Check also the **Local Windows Privilege Escalation checklist** from **[book.hac
|
||||
**.Net >= 4.5.2 is required**
|
||||
|
||||
Precompiled binaries:
|
||||
- Download the **[latest obfuscated and not obfuscated versions from here](https://github.com/carlospolop/PEASS-ng/releases/tag/refs%2Fheads%2Fmaster)** or **compile it yourself** (read instructions for compilation).
|
||||
- Download the **[latest obfuscated and not obfuscated versions from here](https://github.com/carlospolop/PEASS-ng/releases/latest)** or **compile it yourself** (read instructions for compilation).
|
||||
|
||||
```bash
|
||||
#One liner to download and execute winPEASany from memory in a PS shell
|
||||
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/winPEASany_ofs.exe" -UseBasicParsing | Select-Object -ExpandProperty Content)); [winPEAS.Program]::Main("")
|
||||
# Get latest release
|
||||
$url = "https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASany_ofs.exe"
|
||||
|
||||
#Before cmd in 3 lines
|
||||
$url = "https://github.com/carlospolop/PEASS-ng/releases/download/refs%2Fheads%2Fmaster/winPEASany_ofs.exe"
|
||||
# One liner to download and execute winPEASany from memory in a PS shell
|
||||
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "$url" -UseBasicParsing | Select-Object -ExpandProperty Content)); [winPEAS.Program]::Main("")
|
||||
|
||||
# Before cmd in 3 lines
|
||||
$wp=[System.Reflection.Assembly]::Load([byte[]](Invoke-WebRequest "$url" -UseBasicParsing | Select-Object -ExpandProperty Content));
|
||||
[winPEAS.Program]::Main("") #Put inside the quotes the winpeas parameters you want to use
|
||||
|
||||
#Load from disk in memory and execute:
|
||||
# Load from disk in memory and execute:
|
||||
$wp = [System.Reflection.Assembly]::Load([byte[]]([IO.File]::ReadAllBytes("D:\Users\victim\winPEAS.exe")));
|
||||
[winPEAS.Program]::Main("") #Put inside the quotes the winpeas parameters you want to use
|
||||
|
||||
#Load from disk in base64 and execute
|
||||
# Load from disk in base64 and execute
|
||||
##Generate winpeas in Base64:
|
||||
[Convert]::ToBase64String([IO.File]::ReadAllBytes("D:\Users\user\winPEAS.exe")) | Out-File -Encoding ASCII D:\Users\user\winPEAS.txt
|
||||
##Now upload the B64 string to the victim inside a file or copy it to the clipboard
|
||||
@@ -41,7 +43,7 @@ $thecontent = "aaaaaaaa..." #Where "aaa..." is the winpeas base64 string
|
||||
$wp = [System.Reflection.Assembly]::Load([Convert]::FromBase64String($thecontent))
|
||||
[winPEAS.Program]::Main("") #Put inside the quotes the winpeas parameters you want to use
|
||||
|
||||
#Loading from file and executing a winpeas obfuscated version
|
||||
# Loading from file and executing a winpeas obfuscated version
|
||||
##Load obfuscated version
|
||||
$wp = [System.Reflection.Assembly]::Load([byte[]]([IO.File]::ReadAllBytes("D:\Users\victim\winPEAS-Obfuscated.exe")));
|
||||
$wp.EntryPoint #Get the name of the ReflectedType, in obfuscated versions sometimes this is different from "winPEAS.Program"
|
||||
@@ -103,9 +105,13 @@ REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1
|
||||
|
||||
Below you have some indications about what does each color means exacty, but keep in mind that **Red** is for something interesting (from a pentester perspective) and **Green** is something well configured (from a defender perspective).
|
||||
|
||||

|
||||
|
||||
## Instructions to compile you own obfuscated version
|
||||
|
||||
<details>
|
||||
<summary>Details</summary>
|
||||
|
||||
In order to compile an **ofuscated version** of Winpeas and bypass some AVs you need to ** install dotfuscator ** in *VisualStudio*.
|
||||
|
||||
To install it *open VisualStudio --> Go to Search (CTRL+Q) --> Write "dotfuscator"* and just follow the instructions to install it.
|
||||
@@ -123,10 +129,9 @@ Once you have installed and activated it you need to:
|
||||
|
||||
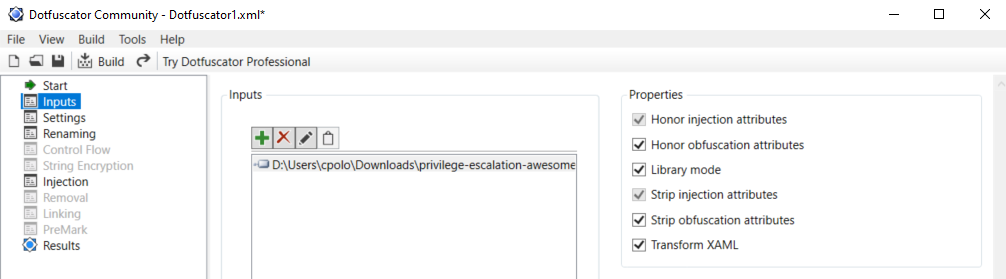
|
||||
|
||||
|
||||
## Colors
|
||||
|
||||

|
||||
**IMPORTANT**: Note that Defender will higly probable delete the winpeas iintial unobfuscated version, so you need to set as expections the origin folder of Winpeas and the folder were the obfuscated version will be saved:
|
||||

|
||||
</details>
|
||||
|
||||
## Checks
|
||||
|
||||
@@ -279,8 +284,5 @@ If you find any issue, please report it using **[github issues](https://github.c
|
||||
|
||||
All the scripts/binaries of the PEAS Suite should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
|
||||
|
||||
## License
|
||||
|
||||
MIT License
|
||||
|
||||
By Polop<sup>(TM)</sup>, makikvues (makikvues2[at]gmail[dot].com)
|
||||
|
||||
Reference in New Issue
Block a user